
How to Java: E5 (For Loops)
Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.


Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.
Just about a year ago, Google launched an update to the Gmail app for Android that let you link accounts from other email services to Gmail, allowing you to read and respond to everything in one place.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually released quite a few awesome Android apps.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Sony's Xperia smartphones are some of the most beautiful Android devices out there—but unfortunately, they're rarely promoted in the U.S. and are seldom available through major carriers (aside from the new Xperia Z5 devices), so not many Americans are aware of how awesome these devices really are.

Getting cool new features before everyone else is just plain fun. To be on the bleeding edge can require a lot of effort at times, since the fastest way to get an update is to find it as soon as it leaks, then get to work on sideloading the new version. Luckily, there's an easier way to get the latest features on your favorite apps, with WhatsApp being no exception.

Hello there Nullbyte users! This will be my first article here.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.
Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.
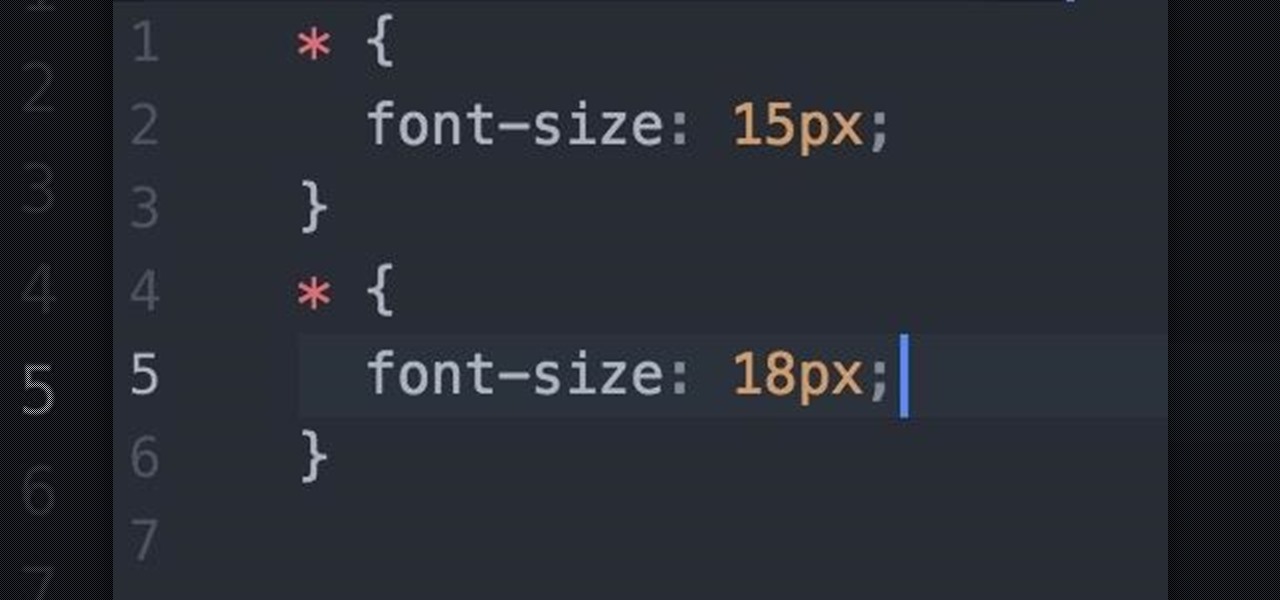
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

What's up guys! It's time to discuss strings in more detail. Review

The Nexus 5X and Nexus 6P have identical camera hardware—in fact, both use one of the highest-end camera sensors ever put into a smartphone. The only real difference between the cameras on Google's latest flagship devices is that the 6P natively supports electronic image stabilization (EIS) whereas the 5X does not.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.
Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:
How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

Whether you've watched Game of Thrones or read the A Song of Ice and Fire series by George R. R. Martin, you probably know the White Walkers (aka the Others) all too well. They're creepy, otherworldly humanoids shrouded in icy white skin and ice-blue eyes. They are not to be confused with the wights, the reanimated corpses that the White Walkers control.

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1
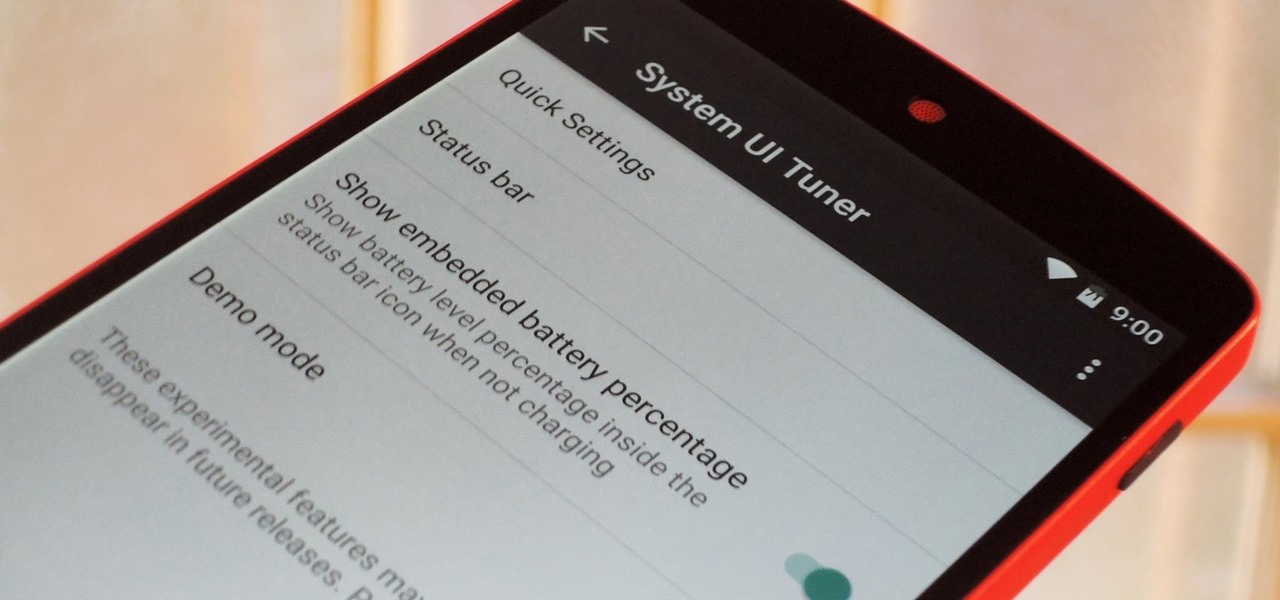
Android 6.0 Marshmallow is bringing in lots of changes to our favorite smartphone operating system, ranging from battery-saving tweaks like Doze to a Now on Tap feature that essentially bakes Google right into every app on your phone. But for folks that like to tweak the interface of their device, a new hidden menu might be the most exciting addition of them all.
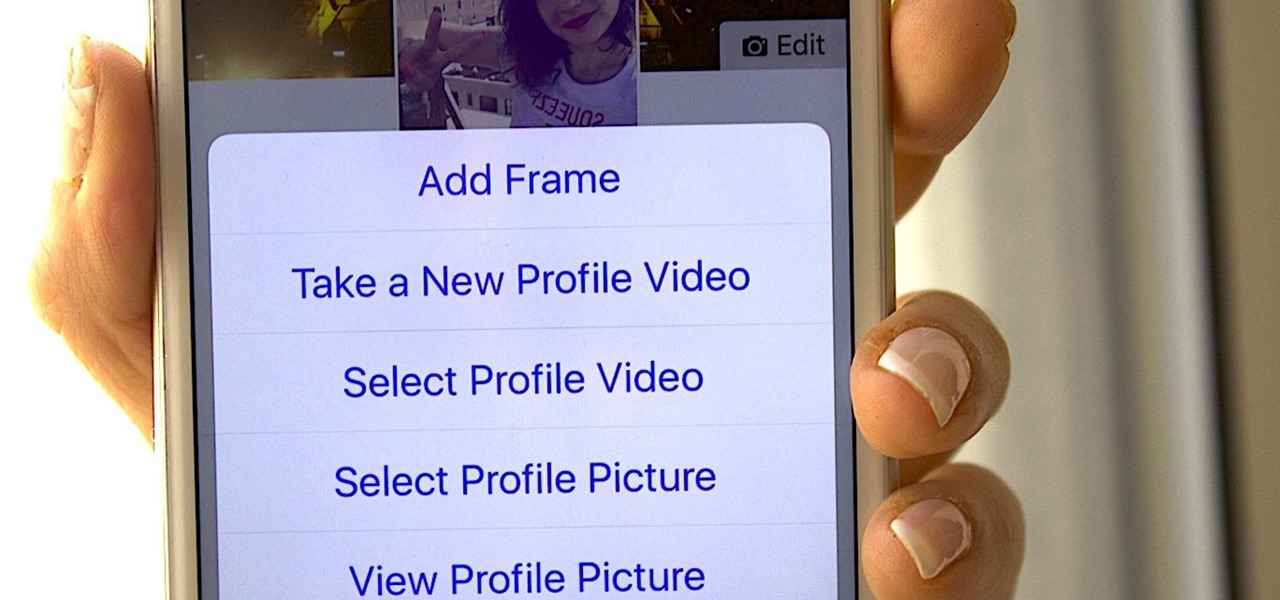
Instead of the still image we've been accustomed to since the inception of Facebook, you also have the option to apply a seven-second video as your profile image, which definitely mixes things up a bit with GIF-like animations. Best of all, this can be done straight from your iPhone or Android device.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

Snapchat provides a handful of filters and overlays which allow you to show off your location, make your pictures more colorful, or even display how fast you're moving. But unlike Instagram, Snapchat only allowed you to use a single filter per photo or video... or at least that's how it seemed.

A no-carb, gluten-free substitute for breadcrumbs. Sounds and probably tastes like cardboard, right? Unless you're talking about Pork Dust. Yes, you read that right. Pork. DUST.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

My all-time top songs are the ones that speak to me on a deeper level, and it's through the lyrics that artists are able to make that connection. It's a feeling unlike any other when it seems that an artist or song is speaking exclusively to you or your current circumstance.

Snapchat has built upon the photo-sharing service it once was to become a money-sending, commercial-shelling, video-messaging giant. They improved their user experience by adding Stories, Geofilters, and even the rarely-used Snapcash feature, but why isn't there something as simple as color filters? Yes, they have filters for black and white, saturated, and sepia, but that's it as far as color goes.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...