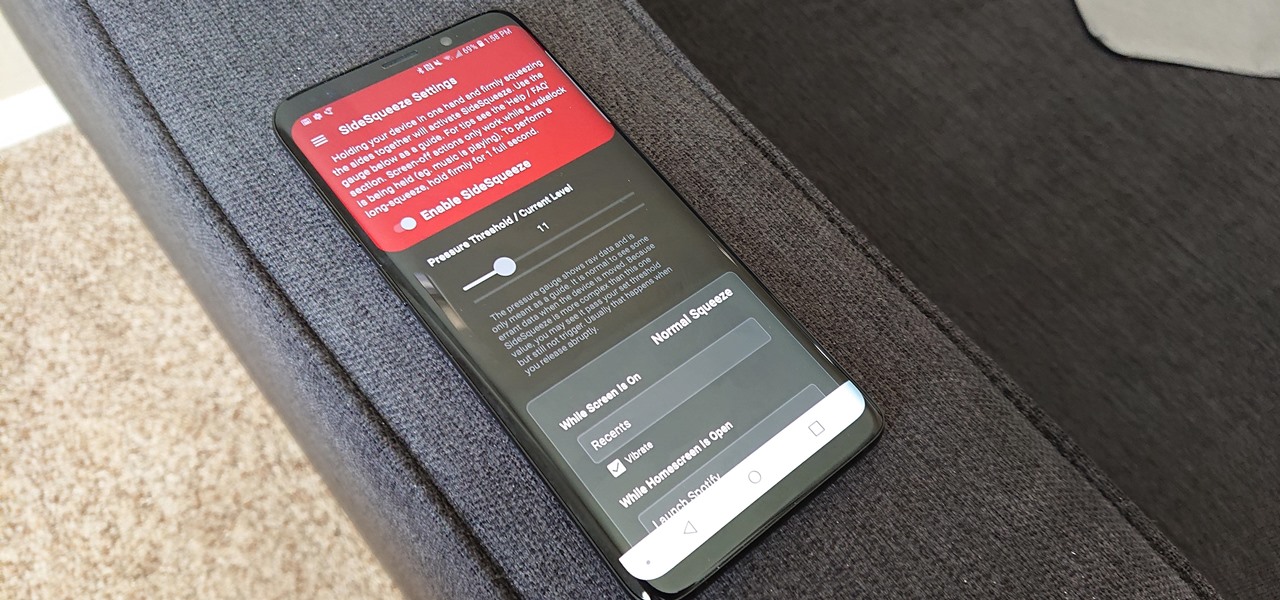
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

Before, the only way to really tell how your iPhone's lithium-ion battery was performing was to use tools such as Geekbench and Battery Life, but now Apple has included some quick battery health checks right into iOS 11.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Pot, weed, bud, herb – whatever you want to call it, the green earthy treat makes everything way more fun. Now that marijuana is legal to some extent in more than half of all US states, we thought it was high time to showcase some apps that enhance your experience with the controversial pastime known as rolling up.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Hello friends. This is actually my first how to.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' and wondered what it meant. You also may have come across this term in reading about the late Victorian era. No worries, I'll tell you all about it! Image by Giovanni Dicandia

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

You may use Safari on your iPhone or iPad to open links and browse the web, but there's so much more it can do for you. On updated software, you can implement third-party Safari extensions in your browser that go above and beyond content blocking, sharing, and performing basic actions.

From Time Machine to Cartoon 3D Style, Snapchat has strung together a run of viral AR Lenses as consistently as Beyoncé drops hits songs.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

You're halfway through reading an article on your iPhone, when the display just turns off. Frustrated, you open the article again, only for the display to go black again. You shouldn't have to keeping touching the screen to keep your iPhone from going to sleep. Luckily, you can delay or even stop your iPhone from doing so with just a few taps.

If there's an influential tweet, you can see what people are saying about it by reading its comment thread. But what about quote tweets, aka tweets someone posted on their own timeline that quote the initial tweet? These don't show up in comment threads, but there is a way to find them.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

If you need some help expressing how you feel to your mom for Mother's Day, Snapchat and Facebook are here with some augmented reality help.

Next to Game of Thrones, Harry Potter is one of the most beloved franchises in entertainment today, and now we have another peek at its dive into augmented reality.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

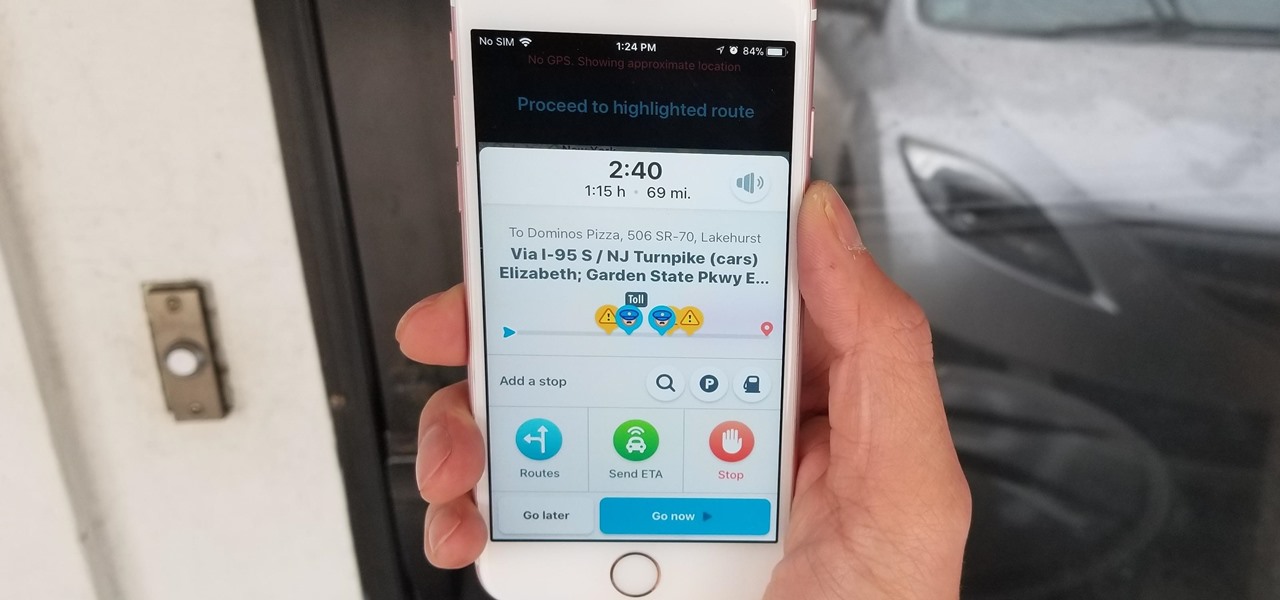
Discovering you're on a route filled with tolls while you're already on the road, with no cash on hand, is never a pleasant surprise. Fortunately, Waze has an incredibly simple solution to nip this potential headache in the bud and save you money while navigating.

Think you're a true Star Wars fan? I bet you haven't created a demo using Apple's ARKit that creates a map of the entire Star Wars galaxy. How's that for being a fanatic?

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

Whether you're hard of hearing, watching a foreign movie, or just like reading along when you're watching a TV show or film on your smartphone, Netflix includes captions and subtitles that you can use. Best of all, if you don't like the way the default captions and subtitles look (color, background, font, or size), Netflix has your back.

As you all journey along with me on my challenge to become some sort of Instagram expert, let me share with you one hack that is currently helping me out a lot. If you've ever wanted to put a line break in your posts, then keep on reading.

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

We just keep discovering hidden features and settings scattered throughout the Galaxy S8's system like little digital Easter eggs that were largely left unadvertised. One such setting is an option that lets you change the placement of your S8's display brightness slider.

It's never fun to fidget around with your phone's camera while you're out and about, especially when it comes to transitioning between its front- and rear-facing cameras. Thankfully, Galaxy S8 users can scratch this one off their list of inconveniences, as Samsung has built in some nifty features that let you switch from the main shooter to the selfie cam without having to look at the screen or tap on the camera switch icon.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

The Oculus Rift's virtual experiences become a little less immersive when you're barely moving in a chair with a headset on, playing on a gamepad—but you don't have to accept that reality anymore.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

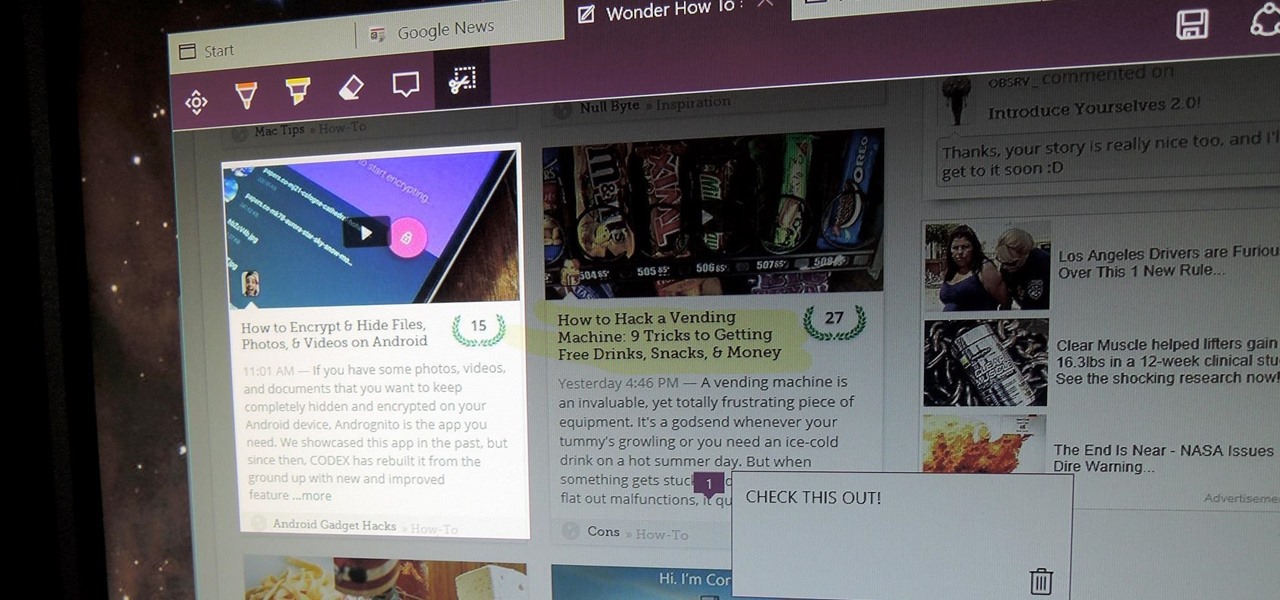
The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...

Welcome back my friends !! Today we'll go through the second part of this C# series

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.