Today, December 7, it was officially announced that Magic Leap has found their replacement for the recently departed Brian Wallace. Magic Leap CEO Rony Abovitz has tapped Brenda Freeman, former EVP and Chief Marketing Officer of National Geographic Channel, as their new Chief Marketing Officer.

People have been transforming mud into art, aka pottery, for thousands of years. This is not a new phenomenon, but often the finished product has a certain utilitarian aesthetic, such as a bowl or vase.
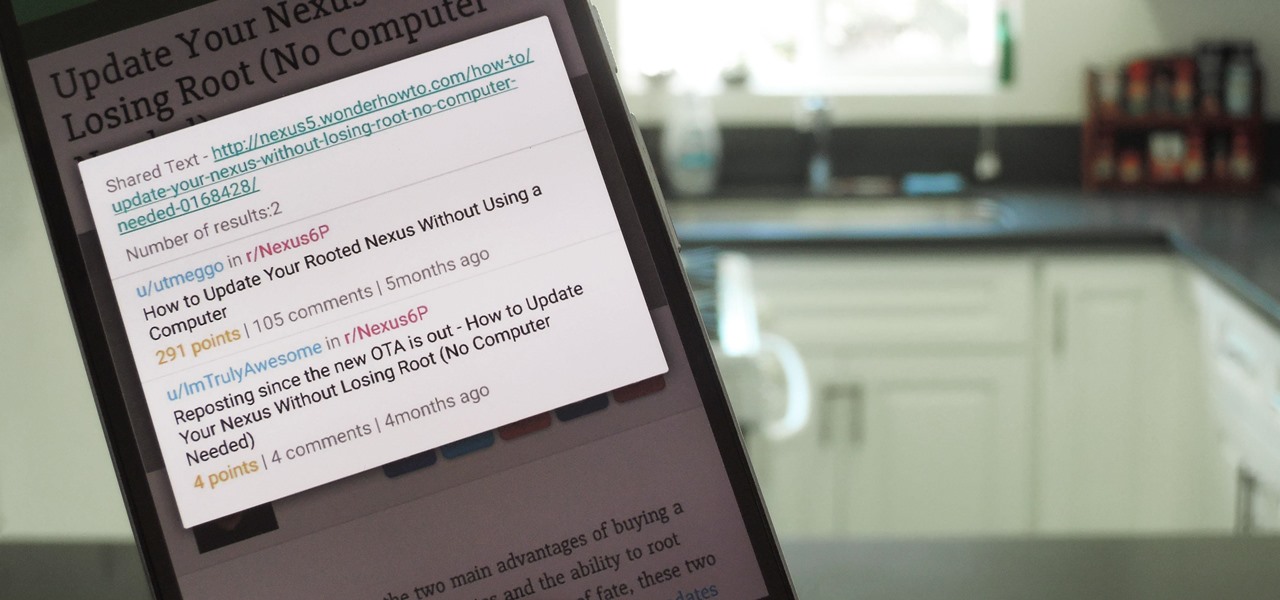
When you want to read product reviews, you go to Amazon—regardless of whether or not you intend on buying the product from their website. By the same sense, when you want to read discussions about certain topics you come across on the internet, there's no better place than Reddit.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.
If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.
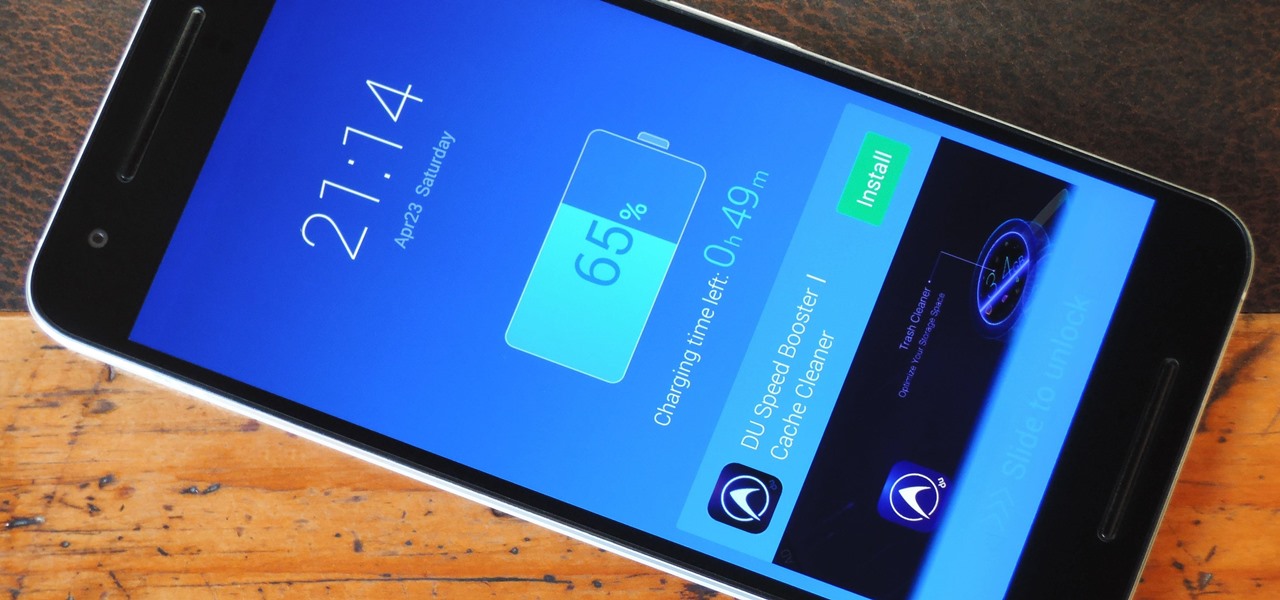
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.

With a price that undercuts flagship devices like the iPhone 6s and Galaxy S7 by hundreds of dollars and a smaller size, new tests show that the iPhone SE incredibly packs just as much power as its bigger brother.

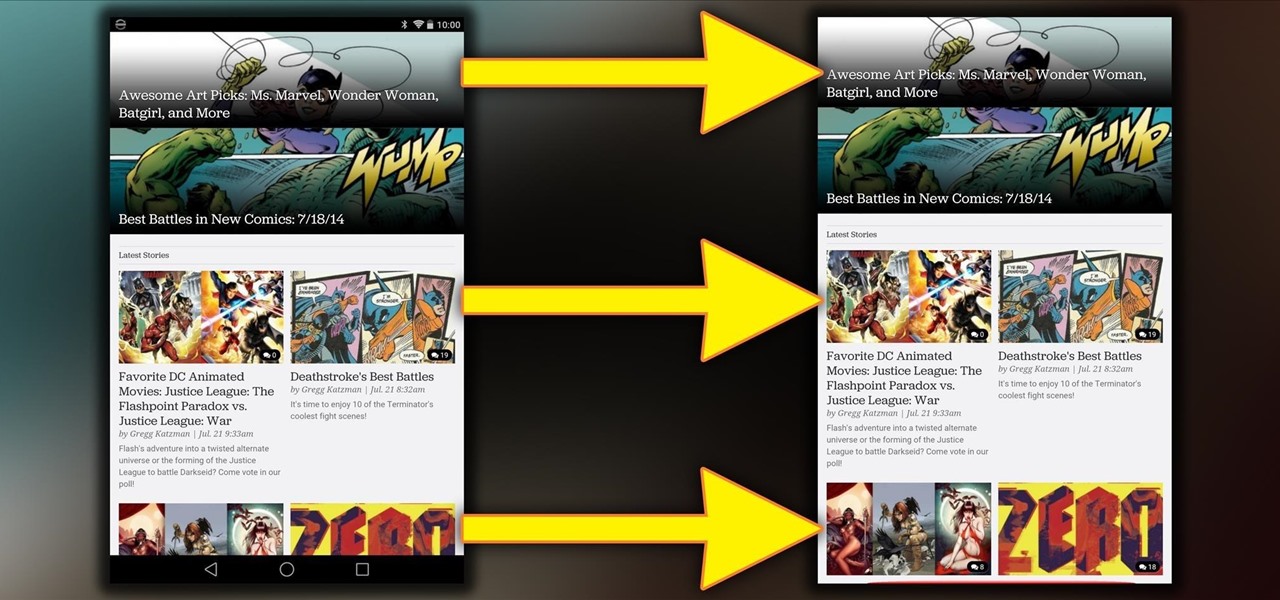
Apple unveiled a 9.7-inch iPad Pro at their keynote event today, filling their roster to four different iPads. The smaller iPad Pro has the same screen size as the iPad Air 2, but comes with significant improvements under the hood. Keynote speaker Phillip Schiller rolled into the details: it's 40% less reflective than the Air with only 1.8% screen reflectivity, 25% brighter, produces 500 nits of light (making it "the brightest tablet available"), and has 25% greater color saturation. It also ...

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

When you click a link from Google search, the link itself turns purple to let you know you've already visited this page. But let's say you're searching for something similar a few weeks from now and you see one of these purple links—you'll probably think to yourself, "What was I reading about on that site?"—and if you don't remember, you'll end up clicking the link again. And if you're a frequent Reddit user, you know this pain all too well.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

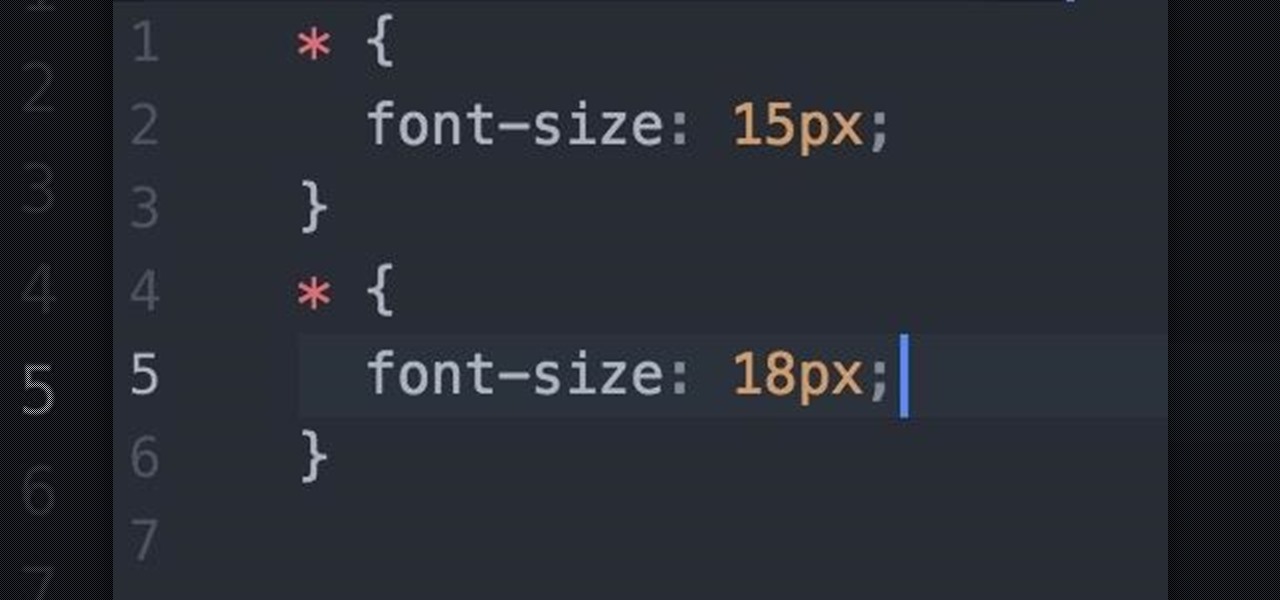
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

My all-time top songs are the ones that speak to me on a deeper level, and it's through the lyrics that artists are able to make that connection. It's a feeling unlike any other when it seems that an artist or song is speaking exclusively to you or your current circumstance.

Well, this is my first article so if it sucks tell me...lol!! Story Time

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files from Safari is almost impossible unless you're jailbroken.

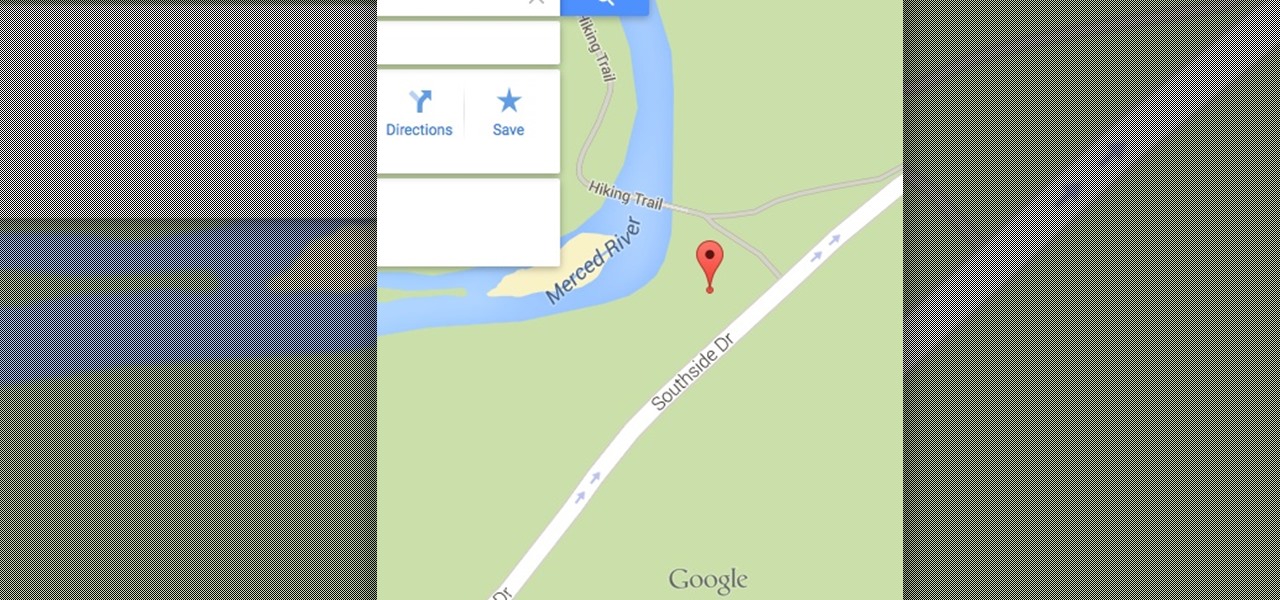
Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...

You didn't have to attend this year's CES to have gadget envy. There are so many great smartphones, computers, laptops, and other gadgets available in the market that the real challenge becomes choosing the right one to fit your needs and your budget.

We all know that opening our work emails at home is a bad habit. Yet reading and responding to emails every time your iPhone dings is worse than you might realize. Not only are you extending the workday, but you are also sacrificing your ability to perform on a daily basis.

Android "Lollipop" introduced a ton of cool new functionality. Unfortunately, the Nexus 5 didn't get all of these features, as some were exclusive to other devices. For example, the Ambient Display function on the Nexus 6 that shows new notifications as they come in with a black-and-white lock screen. Sure, the new Nexus phablet has an AMOLED display that doesn't waste any battery to power black pixels, but it would be nice to have this feature as an option on the Nexus 5, wouldn't it?

Brought to you by Tomcat. Falling snow, warm fireplace, delicious hot cocoa, quiet reading time, mouse. Quick quiz - which one is not like the other? Nothing can ruin a perfectly cozy afternoon in your home like a pest on the loose. With dropping temperatures, you may have some unwelcome residents, like mice, looking for shelter from the cold.

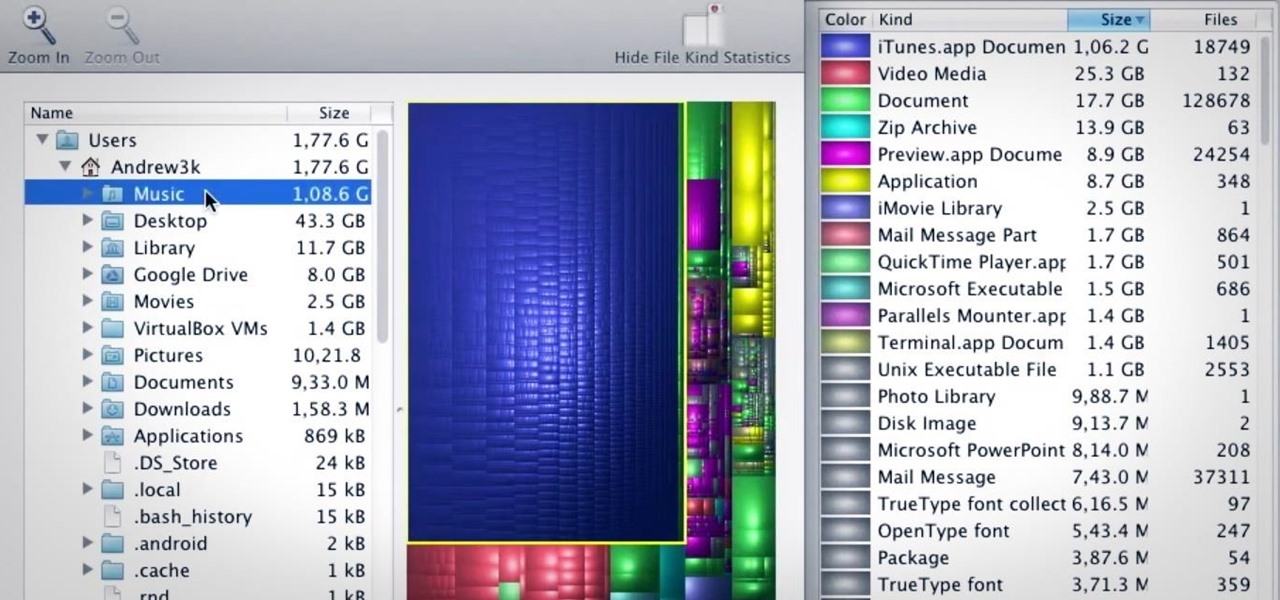
I love my MacBook Air, but the fact that it runs on only 128 GB of flash storage causes me to move most of my files to the cloud. I don't mind having to be connected to the internet in order to access my files, but it's definitely a hassle trying to figure out which files I should move in order to save the most space. Usually, I don't even bother even trying until I see the dreaded "Your startup disk if almost full" warning. Currently, the only real way to find your biggest files in Mac OS X ...

Rooting is a great way to unleash your device's full potential, but not everyone's comfortable with it. Rooting can void a warranty, cause issues with certain apps, and the process itself can be tricky for older devices. Alas, most of the great apps or mods out there require root access, like the ability to utilize a built-in KitKat feature known as Immersive Mode.

Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements.

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.

Honestly, Android's stock alarm icon is completely useless. It doesn't relay any information other than the fact that, at some point in the future, you have an alarm coming up. Considering how pointless it is, I normally install GravityBox or other similar mods just to get rid of it.