Drones are a fairly new craze to hit the nation. While they are accessible to the general population, good drones still typically cost a ton of money and despite all the fun they are, it's sometimes not worth it to actually buy one. If you're one of those people who would love to play around with drones — but don't want to have to buy one — Arcane Reality is developing the app for you thanks to Apple's ARKit.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.
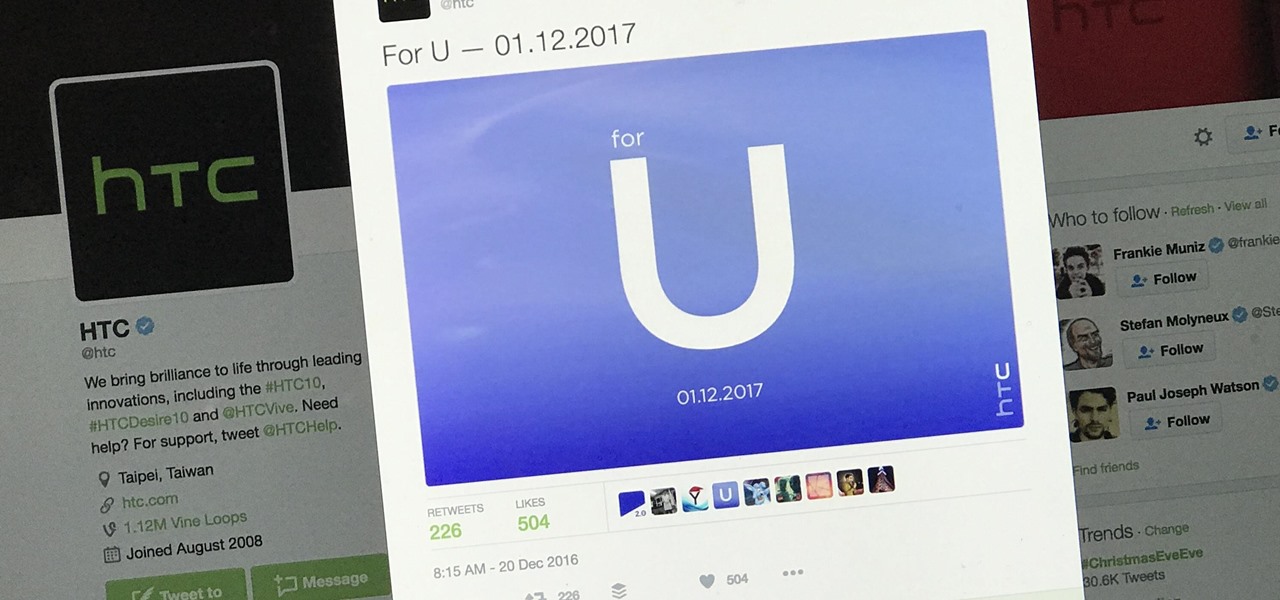
Earlier this week, a mysterious tweet appeared on the HTC Twitter account of a picture containing the letter "U" topped with a tiny "for" and the date "01.12.2017" at the bottom. It is a pretty solid teaser, but for a company that has had a solid year with their Vive virtual reality headset, and all of the other technological appendages they have, it seems a bit ominous for them.

Unity released the Beta 5.6 on December 13 with a bunch of new upgrades in the works, including support for Vulkan, better instancing options, and more improvements to particles—to name just a few that are potentially relevant to the mixed reality community. And today, December 15, Unity has just released the EditorVR that we reported on a few weeks ago as a part of their "Experimental" builds.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

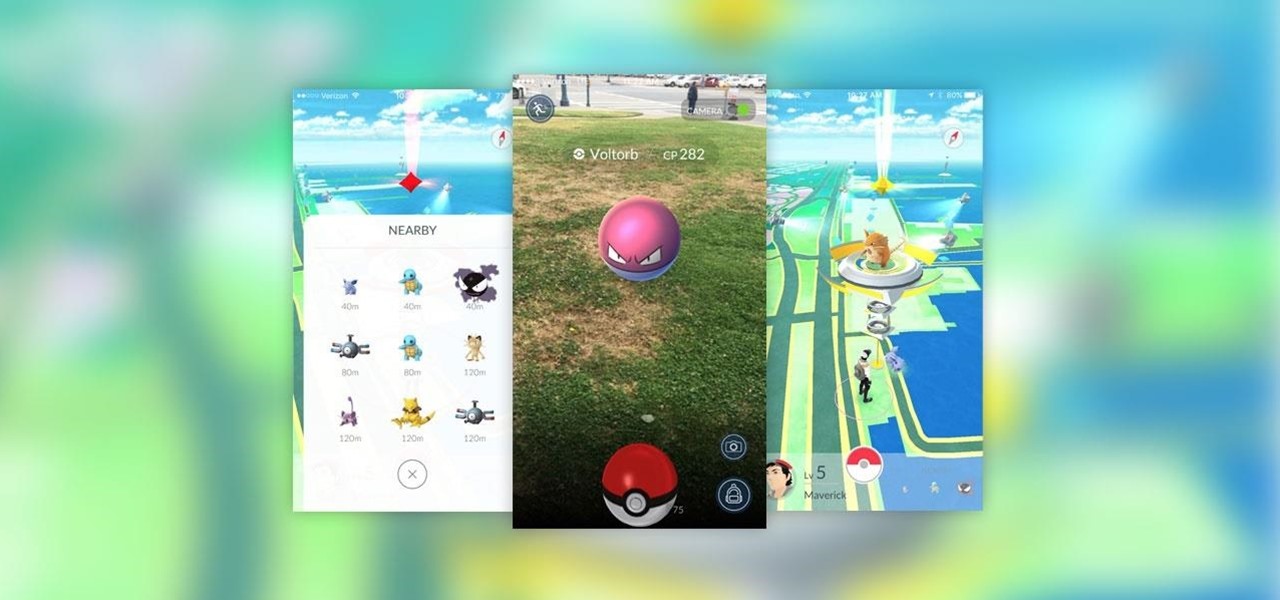
After a relatively short beta-testing period, Pokémon Go is now rolling out to Android and iOS devices right now. If you want to catch 'em all in the real world, your wait is over.

Pokémon Go takes the popular franchise and brings it into the real world through augmented reality, allowing us to play the game while exploring our physical environments at the same time. It doesn't just put pocket monsters into a more realistic context, but it changes the game in some major ways that may delight some players... and upset others.

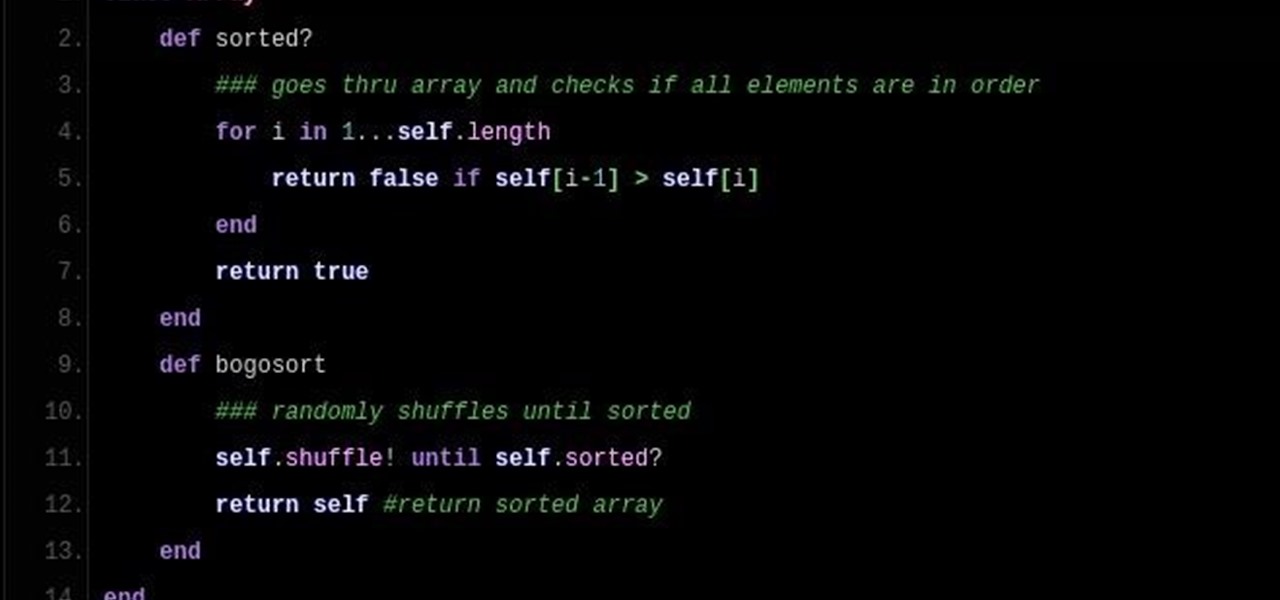
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

What's up guys! It's time to discuss strings in more detail. Review

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Well, this is my first article so if it sucks tell me...lol!! Story Time

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Google Glass is all about transforming the world around us with little to zero interaction from the wearer. Much of this is done using augmented reality—a live view of physical, real-world environments that are augmented by computer-generated input in the form of graphics, sights, and sounds.

I don't know many meat eaters who don't appreciate a good burger, but unless you eat it plain, it usually gets pretty messy. Toppings falling off and sauce running down your arms seems like it's all just part of the process.

Have you ever looked at your iPhone dock and wished you could place an extra, essential, or highly utilized app on there? Currently, with the basic settings you can only place four, but there's always that one that you wish could add to the mix.

For the most part, Xbox Live is amazing, but there is one thing that has been annoying for pretty much everyone, to say the least. Microsoft Points.

The internet is a great place to find information for pretty much anything you can think of. So why shouldn't it be a place for official higher learning? I'm not talking about a course in Wikipedia or SparkNotes, but real colleges offering real college courses completely online. And guess what—it's FREE.

There are tons of situations that require you to give out your phone number, and I think just about everyone has regretted doing so at some point. It can be incredibly convenient to have a secondary or temporary number on hand, so if you don't want to provide your real digits, you can still get the call without revealing your true numbers. And that's where Burner comes in. Burner is a mobile app for iPhone and Android that lets you create alias phone numbers that you can take out of service a...

Facebook is an awesome free online resource that is connected to billions of people around the world. These days, you won't meet many people who do not have a Facebook account. As a real estate agent, you can take advantage of social networking to promote your business and share your listings. By posting on Facebook and creating a page for your business, you gain free advertising to thousands of local buyers. Check out this tutorial and learn how to start uploading videos to Facebook to promo...

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to browse the web with Safari on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

If you want to restore your iPhone, iPod Touch, or iPad, watch this video to learn how to downgrade your iOS 5 beta iDevice to iOS 4.3.3. You've seen what you wanted to see from the iOS 5 beta, now it's time to get back to a real OS.