Marketing and healthcare, two of the leading industries in the adoption of augmented reality, continue to demonstrate applications for the technology in their businesses. Meanwhile, improvements to augmented reality devices are just around the corner with new developments from two display makers.
A Seattle development team is putting the "ARRRR" in AR with the maiden voyage of Captain Blimey, an augmented reality game for iOS and Android devices that puts a pirate premise on Pokémon GO.
This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.
The world of mobile gaming is flush with MMORPGs that entice players with console-quality graphics and gameplay, intense co-op dungeons similar to World of Warcraft, and epic loot that'll give you a leg up over your competition. While there are games like Order & Chaos that nearly match PC-based RPGs, most simply fail to measure up. But the latest entry in this genre, Crusaders of Light, may finally get players to ditch their computers for iPhones and iPads to get their online RPG fix. Crusad...

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

Osterhout Design Group just announced the upcoming release of the newest addition to their smartglasses lineup, the R-7HL, short for R-7 Hazardous Location. ODG worked directly with customers who work in extreme environments to come up with a durable solution that fits their needs; These smartglasses can not only survive but function well in many areas that would otherwise be considered too harsh for augmented reality tech.

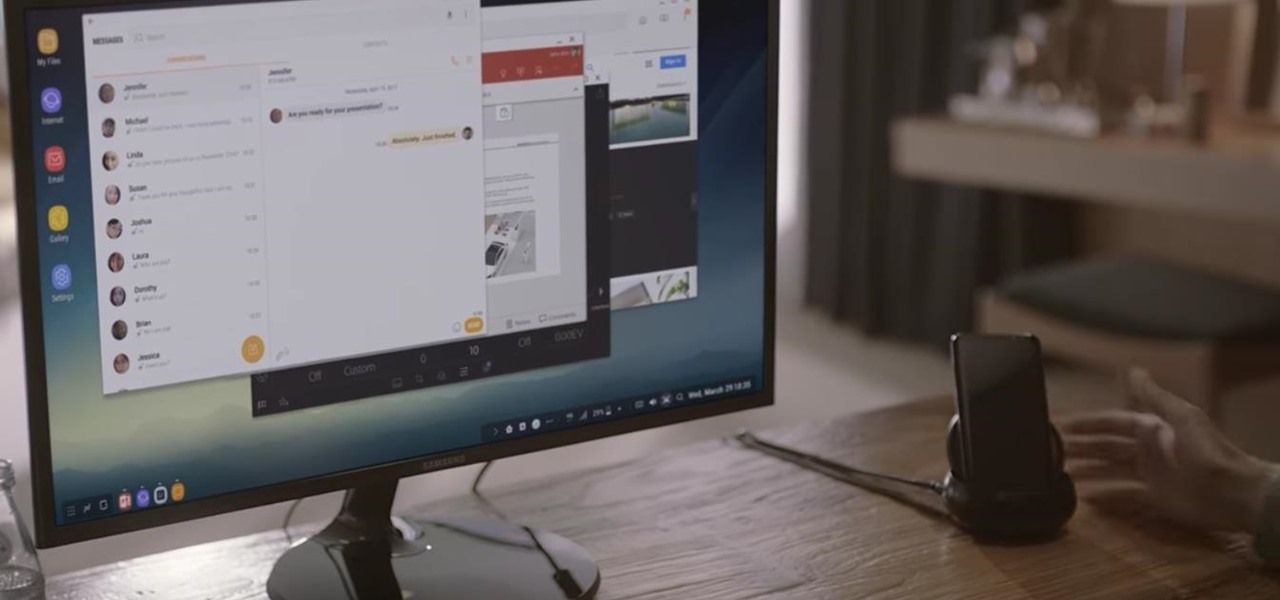
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

Maternal infection with genital herpes, or other pathogens, during early pregnancy could increase risk of autism, or other neurodevelopmental disorders, says a new study.

The iPhone has a handy feature called AssistiveTouch that lets you quickly adjust volume, lock your screen, rotate your display, and even navigate through the phone's interface using a virtual home button. In a way, it's a lot like the on-screen navigation bar that you'll find on some Android devices, but with a lot more functionality, and bundled together in a floating bubble interface.

DigiLens, a company specializing in optical waveguide technology, recently announced that they had closed a $22 million round of strategic investment, also known as Series B funding. This round brought in Sony, Foxconn, Continental, and Panasonic, as well as more traditional venture investors such as Alsop Louie Partners, Bold Capital, Nautilus Venture Partners, and Dolby Family Ventures.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Each year we inevitably fall into the pumpkin spice game. From the usual (like lattes and muffins) to the slightly more absurd (like Pringles and beef jerky)—if the leaves are turning colors and food ain't pumpkin spiced, it ain't worthy of consumption.

In the world of analog synthesizers, hitting a key, twisting a knob, or sliding a fader makes a beautiful musical (or not so musical) sound and can be an amazing and downright satisfying experience. Now it's about to get even more satisfying, if you add Microsoft's HoloLens into the mix as a means to twist those knobs virtually instead.

Now that Google has announced its new Pixel smartphones, folks who rushed to buy an iPhone 7 might be experiencing a bit of buyer's remorse. The new Pixel and Pixel XL are packed to the brim with cutting-edge features and top-notch hardware, and Google seems to be taking direct aim at the iPhone 7 with its Pixel marketing (and their groan-worthy jokes during the keynote).

I'm sure I'm not the only one on here that has googled "Why am I always tired?"... and I'm definitely not alone when I say that all of the advice I've found so far is useless:

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

Thanks to Snapchat, we're all familiar with face swapping and augmentation thanks to some clever, fun technology. But that's just the beginning, because this kind of augmented reality can do so much more.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Virtual reality headsets are all the rage these days, and among the menagerie of tech companies gunning for the top spot, there's one mysterious startup that is ahead of the game—Magic Leap—and you can tell just by watching their latest demo video of their product in action.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Fast food is a guilty pleasure in which we all indulge. When you're short on time and long on hunger, being able to whiz through the drive-thru or run 'in and out' of a fast food joint can be a real lifesaver.

Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

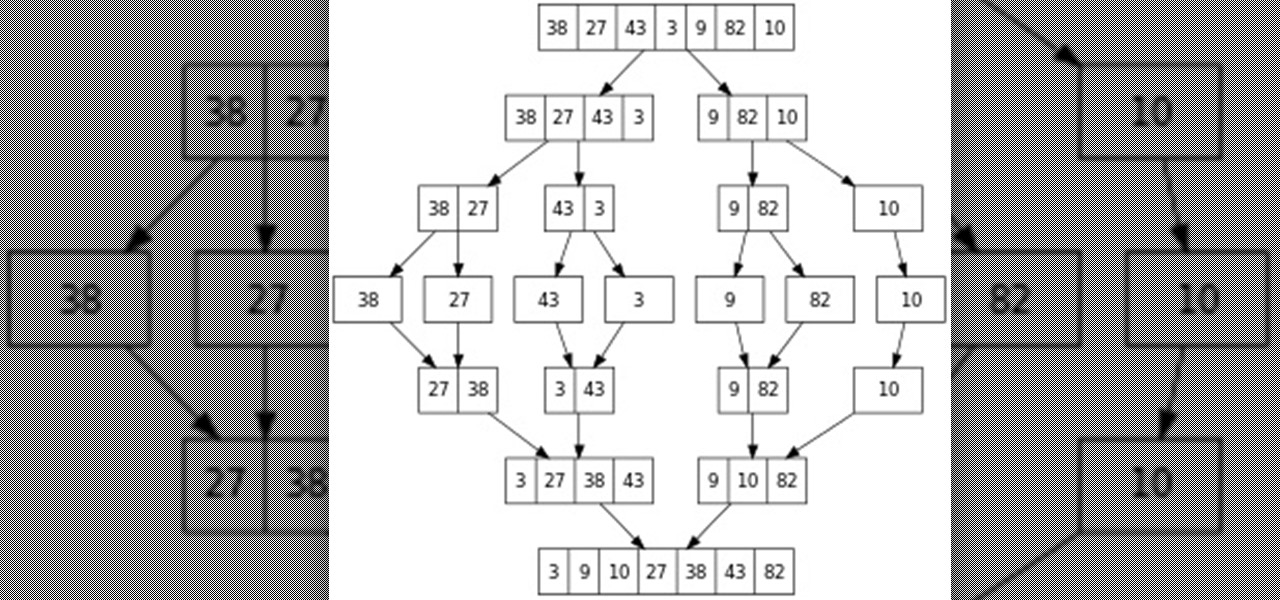
Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Obviously this is just a teaser, and who knows how soon we'll see something like this in real life, but just go ahead and watch the video first before you continue reading.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.