Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.
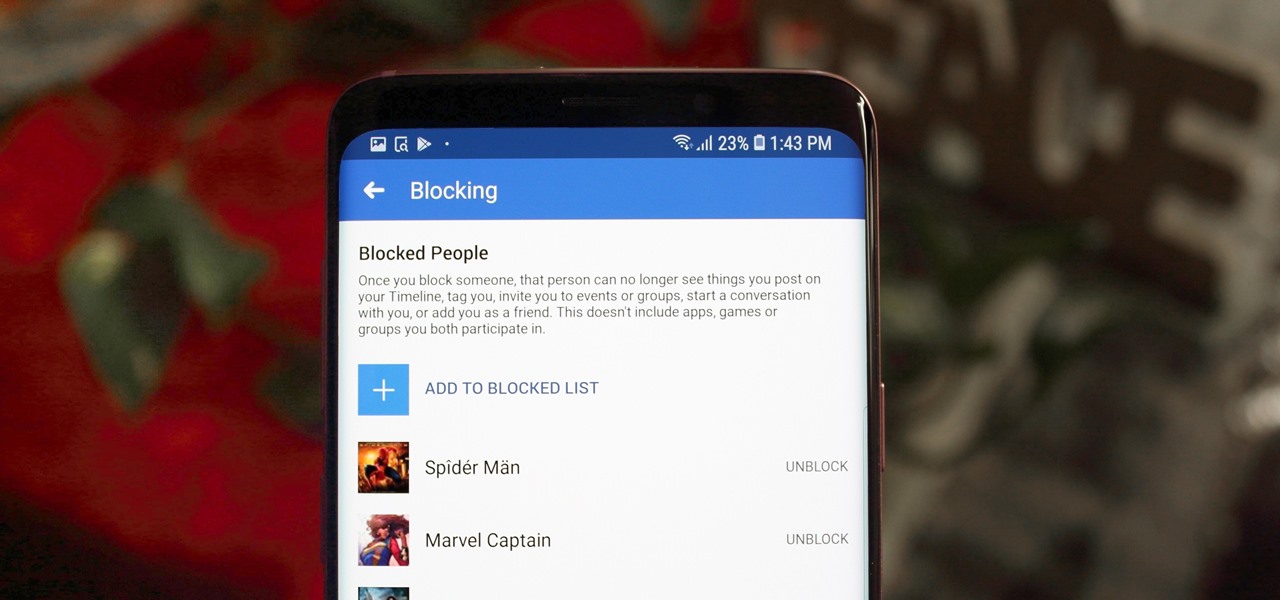
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your profile altogether. It's not just a tool for the full desktop website — in fact, the blocked list is easy to manage right from your phone.

Returning to the spotlight after its debut at last year's CES, augmented reality smartglasses maker Rokid is back with a new update.

Publicly, things have been pretty quiet over at Meta, the augmented reality headset and software startup based in Silicon Valley. But that doesn't mean that the company doesn't have a few strong opinions about the state of AR in 2018.

The last update to iOS 12 featured more emoji, Group FaceTime, eSIM functionality, real-time depth control for new iPhones, and a few other interesting tidbits and fixes. Now, in the latest for iPhones, iOS 12.1.1, Apple brought back a few things that were removed or made more difficult to access in previous updates, and it even has a few new features to offer, albeit small ones.

French cosmetics giant L'Oréal isn't wasting any time putting its new subsidiary, ModiFace, to work. On Thursday, the company launched a new tool that enables a photo-realistic augmented reality simulation of nail polish shades and textures to be accurately displayed on a user's fingers in real time.

Now that the Magic Leap One is out in the real world, the mystery behind the company lies not in whether it will actually ship a product, but when it will ship a consumer product. Or, does CEO Rony Abovitz steer the company in a different direction first?

Augmented reality and drones already go together like turkey and stuffing, but a new iOS app adds some spice to the combination with a new kind of flight path automation.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

Any real Star Wars fan knows that fear is a path to the dark side, as it leads to anger, and then suffering. For players of Star Wars Jedi Challenges, though, access to the antagonistic side of the Force is now available through their mobile apps.

With HoloLens and its enterprise-focused software offerings, Microsoft continues to make an impression on companies looking to adopt augmented reality, with Toyota Motor Corporation among the latest.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children.

While these days it is better known for the cross-platform gaming sensation Fortnite, Epic Games also makes Unreal Engine, one of the top development environments for 3D content and, in turn, augmented reality and virtual reality experiences.

Among all the new Magic Leap app announcements made at the recent L.E.A.P. conference, an update to one of the company's major in-house apps went mostly unnoticed: Create 1.1.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

On Thursday, yet another piece of the Magic Leap puzzle fell into place at Twilio's Signal developer and customer conference in San Francisco.

Electronic Arts is inviting players of The Sims Freeplay and their friends to visit the homes of their Sims in augmented reality with a new AR mode that supports multiplayer and persistent content using ARKit 2.0.

As promised last week, Magic Leap has finally released the long-awaited augmented reality game Dr. Grordbort's Invaders.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

It turns out that Dr. Grordbort's Invaders is not the only Magic Leap demo to become a reality for the Magic Leap One.

Even with all the success HMD had with reviving the Nokia brand in 2017, it seems their second year is shaping up to be even better. Nokia has been steadily releasing sequels to last year's lineup, most with the new minimal bezel design language. The Nokia 7.1 is just their latest creation.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

While many of the latest content partnerships announced by Magic Leap appear to lean towards entertainment and gaming, a new partnership with medical technology provider Brainlab has Magic Leap getting down to more serious business.

Apple often cites its tight integration of hardware and software for its success. Startup Illumix is looking to do the same thing for AR gaming by building an AR platform for its apps.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

With the new iPhones coming out, many see the current mobile market as just another epic battle between Samsung and Apple. But let's not forget there are many other phones that run Android. And when you start to sift through the specs, one stands out as a competitive alternative to the iPhone XR, the LG G7 ThinQ.

Now that the iPhone XS is officially available for pre-order, Verizon and Apple are giving Snapchat users the opportunity to win the device through an augmented reality scavenger hunt rather than forking over $1,000 for one.

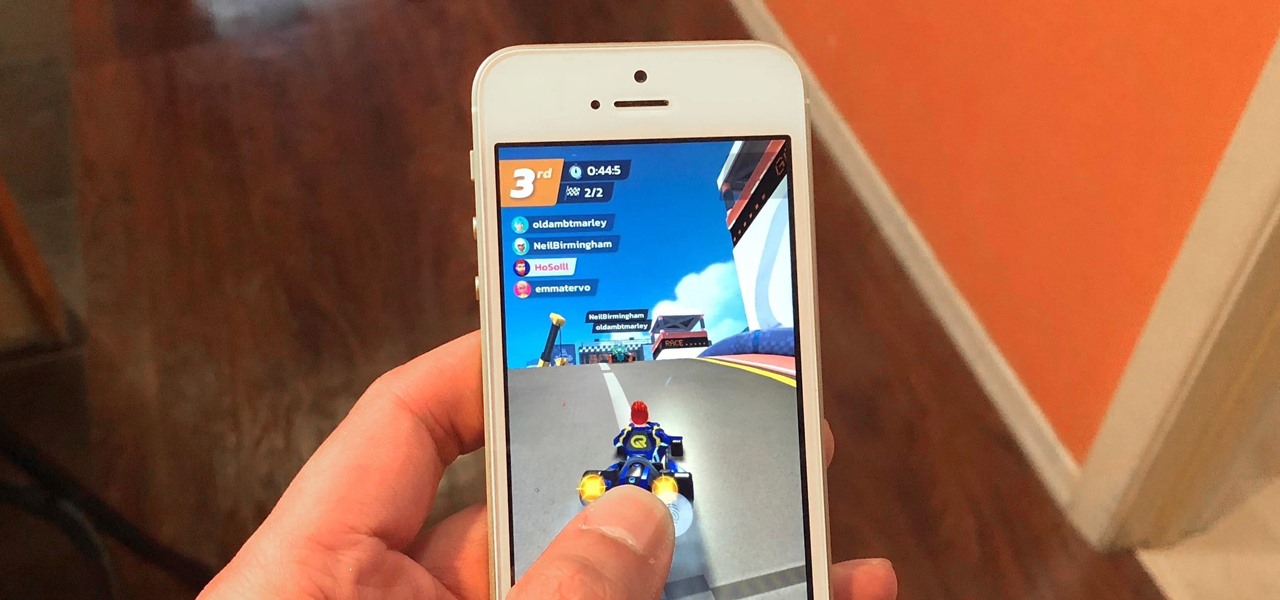
Space Ape has soft-launched Go Race: Super Karts, giving you a fresh take on mobile racing games by blending in elements found within the classic Mario Kart series and RPGs for some seriously addicting gameplay. And while it's only available in Australia, Netherlands, and Philippines, there's a workaround to get this game on your iPhone right now, no matter where you are.

A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world.

Fans attending the US Open Tennis Championships in Queens, New York, which kicks off on Monday, will have the opportunity to meet tennis star Venus Williams in an augmented reality game sponsored by American Express.

They say a picture is worth a thousand words, but augmented reality is giving the United States Holocaust Memorial Museum the ability to add a few more poignant real words to its exhibits.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

A new augmented reality framework from Disney Research could make it possible for fans to take selfies with an augmented reality Mickey Mouse, Darth Vader, or Iron Man that mimic the user's poses.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Another massive piece of the mysterious augmented reality puzzle known as Magic Leap fell into place on Wednesday as AT&T announced that it will be the exclusive launch carrier for the device.