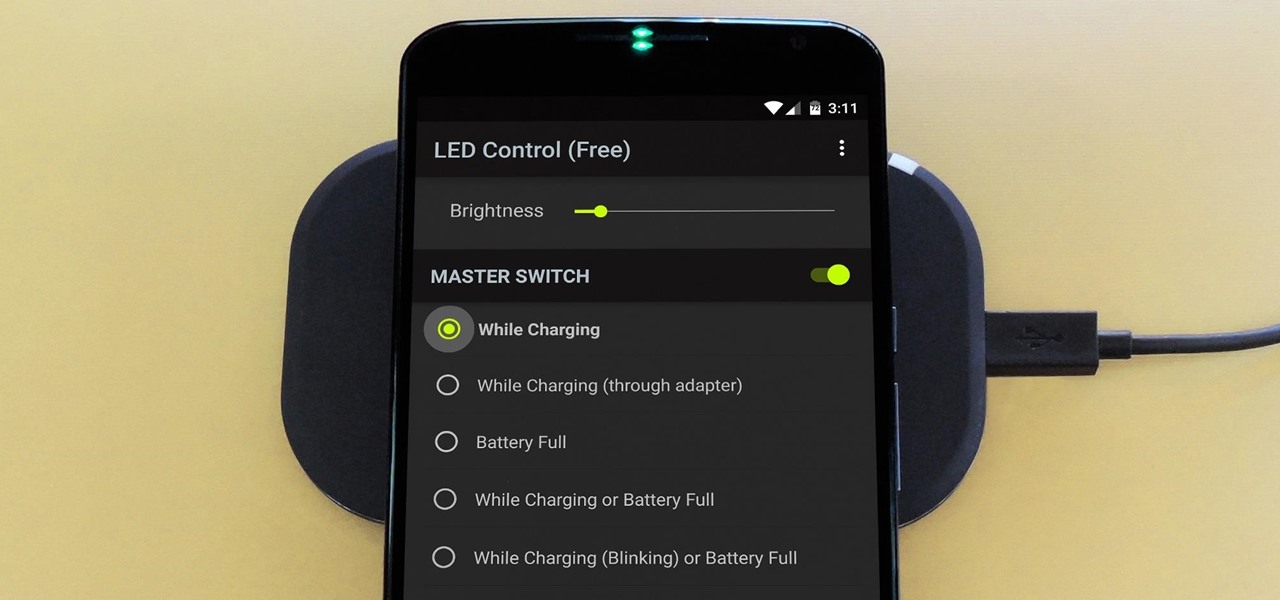
The Nexus 6 has an AMOLED screen that uses virtually no power to display black pixels. To take advantage of this feature, Google included an Ambient Display notification system that shows a black and white version of your lock screen when you get a new message. As a result, the Nexus 6 doesn't use an LED light to notify you of new incoming messages like most phones.

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

We all know that opening our work emails at home is a bad habit. Yet reading and responding to emails every time your iPhone dings is worse than you might realize. Not only are you extending the workday, but you are also sacrificing your ability to perform on a daily basis.
I wrote this about two years ago to help people make realistic passwords. The best part was while writing it I realized I encrypted the list in a manner only the maker would know.... on to the show

Did you know that your face shows others how much alcohol you drink? Whether you've never had a sip of booze with those around you or you're known as the party animal of the group, the genes that shape your appearance also show others just how much you enjoy liquor. Pinpointing the big drinker in any setting is easy to determine: you just need to make eye contact.

Back in iOS 7, Apple decided that it was actually a good thing to make the volume controls HUD translucent. This, of course, means that whatever you're watching on your screen will be obstructed temporarily whenever you adjust the volume.

Motorola changed the way users interact with their devices when they introduced their "always listening" feature on the Moto X. When I first saw it demoed, I couldn't wait to get the same functionality on one of my handsets, and now that has finally come to fruition.

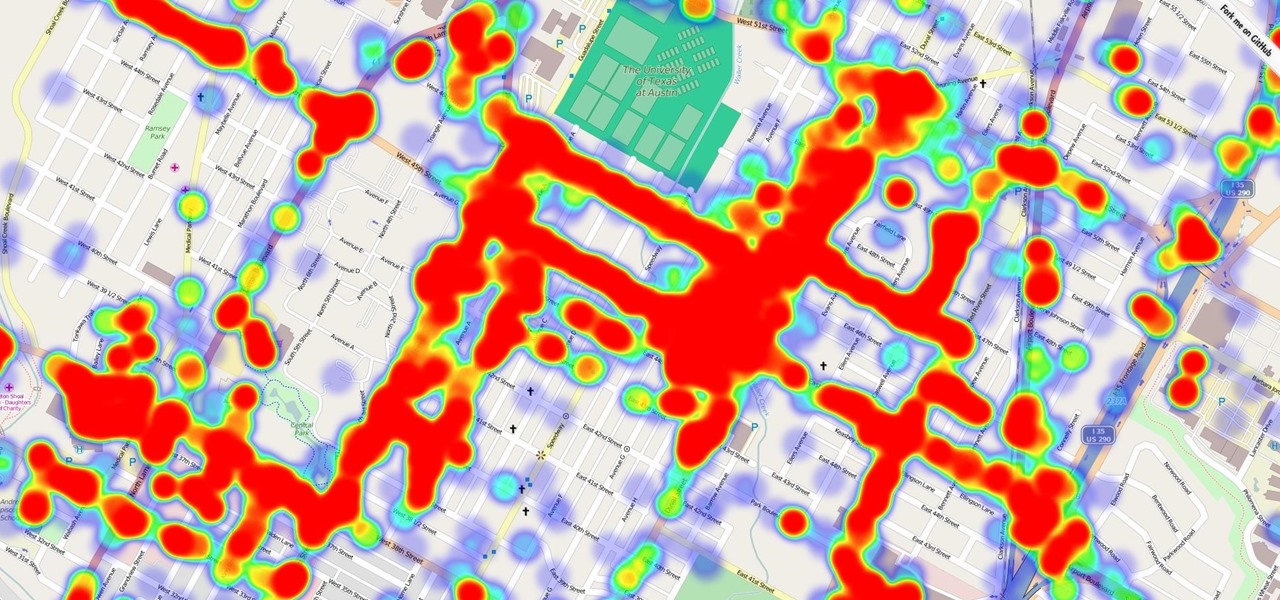
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

After a few unnecessary U-turns, I quickly realized that Apple Maps wasn't for me, which is why I hate that it opens as the default app any time I select a shared location or an address from Yelp. Copying and pasting the address to Google Maps isn't a huge deal, but it's certainly not as fluid of a process as I'd like.

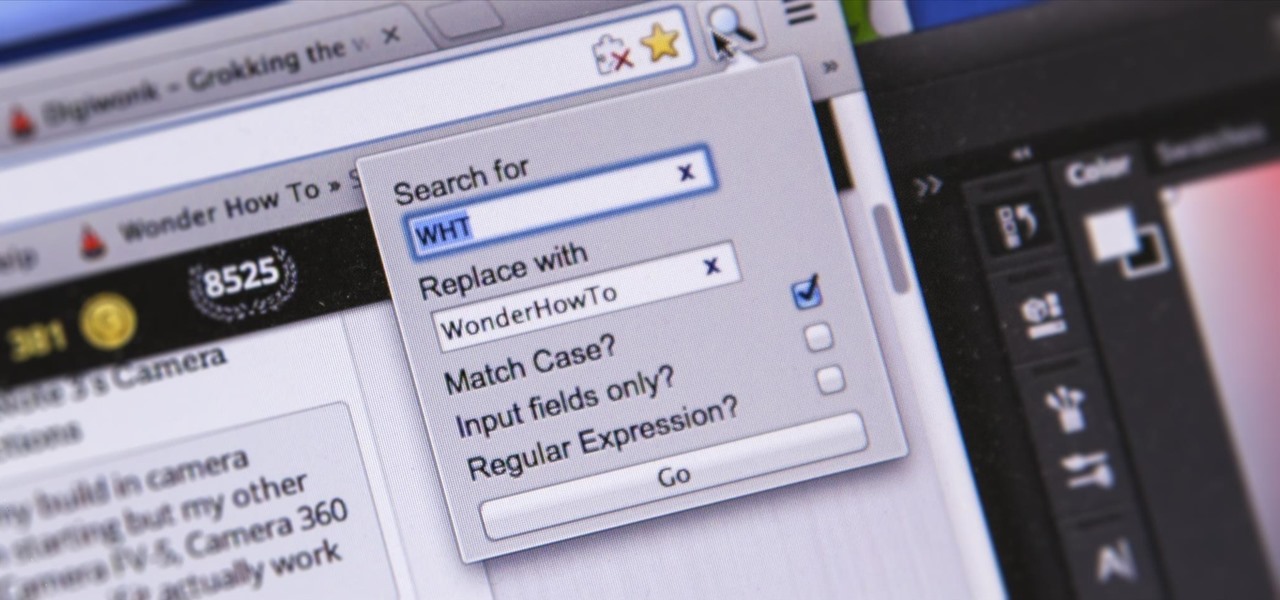
I'm sure you've been there—halfway through typing something out, you realize that one word you've been using more than any other has been misspelled. Perhaps it's a single word, acronym, or line of code that you find yourself typing quite often at work, but this one requires complicated hand gymnastics that you'd simply rather not perform over and over again.

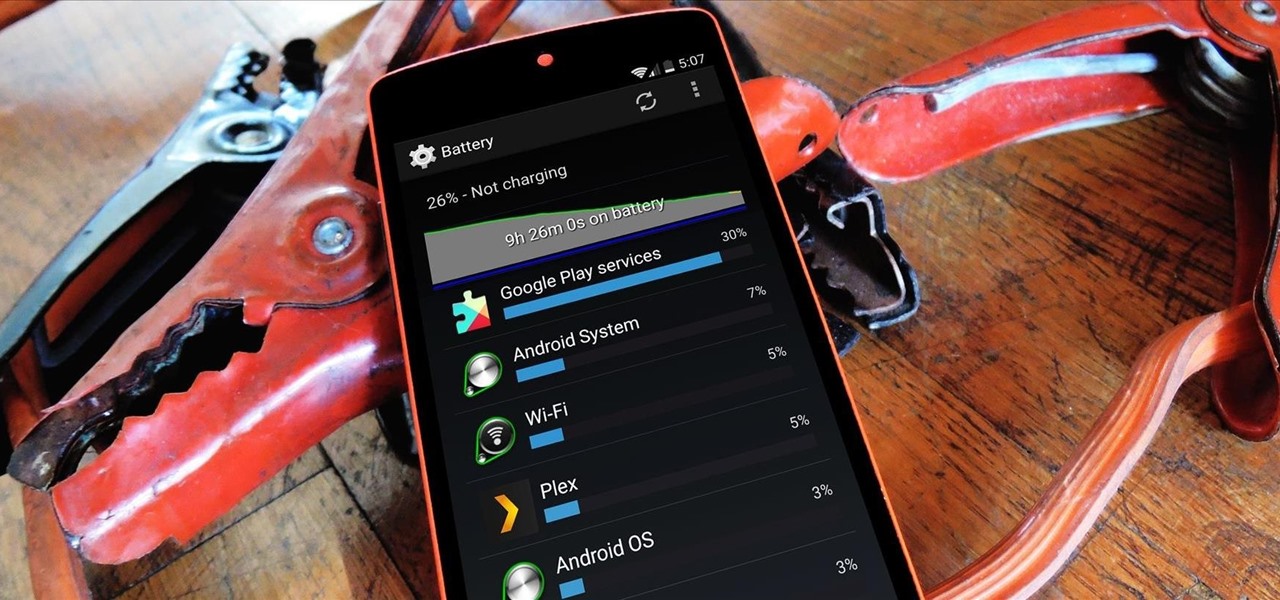
An app can request a wakelock to prevent your Android device from entering sleep mode so that it can sync data in the background. This obviously drains your battery, because instead of running in low-power sleep mode, your processor is fully activated while it performs its tasks.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

You don't have to be Drake to realize that some friends are better than others. There are friends you know are only there for the party, and friends who actually listen when you whine about your life. There are friends you go out with for a beer, and friends you call when you're drunk and need a lift at 4am.

There used to be a time when I thought that gift cards were whack. And then I realized that I would basically be picking my own presents. And as much as I love my grandma, you really only need so many sweaters.

I miss the days where my hardest assignment was drawing a Thanksgiving turkey using the outline of my hand and trying to stay in between the lines. It seems that there is some unwritten rule that adults shouldn't feel the need to draw. Well, not anymore.

If you're like me, then you were a little disappointed after updating your Nexus 7 to KitKat and realizing that not much has changed. The old Jelly Bean look still occupied your home screen, and there wasn't really anything noticeably new overall. All of that waiting and anticipation only to be left high and dry.

As precious as we like to think that all of the photographs on our smartphones are, they're really not. Every time I rummage through my extensive index of pictures, I quickly realize how many one-off pictures I have, which served their purpose a long time ago and are no longer important.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

The day I picked up my iPhone 5S was a very exciting day. I had taken all the correct steps in backing up my old device so that after a quick restore-from-backup (which turned into half an hour), I was right at home on the new hardware.

Have you ever heard the expression "Dress for Success" or "Clothes Make the Man"? When you're wearing a perfectly fitted designer shirt, something inside just shouts, "I look good" and when you genuinely think that, those feeling are radiated outward to all your come in contact with. That said, what kind of designer shirt are you interested in, a bargain basement discount, or one tailored made, outlining your best features?

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Earlier this month, AT&T quietly introduced a new "Mobility Administrative Fee" which levies a $0.61 monthly charge to all postpaid contracts. While it's a seemingly small amount on an individual basis adding up to $7.32 per year, with its huge customer base, AT&T stands to make around half a billion from the tight-lipped move. AT&T has stated that the fee will "help cover certain expenses, such as interconnection and cell site rents and maintenance" that's consistent with other phone carrier...

When I was moving into my current apartment, I had to store some of my things in my ex-roommate's garage for over a month while I was getting settled. One of those things was my dresser. Upon moving it into my new place, I realized something was horribly, horribly wrong—none of the drawers seemed to fit quite right anymore (if they fit at all). The combination of the differences in temperature and humidity in the garage caused them to swell and change shape. Several months later, they fit bet...

Sometimes, figuring out what to cook for dinner takes longer than actually cooking it. I can't tell you how many times I've gotten excited about a recipe, then realized that it requires marinating for twelve hours. When it's already 6 p.m., that just isn't going to work.

I'll be honest—I've never been a huge fan of camping. It's not that I have anything against nature, I'm just partial to showering and sleeping in my own bed. In fact, the only part of camping I've ever really enjoyed is sitting around a campfire. Outdoor fires are perfect for socializing and cooking hot dogs, but they're also great at helping remove one of camping's biggest annoyances.

I loved the Gold Rush unit back in third grade. We went up to the American River and panned for gold, and my panning skills balled above all. I got like three tiny pellets. Of course, it was all fool's gold, aka pyrite, but it was still pretty legit. And this was before wearing gold chains was cool—or not.

In this video, I show you how to build tinfoil cars for crushing with toy Monster Trucks. My son Eston and I love monster trucks. One of the most exciting things when you go to see monster trucks live, is when they crush cars. Problem is, when you use your hot wheels or matchbox cars with your monster trucks, they don’t get smashed. So the realism isn’t there.

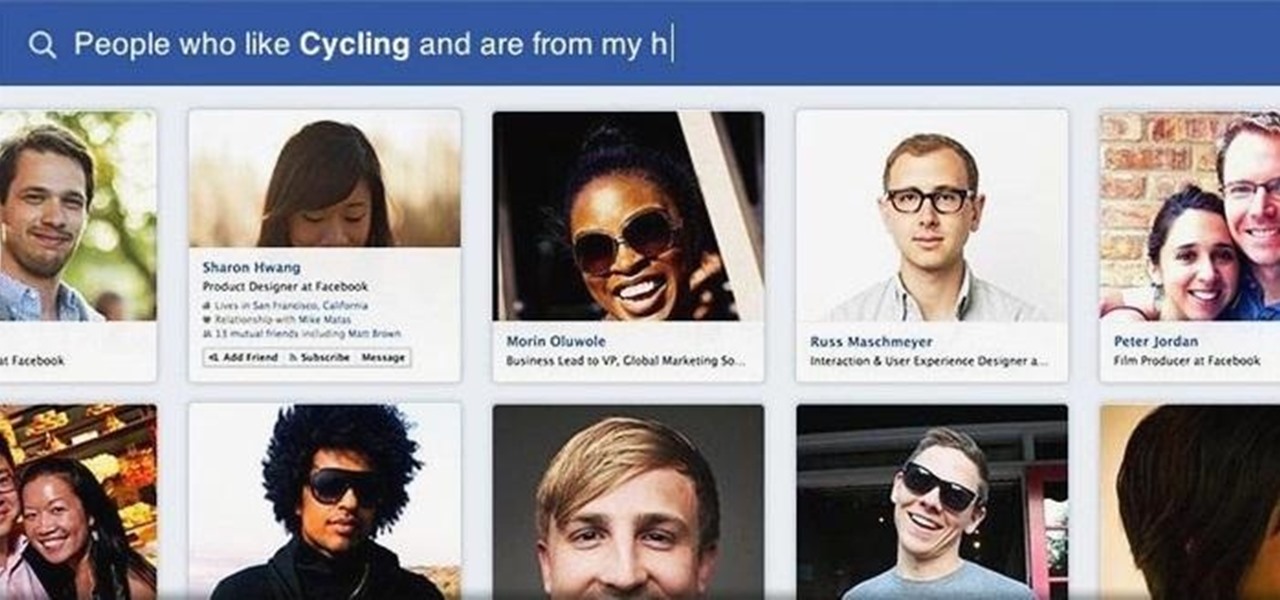
Facebook has been looking to launch a new product for a while now, and it seems they've finally realized what they're best at—being as creepy as possible. If you thought your boss checking out your girlfriend's beach photos was weird, Facebook's new Graph Search has only upped the ante. Now, I don't want to be an alarmist, because I'm sure there are a bunch of great things a Facebook search would find. If you're single, perhaps you could search "Girls that are single that like Goodfellas." Th...

As a kid, I remember hearing the myth that Twinkies could last forever. The rumor was that they were made from chemical ingredients that caused the Twinkies to stay fresh and edible for years and years. Right along with the cockroach, Twinkies were supposed to be the only survivors of the nuclear holocaust that would destroy the entire world. As I got older, I realized the rumor wasn't true. Twinkies actually have a shelf life of just 25 days. And with the news that Hostess is going out of bu...

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

Most of the time, when I’m bored during math class, I play with my calculator to satisfy my boredom. Recently, I've discovered that when multiplying any number by 11, 111, or any number similar to it, that it has a pattern (though I guess everything in math has a pattern). I don't know if this technique is original, because I didn't read anything about this. It's just mere observation. If it’s a tried and true technique, let me know.

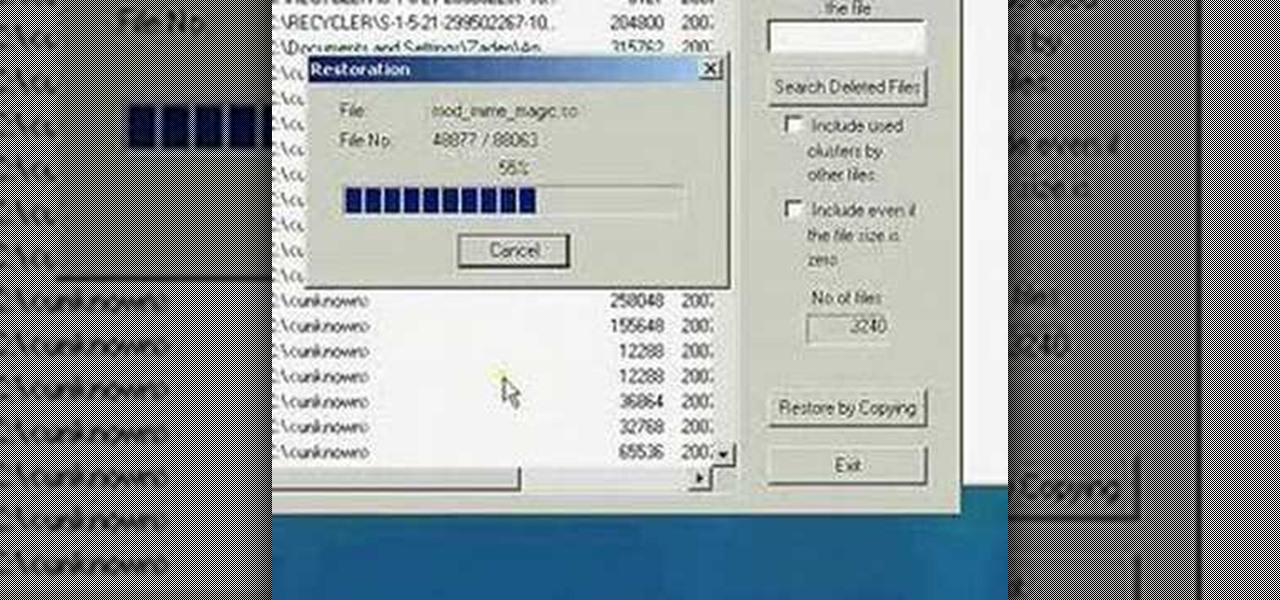
A very unfortunate event is to realize that you deleted some PC files that you need. This happens to a lot of people, but the files can be restored! To do this you will have to download a freeware program called Restoration! After you have downloaded and installed it, start the program, and select the driver for the program to search. The program will search that driver, showing you all of the deleted files in the past. The list will be long, but with a bit of patience, you should find the mi...

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

I don't know about you, but I'm tired of hearing some of the same old jargon from people online who claim that all you need to make it on Instagram is to take good pictures and post consistently. Yes, for sure, but do you really think it's that easy?

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.