Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.
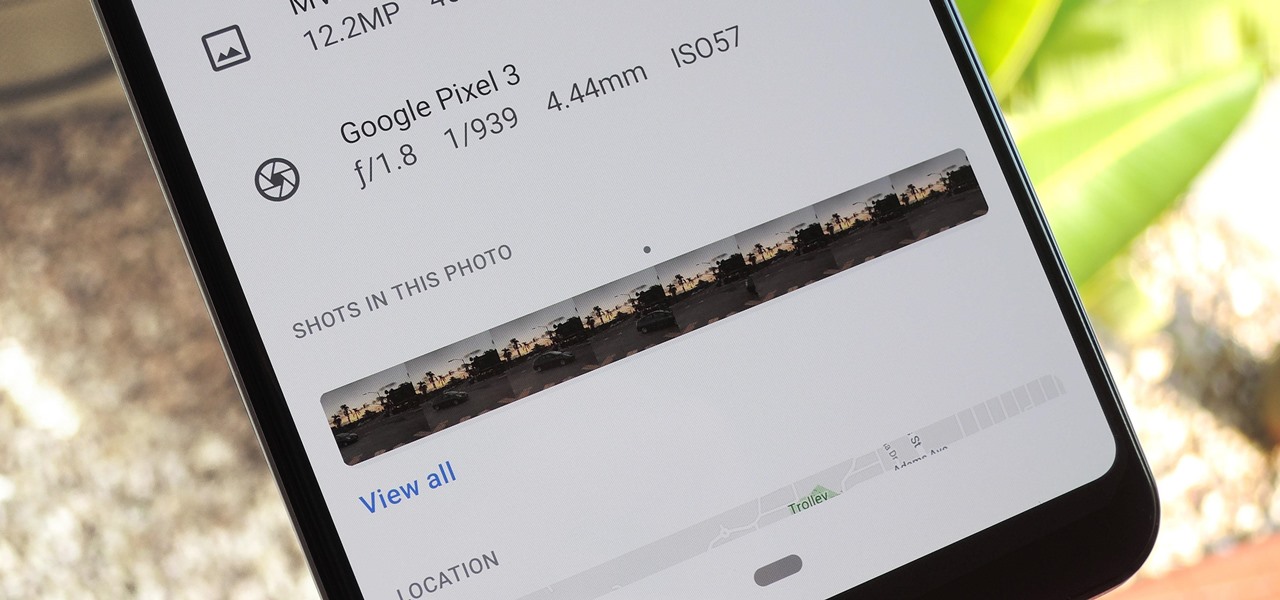
The Pixel 3 runs stock Android, so you might think that since you've used an Android device before, you should know your way around the new phone by default. But Google has actually added several great Pixel-exclusive software features to its flagships, and not all of them are easily discoverable.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

While Apple Maps didn't receive as huge of an update on iOS 17 as other apps such as Safari, Camera, Photos, Notes, Weather, and Messages, there are still some very important new features and changes you need to know about.

The screenshot tool on your iPhone can come in handy in various ways, but it may be even more helpful than you realize. So if you thought you knew everything there was to know about your iPhone's screenshot tool, it's time to put your knowledge to the test.

You may not realize it, but most of your apps include third-party tracking services that monitor your activity in other apps and websites to serve highly-targeted ads to you. But now you can stop the creepy behavior on an iPhone and Android phone.

While there are many ways to see the exact battery life left on your iPhone, you can take all the work out of it by making your iPhone verbally tell you the current percentage every time you start or stop charging it. Best of all, this trick works whether you use wired or wireless chargers.

The close of the second quarter of 2021 brought about a flurry of merger and acquisition and financing activity in the augmented reality industry, headlined by the acquisition of Ubiquity6 and JigSpace's new multimillion-dollar funding round.

If there is one constant in currently available AR headsets, it's that, for a quality experience, they'll carry a high price tag. Price is one of the reasons these devices are mostly marketed towards enterprise customers for now.

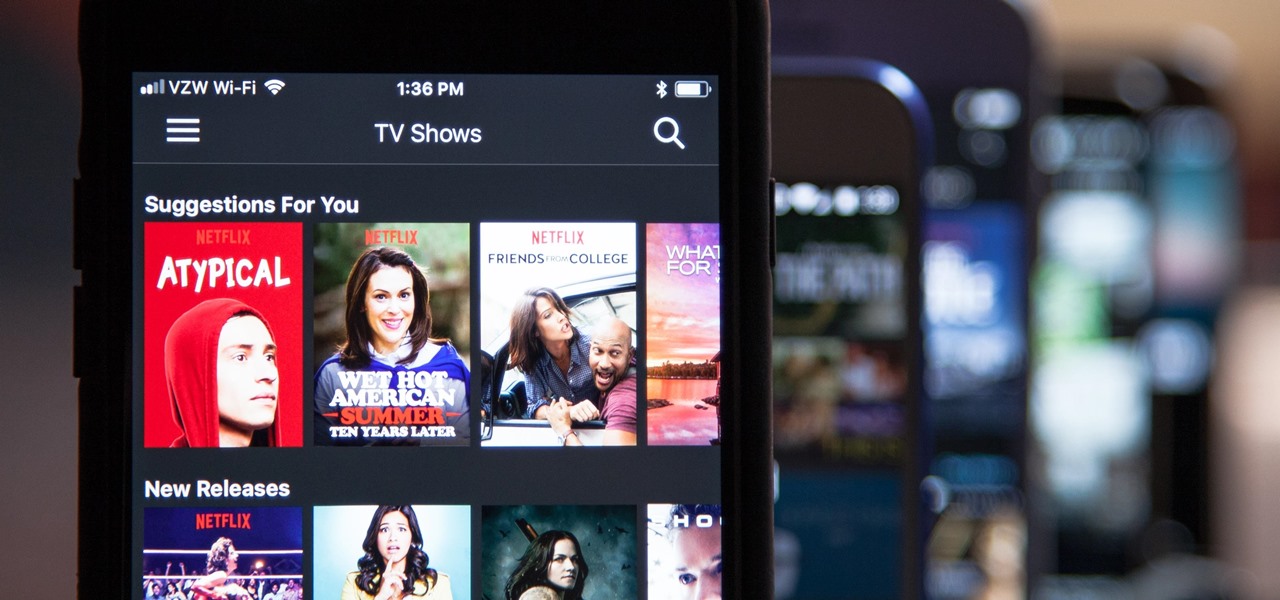
Who here binges TV on a regular basis? I know I do. Never before have we had so many options for watching our favorite shows, especially when you consider how easy it is to stream from anywhere on a mobile device. But sometimes, all that choice gets a little overwhelming. What services are really worth the money? Where should you be investing your Friday-night binges?

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

One of Android's biggest strengths is its flexibility. There's usually more than one way to perform the same task, which makes it easy to find an alternate method that works better for you. Android also has some hidden features that newer users might not be aware of, so we made this list to highlight lesser-known tips and tricks.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Apple designed Find My Friends in 2012 as a means for better-connecting with friends and family. It's pretty useful for scenarios when you need to keep tabs at an amusement park or to get a live ETA when your buddy is coming to pick you up from the airport. You can even share your location with others so they can track your whereabouts as you go about your day.

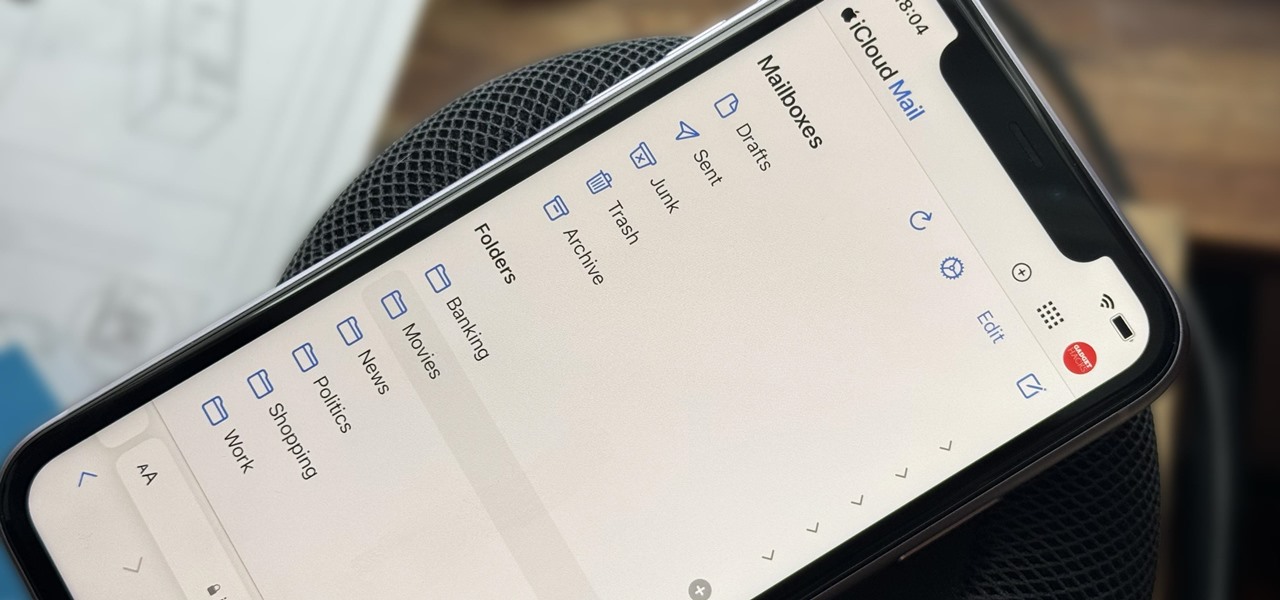
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

If you haven't been using Spotlight Search on your iPhone, we've got ten reasons for you to start. Apple's made some significant improvements to the search interface available on the Home Screen and Lock Screen, and it's more useful than ever.

Since iOS 13, your iPhone's come equipped with a fonts manager that lets you install custom fonts for use in Apple apps and supported third-party apps. To add fonts, you need to use a font provider app that'll load them on your device and register them system-wide, and one of these apps shines above all else.

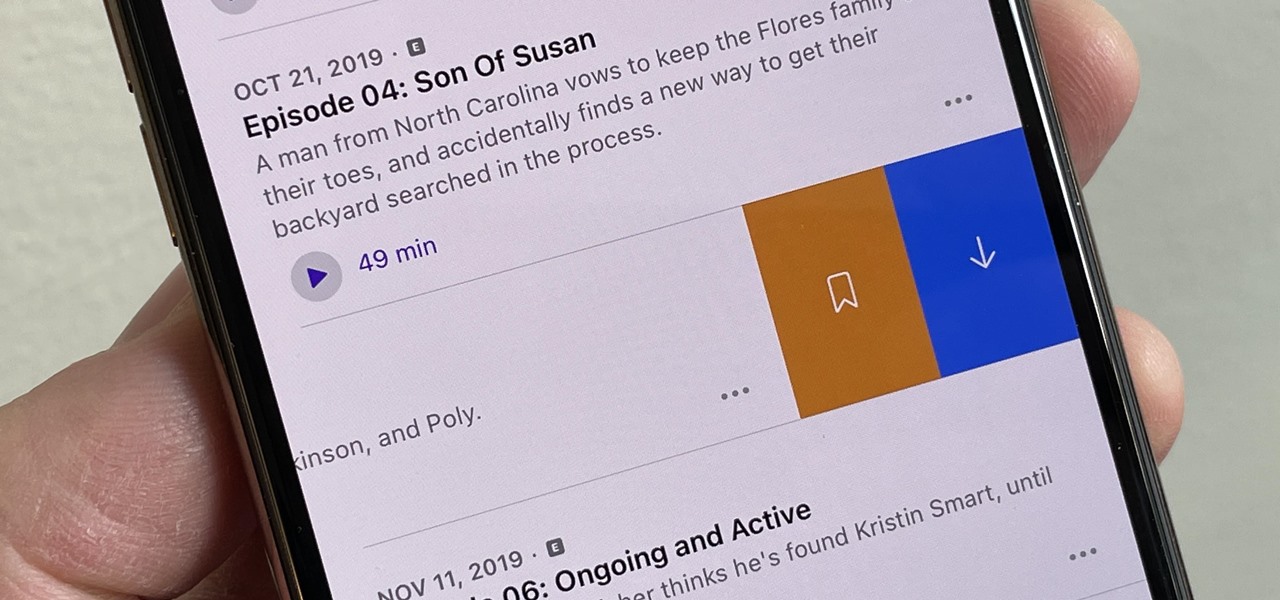
Spotify has caught up to Apple in monthly podcast listenership and is even forecast to surpass Apple soon, but Apple just made some serious changes to its Podcasts app for iOS and iPadOS that could keep Apple at the top.

The iPhone has a setting that will obfuscate the content of notifications on its lock screen until you're recognized by Face ID. Google implemented this same feature in its Pixel phones, but many Android devices have no such option. At least, not by default.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

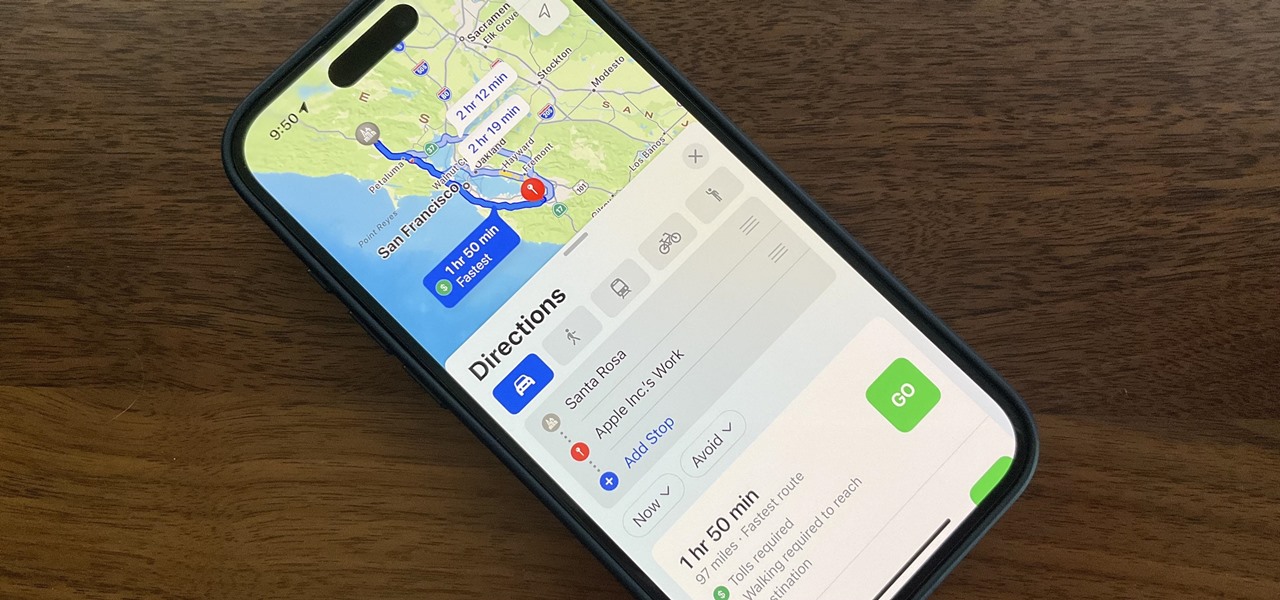
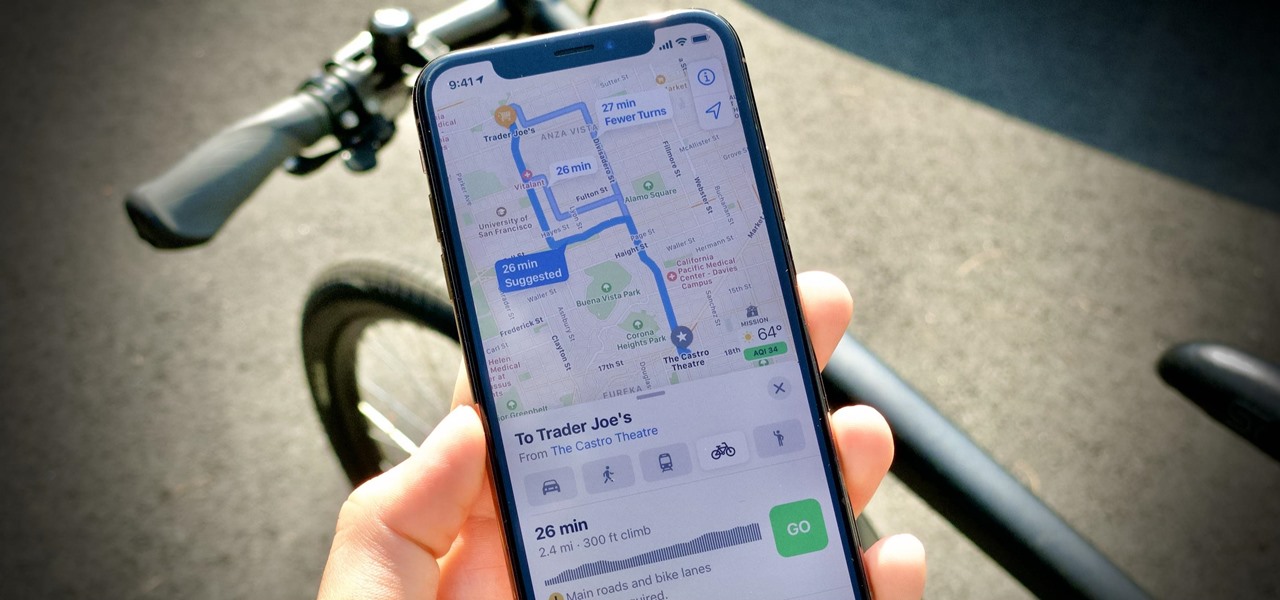
Once the laughing-stock of the navigation app market, Apple Maps is now a powerful, reliable travel companion. Apple rebuilt the platform from the ground up, placing the app in league with Google Maps. That said, there's always room for improvement, as demonstrated by its impressive new features set in iOS 14.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.