If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Duct tape is the king of all household items. You can use duct tape for practically anything, like this sweet wallet. But duct tape isn't the only crafty tape out there; masking tape holds its own, too.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.
On your mission to collect all 242 stars in Super Mario Galaxy 2 on the Nintendo Wii, this is your last World before moving on to the 120 green stars and bonus stars. World S is the key to get the rest!

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

In this video you will learn how to decorate your boy's room with lockers using cheap and fun ways. In order to do that you need to follow this steps and tips from the video: The first thing that you need to do is to get a large locker where you can deposit your kid's toys and athletic stuff. Another tip or step is to install timers to your kid's room. The timers will turn off the light and you won't have to worry because your electricity bill. This tips will help you organize your kid's room...

This video shows the viewer how to take part in a ‘scramble’ golf tournament. This type of event is typically for amateurs and is essentially played as a team sport, this is unusual for golf. The general principal is that everyone plays the first drive. The team then decides which drive was the best. They then move all the balls to this point and all play as if they hit that shot. They repeat the same procedure until one of the balls has been putted. This method allows amateurs to get a reaso...

It was only a few years ago when the idea of a 5+ inch display on a smartphone was unreal. With most hovering around four inches at the time, a phone that big seemed impossible to hold. We've come a long way since then, but it appears another wave of large displays will soon hit us, and they are all at least six inches.

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

I was mesmerized by the decoration in Rosalind’s. It has pictures of the Ethiopian people from tribes, the walls are painted bright yellow and covered with black nyala’s an endanger species found in Ethiopia, amazing hut roofs on top of the tables, Hi-Definition television playing a basketball game and neon lights that attracts the eyes. I felt like I was in a different country.

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device.

A major obstacle to the mainstream acceptance of smartglasses is the current inability able to smoosh processors, sensors, and batteries into a pair of frames that look cool. Wearables maker Thalmic is hinting that it may have figured it all out.

During the unveiling of its content partnership with the NBA, Magic Leap CEO Rony Abovitz, with an assist from former player/current pitchman Shaquille O'Neal, described at least one of the ways fans would be able to experience sports using the augmented reality device.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

If CES 2018 is the starting gate for this year's race to release smartglasses, then Vuzix is already racing down the augmented reality track with its Blade smartglasses.

Thanks to Metaverse, it has never been this easy to create your own AR game.

A few months ago, we gave you a small peek at a new entrant in the race to deliver augmented reality smartglasses to the masses, and now the device is finally ready for the public. ThirdEye Gen is now accepting preorders for its X1 Smart Glasses, which will also provide users with an AR-centric app store.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

How would you feel if the stethoscope used by your doctor to listen to your heart and lungs was teeming with potentially unfriendly bacteria?

Elon Musk's SpaceX is launching the world's most powerful rocket. The Tesla founder and CEO says the company is about to go through "manufacturing hell" to make delivery schedules for its new Tesla 3. Somehow, Musk says Tesla will offer Level 5 driving (so you can take a nap while your car drives you to and from work) within two years.

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

A 'superbug' fungus is currently running riot in the hospitals of New York and New Jersey. This outbreak of Candida auris has contributed to 17 deaths in NYC, according to recent reports.

It's no secret that Samsung had a lot of bad press this year. Despite this, we've reported how, even with the massive negativity in the media, Samsung has been expected to have an excellent Q1. Not only have those expectations been confirmed today, but Samsung has announced they are also working on a new flagship smartphone. One that some say could be the Note 8.

Having a Clostridium difficile infection means stomach pains, diarrhea, fever, and loss of appetite, and if the symptoms weren't bad enough, the disease often reoccurs. Now, new research has found an increased risk of recurrence in people who take medication to treat their stomach acid, gastroesophageal reflux disease, peptic ulcer disease, or stomach discomfort.

If anyone has every told you that they see music they listen to, they have synesthesia. It's a fascinating neurological phenomenon where people experience crossed responses to stimuli, and no one knows exactly how common this is. A rough estimate claims that one in every 5,000 to 100,000 people is a synesthete, but it could be far more common or rare. Nobody really knows.

For anyone who has spent an entire afternoon attempting to assemble a set of IKEA chairs, these wooden masterpieces probably seem pretty appealing.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

The future for the Meta 2 augmented reality headset will have to wait. While shipments were supposedly on their way out back in June, Meta revealed today that they need a bit more time to provide the best possible experience—and that's really for the best.

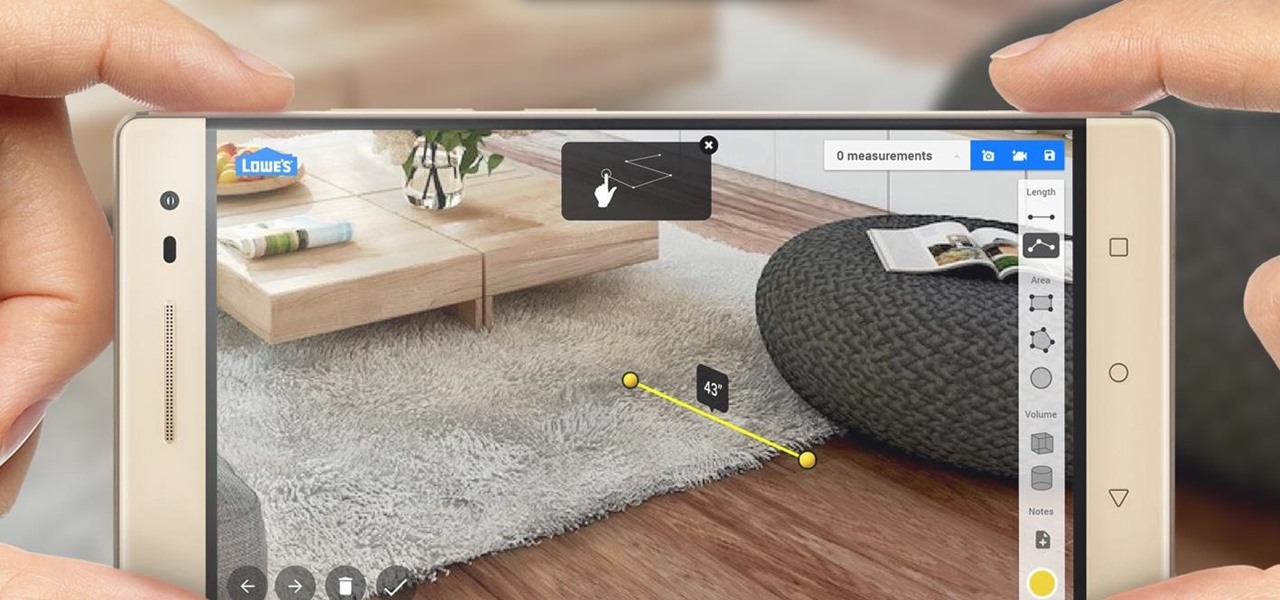
Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

A good chef's knife is a thing of beauty and, with proper care, a joy forever. It can totally change the way you cook and turn even the dullest prep work into a glee-filled task.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Freekeh is the next great supergrain that you might not have heard of yet. According to nutritionists, it comes out on top compared all to other grains, with more protein, fiber, vitamins, minerals, and a lower glycemic index.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Every morning I walk out the door with my headphones plugged in and music blaring. While it's not be the most difficult thing in the world, unlocking my phone and starting my music manually every time feels like a hassle. Pressing play on my headphone's remote will auto-start music in the HTC Music app, but I prefer Google Play Music instead.