For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Bill D., the tech lead at all3sports.com takes us through the steps involved in unpacking and assembling a brand new bicycle. The first he says is to set up or insert the seat post. He recommends using a work stand if you have one at home. He says not to unpack everything at the beginning, but to just expose the seat pack first. Use a wire-cutter to get rid of the film protection used for packing. He has mounted the frame-set on the work stand. The seat post goes into the frame-set. He asks t...

While any form of gambling is set up to make you lose, there are some tips and tricks, shown in this how-to video, to help even the playing field. Penny arcade slots are a reasonable place to start, as the stakes aren't too high, so neither side (you or the arcade) has that much to lose. Watch this video conning tutorial and learn how to beat an arcade penny slot machine.

Ah, the sand between your feet, the sun on your skin, and the debt you're accumulating. However strong my sense of wanderlust may be, I still can't justify dropping thousands of dollars on a vacation. Fortunately, a new site — Wander — promises to help you book vacations that match your budget.

In response to the flurry of doubtful headlines about Magic Leap today, set off by an unflattering article from The Information, Magic Leap CEO Rony Abovitz released a short blog post quickly detailing what to expect from the company over the next year. The gist comes down to this: big things are happening in 2017.

Learn how to spot a dishonest contractor for home repair. It’s no accident contractors have such a bad reputation – they get more fraud complaints than any other workers! Here’s how to find a reputable one – and skip the scammers.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

This series of videos focuses on a typical UV workflow in Houdini 9. Learn how to create projections, edit UVs with a variety of tools, save out UV maps, and apply textures. Please download the project files below to follow along with these Houdini 9 texturing lessons.

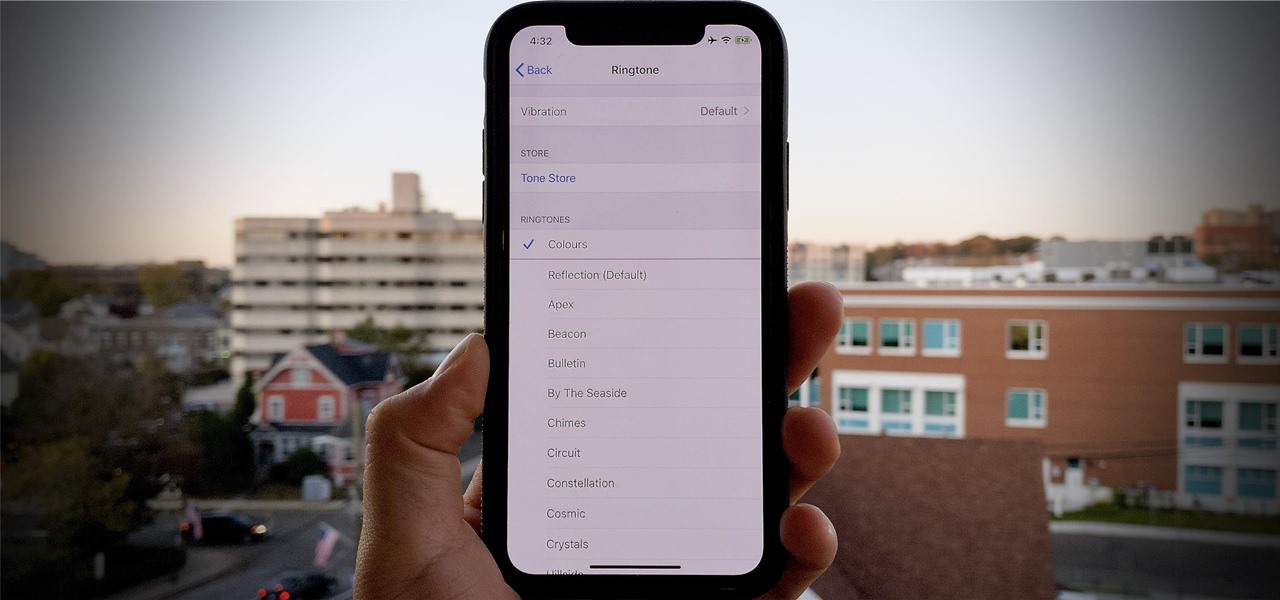
Have you ever heard someone else's iPhone ringing and thought it was yours? Of course you did. iPhone ringtones are iconic, but not varied. If you're using one of the more popular iOS sounds, you'll likely encounter it in the wild multiple times. Why bother, when you can create your own custom ringtones right on your Mac.

It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.

Apple's iOS 13 is nearly here. After four months of beta testing, the latest iPhone software update promises over 200 brand new features, like system-wide dark mode and an overhauled Reminders app. That said, it'll be shortlived, as Apple plans to release iOS 13.1 as a supplemental update just 11 days later. In fact, the company just seeded developers the fourth beta for iOS 13.1 today, Sept. 18.

It looks like Microsoft will finally make good on its promise to bring Minecraft to augmented reality, as foreshadowed via a HoloLens demo in 2015.

The Galaxy S10 is one of the best phones in years from world's largest smartphone OEM. With its astonishing display, new UI, and top-tier cameras, there isn't much to complain about. The one major gripe we've had is the in-display fingerprint scanner and just how slow it is. Thanks to a recent update, it just got a whole lot faster.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

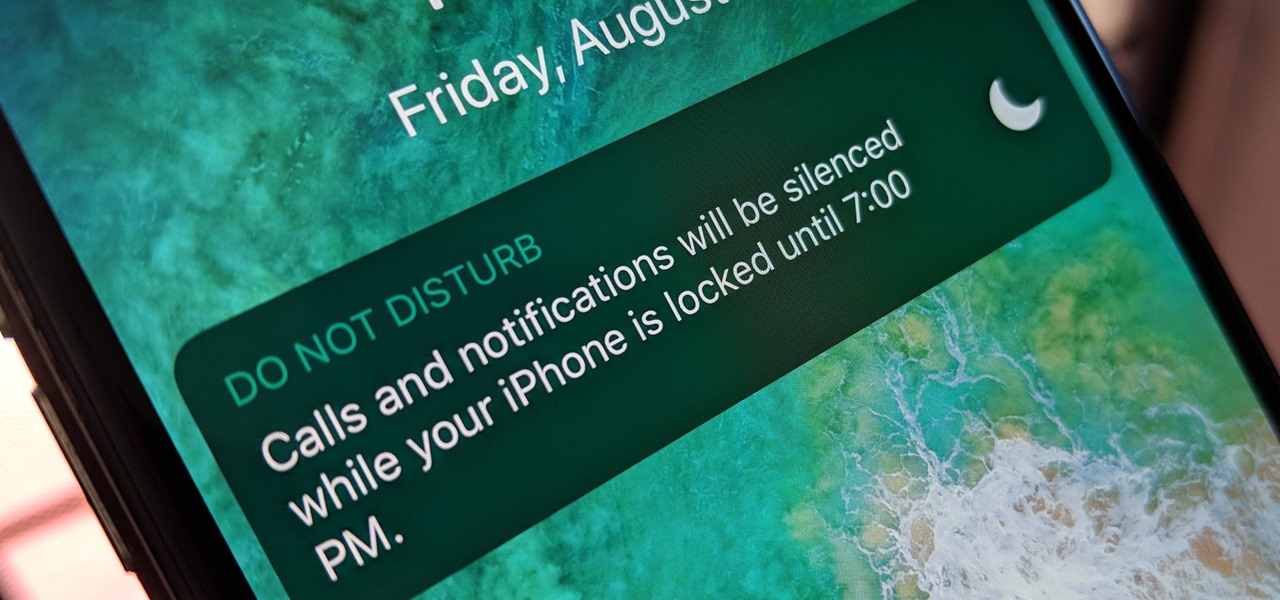
Included with iOS 12 is an easier-to-use Do Not Disturb mode. Not only is there a new Bedtime Mode that makes waking up less annoying, but also new ways to quickly launch the DND temporarily. One example is having the ability to set Do Not Disturb based on a time of day — specifically, morning or evening.

While Apple usually sets the precedent for its consumers to follow, the iPhone SE returned the company's iconic smartphone to a small form factor, one that had been ditched by the iPhone 6 and beyond. However, it appears Apple is finished with 4-inch phones for good, as the iPhone SE 2 looks to be even larger than last year's iPhone X.

In many ways, the Galaxy S9 is a holdout from the golden days of Android. It's one of the last major flagships to sport a headphone jack, it has an impressive array of internal sensors, and perhaps more importantly, it's got a micro SD card slot.

The Oreo beta updates for the S8 and Note 8 have been avilable for some time now. If you're interested in running Oreo on your Galaxy Note 8, you can check out our guide on how to do so. As we dig deeper into the updates, one question on the minds of Galaxy fans is whether or not the Oreo update will support Project Treble. Today, it appears we have an answer.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

A Brooklyn-based startup has launched a glasses-free holographic display for less than the cost of an iPhone 8 Plus.

Apple CEO Tim Cook's June 5 announcement that the company is developing autonomous software should have some companies rattled. At least, Morgan Stanley thinks Tesla should be.

If you're a tech enthusiast, there's no way you're not watching HBO's Silicon Valley. So you surely know the Pied Piper crew's latest shenanigans involve an app that uses a phone's camera to find facts about food items — a sort of Shazaam for food, if you may.

Uber's chance at driverless domination may be ripped away as its legal battle with Waymo escalates. The company's self-driving program is now under threat of closure if the allegations of premeditated theft are proven

Thanks to live-streaming video and social media apps like Facebook, Instagram, and Snapchat, we're all on camera nowadays. Unfortunately, though, we don't have a script to work with when we're shooting selfie videos, so it's hard to come off as perfectly eloquent when you're just freestyling off the top of your head.

Windows Insiders running Build 14971 of Windows 10 in the Fast Ring can now look for the "Windows Holographic First Run" app to check to see if their PCs are up to the task of running Windows Holographic. It won't detect your VR headset yet, but at least you'll be able to see if your computer will be compatible.

Autodesk offers some of the most popular software for computer-aided design (CAD) projects, which involve all sorts of 3D rendering. Their tools are clearly suited for use with the Microsoft HoloLens, but so far very little supports HoloLens development outside of Unity. Why is that?

Smartphones tend to struggle when it comes to recording video in low light situations. Danish phone manufacturer Lumigon included a good camera capable of shooting 4K video on its latest phone, The T3, but the real interest lies in the second camera, which is a dedicated night vision shooter.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Duct tape is the king of all household items. You can use duct tape for practically anything, like this sweet wallet. But duct tape isn't the only crafty tape out there; masking tape holds its own, too.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

Filmic Pro has a superb suite of professional settings — bit rate, frame rate, and mic choice, to name a few — which can enable you to capture the best footage possible. But different shots require different setups, and it can be frustrating to change settings on the fly. Filmic Pro lets you skip that whole process by saving your favorite settings as presets for quick and easy access.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.