
Ingredients 101: Heirloom vs. Hybrid Tomatoes… Ready, Fight!
If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.


If you've been to a farmer's market during tomato season, chances are you know that heirloom tomatoes are pricier (and funnier-looking) than their hybrid counterparts.

It's that time of year where you need to break out the grill and cook food over red-hot coals, whether it's the beginning, middle, or end of summer. Even if you're not a grill master extraordinaire, you can use these hacks to fool your friends and family into thinking that you're a barbecuing badass.

Brining is magic. All you have to do is make a mild saline solution, toss in your protein of choice, let it soak, and cook. You end up with incredibly tender, flavorful meat or tofu for very little effort. So why aren't more of us doing it?

Want to show all your foodie friends that you're really in the know? Then it's time to master the art of making edible dirt. Chefs out there are finding ways to take various foodstuffs and dry, char, and combine them to give the appearance of actual dirt—only with a rich, savory taste.

Many of the beauty products you buy at drug and department stores are loaded with potentially toxic ingredients like parabens, while their active ingredients are made of things like glycolic, lactic, malic, and alpha hydroxy acids and retinoids, which are all derived from foods.

Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

While most people were worried about having the scariest costume when I was younger, I was always more interested in the candy. While everyone wasted time trying to perfect their costume, I was busy mapping out every detail in my city, finding the most efficient way of getting the most candy in my pillowcase(s) before the night ended. Although I'm long retired from the game, it's about time to pass along all of the tips and tricks I've learned from my youth for getting treats. So, here I pres...

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

In this article, I will be showing you how to make a crude form of aspirin from the bark of a willow tree. It is a great remedy for headaches, hangovers, and other minor pain. The use of the willow tree as a mild pain reliever goes back to the Native Americans, who used it in much the same way that I do.

It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

When you need to subtly glance at the time or check your workout metrics without raising your wrist, the always-on display (AOD) on your Apple Watch comes in handy. However, Apple makes it seem impossible to disable it temporarily. You either choose to leave it on or off, with no clear way to shut it down for a while. It might not be obvious, but there is a shortcut that can do just that.
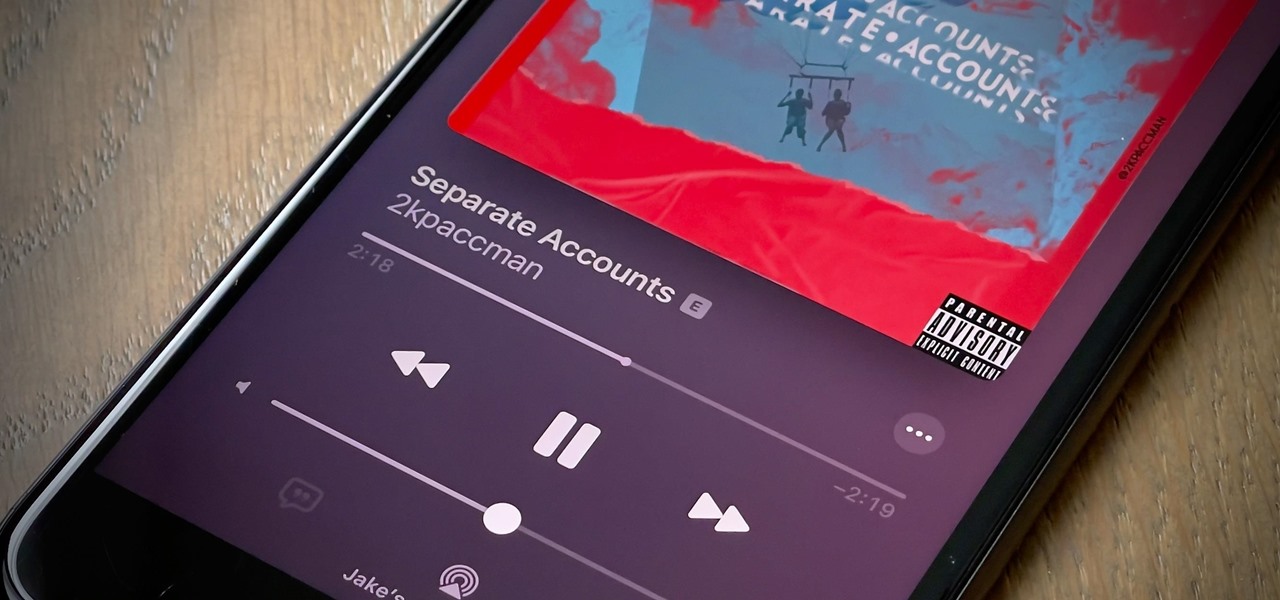
Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.

Since iOS 11, a thumbnail preview appears on your iPhone whenever you take a screenshot. It's useful for access to quick sharing options and editing tools, but you can't disable the preview image. You can wait for it to disappear or swipe it off-screen, but that's as good as it gets — until now. In an iOS 14 update, there's an option to disable the screenshot preview — only you won't find it in Settings.
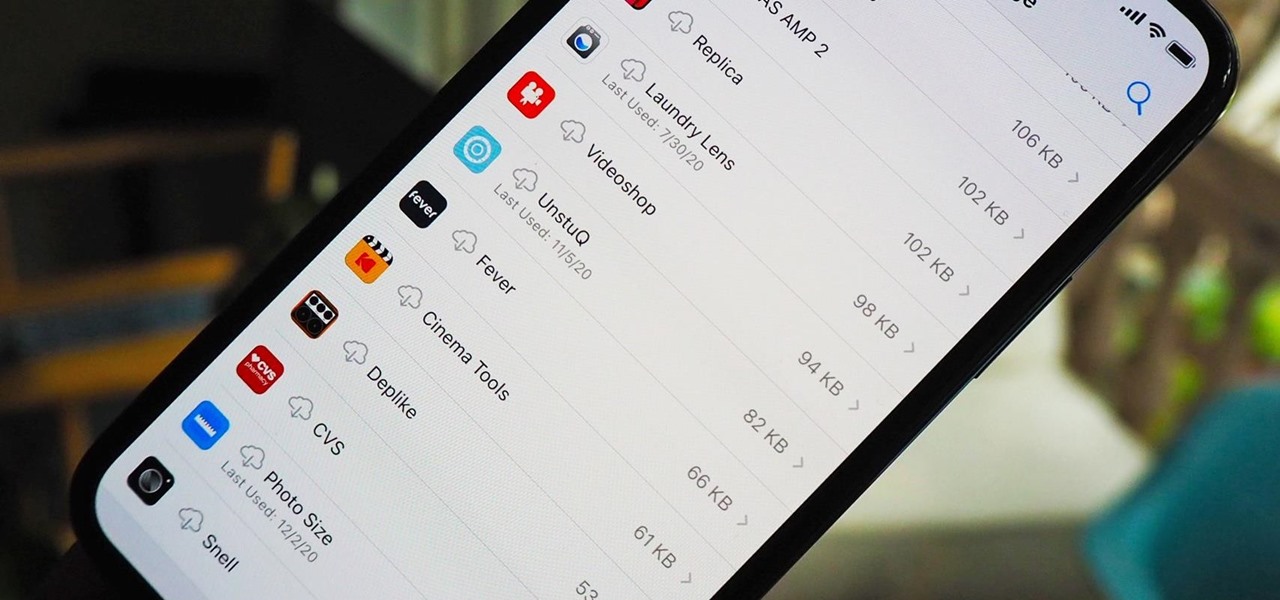
Since iOS 11, your iPhone has been capable of offloading hardly used apps to free up storage space for more useful data. But offloading only gets rid of the app's binary, meaning its documents and data are stored on your device in case you reinstall the app. That can take up a lot of space itself, so it's good to periodically review files for offloaded apps and purge the content you no longer need.

Videos hosted on Streamable may be fleeting or forever. So when you come across a cool video that you want to watch again later, it's a good idea to download it to your device in case it's one that disappears after a few months. There is no built-in download button in the Streamable player, but that doesn't mean you can't save anything on your iPhone.
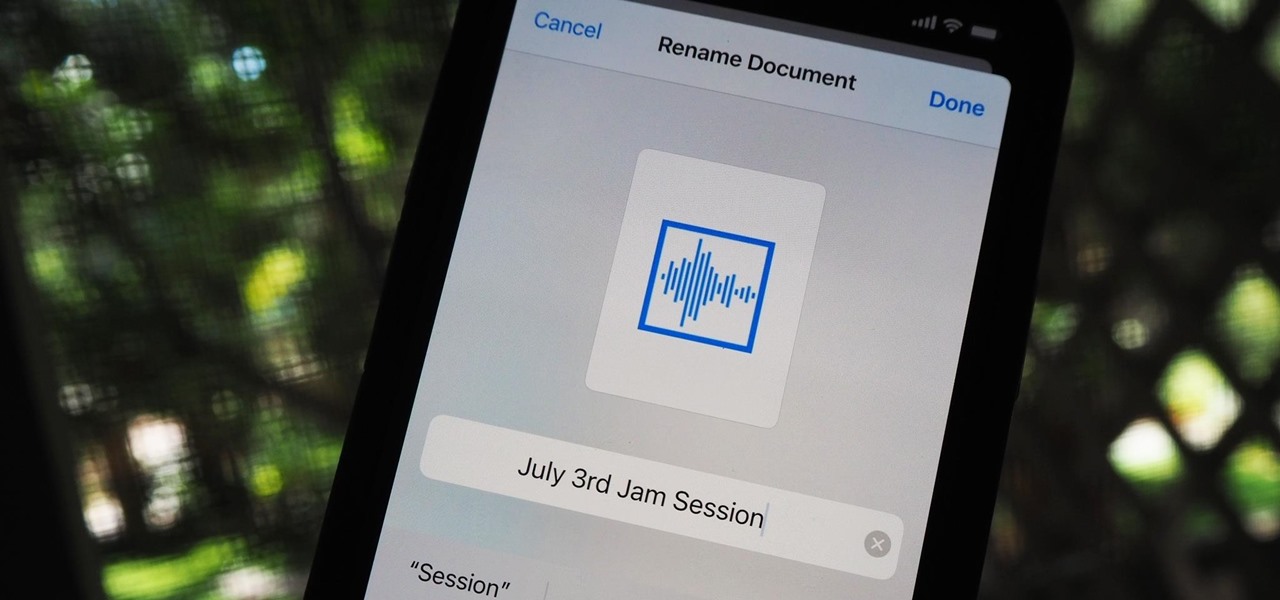
You can easily remove audio from videos in the Photos app on your iPhone, but the same cannot be said about removing video and just keeping the audio track. However, another stock Apple app can help extract the sound clip, and it barely takes any work to set it up.

At the beginning of every year, Samsung drops a fantastic phone in the Galaxy S series, and then tries to top it with the Galaxy Note series in August. This year, Samsung had their work cut out for them. But they managed to improve on their predecessor and properly challenge Apple's best.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

Smartphone technology has become as ubiquitous as automobiles. In Austin, Texas, a city that is widely known as the "Live Music Capital of the World," smartphones have been embraced by the music community not just as a way to document and promote, but to create music.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.