Okay, so that headline definitely got your attention, but what the hell do cats have to do with Android Nougat? Well, apparently, Google's on a far-out trip reminiscent of the post-India Beatles era, because this is actually a thing.

Many phones these days are being manufactured without a notification LED—it's a cost-cutting move, and it's really not an essential component. However, the notification light on Android devices has traditionally alerted users to any missed messages, and this is functionality you can't get without the proper hardware.
Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

Google's new cross-platform video chat app, Duo, is finally making its debut today, following a long waiting period that began in late May. The app was heavily teased during the keynote speech at Google I/O, but was not made available for download until now, so any early hype Google managed to whip up has died down quite a bit.

The new USB Type-C standard was supposed to revolutionize smartphone charging, but so far, it's done more harm than good. Many cable and charger manufacturers are struggling to keep their products in line with the proper USB-C specifications, so as a result, we now have to check to see if a cable is compliant before purchasing one.

No matter how far technology advances, battery life continues to be an issue. Powerful new hardware is introduced each year, but smartphone batteries only get a few extra milliamp-hours to compensate.

Collecting Pokémon in Pokémon GO is only half the fun. Once you've reached Level 5, it's time to get your Pokémon ready to do battle with other Pokémon. This is where Gyms come in.

Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little loophole in our brain to help us accept the unreal.

Samsung's latest flagship devices, the Galaxy S7 and S7 Edge, as well as the Note7, have a useful feature called "Always On Display." With this one enabled, the clock and some other information will continue to be shown on the screen, even when you lock your phone or turn your screen off.

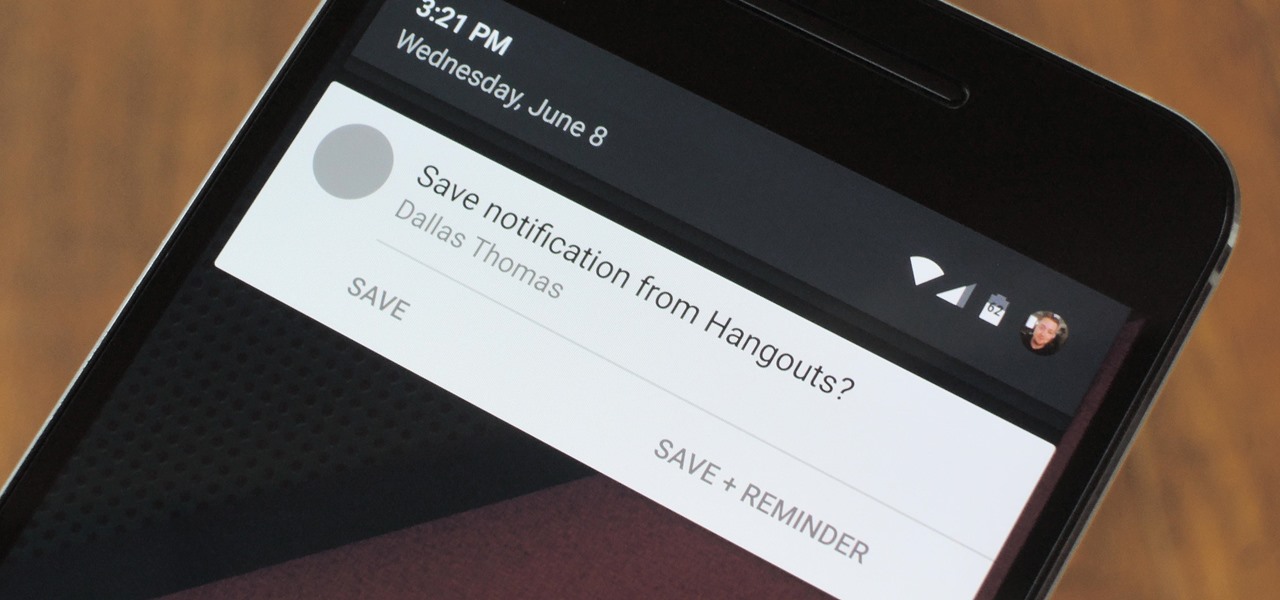
These days, there's almost an expectation that you have to deal with messages as soon as you get them. But that's not always the best way to handle things—sometimes, you're preoccupied with something, and it would be better if you could deal with a new message when you have a chance to give it your full attention.

Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

Automated bots are growing on Facebook Messenger, and while they can be helpful, they also have the potential to get very annoying, very quickly. That's because these bots are enabled by default to send you "sponsored messages," or, you know, spam.

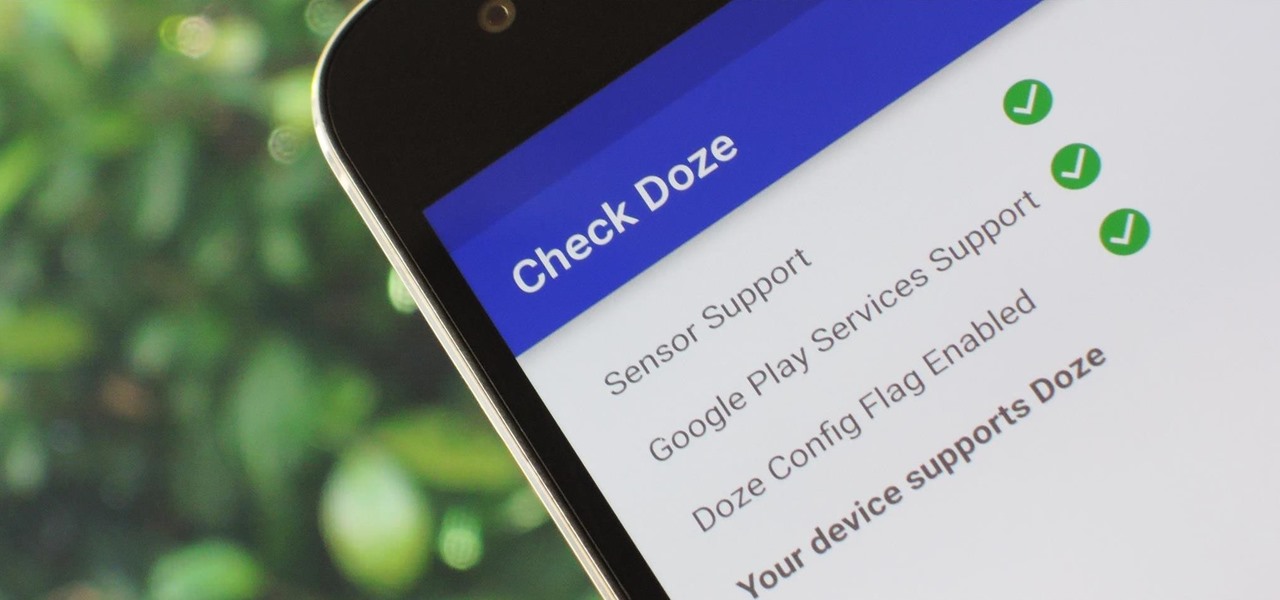
Out of all the new functionality introduced alongside Android 6.0 Marshmallow, a battery-saving feature called Doze Mode has been the biggest hit. Essentially, Doze waits until your device is laying flat and still, at which point it triggers an aggressive battery-saving mode that drastically increases standby time on your device.

When Apple wanted to bring their Notification Center to Mac OS X, I loved the idea. But after using it since its integration in Mountain Lion, it's been more annoying and distracting than anything. More and more apps incorporate notifications, so I'm constantly getting sound alerts and banners in the top right corner that I don't want.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

Samsung has been on a tear with its flagship devices since the release of the Galaxy S6; The S6 edge, the Note 5, and this year's Galaxy S7 models have all been met with universal acclaim, and even the staunchest of critics have almost nothing negative to say. Almost.

Android's flexible operating system allows for lots of customization, and one of the most common ways to add personal flair to your smartphone is to set your own ringtones and notification sounds.

It's about that time again. Spring weather is here, a new season of Game of Thrones is upon us, and we're getting ready for the next version of Android.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Android's personal assistant is more than just a sassy backtalker—it's a full-on suite of all the information you could need at a given time. Google Now, as it's called, uses data from various sources to predict what you'll want to know before you even search for it, and it's an amazing experience once you've got everything set up.

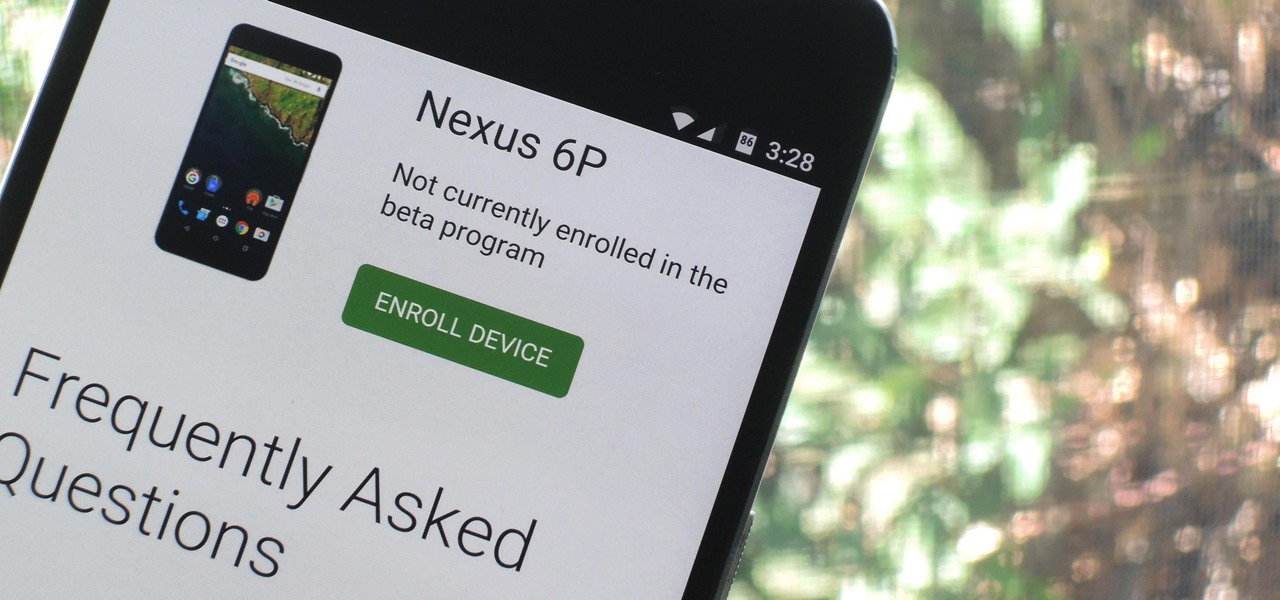
We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

A crick is a sudden, spasmodic pain and stiffness in the neck caused by tight muscles that can absolutely ruin your entire day. It can last for more than one day and can be triggered by the smallest movement of the neck, such as a simple pandiculation, aka a yawn-stretch. Although you can't always prevent them, there are many natural ways to lessen a painful stiff feeling in the neck.

If you've ever prematurely dismissed all of your push notifications before you got a chance to read each one, you know how annoying it can be to dig through all of your apps to try and find the one with the missed notification.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

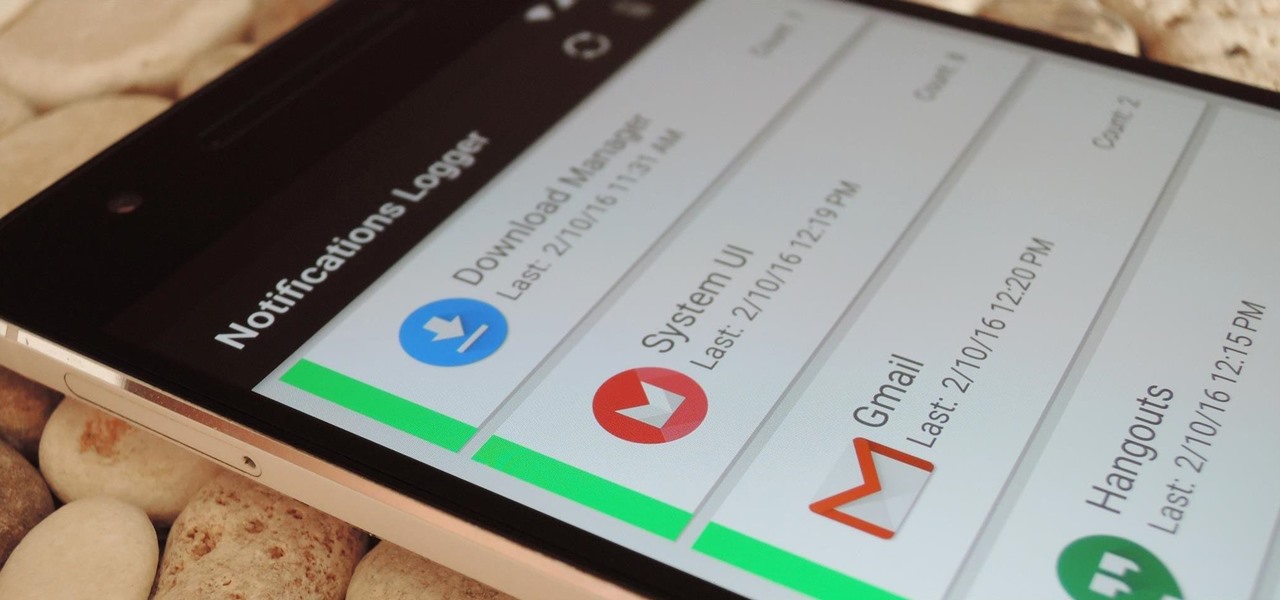
Many users across the web have reported issues with receiving notifications from the Gmail and Hangouts apps on Android. The problem is most prevalent with users running Marshmallow, and the gist is that notifications from these apps are extremely delayed or don't come through at all.

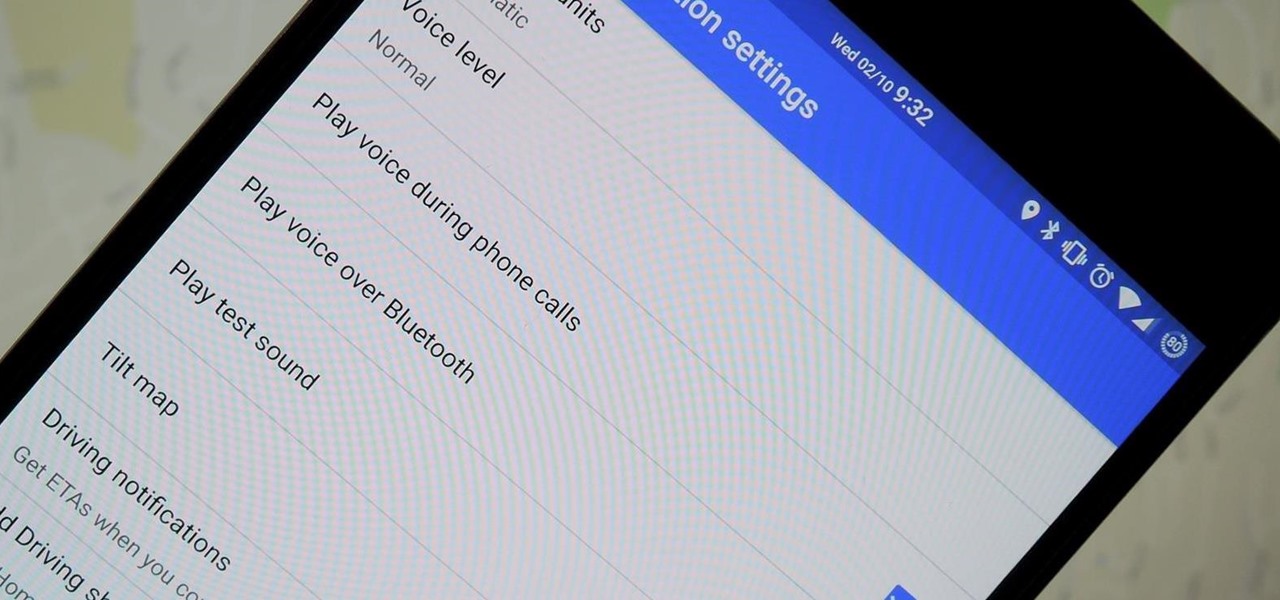
We've all been there. You're driving along with Google Maps pointing the way when you get a call from your friend asking you how much longer it'll be until you show up. You try to offer some lame excuse about how something came up last-minute, but you're interrupted, quite rudely, by Maps's voice guidance. The voice butts in again, and again, and again, to the point that you consider having Maps navigate you to the nearest cliff so that you can drive off it.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

When roast chicken is concerned, perfection is hard to attain. The reason for this is surprisingly simple: the light meat and the dark meat should be cooked to different temperatures. Ideally, chicken legs should be cooked to at least 170°F, while breasts should be cooked to 150°F. Naturally, this poses a conundrum: how can you cook two parts of the chicken to two different temperatures, without taking the bird apart?

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

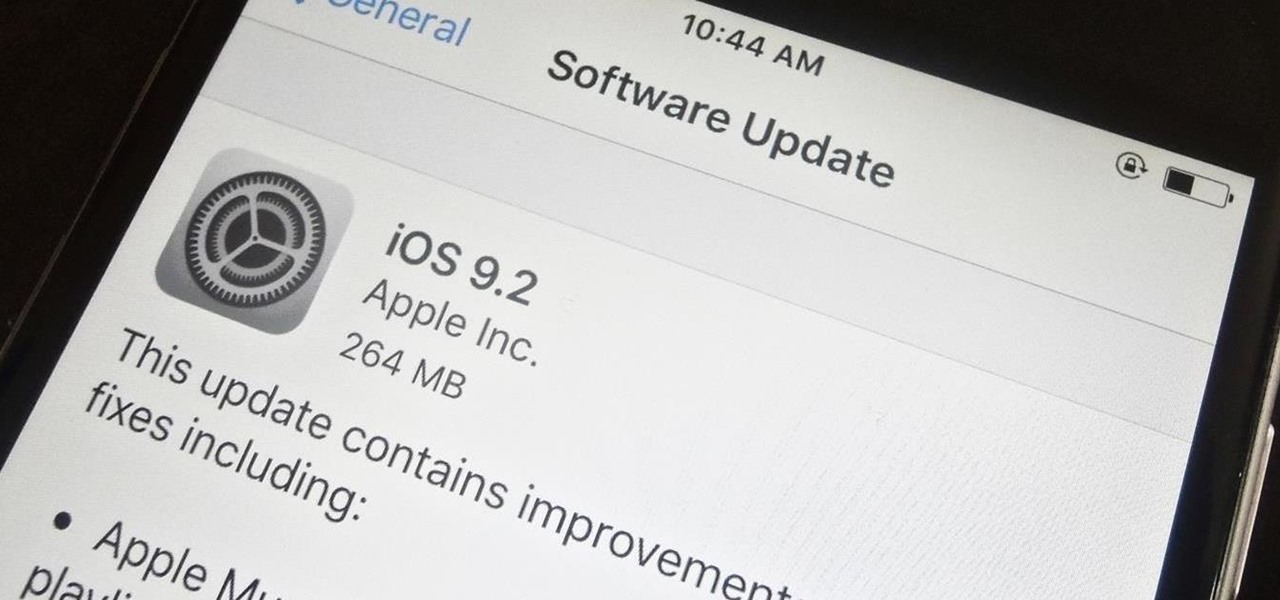
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

In the tech world, it's all too common to slap a fake label and packaging on a lower quality product, especially SD cards. If you've ever bought an SD card on the cheap from a slightly-less-than-reputable source (or even a reputable source, in some cases), how do you know if it's the real deal?

Hearthstone is a collectible card game by world-class developer Blizzard Entertainment. It has taken an entire generation of casual and professional gamers alike by storm. So many people play it, chances are you've already sunk some money into it. So, if you're going to pay a little anyway, you may as well get a discount.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.