Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

While the Apple Watch does have up to 18 hours of battery life each day on a full charge, your results will vary depending on how often you use it and what you're actually doing with it.

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and physical barriers to delineate their cultures.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

You send out a lot of emails, but probably get very few responses. How can you be sure those emails are even opened?

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Theming and modding are a big part of the softModder community, but there are endless ways to customize our Android devices. Which ones should you download? Which ones should you avoid? It's extremely frustrating to find them all—and pick and choose.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

The origami master can fold himself anything he may need. This demonstrational origami video will show you how you can even fold your own origami pants. (Disclaimer: WonderHowTo is not responsible for any papercuts received while wearing origami pants.)

Learn how to play "Human" by the Killers, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Remember those old vinyl records? Remember jumping on the 8-track bandwagon? Switching over to cassette tapes? How much money you spent converting your music collection to compact discs? To MP3s?

It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Elaine gave Whatley.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Despite the cancellation of Mobile World Congress and several high-profile companies pulling out of the upcoming Game Developers Conference, Magic Leap is pushing forward with hosting its own developer conference.

As augmented reality continues its collision course with mainstream adoption, the technology will now have a role in one of the most anticipated boxing matches of the year.

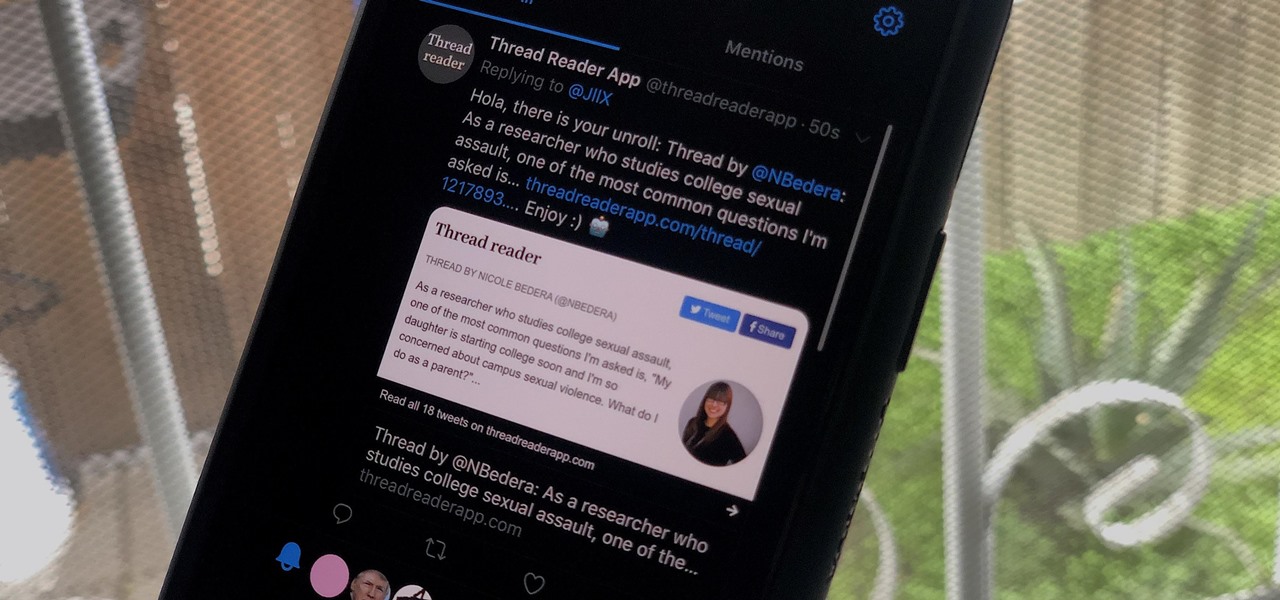
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

In older Android versions, you could flood your status bar with a wall of notification icons. But starting with Android 9, Google made it to where you can only see four icons by default, and it was mostly done to accommodate phones with notches. But Google's only notched phone is the Pixel 3 XL, so what if you have literally any other Pixel?

When Google introduced the Call Screen feature with the Pixel 3, I had never been more excited to get a Pixel device. This AI feature provided real protection against rising spam and robocalls, which billions of people deal with each year. After a recent update to the feature, you can reduce robocalls and other spam calls to nearly zero.

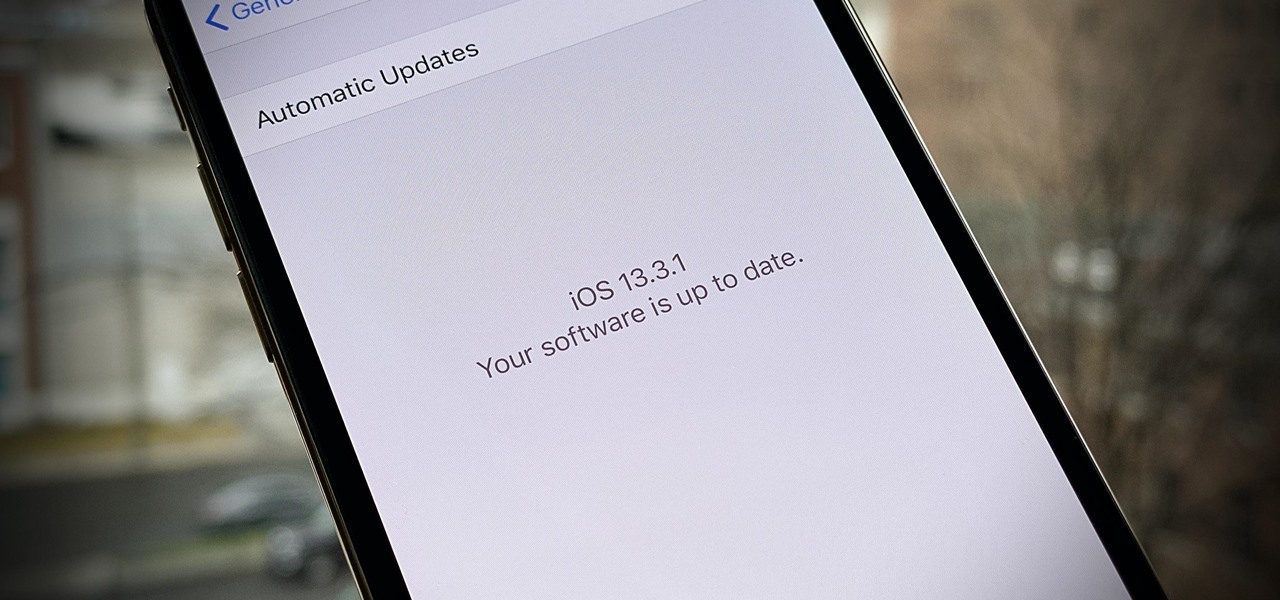
Did you take a vacation this holiday season? It appears Apple did. After the release of iOS 13.3.1 developer beta 1 (then public beta 1 one day later), iOS beta testing went silent for almost a full month. With 2019 now in the books, it seems Apple is back to work, as developers received iOS 13.3.1 beta 2 today, Tuesday, Jan. 14.

While Apple, Facebook, and Snapchat are still working on their first-generation AR wearables, startup North is already preparing to bring its second-generation smartglasses to the world in 2020.

It's no secret that iPhones are expensive. Whether or not you believe the price tag is justified, $1,000 is a lot to spend on an iPhone 11 Pro. But if you're in need of a new iPhone, you picked a great time. Black Friday is rapidly approaching, and for Walmart, many of those deals are already available.