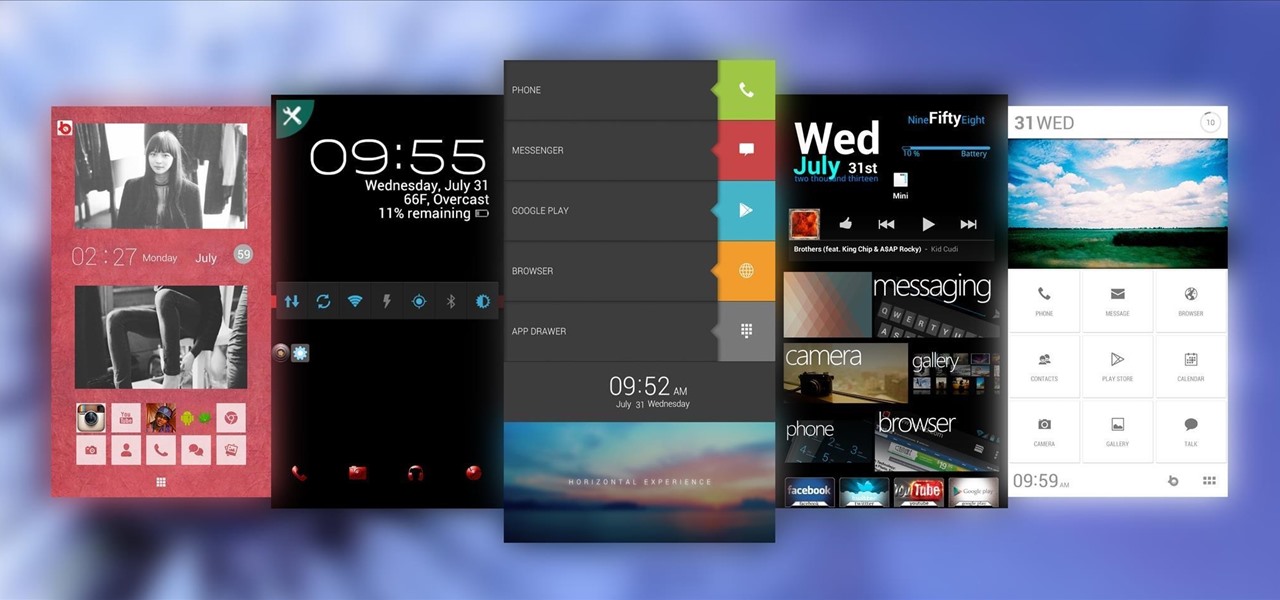
Customizing isn't all rooting and ROMs—there are plenty of ways to customize your Samsung Galaxy Note 2 or other Android device without gaining superuser access. One of the easiest ways is to install an Android launcher, sometimes called a home launcher, that matches your style.

One thing you can always count on from Google Play is a never-ending list of lousy launcher apps. Just search for "launchers" on the store and you'll see hundreds of apps hoping to replace the one you're already using. Problem is, none of them really stand out from the crowd. If you're not interested in a stock-look or iOS clone, you're out of luck.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

The biggest complaint I have with my Nexus 7 is the lack of support for different types of media files. I have a lot of movies and music that I've downloaded off the web, in many different formats, and I want them on my tablet.
Like most Android devices, the Nexus 7 suffers from its fair share of battery gripes. Nobody wants to see that dreaded "connect charger" warning pop up on their screen. NOBODY. Yet it probably happens to you every day nonetheless. What can you do about it besides charge, charge, and charge? Well, there's actually plenty that you can do. You can manage your notifications better, keep your screen brightness low, and kill apps running in the background. Or, you could just optimize your battery t...

Need to remove wrinkles from your shirt but don't want to bust out the iron and ironing board (or don't even have one)? Well, with a little bit of do-it-yourself ingenuity, you can "iron out" that wrinkly top in no time.

You (or your partner, or both) are a Steampunk. Let's get away from all the mindless, unfeeling commercialism for a few minutes and think about dates instead of gifts—where do you take your significant other for Valentine's Day? What would be the ultimate Steampunk Valentine's Day date?

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

Many social networks have become a part of our daily routine. Checking Facebook or sending out a Tweet are things millions of people do every single day. So, one would think that having a great app offering for Windows 8 would be a no-brainer. But, and this is a huge but, there are still no official Twitter or Facebook apps for Windows 8.

Once you have the skills to bring your ideas to life, the hardest part is coming up with ideas. What do you do when you can't think of something to make? What happens when your well of inspiration runs dry?

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

There's only three weeks left until the spookiest holiday of the year, which means stores and costume shops everywhere are bringing out their Halloween inventory full force. So now's a good time to start prepping your Halloween costume—because you really don't want to do it last-minute again, do you?

For those who don't know, LEGO recently came out with a new line called Monster Fighters. This set is about fighting monsters, sure, but it's about fighting classic monsters in a Steampunk universe. Just look at this promotional picture from the LEGO site: That LEGO dude (properly called a minifig) is wearing a vest, pocket watch, bowler hat, and a mean smirk. Not to mention that he has a robotic leg. You won't find the word "steampunk" anywhere in this marketing campaign, but I call Steampun...

There's nothing worse than holding an ice cold brewski on a hot summer day and having no way to open it. If you're a Bud fan, you'll have no problem opening the bottle because most mass-market beers have twist-off caps. But if you have a taste for finer, more expensive brews, you'll more than likely run into the pry-off caps. Pry-offs are used mainly because companies believe it provides a better seal against one of beer's greatest enemies—oxygen. Plus it's a cheaper alternative for craft bre...

If you have children, then you know firsthand how many crayons parents end up buying. There is no such thing as using a crayon until it disappears. Kids use crayons until they are a nub, and then they toss the crayon aside, never to use it again.

Here at WonderHowTo, we've been following the Minecraft LEGO set for quite some time, through its development on LEGO CUUSOO (a LEGO site where users can submit ideas for LEGO sets) to its eventual implementation.

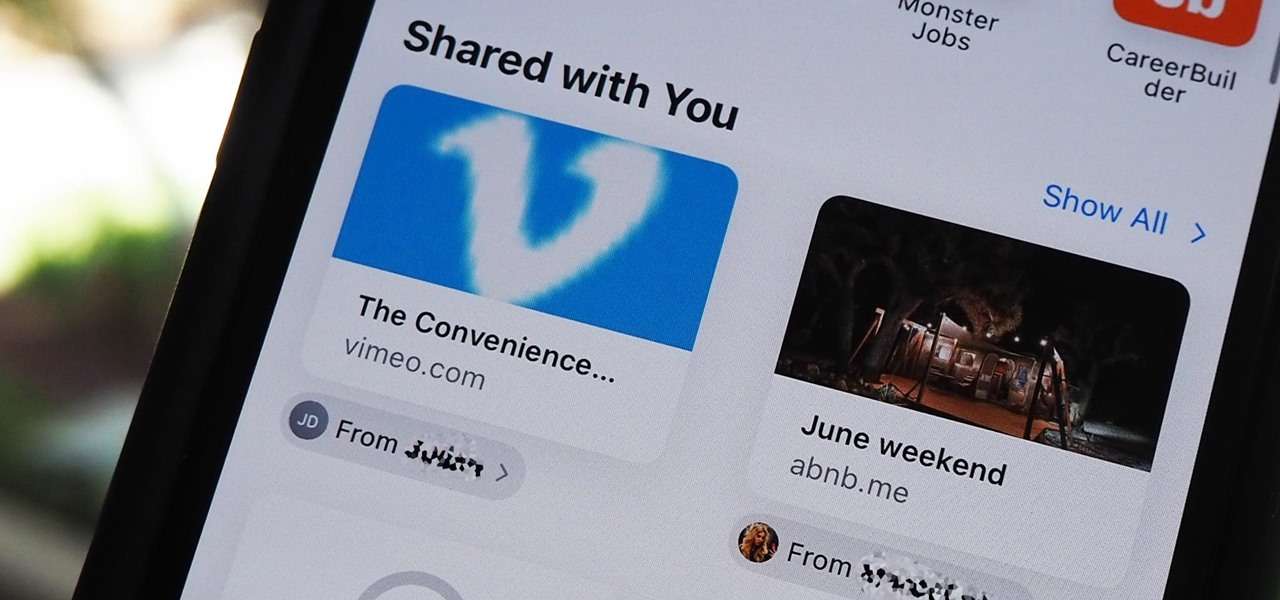
After updating to iOS 15 or iPadOS 15, you'll notice a new "Shared with You" section in certain Apple apps that contains recent shares from conversations in Messages. If you don't like seeing shared content from specific contacts or groups, there's a way to block them from Shared with You on your iPhone or iPad.

When smartphones were first getting popular, apps were much more limited in scope. Because of that, it was easier to find better programs to do what was needed. Now, in the App Store alone, there are nearly two million apps for you to choose from. When you're just looking for an app that will work well for the task at hand, two million is a lot to sort through.

These days, the only thing your eyes view more than your phone's home screen is the backside of your eyelids. So it goes without saying that whatever picture you have as your background gets old pretty fast.

Apps don't need to come bundled with an entire browser just to be able to display web pages — instead, they can call on the system WebView browser to render content for them. Android's default WebView renderer is Google software, which isn't quite as privacy-forward as some other options.

Most iPhones are more than capable of shooting crispy, high-quality video, perfect for any TikTok account to use. But if you're serious about the platform, especially in the long-run, you don't want just any iPhone. Instead, you'll want to pick up an iPhone 12 Pro or 12 Pro Max.

With bans looming or already happening across the world, TikTok still remains one of the most popular, entertaining, and addicting apps you can download right now. The problem is, browsing TikTok can be a bit painful at night since everything outside of the video feed uses a bright white theme. Thankfully, dark mode for TikTok is here, but there's a catch.

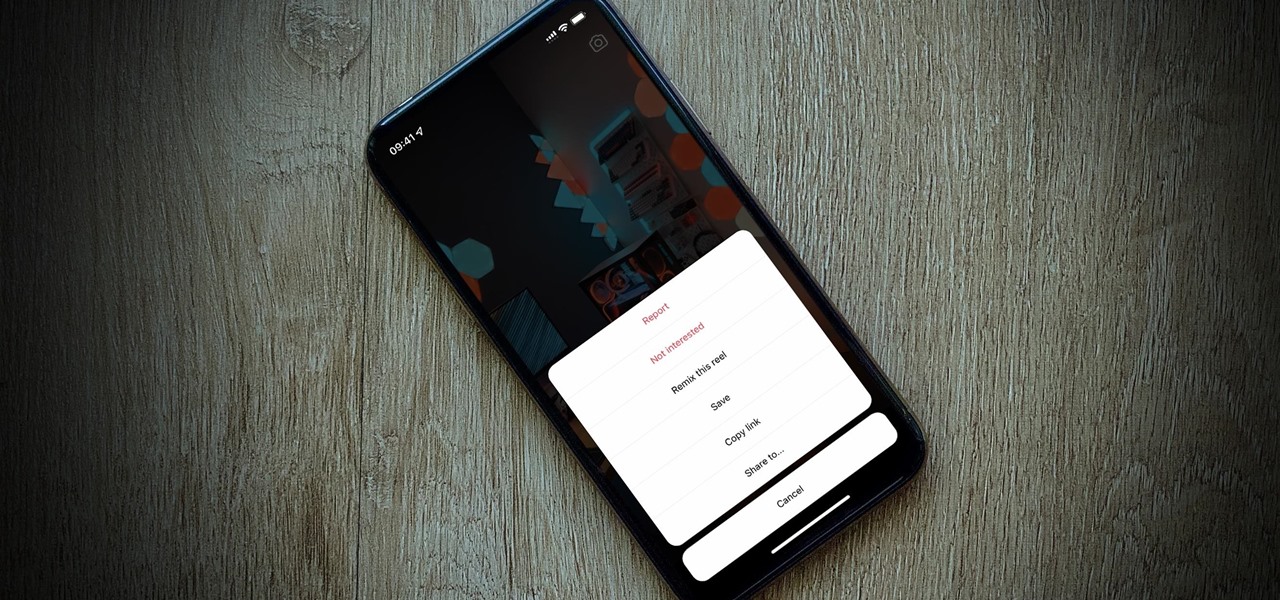
So, you're trying to show a friend or two a hilarious Reel you liked or saved on Instagram, but where is it? Unlike TikTok, Instagram doesn't make it clear where you're supposed to find your liked and saved Reels. Luckily, we can help.

Since its original release as a spreadsheet program called Multiplan in 1982, Microsoft Excel has become the world's premier business software. If you think that it's only good for spreadsheets, you haven't been paying enough attention.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

No matter how many camera improvements a phone adds, you're always better off using manual mode. Known as "Pro Mode" on the Galaxy S20, this feature can remove Samsung's pre- and post-processing from photos, putting you in total control.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

For those not used to it, working from home can be a difficult transition. Everything around you can be a distraction, and distance from your boss and coworkers means less pressure and incentive to get things done. So it's not surprising to see a major drop in productivity during a period of self-quarantine, but your phone can help you stay on track instead of sidetracking you.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.