Strange or uncomfortable encounters can be difficult to get away from sometimes if you're overly polite and don't want to hurt anybody's feelings. Thankfully, your iPhone can help save the day, providing you with a plausible excuse to exit the scene without having to conjure up some last-minute reason on the spot.
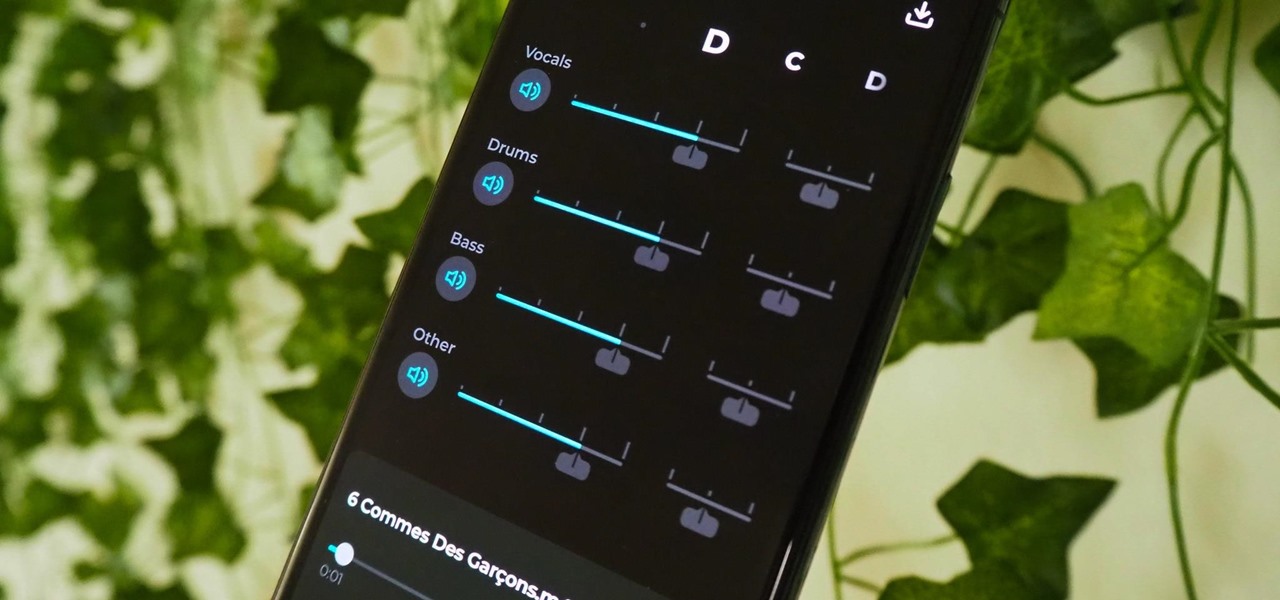
Adobe Audition, Audacity, and other audio editing software have tools to isolate vocals and instruments in regular songs so that you can get an instrumental track for karaoke, vocals for an a capella version, or solo drums, bass, keys, etc. that you can use to learn the song yourself. The software is mostly for desktop computers, and it doesn't always do a good job, but that's where Moises comes in.

For all of its many perks — from the best iPhone camera system money can buy, to arguably the best smartphone display on the market — the iPhone 12 Pro Max is undeniably huge. It has the largest iPhone screen to date despite being 0.46 cubic inches smaller than the iPhone 11 Pro Max in overall size. If you're finding it a little too much to handle with one hand, there are ways to make it much easier to use.

While Apple has been making strides in iPhone customization, it's still not up to par with what Android is and always has been. You can hide apps from the home screen now in iOS 14, but for everything that's still there, you can't add gaps between icons on the same page to segregate them where you want. However, some workarounds give that effect.
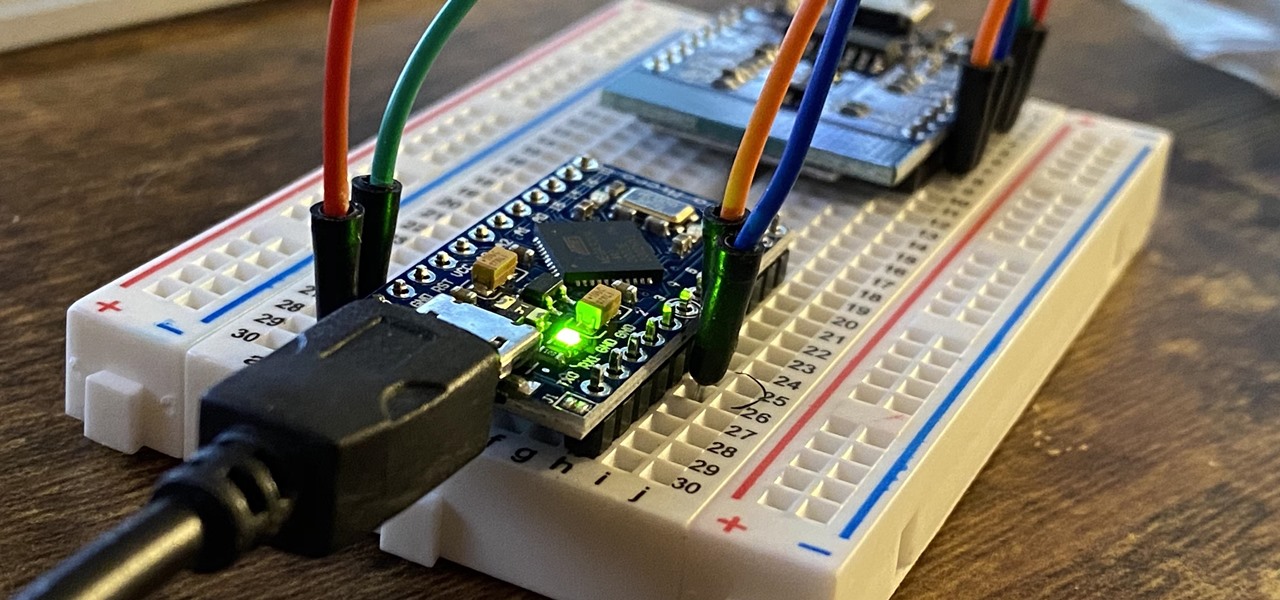
The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if you don't know what the target computer is, you might come up empty. That's where the WiFi Duck comes in handy.

Whether you have or are getting an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, the default way to check the current battery life is via the tiny battery icon in the top right of the status bar. But that does not accurately depict how much juice is left, not as a specific percentage indicator would. If you want the exact number, there are some not-so-obvious ways to find it.

The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max all have positive coverage surrounding their refreshed design, camera upgrades, and 5G connectivity. One piece of negative press you might've seen, however, is about the charger. Specifically, that there's a Lightning to USB-C cable in the box but no power adapter. That means you'll need a charger, and we've got some good recommendations for you.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

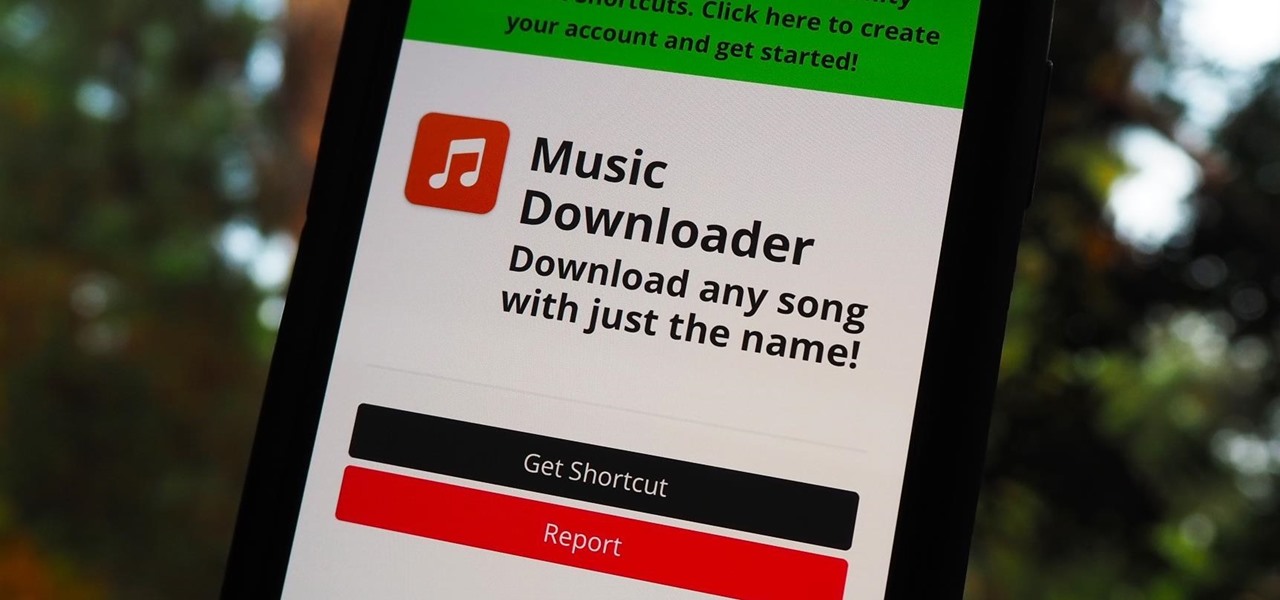
Music streaming services like Apple Music, Spotify, and YouTube Music make it easy to find and play your favorite artists and albums on your iPhone — but they cost upward of $14.99 per month. If you're more into listening to downloaded music, a shortcut can help you find free music online that you can get and playback in almost any media player of your choosing.

Nearly ten years since the first Galaxy Note and yet the Galaxy Note 20 still hasn't solved one of its biggest problems: bloatware. There are still over 20 redundant or unnecessary apps that are on this $1,000+ phone. But while it does require some advanced tools, it's still possible to remove them.

If you've ever been into custom ROMs, you likely know the Dirty Unicorns name pretty well. It's been synonymous with unique features and awesome tweaks when compared to stock. Recently, Dirty Unicorns has returned again in a big way with some neat features for Android 10.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

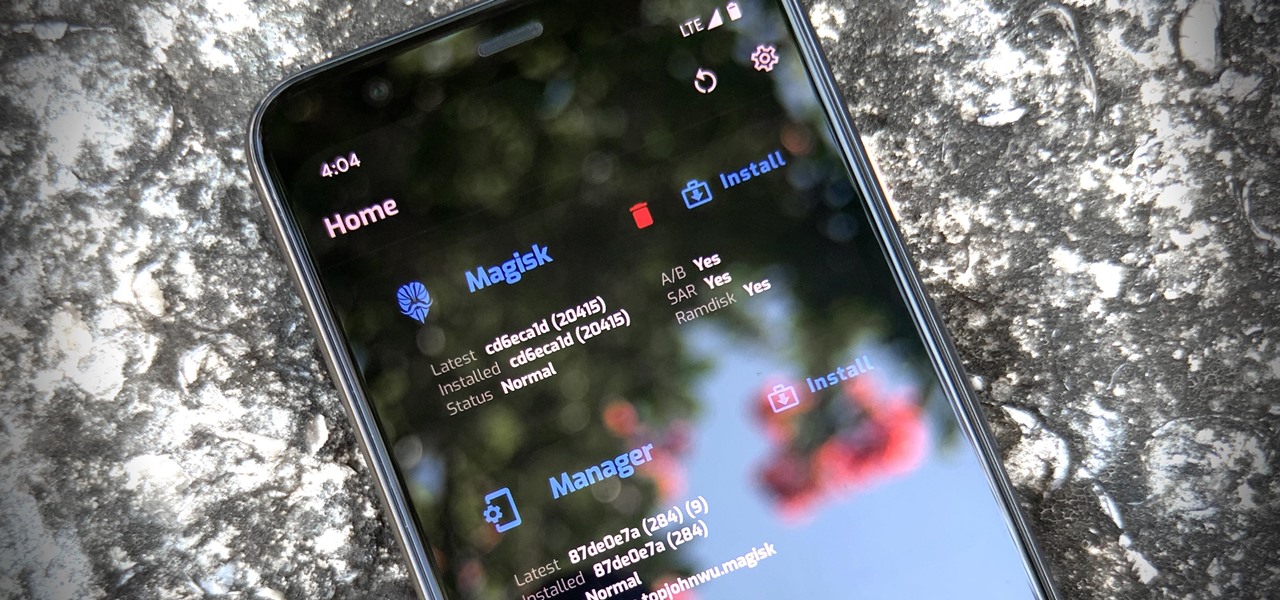
Thanks to Magisk, you don't have to lose root when updating to Android 11. The popular systemless rooting tool already achieved superuser access on Google's latest OS, even before the official release. It's currently in its experimental stages so the process is trickier than usual, but it does work.

The future of TikTok in the U.S. is all but certain. Microsoft, Walmart, or Oracle could save the day by buying the company, TikTok may win its lawsuit, or China's new restrictions could halt everything — but all could fail. Just like Vine before it, TikTok could be on its way out, only for opposite reasons. But will it matter if TikTok gets banned in the States? With the competition heating up, likely not.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

Your iPhone and Mac can speak to each other in many ways, allowing you to start work on one device and seamlessly switch to the other, share clipboards between the two, and pick up phone calls and answer text messages on both. The compatibility is incredible, but there's even more you can do by incorporating third-party software into the mix.

If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI that shows you the signal strength of nearby devices.

Samsung's lineup of Galaxy Note devices for 2020 include the specs-behemoth Galaxy Note 20 Ultra and the slightly more cost-effective Galaxy Note 20. Excuse the pun, but there's a lot to unpack here in terms of unique features and hardware.

Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

We might not be able to hang out with friends in-person during a mandatory lockdown or self-quarantine, but we sure can in "Animal Crossing: New Horizons." Snapping pictures with the new NookPhone feels almost as personal as taking selfies in real life, so, naturally, we want those memories to live on our real phones as well. In pure Nintendo form, however, it's not easy.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

There's never been a better time for streaming movies and TV shows on the go. With so many services available, the only limitation to your enjoyment is your phone's accessories. Whether you're buying for yourself or someone else, here are some of the best gifts that improve the movie-watching experience on mobile.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

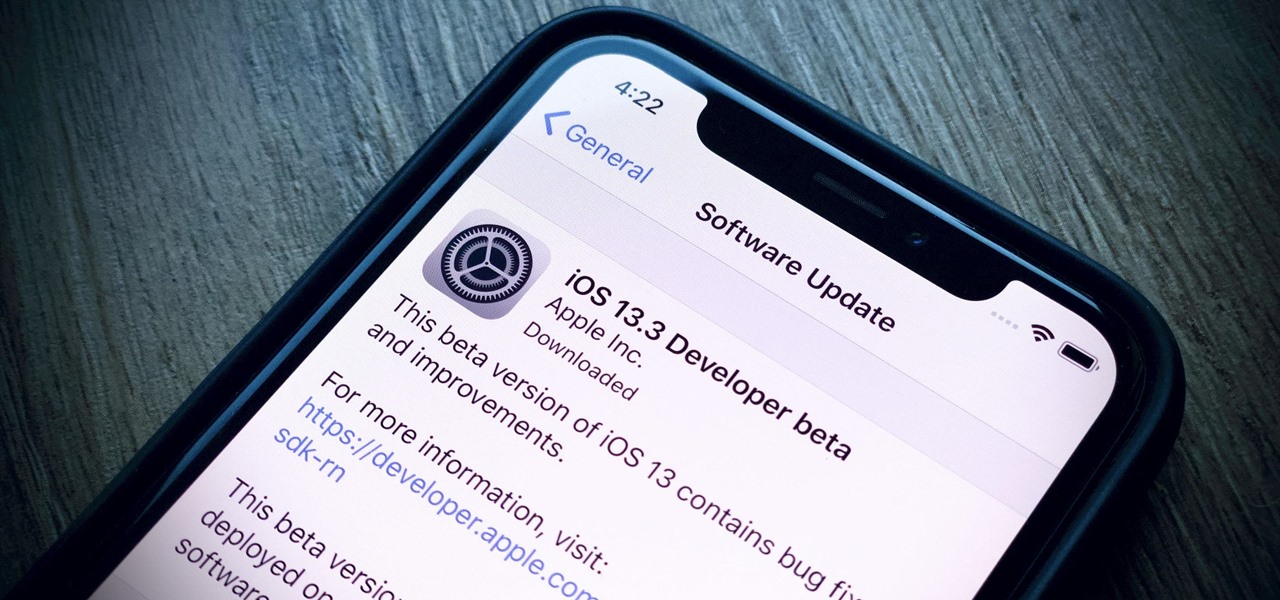
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Apple Watch owners know there's a built-in way to remove water from the device's speaker. However, even though modern iPhones are IP67 and IP68 water resistant, there's no official way to deal with water-clogged speakers that can muffle audio and cause prolonged damage if not ejected. Older iPhone models have it even worse, but there are some easy things you can do to get that water out.

With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

There's never been a better time for streaming videos on your phone. With so many options available (including a potential mobile-only Netflix tier) and so many new smartphones having large screens, there's a good chance you know someone who mainly use their phone for videos. And if you looking for a gift for them, there are some great options.

Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Have you ever seen those super-expensive universal remote controls like the Logitech Harmony and thought to yourself, "Man, I really want one of those, but that's just too much money"?