
How To: Tie a tie with the 'Nicky' knot
The "Nicky" is related to the "Pratt" and provides an excellent compact, medium sized symmetric knot. The "Nicky" is a very practical knot which can be used with most any tie.


The "Nicky" is related to the "Pratt" and provides an excellent compact, medium sized symmetric knot. The "Nicky" is a very practical knot which can be used with most any tie.

DIY Guide to building a birdhouse. This easy to make bird box can be built in 1 day out of one 6 foot long 1" by 6" plank of cedar. Attract more wild birds into your garden (or provide for those already there).

Watch this guide to the adductor muscles. This video provides professional advice on massaging techniques for the abdominal muscles. After some physical exercise, there's nothing better then a relaxing massage.

For the urban artist, this video shows how to leave your own personal touch to whatever you desire via a sticker. While there is no verbal instruction, the music is relaxing and the text messages provide clear directions. Get out there and make your mark!

Franklin Crow teaches you about edge bevelling. Depending on the terrain where you snowboard, you want to bevel your edges to provide the best riding experience.

Using an egg yarn dispenser provides more consistent results, is quicker, and results in less material waste than tying egg patterns without a dispenser. You can use a drinking straw, the empty shaft of a ball-point pen.

The half blood knot with a tuck is similar to the improved clinch knot. The half blood knot with a tuck is a multi purpose fishing knot. The half blood knot with a tuck provides one good method of securing fishing line to hooks, lures, or swivels.

The improved clinch knot (overhand knot variation) is as the other clinch knots a multi purpose fishing knot. The improved clinch knot provides one good method of securing fishing line to hooks, lures, or swivels.
Adobe Photoshop's Magic Eraser Tool provides you with a quick and easy way to change a pictures background or other color area with just a few clicks.

Home accidents. It's up to you to protect your family… your children… from accidents in the home. And there's one place that seems to get the most attention when dealing with safety concerns… The kitchen is one of the busiest, most accident-prone rooms in the house. Design a kitchen that will keep your family and guests safe.

A low tunnel is a kind of mini-greenhouse for your garden. Growing vegetables in a low tunnel requires proper ventilation. In this tutorial, you'll learn how to provide the right ventilation for your low tunnel, keeping your plants happy and healthy.

Puzzles include multiple pieces each with a designated pattern so that when a user regroups the pieces, a picture or a particular image is presented, which provides practice to the coordination of the user's concept to space and structural relationship between pieces. However, no matter how large the quantity of the pieces is, puzzles only provide user's spatial concept in two dimensions. To enhance spatial concept and increase entertainment to the user, building blocks are promoted so that u...
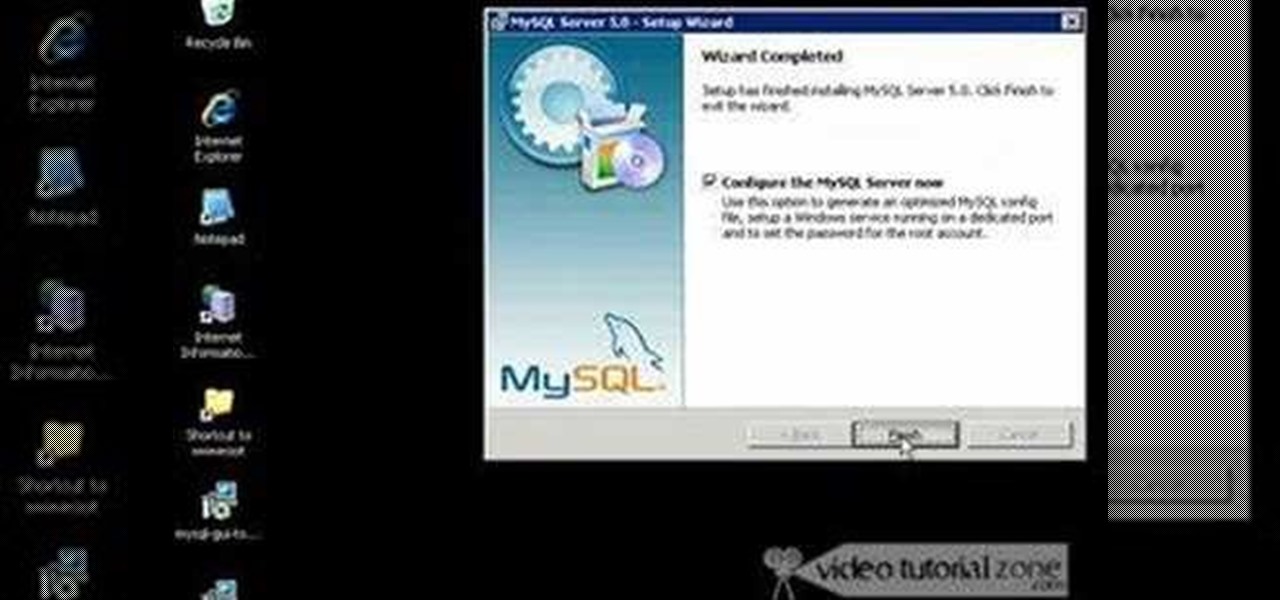
MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

Long gone are the days when you needed a fancy recording contract to write and distribute a smash hit. Thanks to a growing number of increasingly powerful and affordable music production platforms, it's now entirely possible to create pro-level audio tracks and even accompanying videos in the comfort of your own home with little more than a laptop and a pair of headphones.

Lossless quality isn't for everyone. If you can't distinguish between lossless audio and other formats, you probably but don't need it. But if you're a musician who's sharing ideas with bandmates or a journalist interviewing people for a video, you might want the best possible quality, which is what lossless offers. And you might not know it, but the Voice Memos app on your iPhone supports it.
After teasing the feature in Android 10, Google finally added proper native screen recording to Android 11. But when you start a capture, you'll see a small red indicator in your status bar as long as recording is ongoing, which can really distract from your video. Thankfully, it can be removed with a little ingenuity.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

If reaching up to access Camera controls like the flash, HDR, and timer wasn't bad enough, it's gotten a lot more tedious on recent iPhones like the X, XS, and 11 series thanks to their tall displays. If you have a jailbroken iPhone, however, you can easily fix this issue using a free tweak.

All those Apple commercials encouraging people to use their iPhones to make their smartphone movies look amazing, but how can you achieve some of the same looks? That's the question many often ask after plunking down over $1,000 for a brand new iPhone, shooting some video, and getting somewhat mediocre results.

There have been enough music artists releasing Snapchat AR experiences over the past week to fill a small festival. Count them with me: Bruno Mars. Gucci Mane. Kodak Black. Missy Elliot. Imagine Dragons. Panic! At the Disco.
XDA recently reported on a leaked version of the upcoming Pixel 4's camera app. By testing the app, they were able to find upcoming Pixel 4 features like a new Night Sight mode that can photograph stars. Well that leaked version has leaked itself, so now you can install it on your own Pixel phone.

The S Pen in the Galaxy Note 10 and 10+ has improved to make remote usage even easier. Controlling your phone with just the stylus is no longer a party trick, as you can now move around and take actions in both first-party and third-party apps. One of the best examples of this is the Camera app.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.
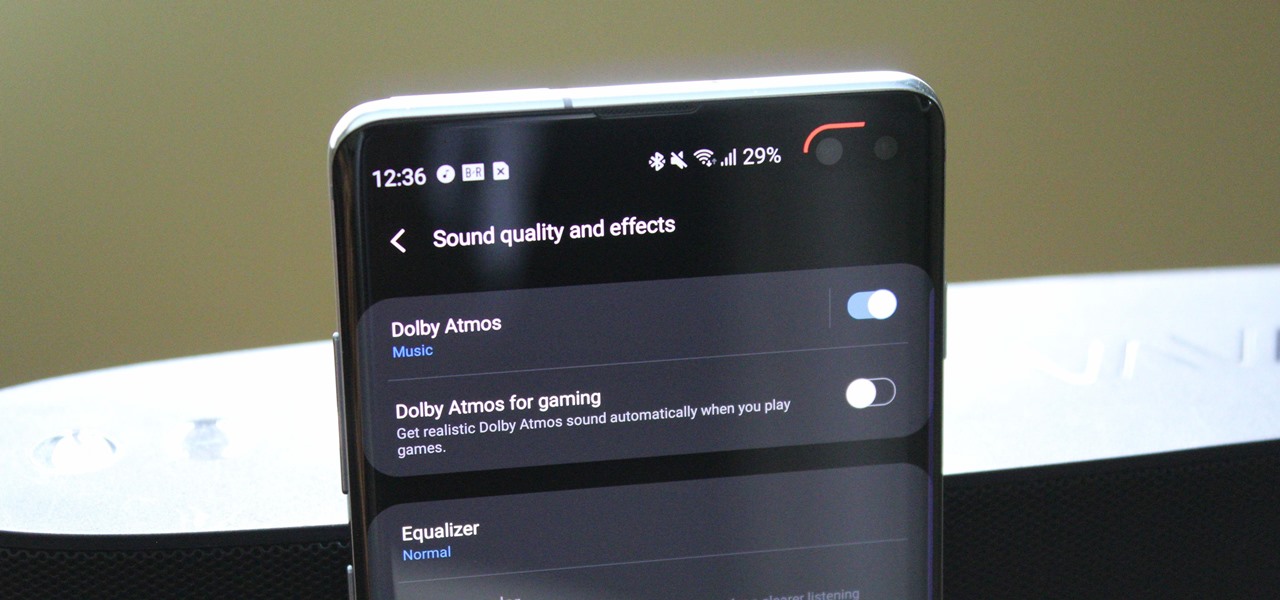
While the audio experience is solid on Galaxy phones, it isn't the absolute best out of the box. That's because Samsung has partnered with Dolby Laboratories to provide its industry-leading sound technology known as Dolby Atmos, but it's turned off by default. Once enabled, your audio experience will go from good to great.

The Music sticker is one of Instagram's best features. With it, you can add music directly to your story, incorporating a high-quality soundtrack to your favorite moments. On June 6, Instagram upped the ante on this feature, introducing live song lyrics that play throughout your story. Karaoke, anyone?

As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

Augmented reality developers who have exhausted their treasure trove of video tutorials and panels from the recent Magic Leap developer conference can now shift their continuing education attention to Unity.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

Data breaches are all too common now, and the latest one you need to know about involves Timehop, a mobile app that makes it easy to reminisce over old photos. The breach, which took place on July 4, was revealed on Sunday, July 8. At the time, Timehop disclosed that 21 million users had been affected by the breach, but it now appears that all users were impacted in some way.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

While Huawei smartphones haven't always been the best choice when it comes to custom ROMs, one thing that has always been accessible is the ability to unlock the bootloader. An unlocked bootloader is the first step into the magical world of rooting, but after May 24, Huawei will stop offering this service.
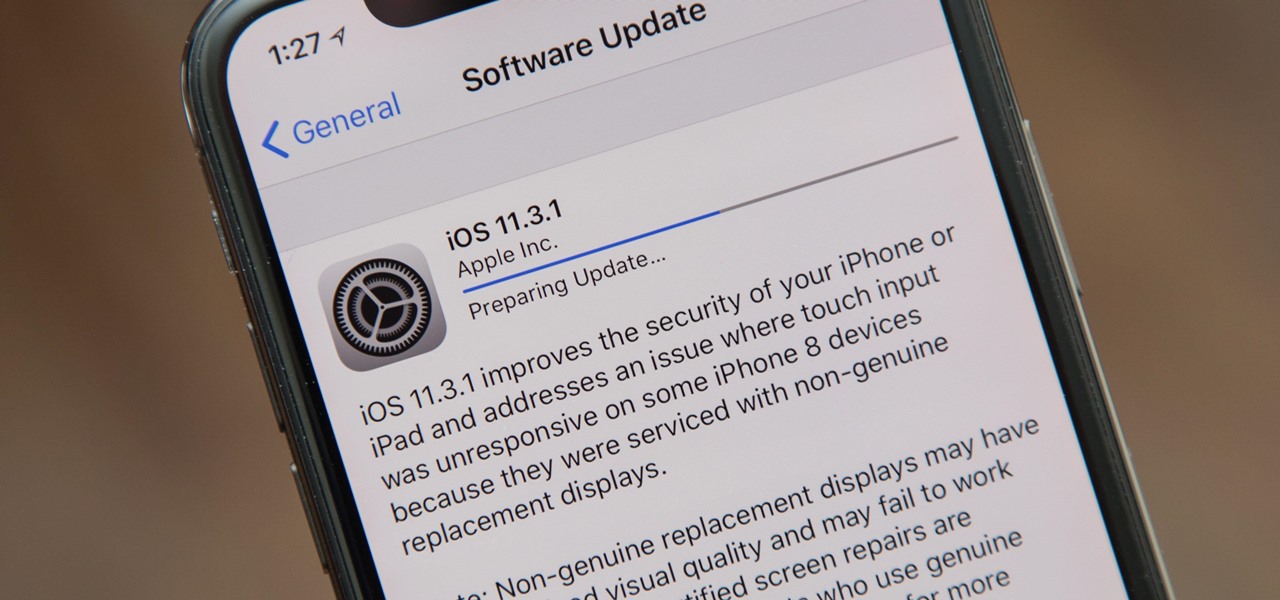
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.
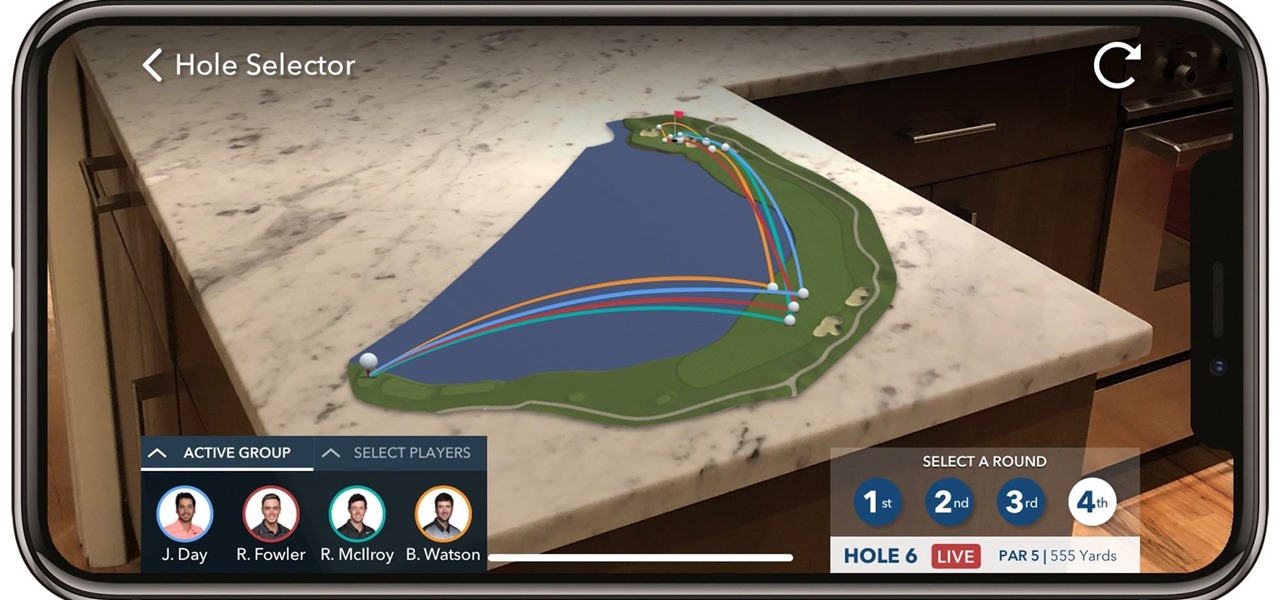
If you're a golf fan who can't attend the Arnold Palmer Invitational in person, you can still follow the next stop on the apparent Tiger Woods comeback tour in augmented reality with an iPhone or iPad.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

Now that the holiday season has officially kicked off, Office Depot has updated its popular Elf Yourself app with a few new augmented reality options.