Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Back in August, Google unveiled a new YouTube Gaming service meant to compete with e-sports streaming sites like Twitch. At its launch, the service was capable of broadcasting desktop PC gameplay, but when it came to the mobile segment, users were only capable of viewing streams hosted by others.

As mobile devices become more and more popular, service providers have unfortunately resorted to capping data. What this means is that, depending on the plan you have with your ISP, you could have limits placed on how much data you can use for a set period of time. Once you've hit the limit, your ISP could drastically slow down or throttle your internet speed or charge you outrageous overage fees.

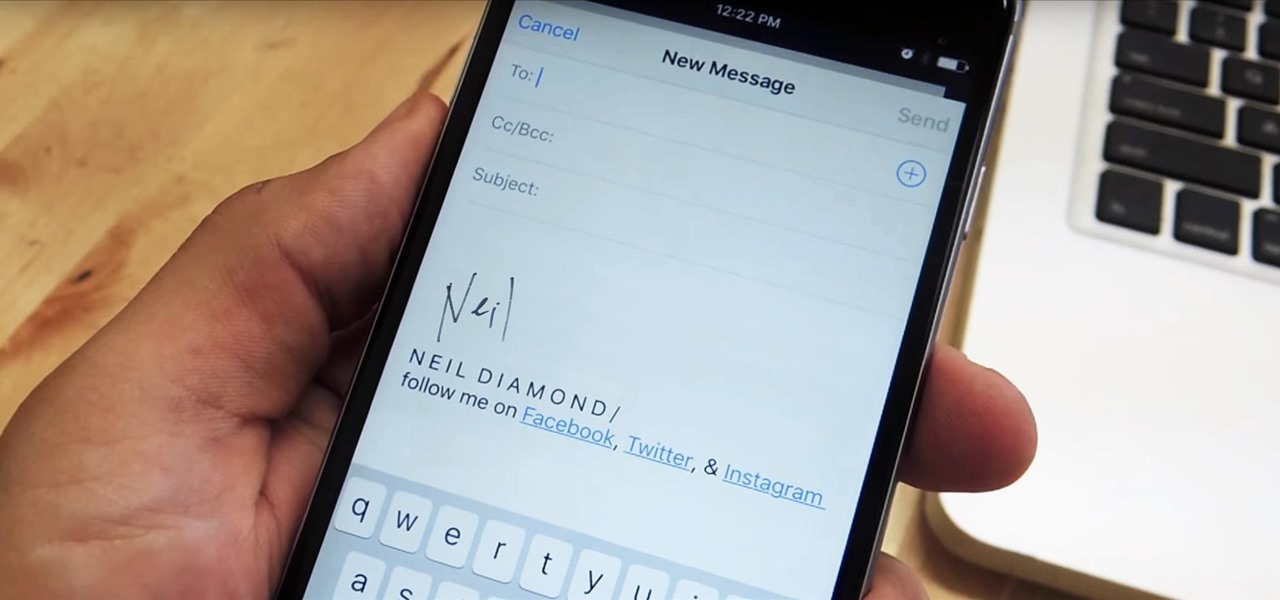
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. In these cases, using an app to find the best wallpapers out there can be just what you need.

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.

Make no bones about it—having an "undo" option is a freaking godsend. Whether you accidentally deleted an entire essay, screwed up the shading on a Photoshop job, or sent an email that wasn't quite ready, having the option to undo a click or button-press can definitely be a lifesaver.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little worlds.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

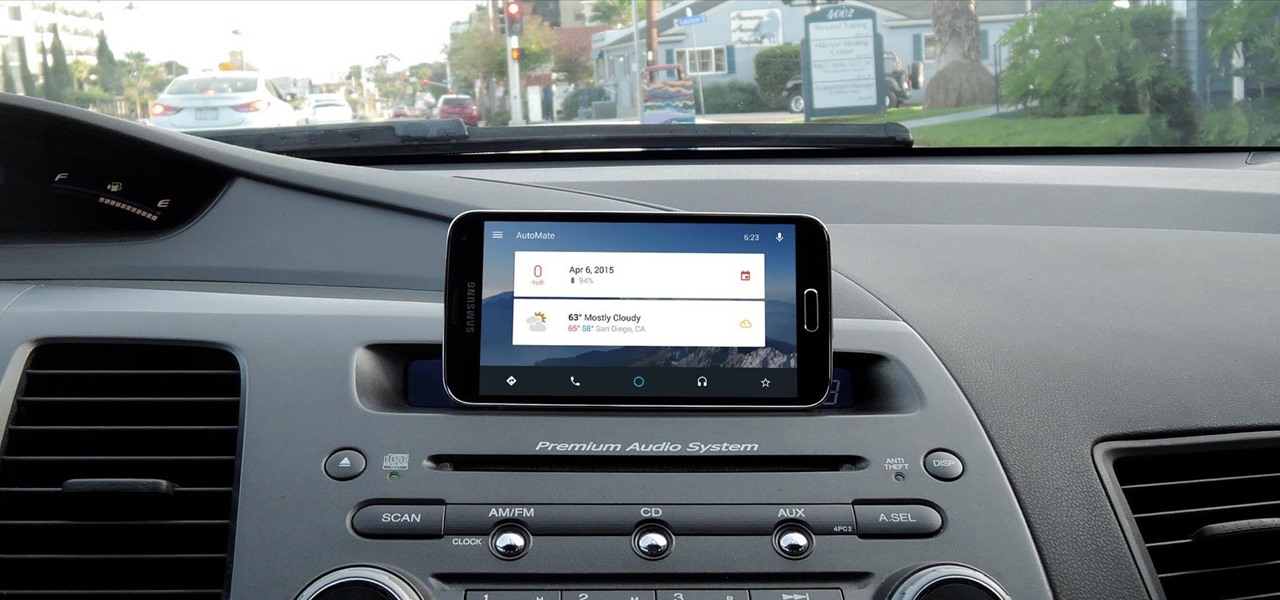
Auto manufacturers are slowly starting to debut models with Google's new Android Auto software baked into the dashboard console. Starting with the 2016 model year, we should see vehicles from Honda, Ford, Chevrolet, and many others sporting the new software.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Tinder, the extremely popular dating app, has the wonderful tagline, "Any swipe can change your life." However, if you downloaded their most recent update, your next swipe could cost up to $19.99.

If you're a fan of double-tap to wake gestures, you're going to love the newest app from ElementalX developer Aaron Segaert. On supported kernels, it allows you to associate custom apps and activities with each of the wake gestures you've set up, which will immediately be launched even with the screen off.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Samsung phones have a pretty nifty little feature called Smart Stay that will prevent your screen from turning off while you're actively using your device. Trouble with this is that it's exclusive to Galaxy devices and it uses a ton of battery since it monitors the front-facing camera to detect when you're facing the screen.

Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don't light up the associated pixels, meaning virtually no power is used. Since black pixels use little to no power on an AMOLED screen, more black pixels means lower battery consumption.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

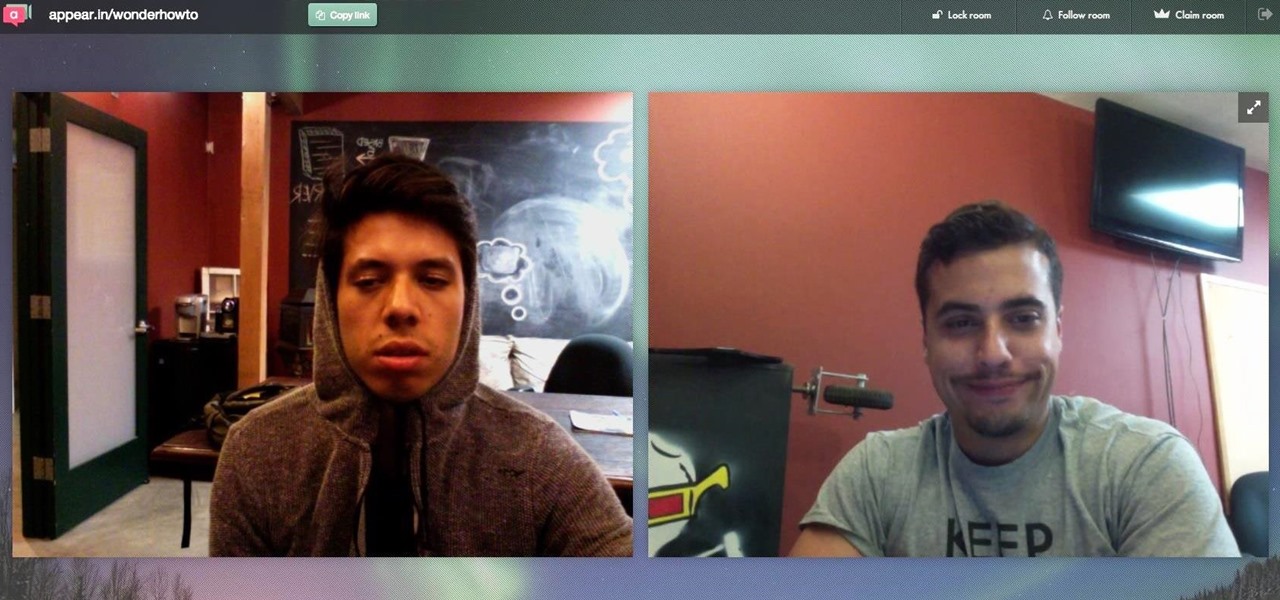
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.