It's time to go achievement hunting, as well as treasure hunting in this tutorial. The game is Red Dead Redemption and there are nine hidden treasures, each with their own video. It can take a long time to find these treasures if you were trying to get them on your own, but with the help of the videos, it much easier. So good luck, take your time, and enjoy!

Weird gifts from friends and family aren't the only things you can score on your birthday. With a little advance planning, you can get lots of freebies.

Check out this Halloween makeup tutorial and learn how to create this sweet ladybug look. Be creative this Halloween! This Halloween ladybug makeup look will wow everyone.

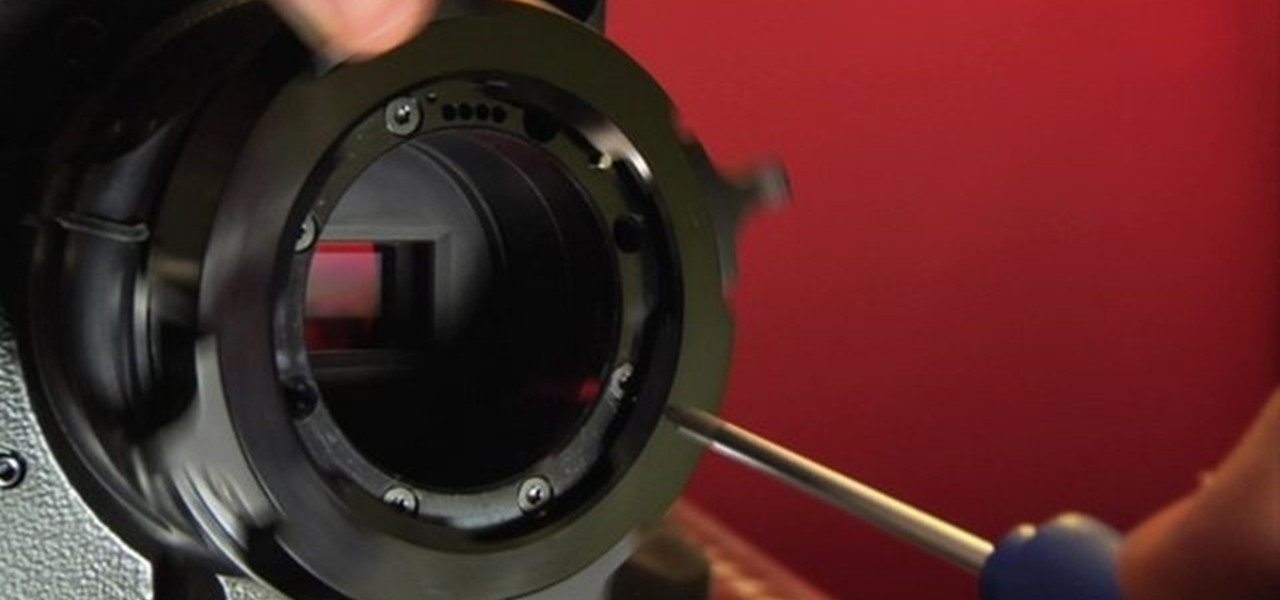
Douglas Underdahl from Long Valley Equipment www.longvalleyequip.com shows you how to change the RED camera's PL mount to Nikon

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

A recent update to Google Chrome replaced the colored avatar menu in the top-left (Windows) or top-right (Mac) corner of the browser that let you easily switch from profile to profile with a plain gray button that simply names what profile you're in.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

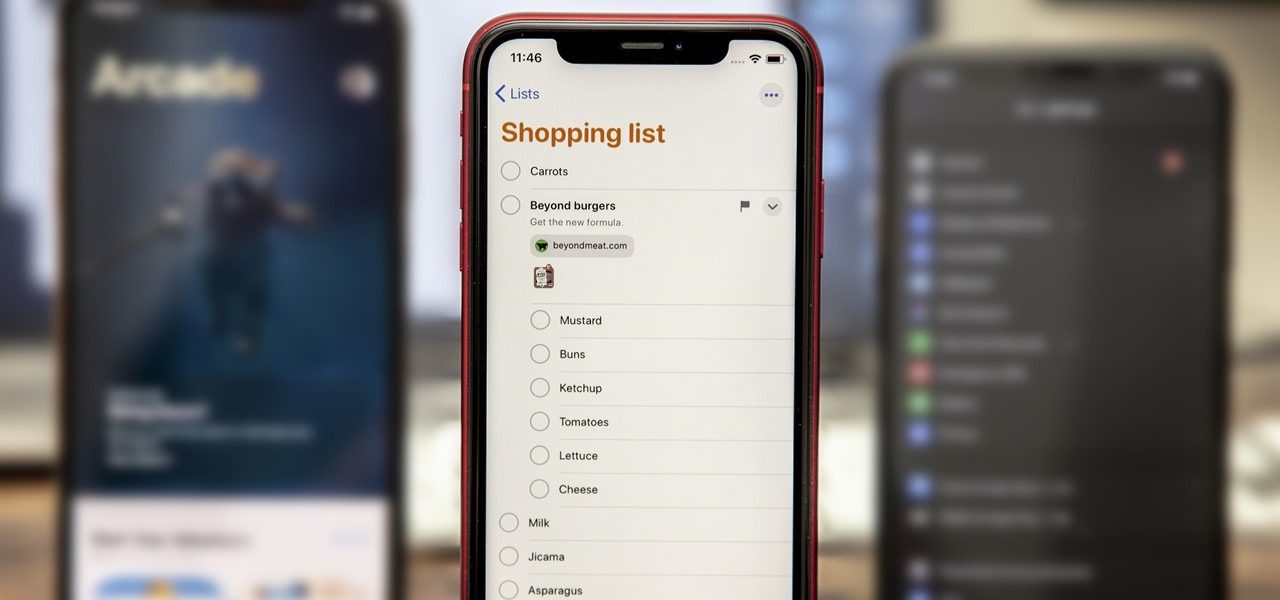
While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Reminders a shot, you may want to ditch that third-party to-do app you've been using.

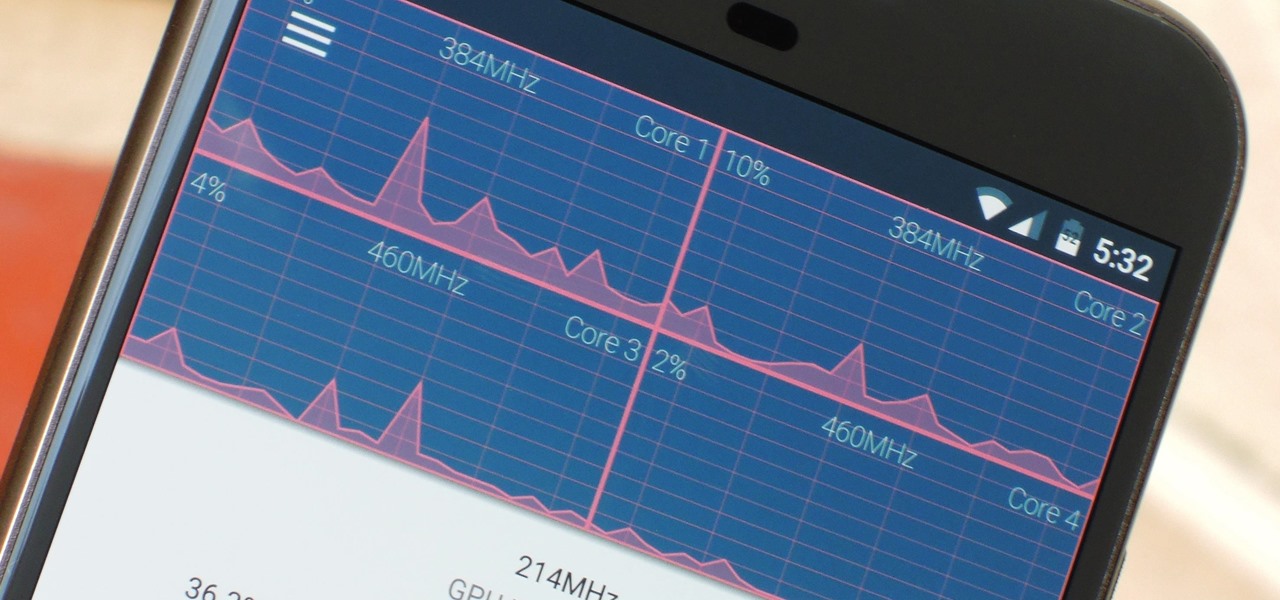
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

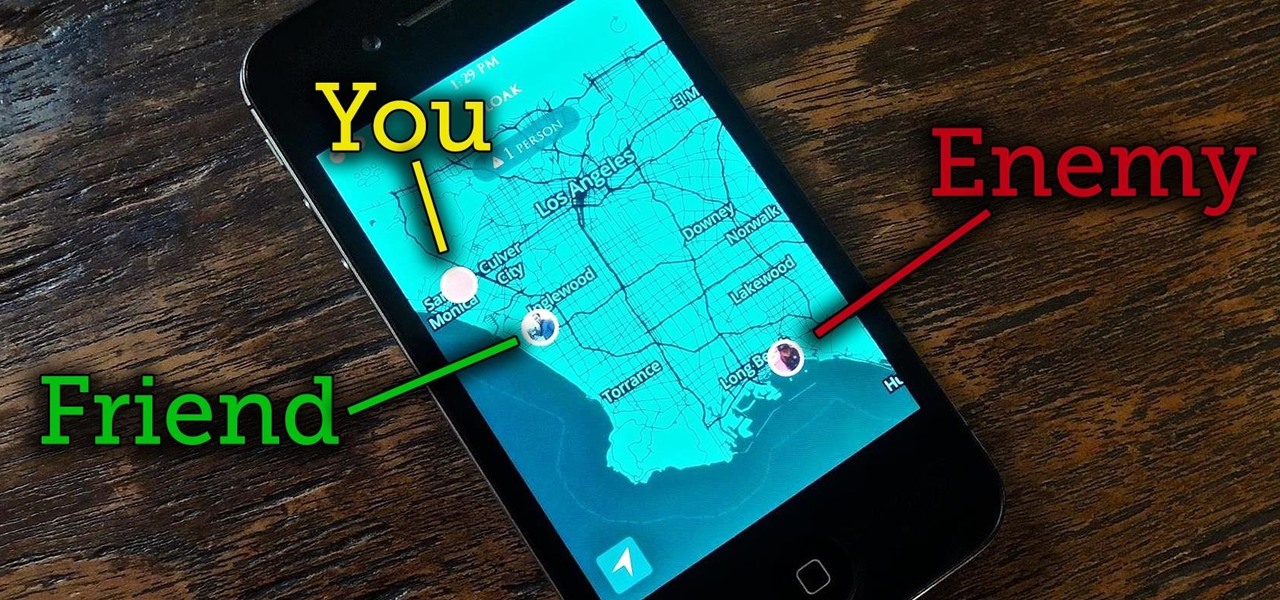
I never want to bump into my ex-girlfriend while out in the city (talk about a buzz kill), so if I could get an alert telling me that she's at Shortstops down the street, I'll avoid that area completely. This is where the new, interesting app Cloak - Incognito Mode for Real Life from dev Brian Moore comes in.

In this short, fun and informative tutorial, Andy Field demonstrates the Oil and Water trick using four black cards and four red cards. Four cards are placed on one side of the table and the four red cards are placed on the opposite side of the table. He then mixes the cards, pulling one card from each side to make a new pile of cards with alternating colors. One red, one black, one red and so on and so forth with each of the eight cards. After letting the cards sit for just a few seconds he ...

The Red One Camera has loads of menu and sub menus to explore. In this video, we dive into the video menu button on the back of the Red Camera. The focus is the video sub menu and all the feature contained within, including color, gain, and detail.

El Dia de Los Muertos, or Day of the Dead, is a holiday celebrated on November 2nd in Mexico and by Mexican Americans that commemorates the spirits of those who have died. The celebration consists of bringing your loved ones a dish they liked and sometimes decorating their graves with flowers and flags.

Try out these colors for fun - red, burgundy, black and smoke-ish colors for a hot blood-red look. Petrilude walks you through this amazing and gorgeous blood red makeup look. Pair it with a red dress that will leave your date hot with lust and passion.

Fourth of July is coming up in just a few measly days, and while we're sure you've probably already fired up the grill and purchased aquarium-sized packs of hot dogs, ground beef, cole slaw, and potatoes for your potato salad, you can show your patriotism through more ways than just food.

This video shows us how to draw an electric eel even if we are not professionals. We start by drawing a flag shape (like two cylinders connected) as this being the body. After this we can draw the eyes, one fully visible and the other only little because is in the back. Now we draw an open mouth and here we can let our imagination go wild an could put there some fangs, a tongue but do not forget to draw some shadows in there to be more realistic. For shadows you can use the edge of your penci...

Mixologist Chris McMillian walks us through the history and creation of the Singapore Sling in this instructional video. The drink originated in a hotel in Singapore--the drink used to be a Collins with a splash of cherry herring. This recipe is the original recipe from Raffles Hotel, where the drink was first made.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

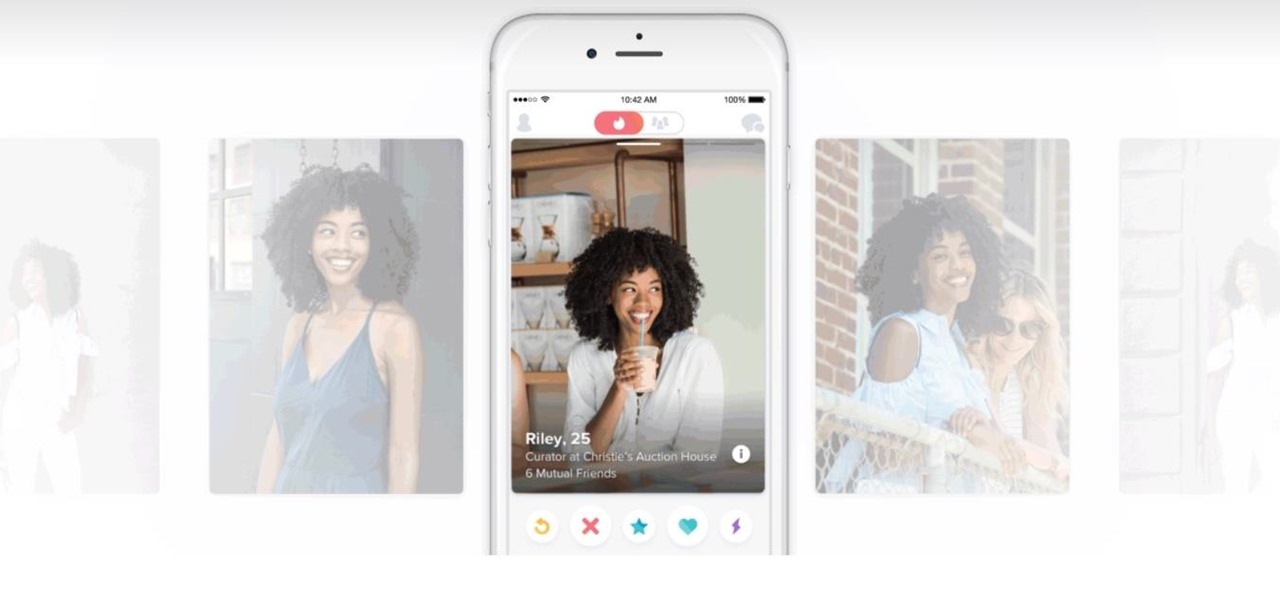
If we're being honest, very few people go on Tinder to fall in love with someone's personality. Oftentimes, the only reason they'll look at your bio is to make sure there are no red flags.

Some people hate cold weather, but there are also plenty of things to look forward to in the wintertime. The holidays, building awesome snow sculptures (or igloos), and hot chocolate, to name a few. But with all the good also comes one gigantic downside—more people get sick during the winter than any other time of year.

The Red Riding Hood movie by Catherine Hardwicke is a decidedly dark take on the story, which is pretty dark to begin with. This presents great opportunities for dark, sensual makeup both in the film and on your though, should you decide to watch this video and try out this dark, almost Victorian makeup take on Red Riding Hood.

Red Riding Hood is about to take predominantly young and female movie audiences by storm. This makes her a very topical choice for a costume party or just for emulation, and this video will show you how to do an awesome dark Little Red Riding Hood (the movie dropped the Little, I guess it's a little sexier without) makeup look and costume.

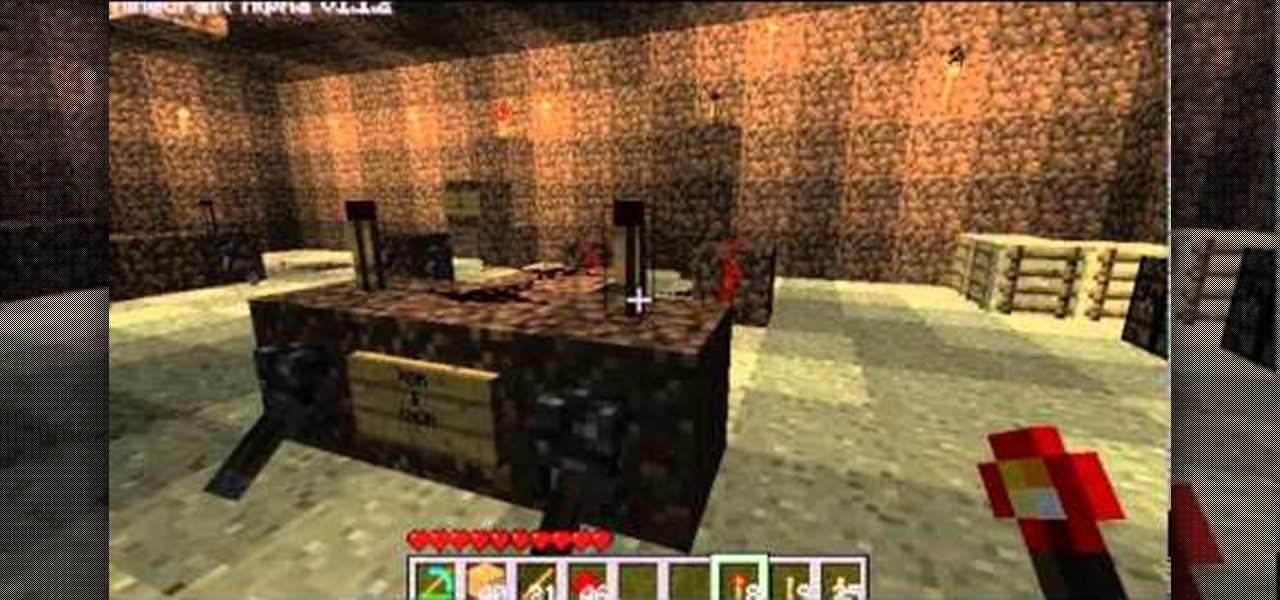
Everyone talks about Minecraft and Logic Gates all the time and the various uses for red stone, heck, someone even made a fully useable calculator! But using Red Stone takes a special kind of math and logic that some may be confused about. In this video you will learn the basic uses of red stone and also the logic and theory behind it and how it all works.

No one in their right mind would ever volunteer to be one of the Red Shirts, the security officers from Star Trek who so often died during the crew's away missions. Well, it is a pretty easy-to-make and easy to recognize costume, so it might be a good choice for your next nerdy Halloween party or other get-together. This video wills show you how to make a Red Shirt shirt of a long-sleeve shirt and paint.

The action's in Level 2 of Lara Croft and the Guardian of Light this time, and the goal is to find all of the hidden red skulls and to destroy all of the trucks. If you get all of the red skulls, you can earn the "Seeing Red" achievement. Jack and Geoff from Achievement Hunters walk you through the process.

In this tutorial, learn all about the controversial and artificial food dye, Red 40. Red 40 is linked to hyperactivity in kids as well as ADHD, migraines, stomach aches and jitters. The UK is actually banning Red dye 40 this year.

In this video, the viewer is shown how to apply red, silver, and glitter nail polish to make various patterns. First, you need to apply two coats of a natural, pearly color. Next, she uses a very thin brush to apply her red patterns. She uses one red to make lines and another red to fill in. Then she adds a dark, glittery red to coat over the filling. The same procedures and brushes are used to apply the silver on her nails. Finally, she applies small rhinestones to her nails by using the wet...

Learn how to do red eyeshadow with MAC Key Artist Chris D Par. Pursebuzz is a YouTube makeup star. Her makeup tutorials are widely watched and favorited. Pursebuzz delivers beauty tutorials on makeup application and hairstyling. Search Pursebuzz on WonderHowTo for all of of her beauty how to's, including skincare, hair, makeup and celebrity looks.

Check out this instructional cinematography video to learn how to install the Nikon mount on a professional RED ONE camera. This is not an official method, but simply one way to do it until RED officially releases its own how to video. If you don't have steady hands, you may want to take more precautions into covering the sensor while you work. This video tutorial does an excellent job of guiding you step by step along the way to better utilize your RED ONE camera.

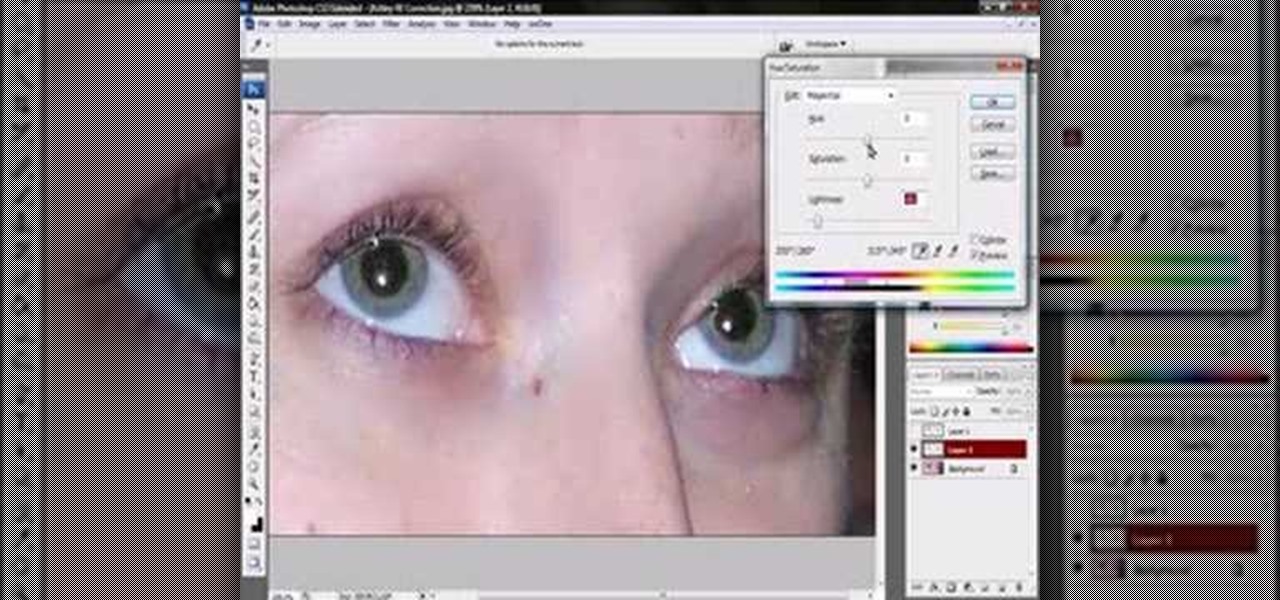
Jordan shows us a simple way to remove the red eye created by the flash of a camera using Adobe Photoshop. No matter where the red eye came from, you can remove it easily from any picture after watching this Photoshop tutorial. There are many ways to remove red eye and some are dirtier than others, but this method will give you a nice natural looking pupil in the end.

Glitches are everywhere in the video game world, and you can call them what you want... glitches, cheats, cheat codes, hints, secrets or tips. In order to find a glitch, you have to keep your eyes open or follow a recommendation from a gaming friend. Either way, to catch a secret glitch, you need to be ready; the cheats for the taking, whether a weapon or secret passageway, so take it, before it gets patched.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.