Do you want a unique way to display your vacation photos or present your holiday newsletter? Try making an instant book. This video, you will guide through the simple process. The presenter starts by referencing Esther K. Smiths book: How to Make Books. You do not need a lot of materials, just scissors, paper, and some pictures. After showing examples of different types of paper you can use, she demonstrates the step-by-step process of folding and cutting the paper. She even shows a slow moti...

The video shows us how to edit footage from Canon 7D at 1080/24p using Avid Media Composer. Canon 7D is first of the video DSLR which is actually an easily editable of an Avid media composer. If you are shooting a project at 1080 24P, then Canon 7D records the footage at 23.98 which is perfectly compatible and tested with Avid. Firstly create a new 1080/24P project. Now import footage from a CF card in DNxHD codec. Then edit the time line in real-time apply the real-time effects but here the ...
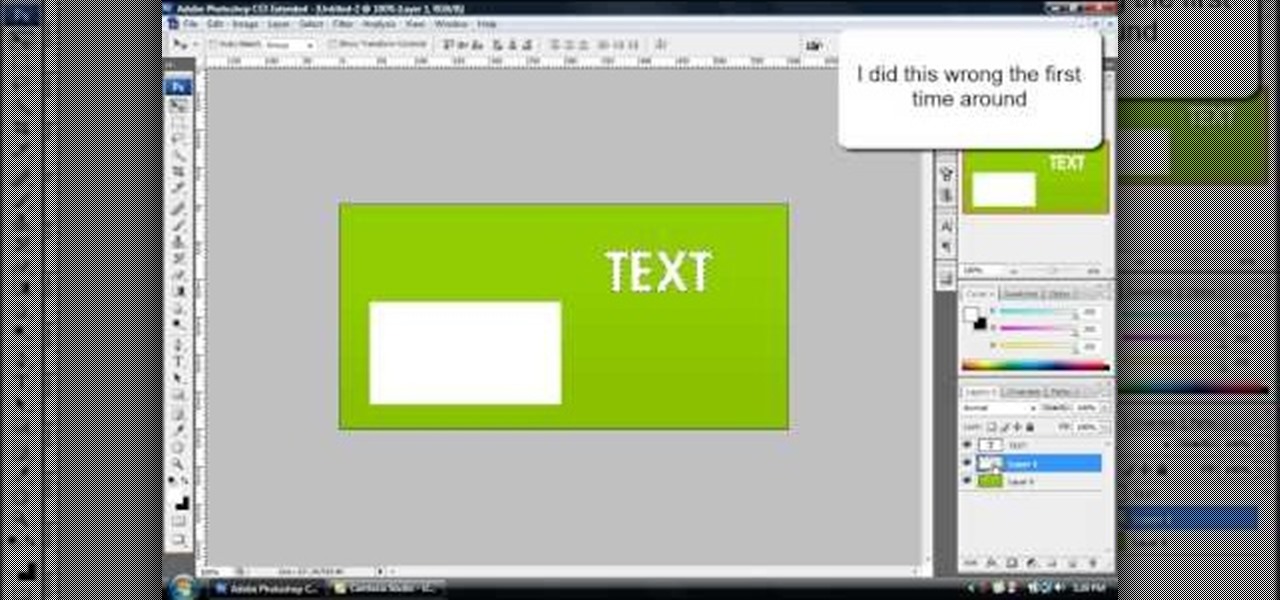
Melvin from QZPStudios takes you on a quick tutorial in which he creates an embedded text effect in Photoshop. This could be a useful trick for website designers who want to create banners containing text which have a shadow effect.

FAST is an expedited travel program for commercial truck drivers that travel between the US and Canada. FAST cards are available to citizens or permanent residents of Canada or the US. The FAST program is viewed as a privilege by both Canada and the US. You can be denied for the FAST program if you do not have a clean driving record and a clean record with the Canadian Border Services and The US Customs and Border Protection. Things such as being caught with undeclared items and having a crim...

Carving a net needle from wood is probably easier than you think as long as you have your trusty Swiss army knife at hand. It has a wide array of available tools in a small unit. First you will need a piece of balsa wood. It should be 1/8 of an inch thick by 3 inches wide and 8 inches tall. Using the sharp narrow blade of the knife, you will cut 3 reference holes in a triangular pattern. The points of the triangle should be 1 inch apart at the bottom and the triangle should be 2 inches high. ...

This video shows you how to use couplers for cake decoration using these steps: 1. Couplers usually come in two plastic pieces, a base and a ring. This system fits inside cake decorating bags or cones and allows you to use the same icing with different tips.

These elephant-shaped towels are so cute and easy to create that you’ll never want to use them for drying.

You're standing right in front of us, but your voice sounds like it's coming from over there! Color your friends impressed by learning the fine art of ventriloquism.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to track a USB device.

This step-by-step video tutorial shows you how to install CHDK onto your Canon digital camera. CHDK is a firmware enhancement that operates on a number of Canon cameras. CHDK gets loaded into your camera's memory upon bootup (either manually or automatically). It provides additional functionality beyond that currently provided by the native camera firmware.

This is a three-part 3ds max video tutorial that takes a look at using reference photos for creating a head texture. If you have photographs that can work, there really isn't any reason not to use them since they can often provide plenty of subtle details that would be very time consuming to add otherwise.

Expand your friendship bracelet horizons by learning how to weave a new one! In this video, learn how to make a friendship bracelet for any friend with their name woven in! Show your friend how much you care by giving them this personalized friendship bracelet.

Play on your own private server on World of Warcraft, be sure to follow the instructions to the letter!

Learn how to say the alphabet in Korean and recognize the symbols for each letter.

This tutorial shows the use of the Excel program PROPER. This capitalizes the first letter of every word of a text stream in a spreadsheet program.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

It's already Halloween and the night is fast approaching. You swore to yourself last year that you wouldn't wait until the last minute again for a Halloween costume, yet here you are on Samhain without a costume… again. All of the costume shops are sure to be crammed with last-minute shoppers, and you don't feel like spending a lot of dough anyway, so what are your options?

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.

Besides its extensive collections of add-ons for Android, Firefox's mobile browser apps have many built-in features that you won't see in other mobile browsers. One feature in particular, available for both Android and iOS versions, makes it easy to switch back and forth between search engines for any query.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

One of the least important but most noticeable changes in any iOS update is the look of home screen icons. In the new iOS 11, there aren't any drastic icon differences compared to iOS 10, but there's definitely a few design modifications for some of the main stock apps, such as Maps and the App Store.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

All Galaxy S8 models apparently weren't created equal. According to numerous user reports, it appears that Snapdragon-powered Galaxy S8 variants are using an older flash storage standard than what Samsung was originally advertising.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google Allo—but now it's gone mainstream.

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

Use the Excel Vlookup function in Microsoft Excel 2007 to look up data in a table. This tutorial looks up the level and value of a product from a stock list using the Vlookup function in Excel.

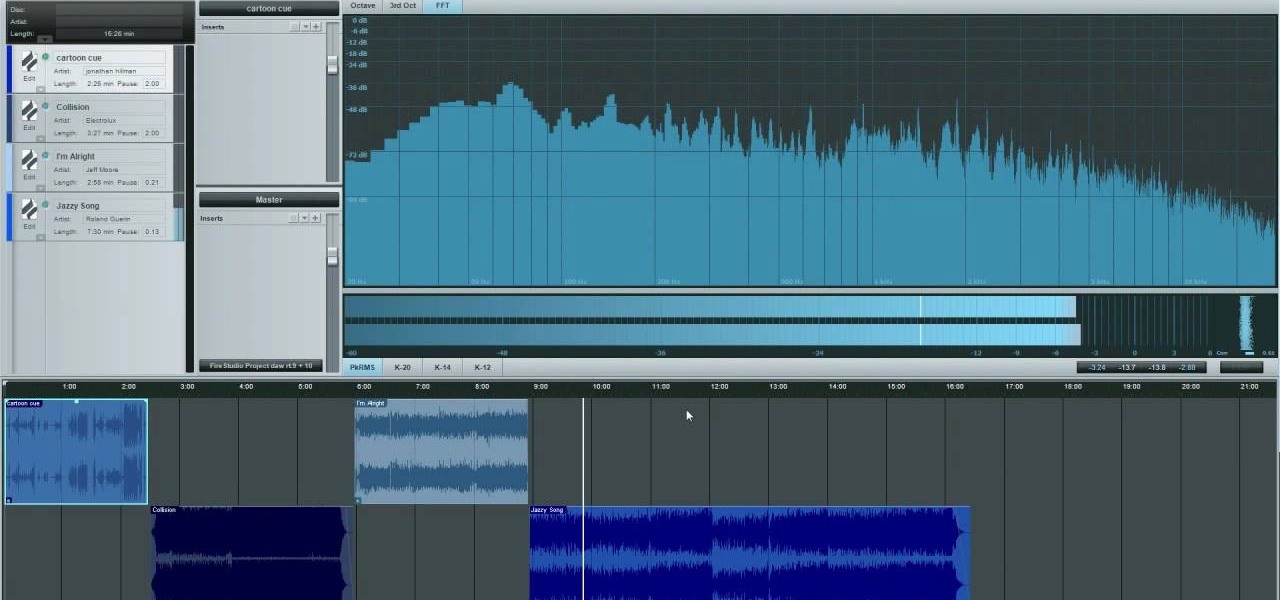
Two books were presented as suggested reading. One was by Bob Katz: Mastering audio; art and science. The other was Bob Alginski: the Audio Mastering handbook. Mastering takes a collection of songs and makes them sound like they belong together by making certain technical changes. The project page in Studio One is where the mastering is done. Drag in your sound content that you will be working with. Make sure you have the most recently updated version. If you are using multiple tracks, you mu...

In order to make a wallet with duct tape, you will need the following: duct tape, scissors, a ruler, a pen, plastic, credit card, and a smooth surface. Cut a strip or duct tape 8" long. Place it on a flat surface, with the silver side facing up. Cut another piece. Attach it to the first piece, laying it down at half the width of the first piece. Fold it over. Try to avoid making bubbles. Now, make a sheet by cutting 8 strips and attaching them together in the same manner. With a ruler, measur...

If you have not used your eRecovery system in a long time and have forgotten the password, have no fear. This video is here to help you retrieve your details and use your program again. In this clip, learn how to recover any lost passwords with Acer's eRecovery Manager for Linux.