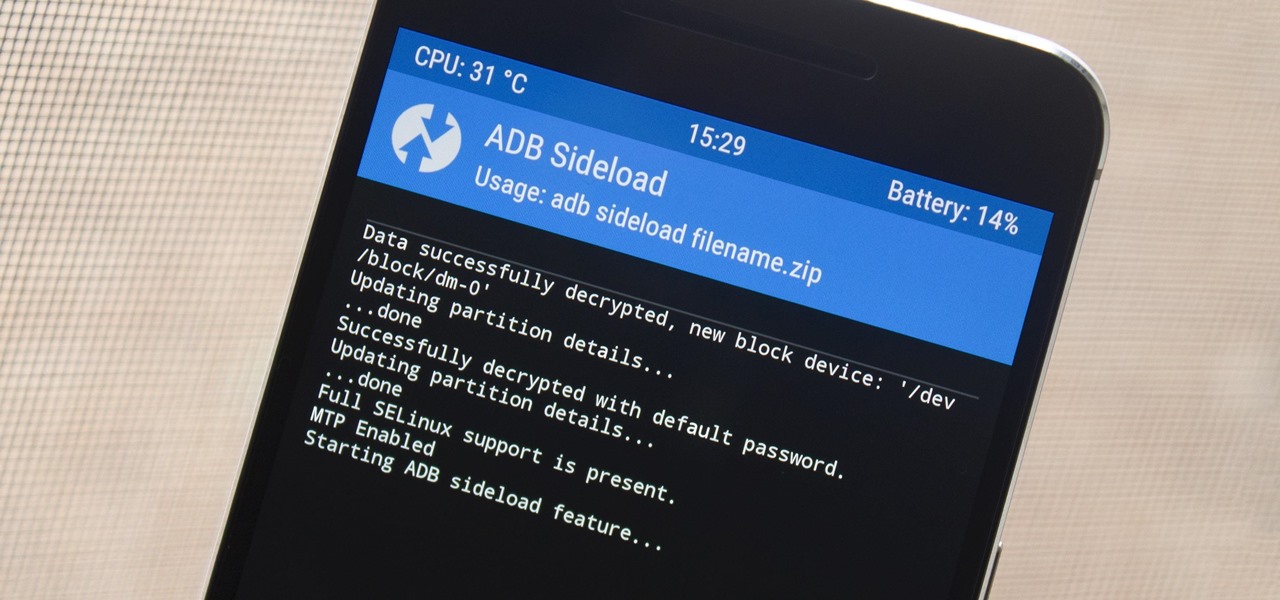
If you're one who likes to tinker with Android, TWRP is the first thing you should install. It replaces your phone's stock recovery mode interface and adds over a dozen advanced features to your device—most notably, the ability to flash ZIPs that can modify practically every aspect of your operating system. It's certainly one of the most powerful tools available for Android, and there's simply nothing capable of replacing it.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

There are two things you're not supposed to talk about in a social setting: religion and politics. When it comes to the latter, though, a certain orange-hued reality TV star has made it all but impossible to stay mum about the goings-on in DC.

I don't know about you, but visions of pumpkin pie and cornbread stuffing and big, juicy turkeys are constantly dancing through my head right now. I'm sorry, healthy eating habits, but it's Thanksgiving week, and all I can do is think about food.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here.

Whenever I go to Jamba Juice, I usually gravitate towards either the Matcha Green Tea or Caribbean Passion smoothies. But when I learned about their secret menu a few years ago, I felt like a little kid all over again—especially with flavors like Pink Gummy Bear and Orange Dream Machine.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Butter is one of the most versatile ingredients in the world: its variety of uses range from brightening a morning piece of toast to finishing a beautiful rib-eye steak with decadent flair.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Carriers like to distinguish their Android phones from the competition by making small changes to the interface here and there. This practice is so common that Android now has a built-in system for managing these small tweaks.

Chromecast is so small and portable that it would seem to be a perfect device for making PowerPoint presentations. But even now that you can mirror your Android device's display, there are still a few issues.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Finding the right theme can be a pain. Some are too gaudy or simple, while others look like they were thrown together as a joke. So why not try your hand at making your own?

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

Google's new camera app has a highly innovative and unique feature dubbed Lens Blur, and the most interesting thing about it is not necessarily what it does, so much as how it does it.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

As the cooler weather starts rolling in your pet will need more than just his natural coat to keep the shivers away. Take him out in style by designing a simple yet elegant tailored coat that will fit him perfectly. Here is an easy lined tailored coat with a nice thick comfort strap to keep him snug. Watch this video and follow the accompanying written instructions.

Whether it's because you want to make a quick tutorial video or want to show off your gameplay skills, recording the screen your Nexus 7 tablet isn't an easy feat. At least, until now. Hidden inside Android 4.4 KitKat is a built-in screen capturing feature, but it takes a little effort to dig it out.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Writing longhand may boost learning and goal achievement, but that doesn't mean squat if you don't have pen and paper on you.

Particles, such as electrons, have a property called spin which can be measured at any angle, but when measured always results in one of two answers—up or down.

Winter is coming... and if you don't get that Game of Thrones reference, it's okay, you're still cool in my book.
Are you scared that the RIAA is about to track you down for illegally downloading songs. Well, here is a method of obtaining many songs absolutely free that is virtually untrackable

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

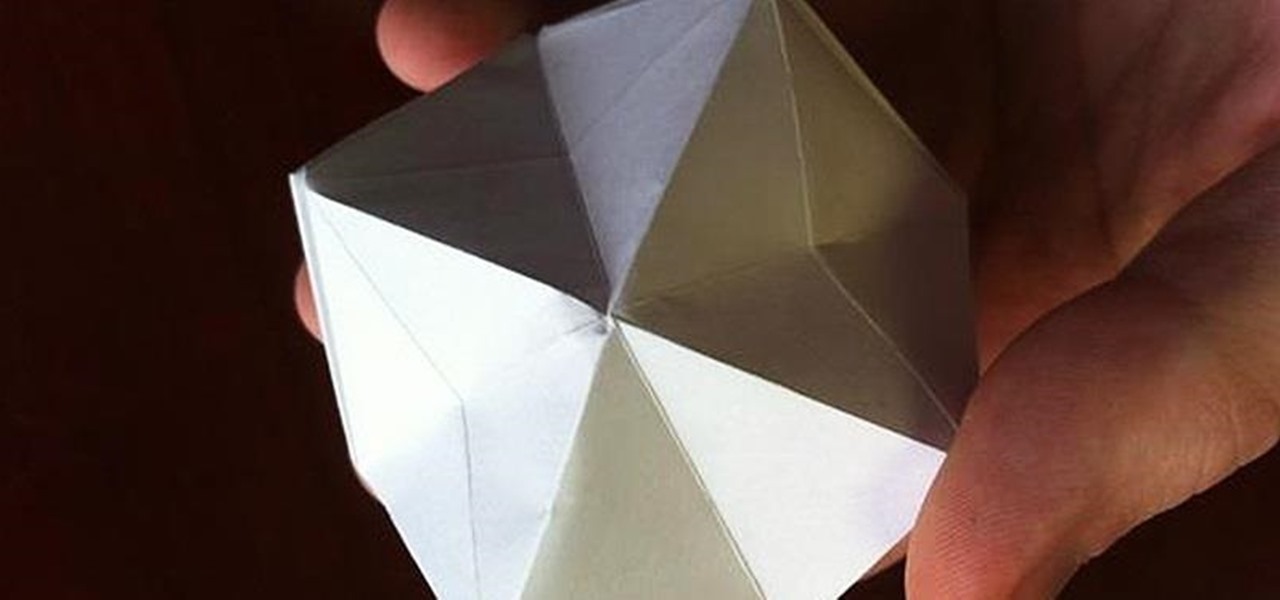
One of the most popular and basic origami geometric shapes is the "water bomb," which is a simple inflated cube. With a few extra folds and only a minor shift in approach, a more complex geometric shape can be achieved.

Ever thought about writing your own poems? You can learn how to in minutes by watching this adorable video. In it, you will discover how to create your own Limerick and haiku poems. A limerick is a rhyming poem that contains 5 lines and a haiku is a Japanese style poem containing 3 lines. This tutorial will teach you all about the amount of syllables you will need in each of the poems as well as several example poems for you to use for reference. Also, don't forget to take notes!