Many injuries do not require an ambulance, but they must be referred to medical aid for further treatment. This first aid how-to video will show you how to identify wounds that require further treatment. Underlying and dirty wounds, foreign objects, and stitches are all injuries that require a patient to go to a doctor or hospital.

This video is designed to give lots of clear and helpful information regarding the rib cable cast on" method, also referred to as the "alternate cable cast on" method. It is used as an edging for rib fabrics and forms a somewhat 'invisible' cast on edge that blends perfectly with the rib texture.

Demodex… what is it? It's a lot of tiny parasitic mites that could be plaguing your pet and attributing to hairlessness. Learn how to care for your pet with help from VetVid. See how to care for and treat Demodex (mites) in dogs with this video tutorial.

Check out how to demonstrate the Kaye effect using shampoo and lanyard with this tutorial. On dribbling shampoo from a small height above a pool of the same shampoo below, every now and then liquid lanyards of shampoo leap forth in a behavior referred to as the Kaye effect. Such behavior is characteristic of a viscoelastic fluid. This is a great science experiment to do with your kids. Watch this how to video and you will be able to create the Kaye effect at home.

Check out this cool video where you will learn how to create the liquid rope coil effect. Honey is dribbled off the end of a chopstick into a pot below. As the falling stream stikes the pool of honey below, it turns itself into tight circular coils which rapidly begin to pile one on top of the other. A growing column of liquid coils of rope begin to emerge from above the surface of the honey in the pot in an effect referred to as the liquid rope-coil effect.

Check out this cool video and learn how to create the Allassonic effect with a coffee cup, instant coffee and boiling water. When the bottom of a ceramic cup filled with boiling water and a heap of instant coffee is tapped at regular intervals the pitch of the sound heard slowly increases over time.

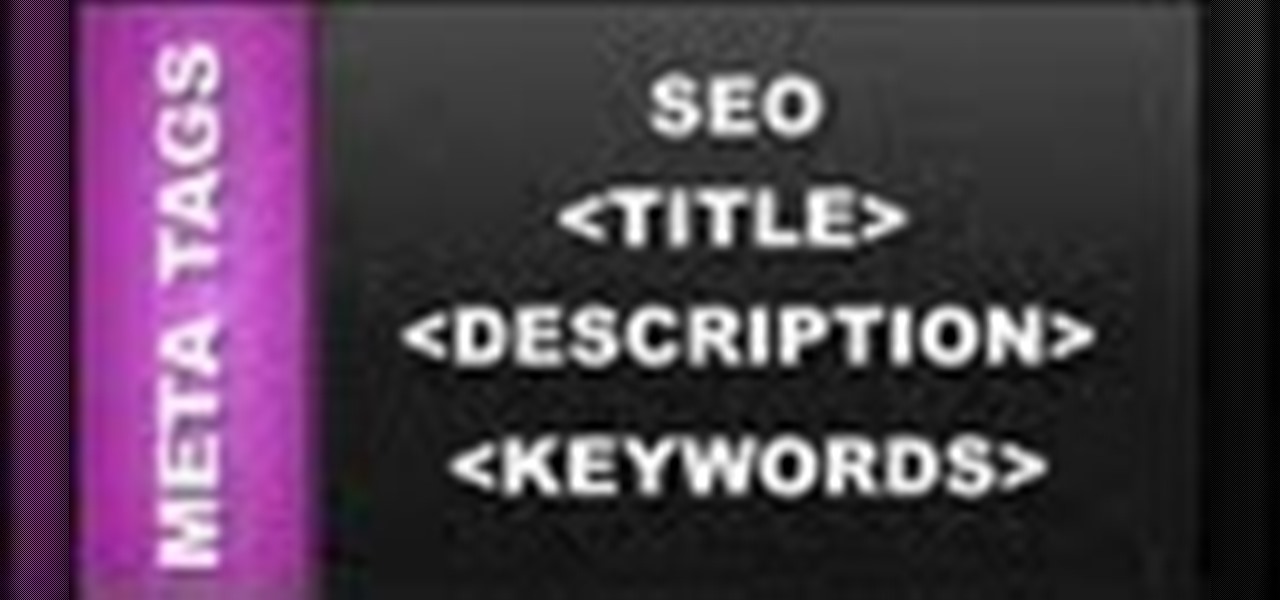
This web design tutorial will teach you how to add titles and descriptions that are relevant to your web page. Also you will learn how to add keywords for your website by using the website properties panel to add relevant keywords and phrases to your document in Xara Web Designer. The concepts taught for this web design tutorial are also referred to as Search Engine Optimization (SEO) meta tags.

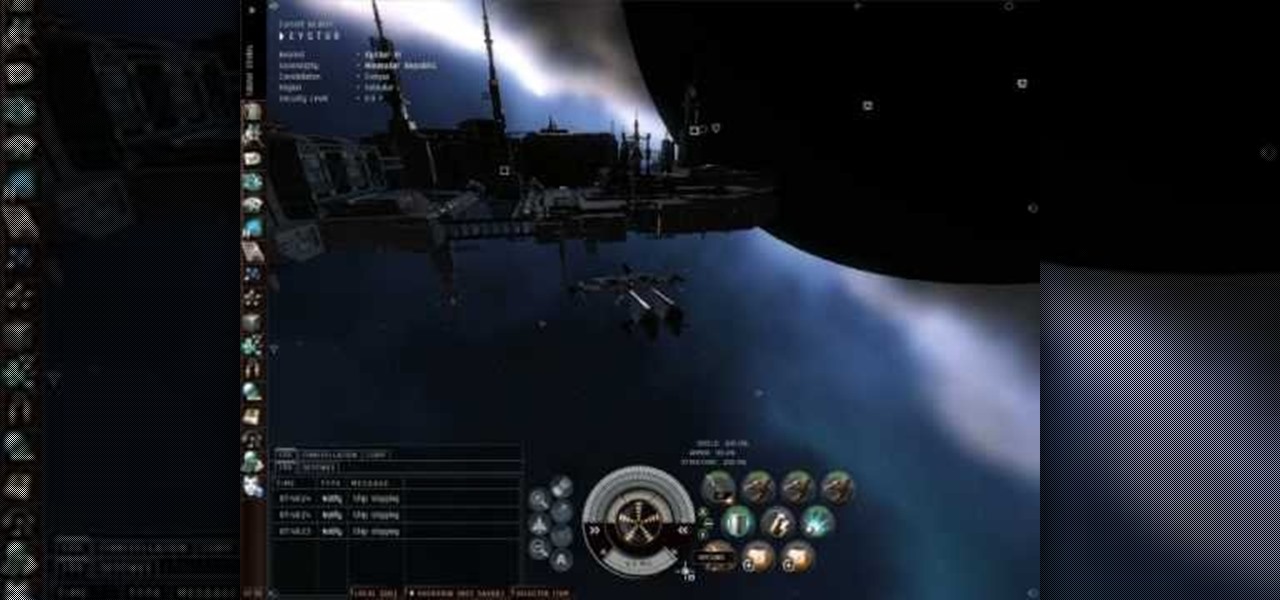
Weapon grouping has become available in the Quantum Rise expansion for EVE Online. This allows you to load ammunition for up to three separate weapons at a time - useful in a dogfight! This tutorial shows you how to group your weapons to take advantage of this new feature.

When a rod mounted in a hand drill is dipped into a liquid and rotated, for certain non-Newtonian fluids the liquid will climb the rod - sometimes to quite spectacular heights.

When wet sand along the water's edge at the beach is stepped on, it becomes partially dry in a small area surrounding one's foot. The dry patch is evident as the thin reflective film of water at the surface surrounding your foot is no longer there and has instead been drawn into the bulk of the sand beneath your foot.

Update: this article is referring to the 1.9 pre-release beta version, which is now commonly referred to as 0.1.9, released in October of 2011.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Many tech insiders are waiting for augmented reality to go mainstream, but if you look around hard enough, you'll find that it's already gone as mainstream as possible, thanks to talk show host Ellen Degeneres.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

As we slowly approach its January 3 start date, CES 2017 seems to be shaping up to be an exciting year for smart glasses as well as augmented and mixed reality.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

A fire snake, also referred to as a black snake or sugar snake, is a classic science experiment you can do right in your own kitchen using a baking soda and sugar mixture and a fuel to ignite the reaction.

This Video will show you how to Remove Gel Polish Easy. Let me Tell You my Story...lol

Ever wonder what your brain looks like while you're singing? No? Neither had I, but as this music video for the song "Better Man Than He" by SiVU (aka James Page) will show you, the answer is "pretty cool."

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Gerridae—you've probably seen these weird bugs gliding across the surface of the water when you're out swimming or fishing. These insects are commonly referred to as water striders, or more cleverly, Jesus bugs, for their ability to "walk on water". It's a pretty cool trick, but what could it do for science, right? Turns out, quite a bit. Photo by felixtsao

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Samsung's new line of Galaxy S20 flagships have a water resistance rating of IP68. This means you don't have to worry as much about getting the phones wet, but there's a limit to that.

Bus stops can provide shelter in the event of rain, and now they also protect you from augmented reality squid.

This year marks the first for Apple to exclude the Home button from any new iPhones. If you're going from a Home-button iPhone to a new XS, XS Max, or XR, you might be a bit stumped when trying to perform basic tasks, such as activating Siri. While you can't hold down the Home button any longer, there's a new method that's just as quick.

The Galaxy S9 is a great phone powered by the Android ecosystem. This includes Google's family of apps — many of which overlap with Samsung's in functionality. This can lead to redundant apps that siphon resources from your phone, but fortunately, there's a way to dull some of the noise and disable built-in apps.

After years of tantalizing drone video, and then brief glimpses from special guests sharing photos on social media, the Apple Park Visitor Center finally opened to the public on Friday, Nov. 17.

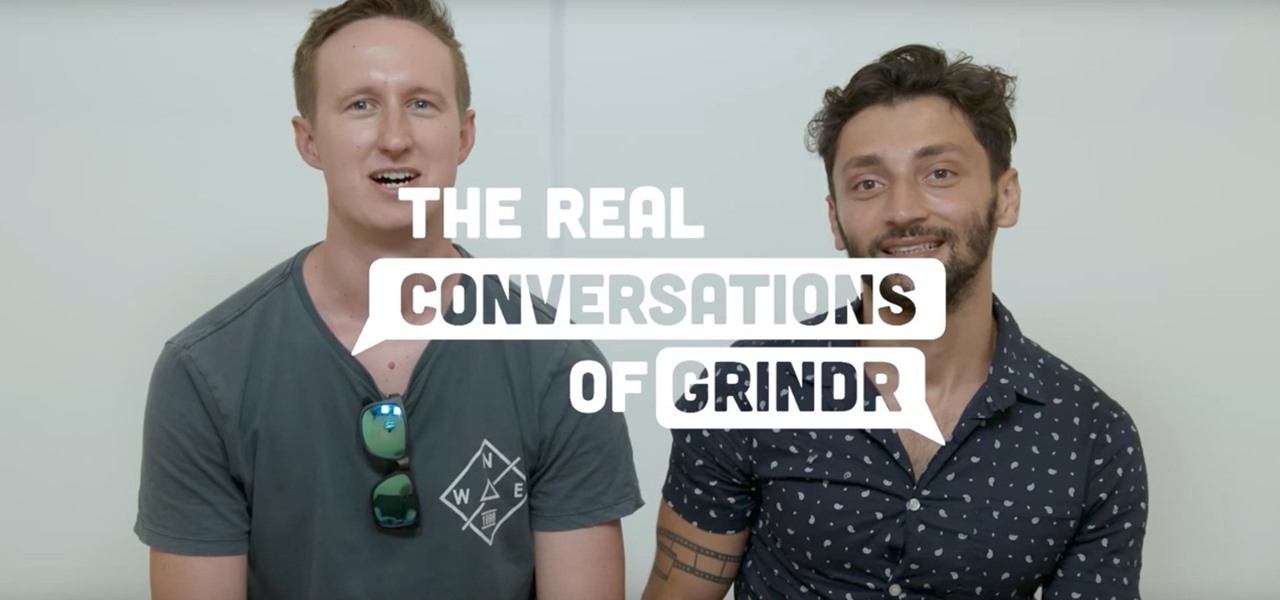
With significant advancements in the treatment and prevention of HIV, you'd think the stigma surrounding the deadly virus and AIDS, the syndrome the infection causes in the body, would have lessened. Unfortunately, a new project looking at conversations on Grindr — a social networking app for gay, bi, curious, and queer men — has shown that this stigma is very much present.

Apple CEO Tim Cook's June 5 announcement that the company is developing autonomous software should have some companies rattled. At least, Morgan Stanley thinks Tesla should be.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

Engineer Anthony Levandowski has officially been kicked off Uber's driverless program by a judge as the company's legal war with Waymo continues.

Google loves to play games. That's just what they did when they went ahead and teased us with a few Android O hints after Reddit user Zitroney unlocked an Easter egg in a Google Creative Lab developer's app ShortStories.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.