I know people who hate mayonnaise. I know people who detest ketchup. But I know almost no one that hates mustard, and that's because mustard has a complexity and depth that bland mayo and ketchup do not. Mustard runs the gamut from smooth and subtle to sharp and spicy, especially when you know how to make your own.

Google's got a hit on its hands with this one. Android 5.0—AKA "Lollipop"—will be making its official debut next month, but a new preview build has given us a glimpse into the future, which looks brighter than ever.
Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Material Design in mind.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

It was only a matter of time before the apps from the new Samsung Galaxy S5 leaked for everyone to download and install, and today we've got one that takes advantage of the IR blaster on your Galaxy Note 3.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?

Even if you haven't heard of ube (pronounced "OO-beh"), you've probably seen pictures of desserts made with this brilliant purple yam.

Contrary to popular belief, sushi is not the raw fish that one gets at Japanese restaurants, but the rice that comes with it. It's hard to tell whether this popular misconception led to or came about because of the primary flavors that we think of in sushi are the fish. We often say a sushi restaurant has great fish, but almost never that it has great rice.

It's common knowledge that certain foods foster brain development, health, and memory. Fish almost always makes the list, as do any foods that are loaded with antioxidants like blueberries, nuts, whole grains, green tea, and dark chocolate. Spices like turmeric are being studied for their ability to prevent Alzheimer's, among other things.

Giving a speech in front of a large crowd doesn't need to be the nightmare everyone imagines it to be. We speak to many people every day and yet it is still very common for a person to be nervous when delivering information in front of several people. This fear can be overcome by practicing how to give a speech and being prepared.

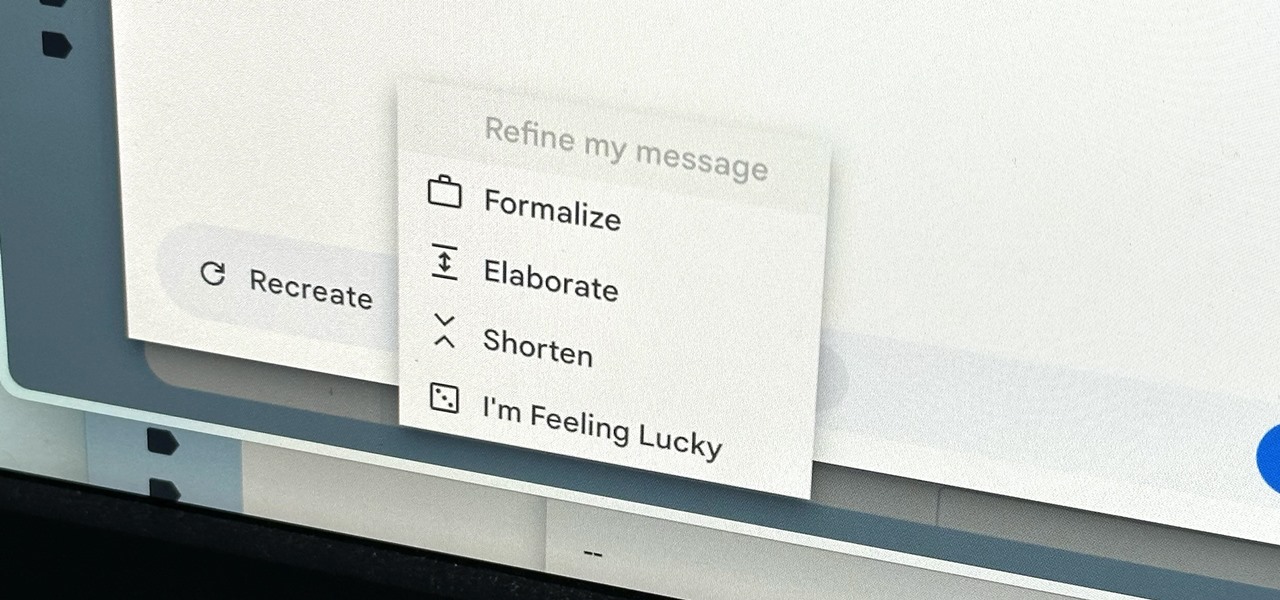
Thanks to rapid advancements in the field, generative AI can do some amazing things already, from generating text, images, and video with just a prompt to automating tasks and developing new products and services. Now, artificial intelligence can even help you craft emails directly in Gmail.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

With Apple's Photos app, you no longer need a third-party tool on your iPhone, iPad, or Mac to blur or pixelate faces in your photos, helping you safeguard identities when sharing online.

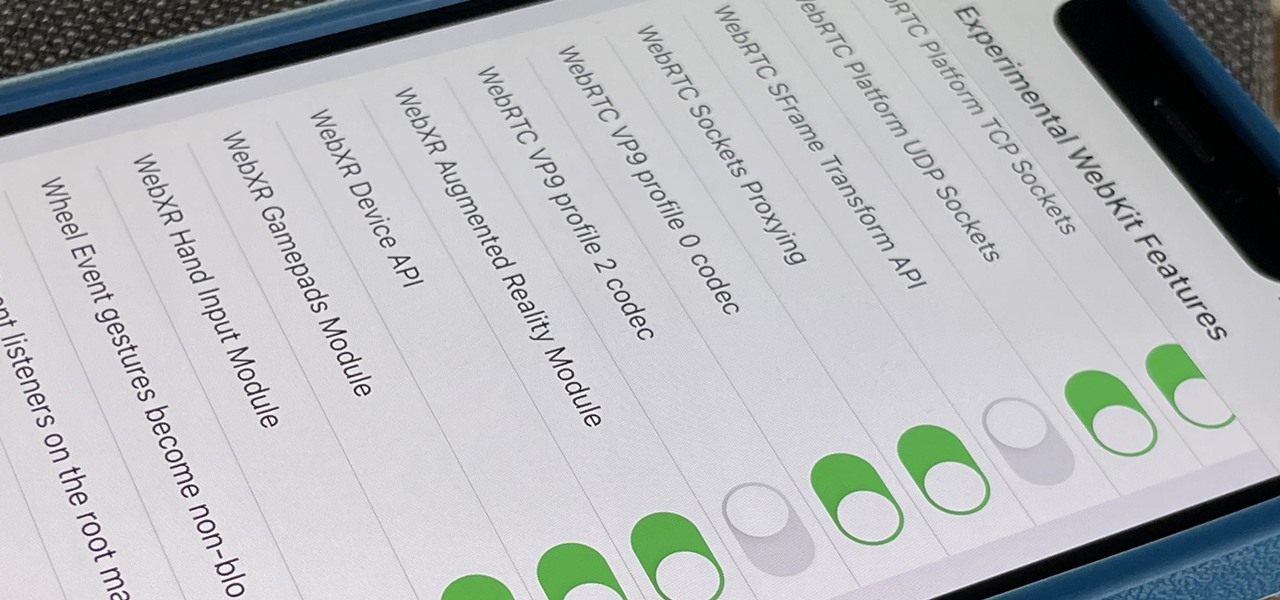
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

It's all fun and games until the technology is actually put into use and you realize augmented reality is now part of Death Star.

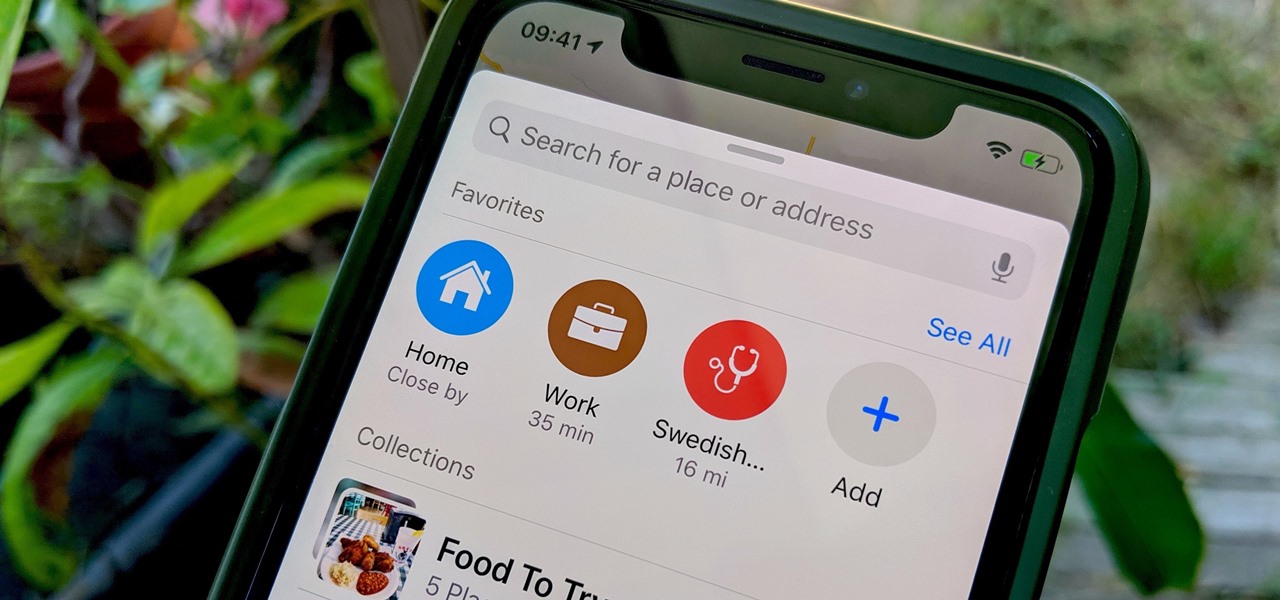
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Tell the truth. The bat picture creeps you out. You are not alone. But in reality, bats truly are some of our best friends. They gobble thousands of disease-spreading bugs a night. But they also carry viruses that can be deadly to humans. So, bats — friend or foe?

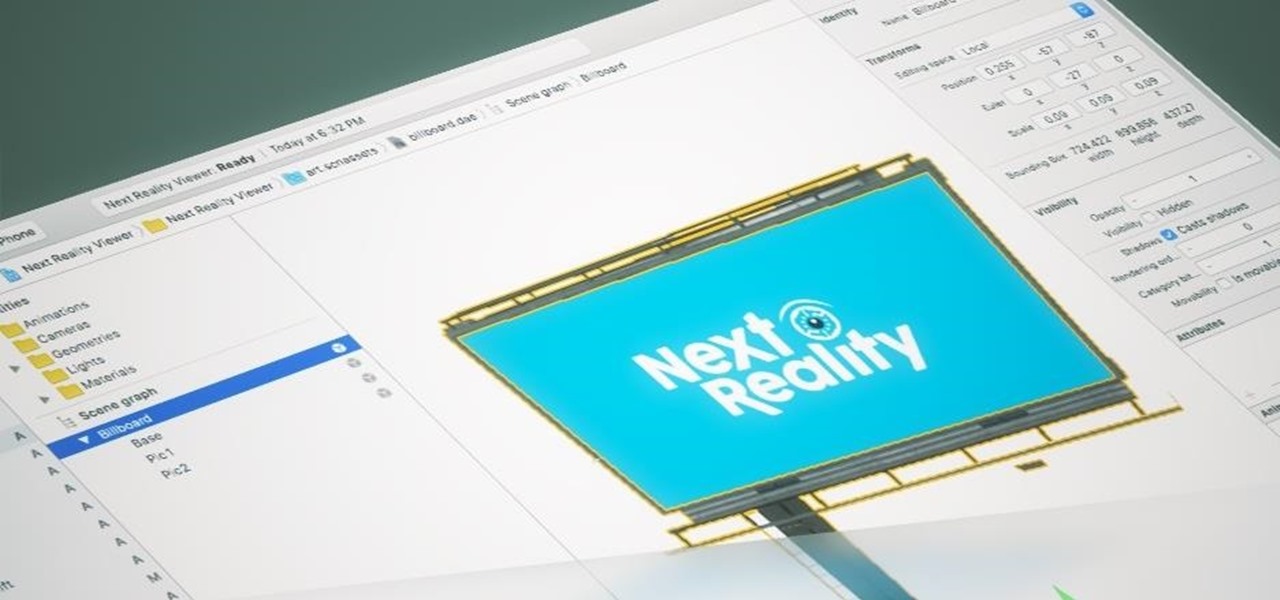
The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

Are you looking for a little microbe magic? Think composting. Composting is a great way to reuse food and plant waste that you would otherwise throw into the trash, which would just end up in a landfill somewhere. During the composting cycle, microbes reduce this organic waste until it can be fed back into the soil as rich, crumbly compost. When returned to the soil, compost feeds plants and improves the nature of life underground. Sound like a great idea? It is — and it's easy.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

It feels like someone reached into your chest and squeezed. Your head throbs in unison with your heartbeat. Clammy dread coats your body in sweat. Whether you call 911 or someone does it for you, the ER is your next stop.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the trash, not topping your toast.

There are literally hundreds of granola recipes floating around the internet—but I can tell you right now that they're all completely unnecessary. You don't need a recipe to make granola; I've been making granola for years and have never once used one!

Common knowledge is a funny thing: it represents a majority's opinion on a particular subject and somehow makes that opinion fact. If that 'fact' goes unopposed and unchallenged, then it is passed on and preserved from one generation to the next—regardless of whether it is true or not.

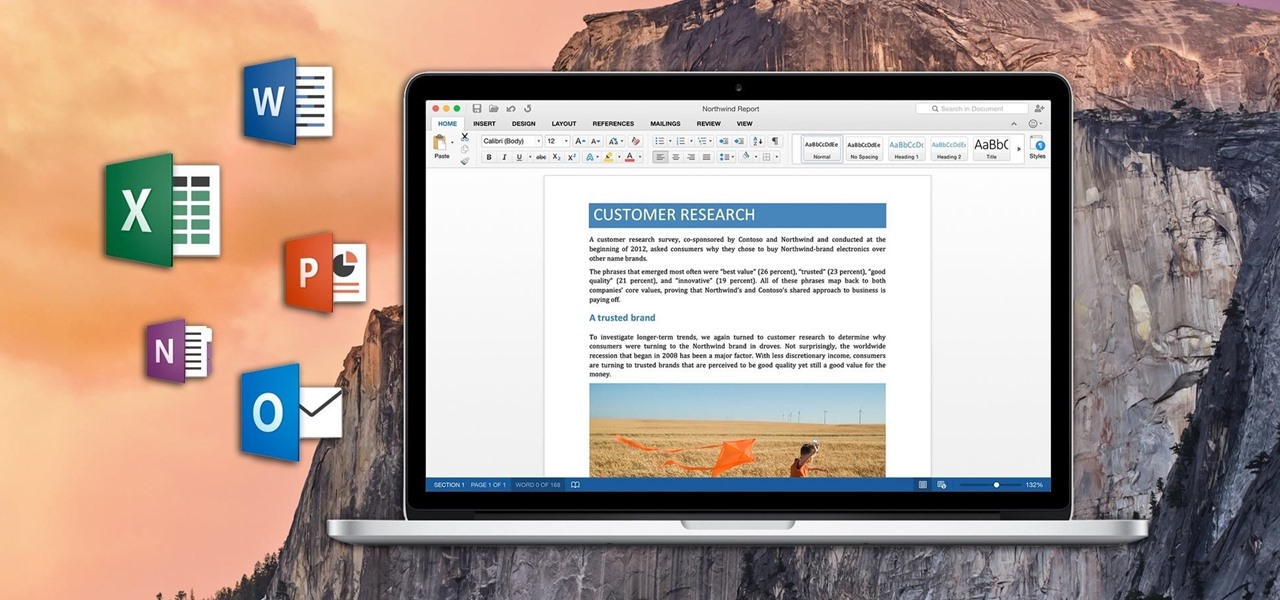
If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

Apple's grand reveal of iOS 8 at WWDC in San Francisco is still a few days away, but that doesn't mean there isn't any speculation as to what features and enhancements might come packed in the new mobile operating system.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.