I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Most recipes don't specify what type they mean when they call for onions. While using whatever kind you already have won't necessarily ruin a dish, using the best one for what you're cooking will definitely make your food taste better.

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

We always know roughly when Apple events are coming, but when their new product events pop up, they're always a pleasant tech refresher from the Cupertino tech giant.

IT is a competitive field, and finding success requires more than knowledge of a couple of coding languages or knowing how to google really well. To stand out among your peers and competitors, you should learn everything you can and get as much diverse experience as is available.

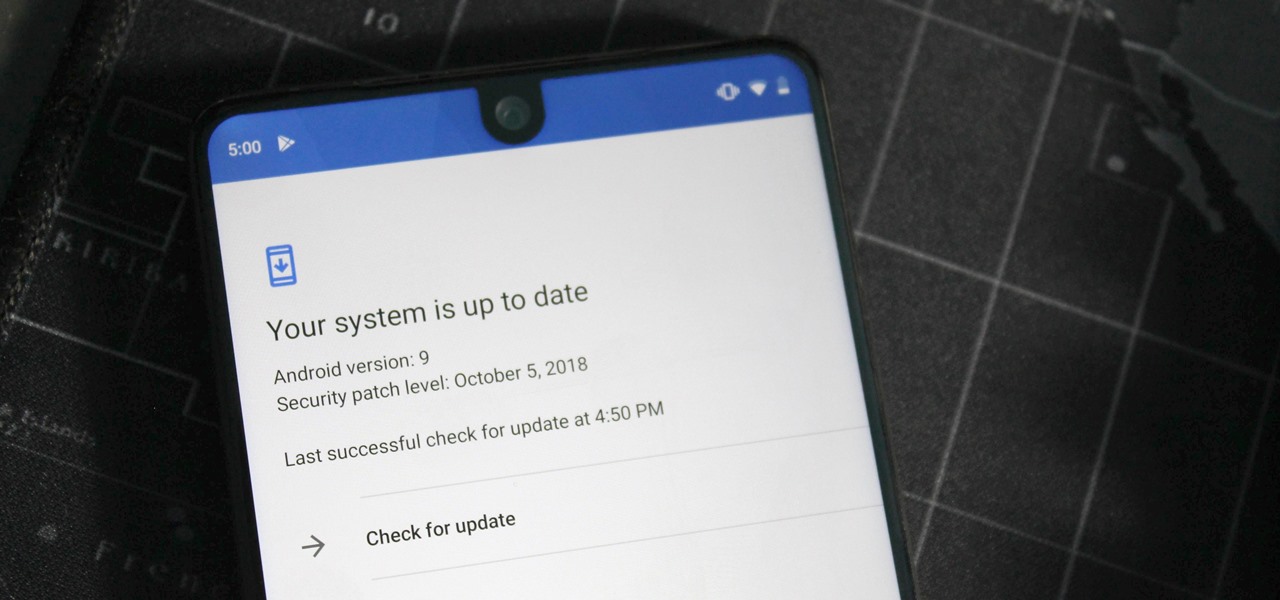
One of the issues with rooting your device is the inability to update your phone via OTA. Any security patches or software updates pushed out by the OEM are lost because your bootloader is unlocked. However, you still can update your device, it just a take a bit more effort.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our refined hacking Ubuntu container. Before we dive right in, though, let's make sure we still have a functional Docker installation.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

I think it was about Day 3 of working on our massive, all-encompassing Pixel 4a root guide for beginners when I realized something: Not everyone needs their hands held through each tiny step. If you just need a quick refresher, some links, and maybe a fastboot command to copy, this Pixel 4a root guide is for you.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

If you have Snap Spectacles 3, the dual camera-equipped sunglasses capable of capturing 3D photos and video, by now you've likely jazzed up the videos you've captured on the wearable with Lenses via Snapchat.

5G is here. Well, not everywhere. All three wireless carriers have turned on their 5G networks, but only in select markets. Like 4G, each carrier is doing things a bit differently, which means your 5G experience will not be the same across the board.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

This clip demonstrates how to create a caustic lighting effect using Houdini's Mantra PBR rendering engine. The first part starts with a refresher on refraction. More generally, guide looks at setting up normals correctly, then at the glass shader in Houdini, faux caustics and shadows, and using an environment light in PBR to generate 'background' reflections. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acq...

I've heard some people say that "brown people smell bad!" Ahem. Brown people don’t smell bad! Okay, some do, but so do people of all races and cultures. How a person smells has nothing to do with their race, but rather choices they make. I choose not to smell bad, and take steps to make sure that does not happen. Personally I cannot stand bad smells. It's something that makes me feel sick, so I try my best to make sure that I am not the cause of a certain odor. The following are steps I take ...

While many of us carved pumpkins when we were younger, pumpkin carving is a seasonal skill, only needed around Halloween. If you're looking for a refresher course on how to carve a pumpkin, this tutorial will walk you through the process. Be sure to pick out the best pumpkin at the patch!

This After Effects tutorial by Aharon Rabinowitz shows you how to use layer blending modes and offers some really good work flow hot key tips for the blending modes. This is a great video for beginners or users that need a refresher. Use layer blending modes in After Effects.

Most of the oddest games in the world are free web games. They may not always be well made, but low budgets (and consequently low risk) allow them to be as weird as they fancy. That's a big part of why they are so interesting. Prime examples such as Don't Take It Personally, Babe, It Just Ain't Your Story and Lesbian Spider Queens of Mars have graced these pages previously, and both are great games. But the quality of the games hasn't stopped mysterious Glorious Trainwrecks user snapman (else...

Have you already abandoned your New Year's resolutions? Maybe you need a refresher on how to stick to your goals and avoid succumbing to your worst temptations and unproductive habits. No matter where you are in life right now, all of us can benefit from increasing our sense of willpower.

Jezebel's back with another Beauty 101 (1, 2, 3), and this time the issue at hand is body odor. Everybody gets a little stinky from time to time (some more than others), but have no fear- there are solutions. Jezebel readers also address problems such as pit stains, excessive sweating, and natural deodorant alternatives.