It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

In a surprise twist, Apple released iOS 12 public beta 8 to software testers on Thursday, Aug. 23, right alongside iOS 12 dev beta 10. The release comes as a bit of a shock, as the company released iOS 12 public beta 7 just three days earlier. The official build of iOS 12 now feels closer every day.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.
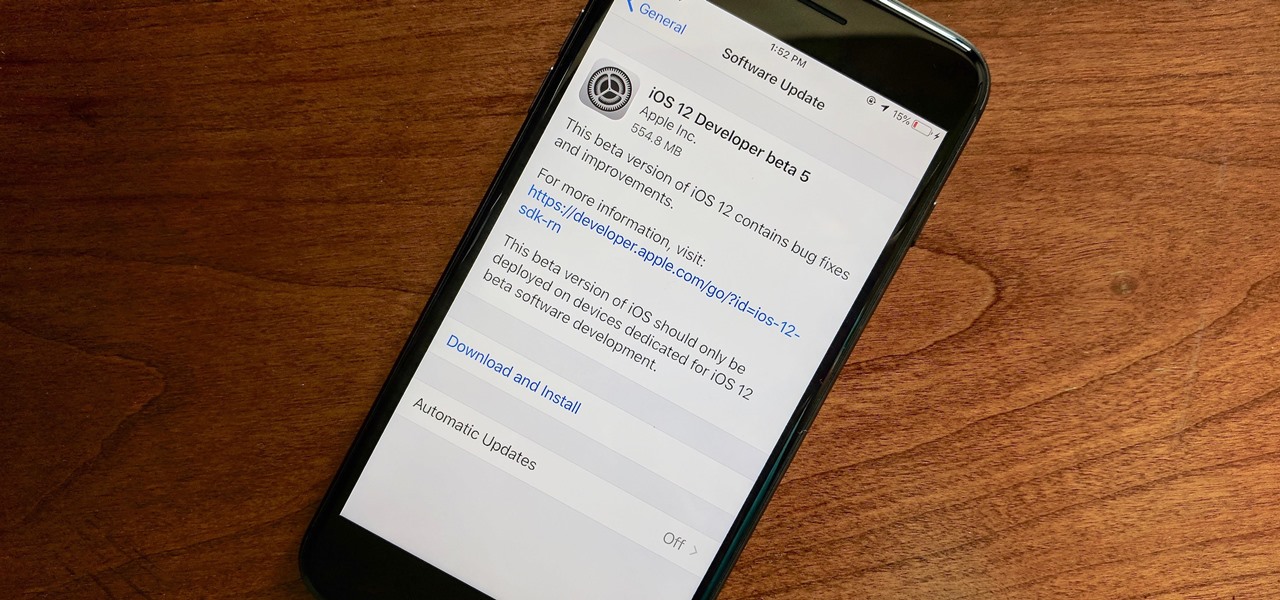
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.

Have you ever seen pictures or videos of balloons being let go into the sky and randomly floating away in all directions? It's something you often see in classic posters or movies. Well, guess what? Now you'll be able to do that without having to buy hundreds of balloons, all you'll need is ARKit!

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

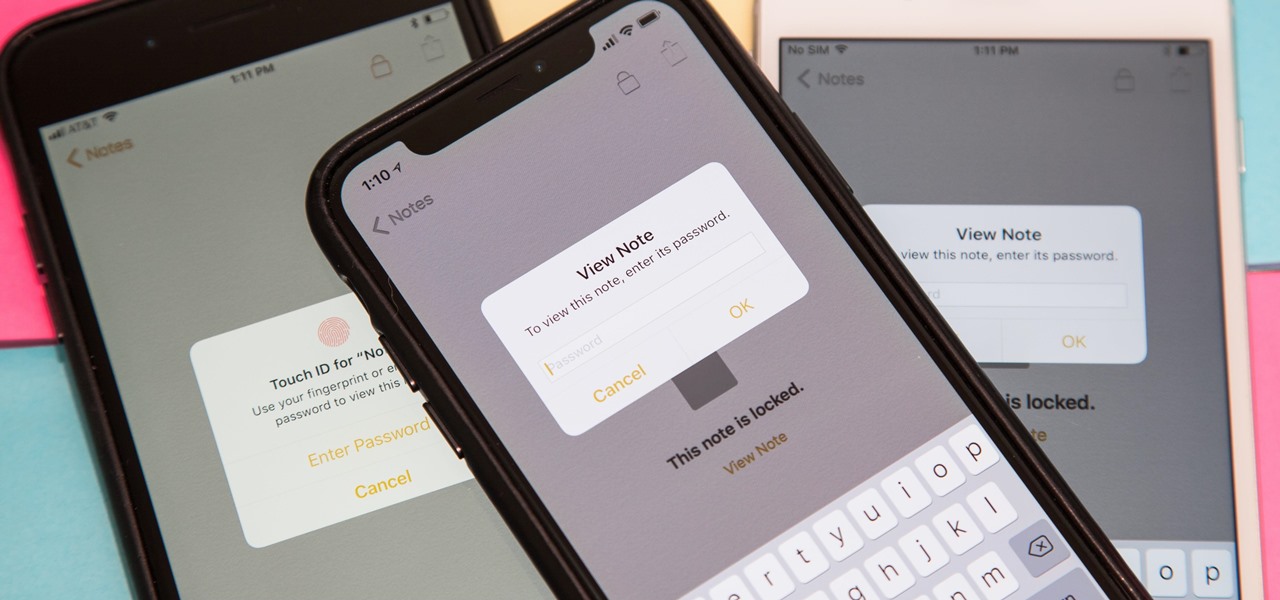
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

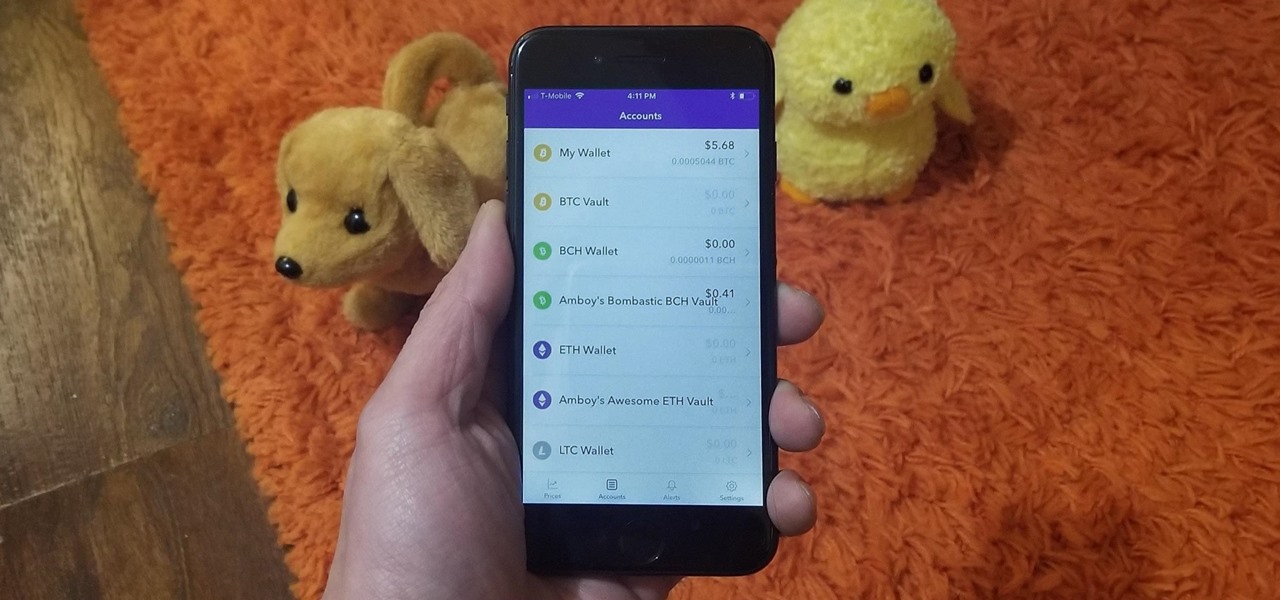
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

The world of investment and finance can be labyrinthine in its very nature — and even more complicated in regards to augmented and mixed reality. While these new emergent technologies are teeming with explosive levels of unrealized potential, there's still a big layer of uncertainty in terms of return — but these investors aren't afraid to take the leap.

The search for the causative agent of colony collapse—the mass die off of honey bees throughout the US and Europe—has escalated with increasing confusion lately. Everything from pesticides and stress to viruses and mites have been implicated, and some researchers think that many of these environmental factors work together to take down hives.

The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announcements on the horizon.

I've seen my fair share of heartbreaks when it comes to used phones. As a repair tech, I often had to try and help out customers who bought used handsets which turned out to be useless, either because it was stolen or not working on their carrier's network. More often than not, there was very little I could do. To help you from being stuck in the same situation, here are some tips to prevent you from getting scammed out of your hard earned money when buying a used handset.

Tonic water, seltzer water, club soda, and mineral water: these 4 types of "bubbly water" are often, erroneously, used interchangeably. But the truth is that each possesses unique qualities and uses that set them apart from each other.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Everyone and his mother (and grandmother) has a chocolate chip cookie recipe that he swears is the absolute best recipe, guaranteed to produce a chocolate chip cookie so good it will make you weep with joy. The problem with that is that everyone—relatives included—has a different idea of exactly what constitutes a perfect chocolate chip cookie.

Common knowledge is a funny thing: it represents a majority's opinion on a particular subject and somehow makes that opinion fact. If that 'fact' goes unopposed and unchallenged, then it is passed on and preserved from one generation to the next—regardless of whether it is true or not.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

What if I told you that you could read minds? You'd most likely think I was crazy, and you'd be right. But what I really meant is that you could make people think that you could read minds, something that's not the least bit crazy.

There are more actions available for the Action button, but only a handful of iPhone models have that button. However, there is another button with new features you can use, and you can access all the fresh features on any iPhone model that can run iOS 18.

The iPhone 15, iPhone 15 Plus, iPhone 15 Pro, and iPhone 15 Pro Max are Apple's most powerful iPhones to date with features like USB-C connectivity, improved camera capabilities, and faster CPUs. But no matter how impressive these phones are, they can still freeze, become unresponsive, or get stuck when powering on — and a force restart is how you get things working again.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

The legal battle between Epic Games and augmented reality startup Nreal isn't cooling off anytime soon.

Apple released the fourth beta for iOS 14.7 today, Tuesday, June 29. The update comes 15 days after iOS 14.7 beta 3, and restores battery service messages that may have disappeared after reboot on some iPhone 11 models.