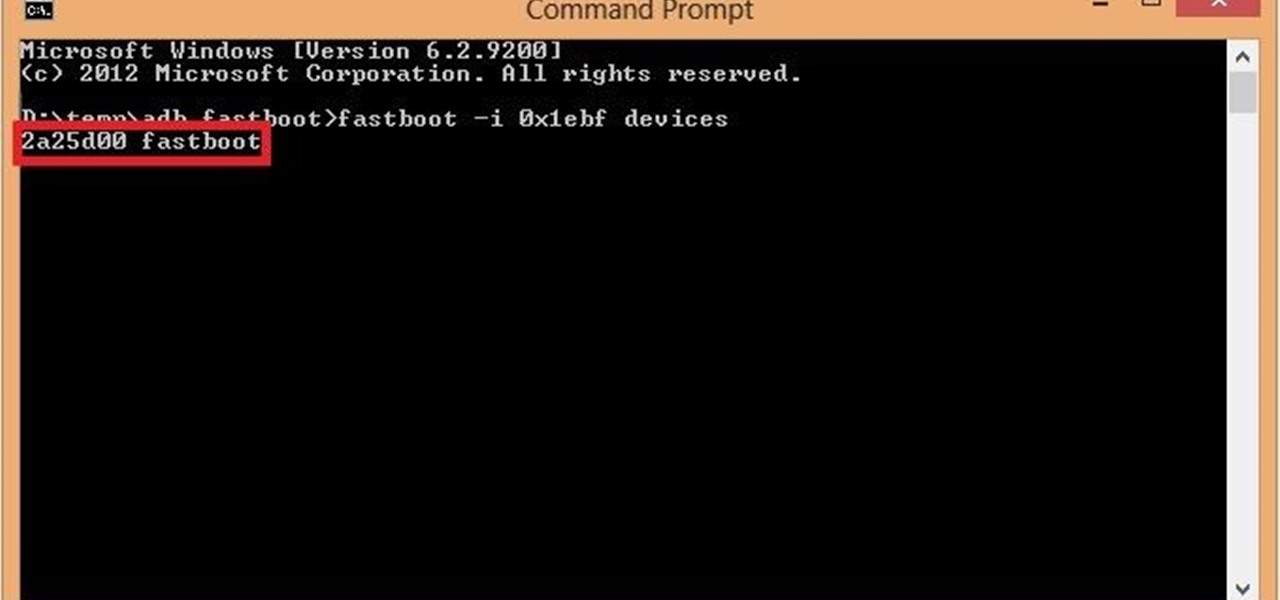
Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing.

Hearthstone is a collectible card game by world-class developer Blizzard Entertainment. It has taken an entire generation of casual and professional gamers alike by storm. So many people play it, chances are you've already sunk some money into it. So, if you're going to pay a little anyway, you may as well get a discount.

This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are generally brief explanations and you might miss something or the other. Moreover, in most of them, ported Clockworkmod recovery has been used which is less stable and lacks features. So keeping your worries aside, look nowhere ...

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

There are many different reasons that you might want to revert your Samsung Galaxy S5 back to stock. The main one would probably be that you need to return your device to the manufacturer for warranty purposes. And if you've used root to modify system-level files and components, you'll need to undo those changes before you send the phone back.

When it comes to squeezing as much battery life as possible out of our smartphones, most people aim for software solutions, or ones that can otherwise be easily managed right from the touchscreen.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

You know how annoyed you get when you put a quarter into the vending or washing machine and it gets stuck? There's a quiet rage that boils inside you. Now, imagine that quarter is a sixty dollar video game, and it's stuck inside your brand new, four hundred dollar PlayStation 4 system.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

Google's Nexus 7 tablet has just been released, and for only $199, it seems like a great deal. Now, some of you are probably immediately thinking that you're going to want to root this thing as soon as possible to install all of your tweaks. Luckily, some clever hackers have already developed a fairly automated solution to rooting the device. Here's how it works. A word of caution however, rooting your tablet will very much void the warranty and there's no 100% guarantee that this procedure w...

If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

This may very well be the most important video series you will ever watch. You may not think it now but the next time you are pulled over as the officer is asking for your license and registration you will will be thinking of these tips and happy you took the 10 minutes to learn them.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade DS-2000 Series Telescope to ogle the universe.

In this video the tutor shows how to mount ISO's using Power ISO software. To do this follow the simple procedure shown in this video. Download the Power ISO program from the link given in this video and install it. You need to purchase the key to install the software or you can use the key provided in this video. Now restart your computer. After restarting open the software and go to mount ISO at the top right corner. Select the image that you want to be loaded. Finally run the virtual CD dr...

In this video the instructor shows how to repair the volume on your iPhone. This video advices caution and is not responsible for any damage caused to your property. While using iPhone people often face different kinds of problems with volume like low volume or no volume at all. If the warranty expires then throwing away the iPhone and getting a new one because of this is not a good idea. To get around this follow the given procedure given in the video. Now open your iPhone and use a safety p...

Some say it is impossible to replace a battery in a PalmOne LifeDrive device, but don't let rumors hold you down. Replacing the internal battery in the PalmOne LifeDrive is easier with a little knowhow. This step-by-step video demonstration will show you the procedure for replacing the battery in your PalmOne LifeDrive PDA. You can use the replacement battery found in the video, or any other replacement battery, the results are the same.

Have a tweaking Zen Vision M? Your battery might need replaced, so do it yourself instead of paying someone else to do it! You don't need to pay an expensive professional when you only need to pay for the battery. This step-by-step video demonstration will show you the procedure for replacing the battery in your Creative Zen Vision:M Portable Media Player. You can use the replacement battery found in the video, or any other replacement battery, the results are the same.

This is just a quick video to help you replace your iRiver Digital MP3 Player's battery. Patience is key in completing this disassembly and replacement, using just a small screwdriver and a few minutes of your time. This step-by-step video demonstration will show you the procedure for replacing the battery in your iRiver H320 or H340. You can use the replacement battery found in the video, or any other replacement battery, the results are the same.

Don't let an overpriced professional take over your Garmin battery replacement when you can do it yourself for a far less price and a higher feeling of satisfaction. Your GPS will thank you with years of use. This step-by-step video demonstration will show you the procedure for replacing the battery in your Garmin iQue 3600 GPS unit. You can use the replacement battery found in the video, or any other replacement battery, the results are the same.

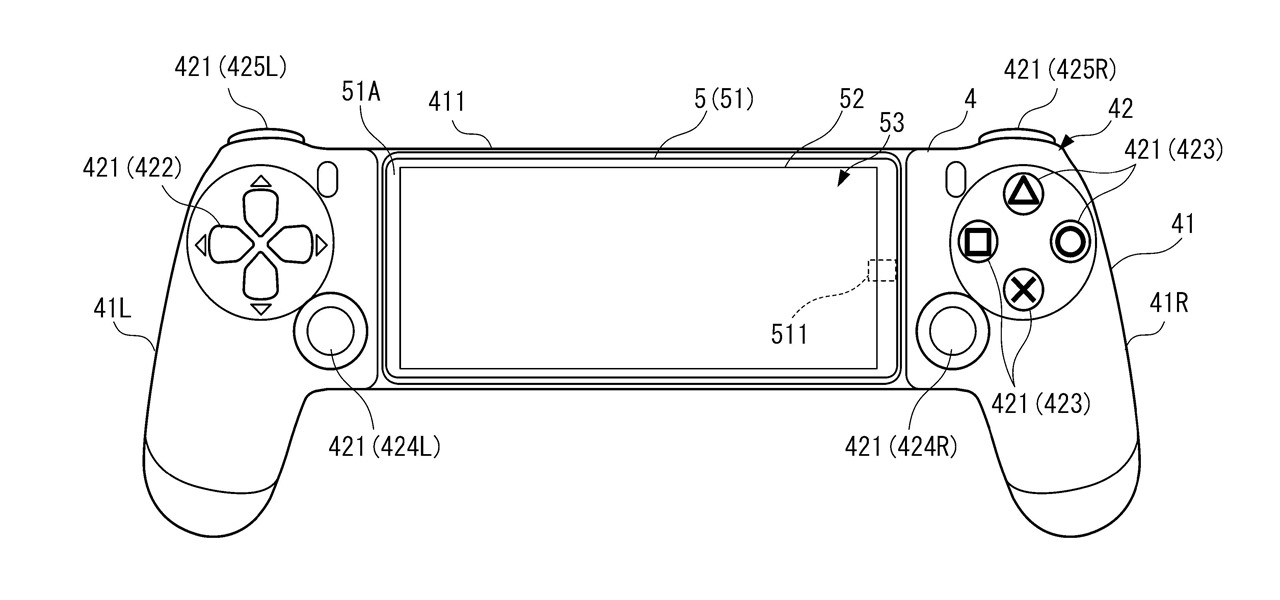
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

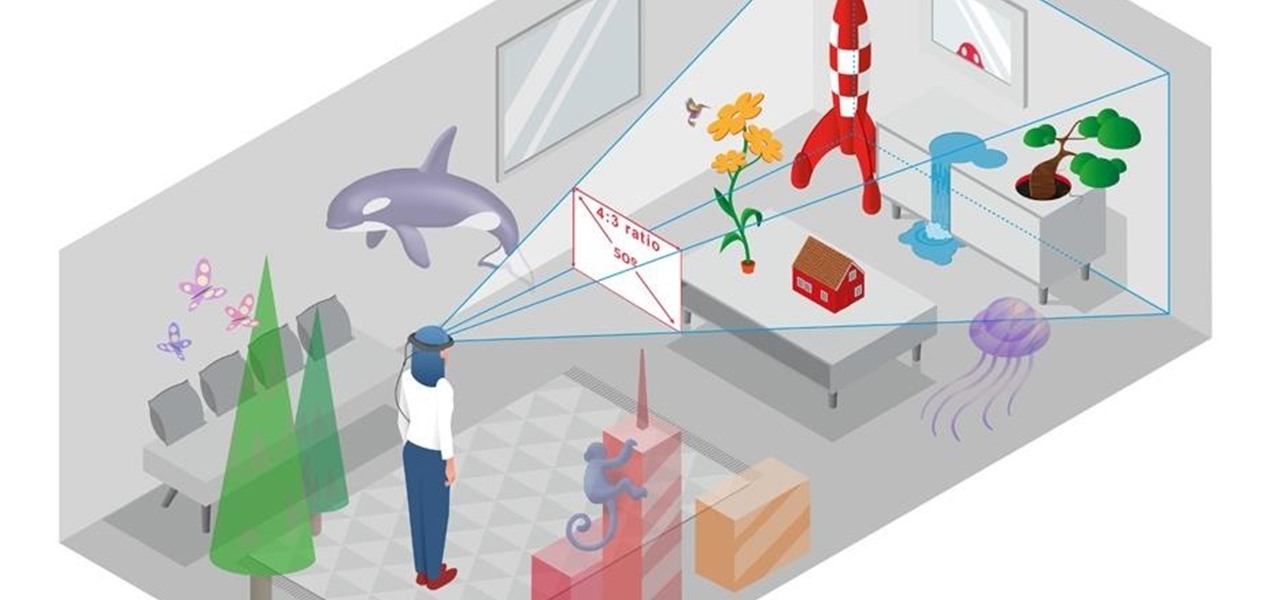
In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

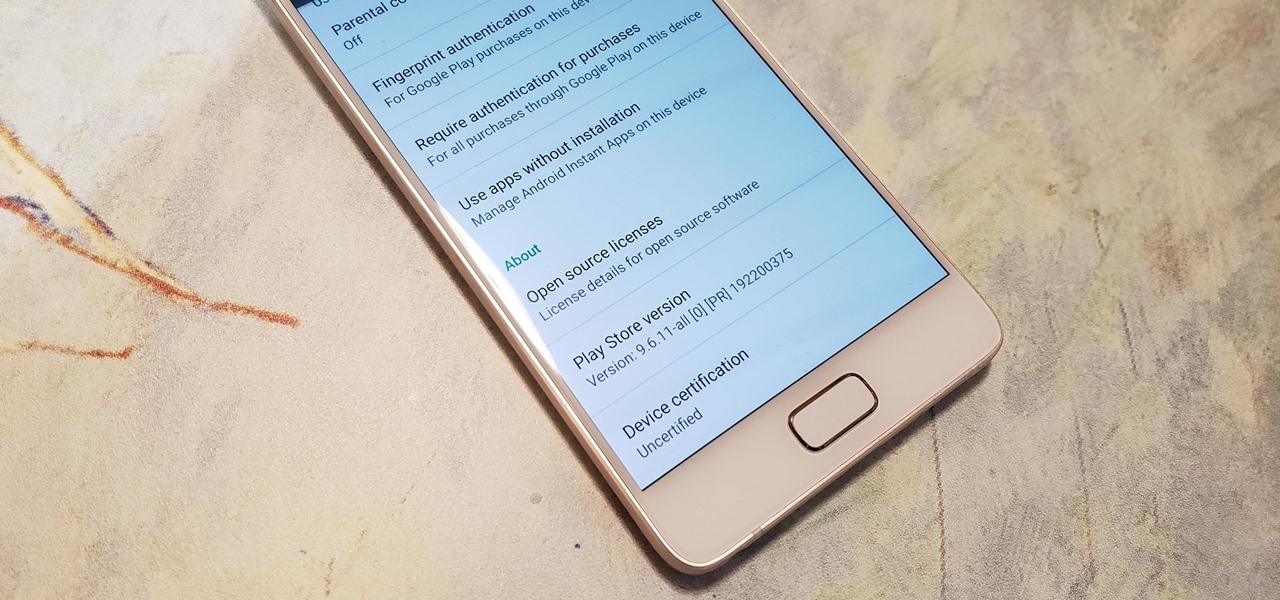
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

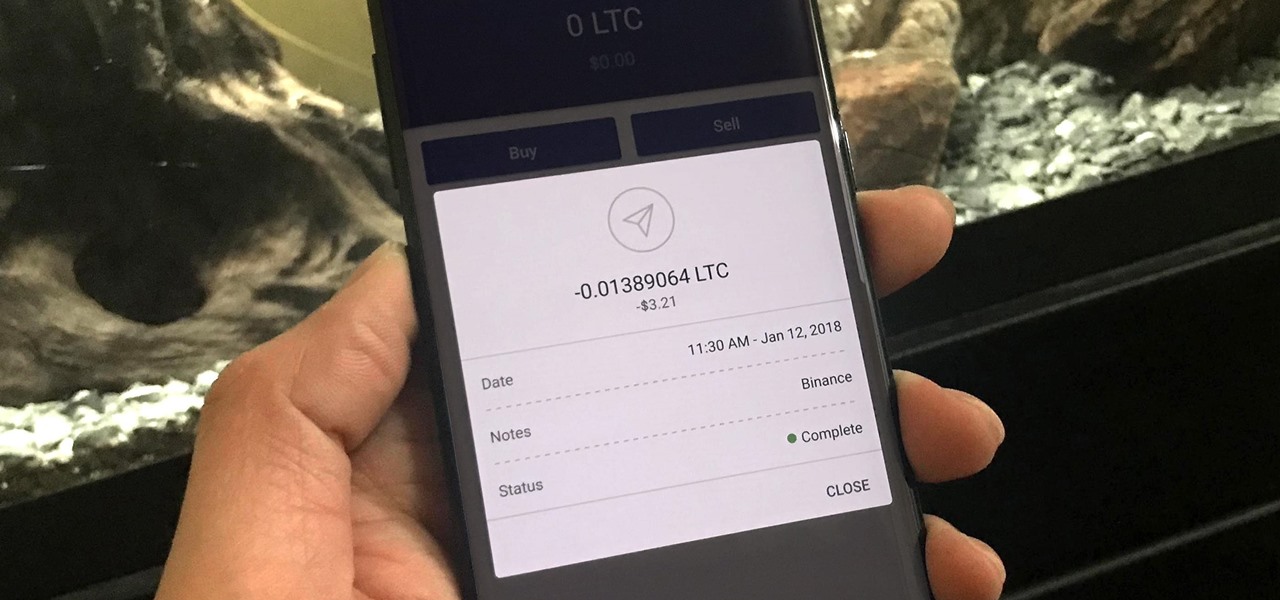
The most convenient way for US users to buy Ripple (XRP) or Stellar (XRM) is through Binance. However, you can't deposit money directly into this app, but you can deposit cryptocurrency like ether or bitcoins to buy other alt-coins. The easiest way to do that is by using Coinbase, the most popular cryptocurrency app.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.