The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Having found success in video games and a hugely popular Netflix series, The Witcher franchise is now on the hunt for the coin Pokémon GO has earned in location-based augented reality mobile games.
While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Reminders a shot, you may want to ditch that third-party to-do app you've been using.
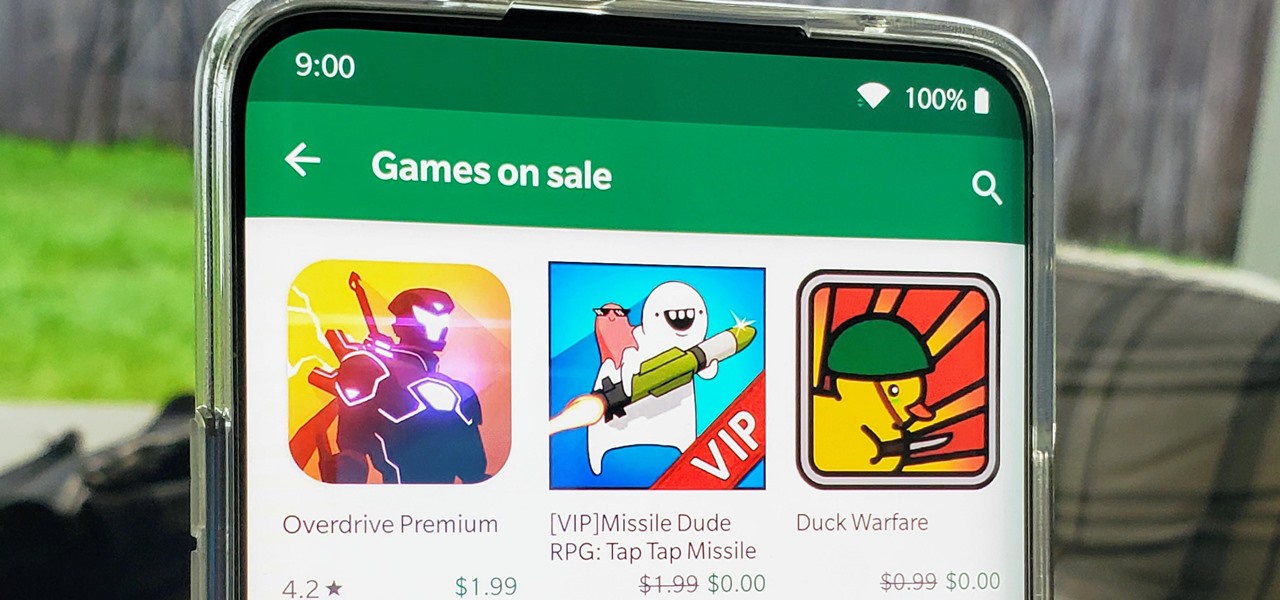
I think we all like the idea of getting paid games for free with minimal effort. Typically, though, anything claiming to help you do that is either illegal or a scam. But there are actually quite a few no-fuss methods that can get you paid games without going too far out of your way. From checking notifications to discovering hidden offers, you might have something waiting for you.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

The Lens Studio creators have published more than 1.5 million AR effects to Snapchat. One of them is Audrey Spencer, who shared her story with us and provided her insights into Lens Studio as a storytelling device. Meanwhile, Snap has added new capabilities to the platform to stoke more creativity from its creators.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Apple announced support for mobile driver's licenses and state identification cards in Apple Wallet back in 2021, and Arizona was the first state to jump on board in 2022. Fast forward to now, and only eight states let you add a driver's license or state ID to Apple Wallet on your iPhone and Apple Watch. It has been a slow rollout, but more states are coming or are at least showing interest.

You may think your iPhone has all the features you could ever need or want, but that may change once you discover the features and services you're missing out on by residing in the United States.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

This may very well be the most important video series you will ever watch. You may not think it now but the next time you are pulled over as the officer is asking for your license and registration you will will be thinking of these tips and happy you took the 10 minutes to learn them.

If you're a Mac user, it's fair to assume that you may be a little skeptical when it comes to Microsoft products. Microsoft knows this, of course. Which is why the company has decided to offer Mac users a free, one-month trial of the latest version of their popular Office productivity suite, Microsoft Office for Mac 2011. They're betting you'll like it so much you'll buy it. And, if you're already a Office for Mac 2008 user, they may be right! Think you're tough enough to resist Steve Ballmer...

Thanks to online music services like eMusic and iTunes, compact discs are becoming a far distant memory, turning local music shops around the country into desolate wastelands. The once mighty movie rental store Blockbuster is now bankrupt because of online streaming services like Hulu and Netflix. And Borders and Barnes & Noble are closing stores left and right thanks to eBooks available on eReaders, like the Amazon Kindle. Everything is moving to the digital world, and everything is finding ...

In this video tutorial, viewers learn how to sync to an iPod or iPhone. Begin by connect the device to your computer using the provided cable. If connected for the first time, an assistant guides you through the setup and registration process. During setup, you will give your device a name and choose which items to automatically save. Make sure that your device is selected in the iTunes window and click on the Music, Video or Photos tab. Then simply select an entire library or specific file t...

Getting your own blog is easier than what you can imagine. Thanks to WordPress. One need not be a techie to follow the steps mentioned below (though certain stages might require third-party advice).

According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the Wi-Fi version or the 3G model.

The iPhone 4 for Verizon is already old news, thanks to Sprint's unveiling of the Kyocera Echo smartphone last Monday.

David Newton, professional photographer and technical editor at Canon Professional Network, teaches you how to customize white balance settings on a Canon EOS camera. The EOS camera have 7 presets plus an auto and a custom white balance setting. You will be using the custom setting. The custom white balance will create a compromise between different types of natural or artificial light existent in the scene. You will need a white piece of paper or a paper with 18% grey color. The last one can...
Requirements: Citizen of the United States

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?
2011 Malibu DownWinder Registration Form
Type: Photography, no visual or graphic art manipulation or HDR Theme: Show Off Your School™
Type: Photography, no visual or graphic art manipulation Theme: Streetscape

Type: Photography, no visual or graphic art manipulation Theme: World's Cutest Pet
The cryptology course went live today and is accepting anyone who is interested for registration. Check out the link for more information and to view the other awesome free online courses!
Healthcare providers have unique desktop environments that range from "Workstations on Wheels" to nursing stations in

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

GIVEAWAYOFTHEDAY OFFERS VISITORS FREE SOFTWARES (MOST CANNOT BE UPDATED IN THE FUTURE, YET ALMOST ALL CAN BE INSTALLED LATER, GRANTED YOU HAVE THE REGISTRATION KEY FOR THEM. THE SOFTWARE'S ARE USUALLY UNIQUE, YET SOME DAYS THERE ARE VARIOUS CONVERTER'S & SCREENSAVERS, WHICH KIND OF MAKE YOU VEER FROM THE SITE PERIODICALLY. BUT KEEP ON EYE ON THE SITE, AS MANY TIMES THERE ARE VERY UNIQUE AND FABULOUS SOFTWARES TO BE HAD.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Shortening URLs has become a necessity in this age of Twitter and limited-character status updates. It not only allows us to cram more words into our oh-so-important Twitter statuses, but it also helps us with a few other things.