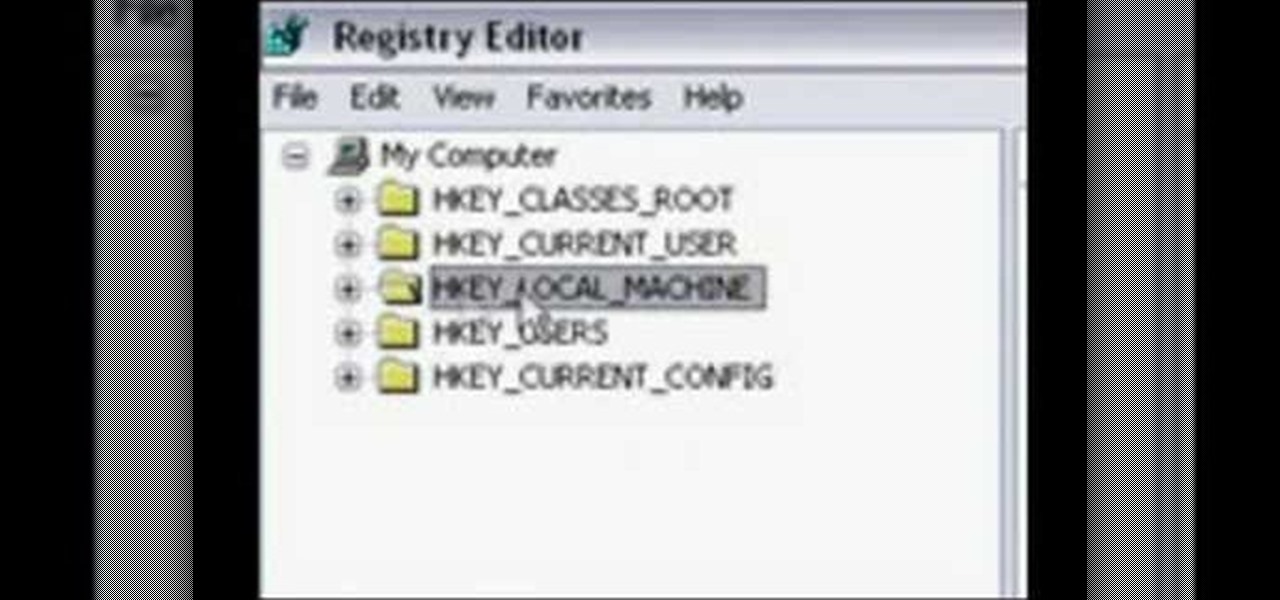
Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

IS THIS ANNOYING? Would you rather not subject others to the virtual VITUPERATION implied by CAPS LOCK? This video will show you how to use these registry tweaks to disable caps lock on your Windows 7 or Vista PC.

Why can't you play DVDs in Windows Media Player? Who knows, but this video tutorial will help you tweak the settings in Windows XP to start watching DVD movies in Windows Media Player 11 in no time. It's a simple registry tweak that enables DVD usage, so you don't have to buy or download another program to play them.
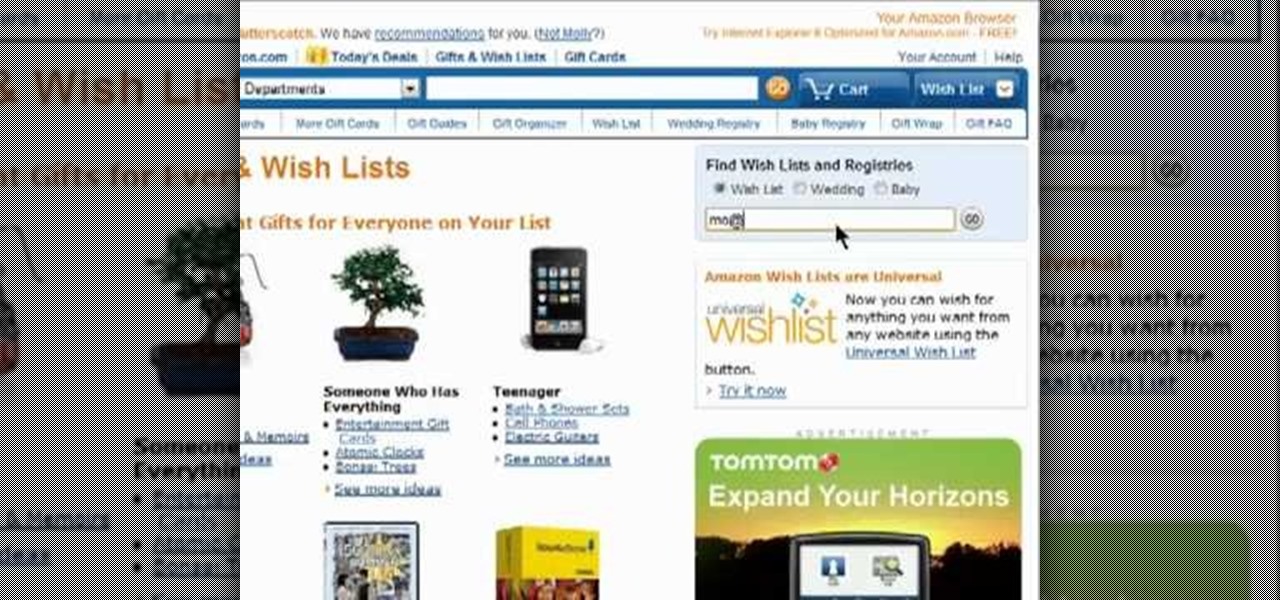
Someone you know have a birthday or wedding coming up? Search Amazon to see if they've set up a wish list (wishlist) or registry! It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started finding wish lists on Amazon yourself, take a look.
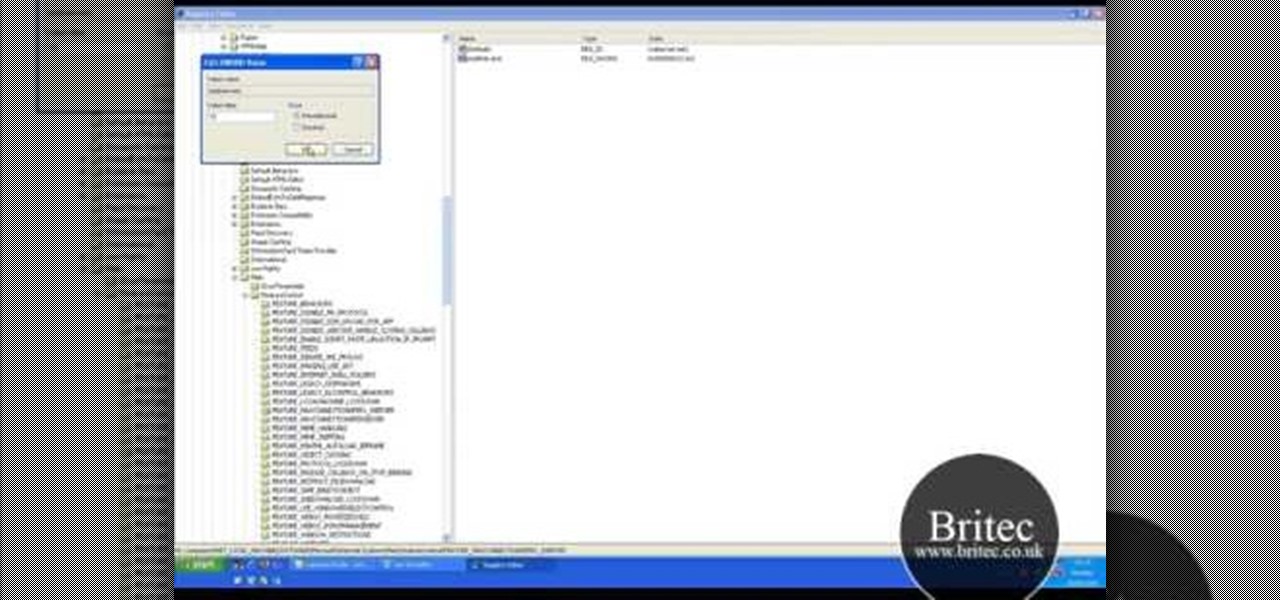
Want to increase the maximum number of possible connections in version 8 of Microsoft's IE web browser? With this little registry hack, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

Want to know how to make HijackThis, the popular malware scanning program, display only malicious registry entries? Learn how to use the Ignore List to acheive just that with this free home computing how-to from the folks at CNET TV, which offers complete instructions on how to tweak HijackThis to make removing viruses and spyware a breeze. For more information, and to get started protecting your own Windows PC from malicious software, watch this handy how-to.

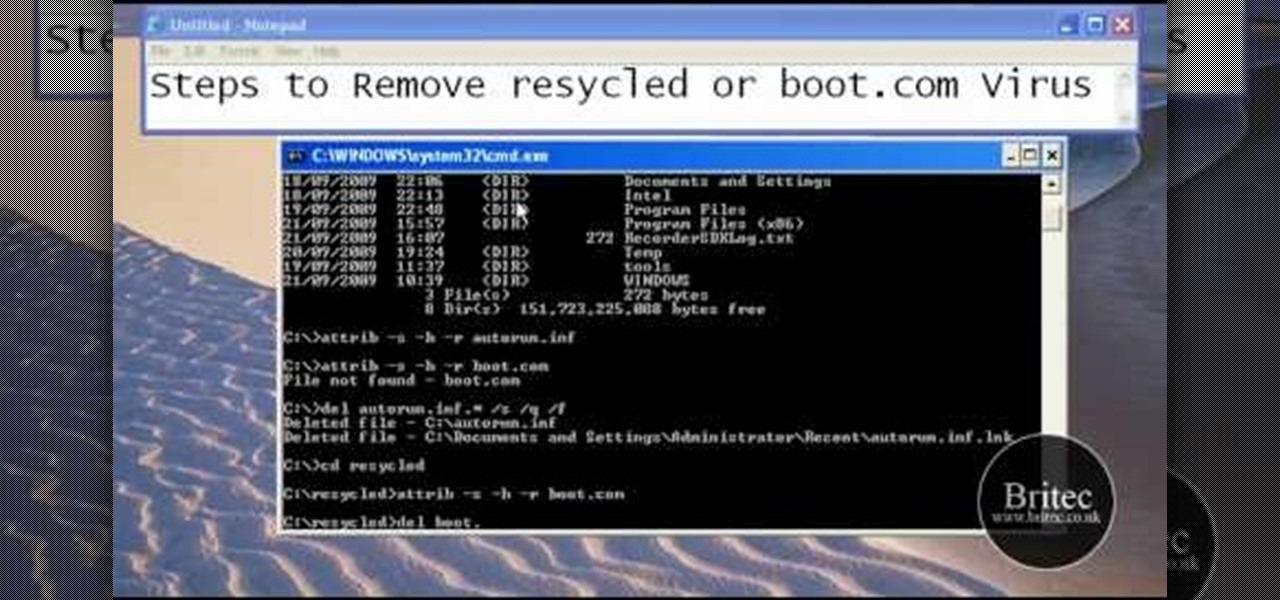
This tutorial describes the procedure to remove autorun.inf and boot.com virus. This virus is commonly called as resycled/boot.com virus, which could damage the system files and may steal important information from the system.This can be removed by any malware / spyware remover like Malewarebytes.

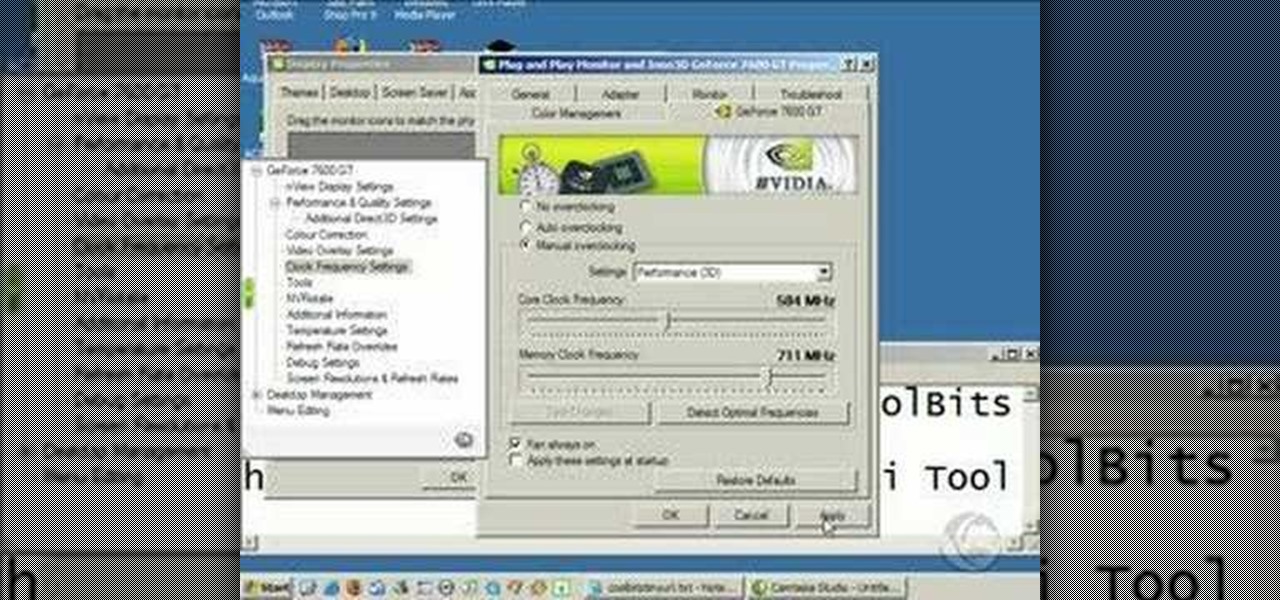
5 minute video on how to overclock your graphics card. Includes installation of coolbits registry mod. Links to featured tools are included in the video.

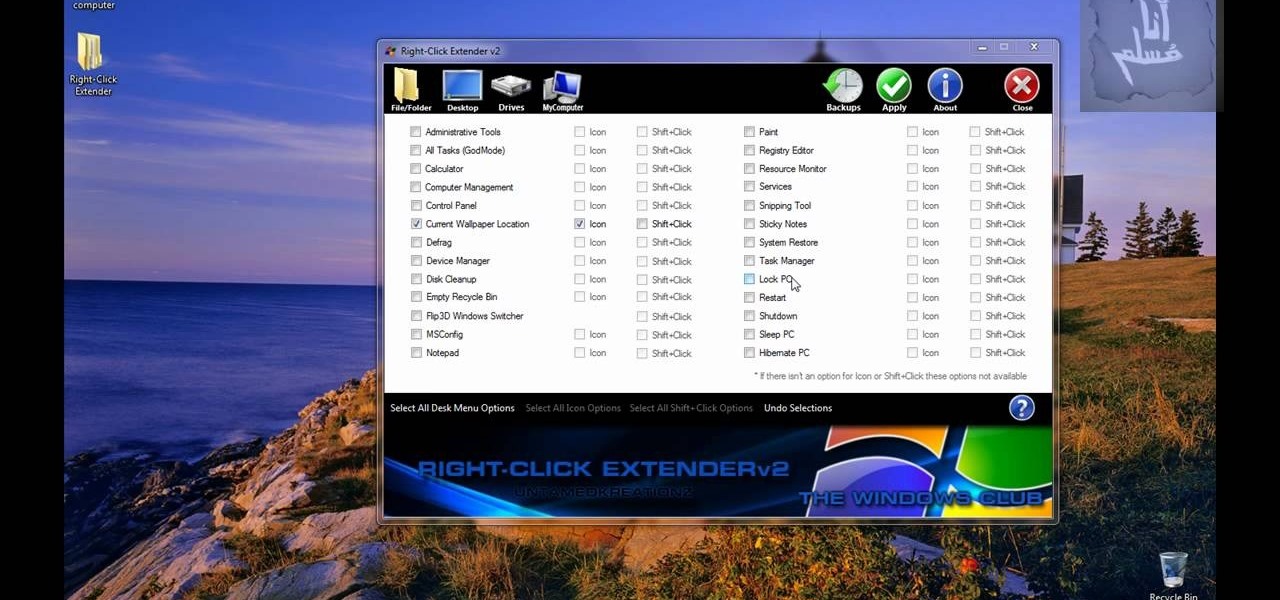
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

In this video, we learn how to change The Windows 7 Start Orb. First, you will need to download Universal Theme Patcher to your computer, which you can find at: Freeware Geeks. Once you download this, install it to your computer and make sure you choose the right type to download. Also, download the registry files from MediaFire, click the "take ownership" option when you right click on this, then double click on it. When the window comes up, click to add the ownership option. Now, go to the ...

This video tutorial is in the Computers & Programming category which will show you how to boot up your computer faster with boot defragment. Boot defragment places all the boot files together in the hard disk making it easier for the booting process to start. Click on start > run, type in 'regedit' and click OK. This will launch the registry editor. Here you double click on hkey_local_machine to open it. Then you double click on software > Microsoft > dfrg >BbootOptimizeFunction Click on 'ena...

Check out this tutorial and make Windows 7 you're own by customizing the log in screen. This is fun to do and will, no doubt, make you feel more connected to your PC.

Steps adopted to bypass Windows Genuine Advantage Notification in Windows NT are:1. Open my computer2. Open the Local Disk (Where the Operating system is currently installed).3. Open windows folder and enter into the folder, system 32.(Shortcut: My Computer>Local Disk C>System 32)4. After entering system 32 (Folder), find and delete the file-wgatray.exe5. After deleting wgatray.exe file, go to the start menu and launch the run application6. In run, type in regedit and click OK,7. In regedit, ...

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

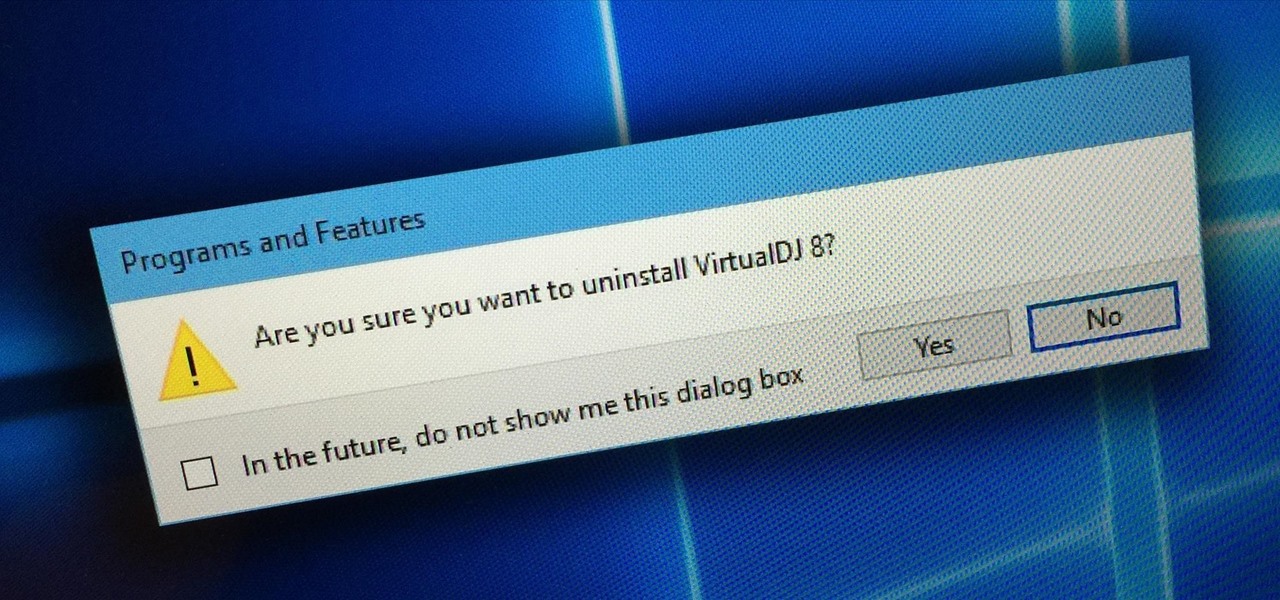
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Level up on Happy Aquarium by hacking it with Registry Helper. Huh? No Cheat Engine? See for yourself. This won't work for all computers, so test it out for yourself.

If you want to stop telemarketers from calling, use this guide and try a multi-pronged approach. You Will Need

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

Start by clicking start and type regedit in the search box. Hit enter and when the screen opens go under hkey current user and click on control panel and then desktop. Under desktop go to menushowdelay. Under menushowdelay right click and then click modify. In the box that pops up set the value to zero and click ok. Then close the registry editor. Next you will want to download ram booster 2. 0. Once you have downloaded and installed the ram booster program you will want to edit your options....

Baby showers are fun ways to celebrate new mommy-hood. You won't want to forget the traditions though. Check out this video before you start planning and make sure you have an nice balance of etiquette and fun.

Privacy is important. Whether its a telemarketer or a crazy ex, sometimes you may need to block someone from contacting you. With this tutorial, learn how to get rid of those pesky callers.

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

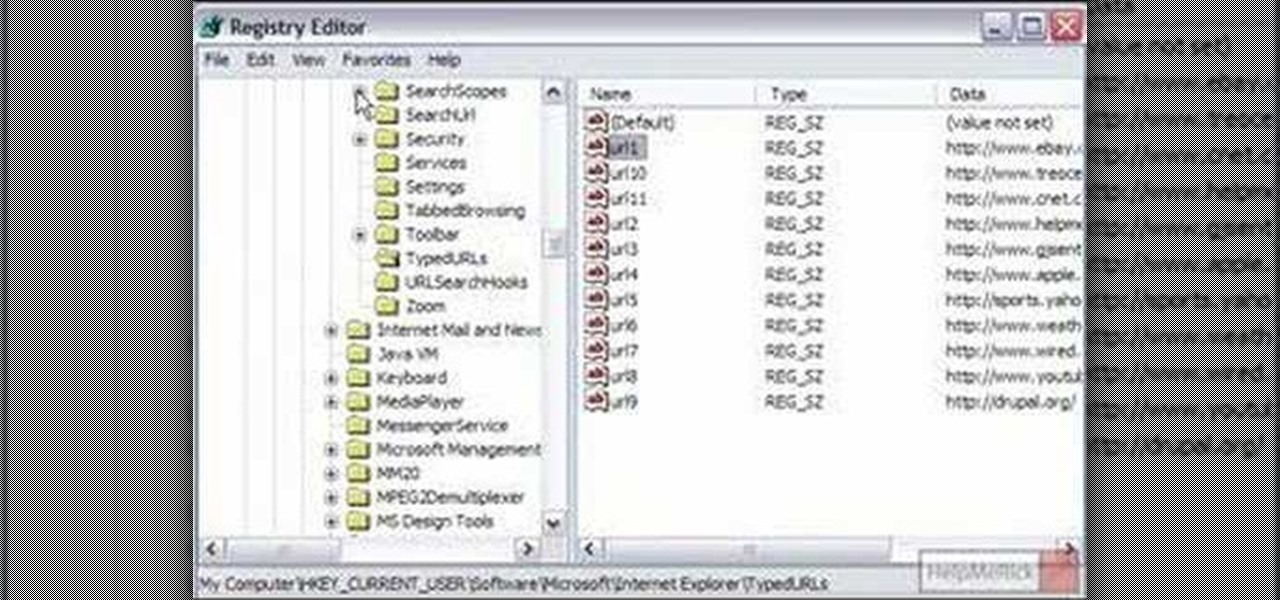
Ever wondered how to go about deleting individual entries from the Internet Explorer address bar? While it's possible, it's not particularly easy. You can do it all at once by purging your entire history through Internet Options or you can hack your Windows registry. For more information, or to try this hack for yourself, take a look!

Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

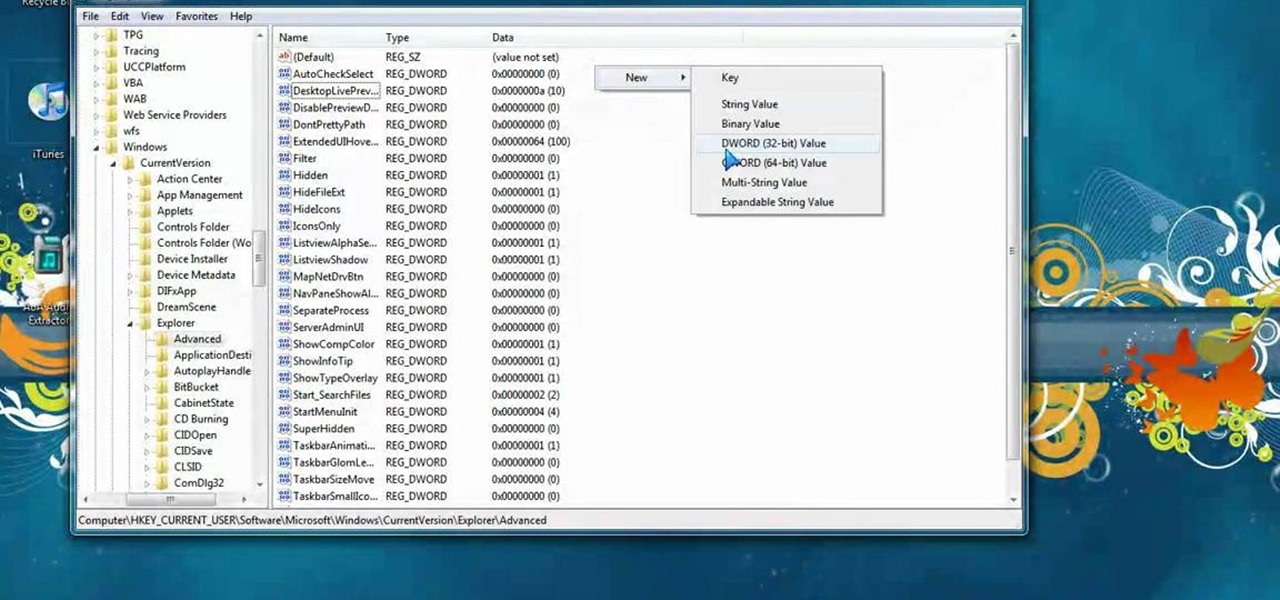
In this video, we learn how to tweak Aero Peek and Desktop Live Preview on Windows 7. First, go to registry editor, then current user, then software, then Microsoft, and go down to Windows. After this, click on current version, explorer, and advanced. Now, right click on the white space and click "new keyword value" and name it "desktoplivepreviewhovertime". After this, double lick and change it to decimal, then change the value data to 10. Next, create another keyword value and name it "Exte...

In this tutorial, we learn how to protect a Windows PC from spyware & malicious software with Dave. You can get spyware from downloading random things, so a great way to make sure you don't download these things, is to use Firefox and search your items before you download them. If you do happen to get these, use SpyBot to find and destroy the viruses you have downloaded. It's free to download, you just have to search it on Google, then download and install it. This will help save your compute...

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

You'd think the ability to block calls from certain numbers would be built in to most phones by now, but that's certainly not the case with the iPhone.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

I love the holidays, but man am I sick of receiving oversized sweaters as Christmas presents. As well as people think they know us, their gifts often say otherwise. Instead of stocking up on useless items and articles of clothing you'll never wear, it's high time to create a wish list that's easily sharable amongst family and friends, and it's incredibly easy to do on Android.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Reports of Zika-related birth defects are coming in at shockingly low rates in Puerto Rico. While that might be something to cheer, one former US government official is saying there could be a nefarious reason for the low numbers.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.