The mere mention of "cupcake" conjures up visions of frosting-topped treats served to partygoers and birthday-havers by the dozens. After all, how many cupcake pans have you seen with less than 12 spots? Sixers are fairly common, yes, but what if you just want to bake one or two cupcakes to enjoy alone or with a pal?

Back in July, Oreo released their newest, limited-edition flavor, Choco Chip. These one-of-a-kind cookies are made up of golden, vanilla chocolate chip wafers with a chocolate chip creme filling.
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

The magic of an ice cold popsicle on a hot summer's day is undeniable, whether you're a child or a kid-at-heart. Neon-colored, store-bought popsicles may have a special place in your memory, but homemade popsicles are pretty hard to beat. Here's how to create delicious frozen treats that will both delight your inner child and tickle your adult taste buds!

If you love sitting poolside with a slice of watermelon, then I've got a real treat for you. Picture yourself cooling off with a slice of juicy watermelon topped with fresh ingredients like soft cheeses, herbs, and fresh summer fruits. Watermelon pizza is a wondrous thing—a creative take on the classic watermelon salad, only pizza-fied!

For those of you that prefer a soft-baked cookie that is fluffy in the middle, using cake flour instead of regular all-purpose (AP) flour is your secret baking weapon. "But I don't have cake flour," you protest. Fear not: if your kitchen is sans cake flour, you can easily whip some up by mixing together AP flour and a little bit of cornstarch for the same results.

Instant ramen makes me nostalgic for my college days, when a bowl of this cheap noodle soup was my go-to comfort food for many all-nighters.

You've probably noticed artichokes at the front and center of your local grocery store or farmer's market recently, as spring is artichoke season; They may look like strange, complicated vegetables if you've never cooked them before.

Making yogurt at home doesn't sound like an easy task at first. We initially saw it as detailed, hands-on, and precise—a process that required special equipment, specialized (and expensive) live-culture bacteria, and loads of yogurt knowledge.

I know I'm in the majority when I say that grilled cheese sandwiches are one of life's simplest and best pleasures: gooey, rich, melted cheese, sandwiched between two perfectly-buttered pieces of toast... perfection.

Let's set the scene: you're at home, it's late in the evening, and you have a hankering for those deliciously decadent chocolate-wrapped squares of ice cream goodness. You could drive to the store and pick up the usual pack of Klondike Bars in the ice cream aisle... or, you can easily make these babies in the comfort of your own home with only three ingredients for a fraction of the cost—in any flavor you want! The choice is obvious. So, without further ado... Ready, set, Klondike!

There are few things more annoying in life than getting interrupted—especially when you're in a groove, jamming out to your favorite song. If we can all agree on that sentiment, then why is it that our phones mute the music we're listening to for a few seconds whenever a notification comes in?

The Oculus Rift is finally shipping to customers in more than 20 countries, and we're getting a good idea of how the device holds up from the initial reviews. You'll see some common threads throughout: along with an impressive virtual reality experience, the device is very comfortable with a solid design.

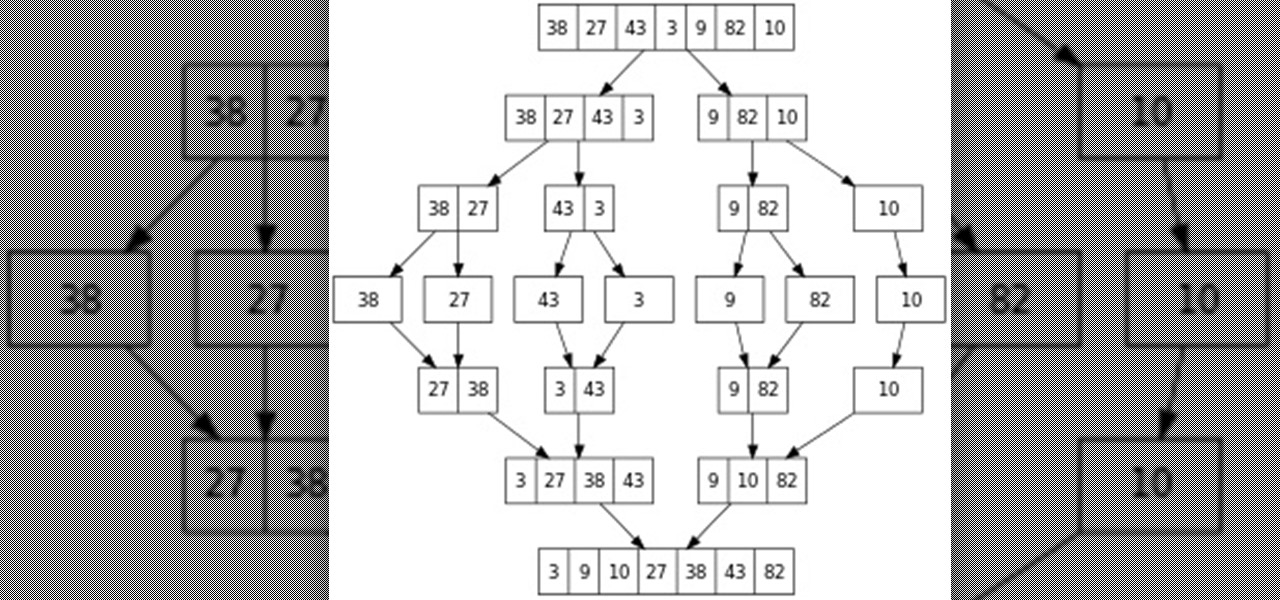
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

My Cuisinart ice cream maker was a wedding gift; it wasn't something on my list, but I jumped up and down with delight when I unwrapped it. I never would've purchased this appliance on my own because it didn't seem practical, yet I loved the idea of making homemade ice cream.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Switching your favorite facial cleanser isn't an easy choice. Since everyone's skin type can range from dry, to oily, to some complicated combination of both... well, let's just say that the conventional wisdom is to stick to what you know works.

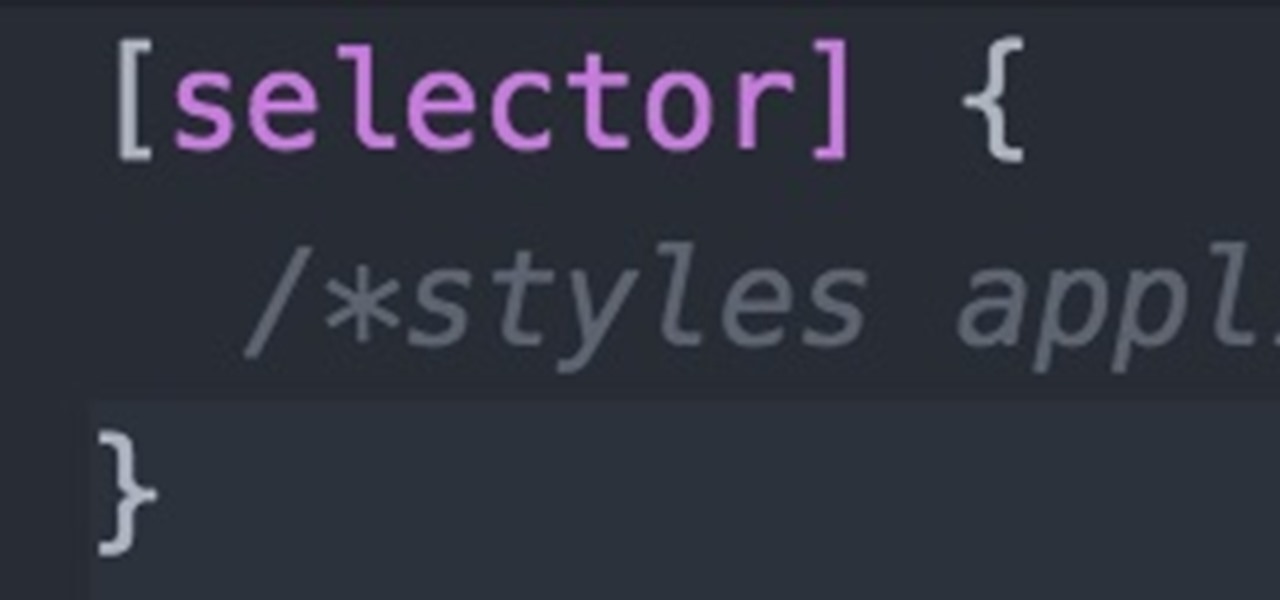
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one tiny, inconspicuous tool that solved all of these problems: the coffee grinder.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Alcohol isn't exactly considered a healthy lifestyle choice; more often than not, it's associated with empty calories and bad decisions. But that doesn't mean there aren't a few benefits to drinking in moderation. In fact, gin is a liquor with a wealth of potential benefits to offer. So read on, and discover ten ways in which gin might actually be a good drink for you.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Hair dyers are pretty straightforward tools, but they can actually do way more than just dry your wet hair or defog your bathroom mirror. From the kitchen to the backyard, a blowdryer can help you solve common problems around the house and beyond, and here are our 10 favorite uses.

Dropping upwards of $60 on a new game can really break the bank, and being a struggling college student leaves me having to decide whether to pick up the latest title or, you know, eat. But often my more primitive urges win out, meaning the only way to enjoy the latest and greatest games are vicariously, using increasingly-popular live streams.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Although pasta is a remarkably simple dish, I find it to be one of the most aesthetically appealing foods. The noodles—especially thicker iterations, like linguine and fettuccine—are graceful and luxurious. Add in some sauce coating the noodles, and a sprinkle of Parmesan or a drizzle of olive oil, and pasta single-handedly reminds us of a basic tenet of cooking: sometimes keeping it simple is the perfect way to go.

If you have a ton of photos and videos on your iPhone, backing up to iCloud is probably a no-go since it only provides 5 GB of free storage. Yes, you can buy more storage, but who wants to do that? And what happens if you run out of storage, stop backing up, and your phone gets lost, stolen, or damaged.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

While I frown upon any form of uneaten cookie, sometimes we overestimate our late-night cravings for baked goods leaving us with extra cookie dough at 4 a.m. If you're in the privileged dilemma of not having enough excess dough to make another batch of cookies but just enough left over that you can't justify tossing it, don't fret. Here are five effortless and unexpected ways to salvage it.

Any bObsweep vacuum needs regular maintenance at home. All owners should know how to change and clean the main and side brushes, empty the dustbin, and replace the filters inside.

In the realm of Android mods, none is more powerful than a custom recovery. This is installed in place of the stock offering, and it lets you back up your entire system, flash mods, and install custom ROMs.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

When I was a kid, there was just pizza. You ordered from whatever nationwide chain was near you and they made your pizza in an oven. There certainly weren't these highfalutin pizza subsets that have more choices than a cheese shop. Wood-fired, brick oven, artisanal, make-your-own — it's enough to make you long for simpler times.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!