
How To: Use Social Engineering to Gain Unauthorized Access to a Hotel Room
Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.


Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Cookies for breakfast seem like a clear dietary no-no, but these three-ingredient breakfast cookies are easy, healthy, portable, and can be made in advance. They're also dairy-free, egg-free, and have no added processed sugar, so they can also be called allergy-friendly cookies. If you use gluten-free quick oats in this recipe, they are also gluten-free breakfast cookies! Besides all of those reasons, these cookies are only about 50 calories each when they're made with just the original three...

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

When you think of nail polish, it's probably almost always in the context of a manicure. I mean, that's what it's made for, right? But there are plenty of other things you can use clear or colored nail polish for besides painting your nails.

MAC addresses (not to be confused with Macs) are unique identifiers assigned to network devices in order to access the internet. Hotels use these Mac addresses in order to check if a registered patron has agreed to their terms and conditions, how much bandwidth is being consumed, and of course, whether they've paid or not.
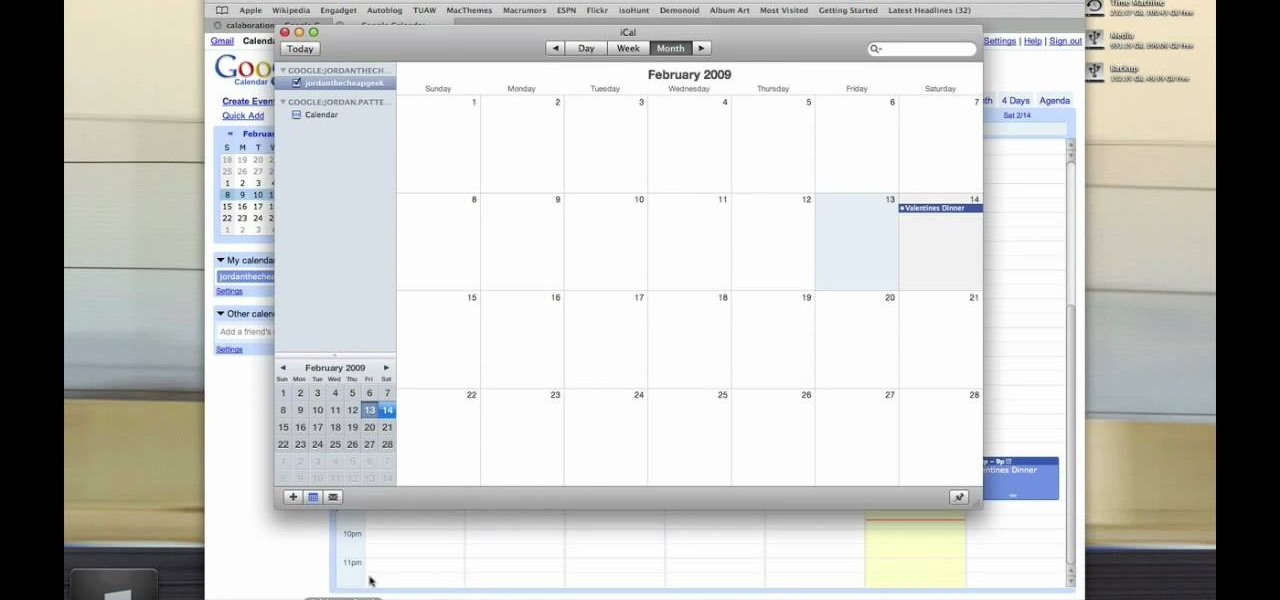
Jordan Patterson the Cheap Geek has made a video showing you the steps to sync your contacts and calendars on three mobile devices together, the iPhone, a laptop running Windows, and a Mac running OS X utilizing a few downloaded programs and Google Calendar. First he shows you how to sync calendars on the Apple computer, by downloading a program from Google code called collaboration code, and then running it. After putting in his g-mail account information, he tells the program which calendar...
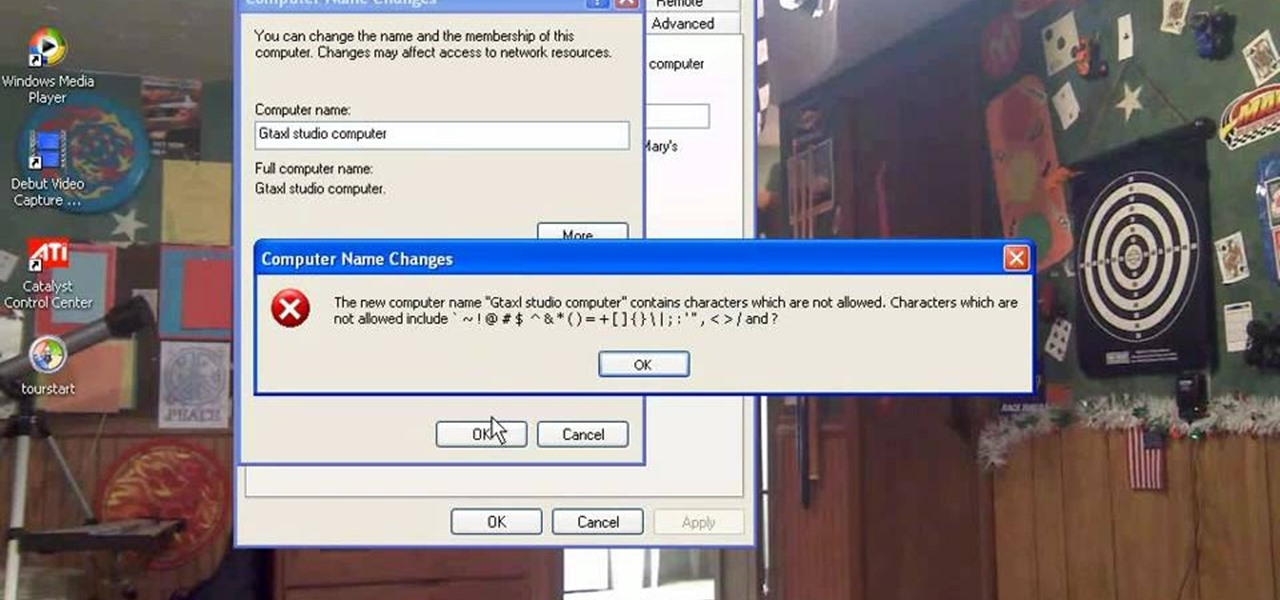
This how-to video explains how to changing the name of a computer, workgroup in a network and the description on a Windows XP.

Ready to rock and roll? You don't have to listen to music through those teeny tiny computer speakers anymore! Check out this cool tutorial, and learn how to connect stereo speakers to your laptop or PC and get the most out of your music.

Paula Deen of Get Cooking will show us how to make peach cobbler. Ingredients are as follows: 1 1/2 cup self-rising flour; 8 tablespoon or 1 stick of butter; 1/2 cup of water, 2 cups sugar, divided; 4 cups peeled sliced peaches; 1 1/2 cup milk; ground cinnamon

The bigger the group chat, the harder it is to follow. Messages start flying one after the other, and before you know it, you're hopelessly lost in the conversation. With most chat apps, there's nothing you can do, other than telling your friends to slow down a bit. But on Telegram, you can make them slow down.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.
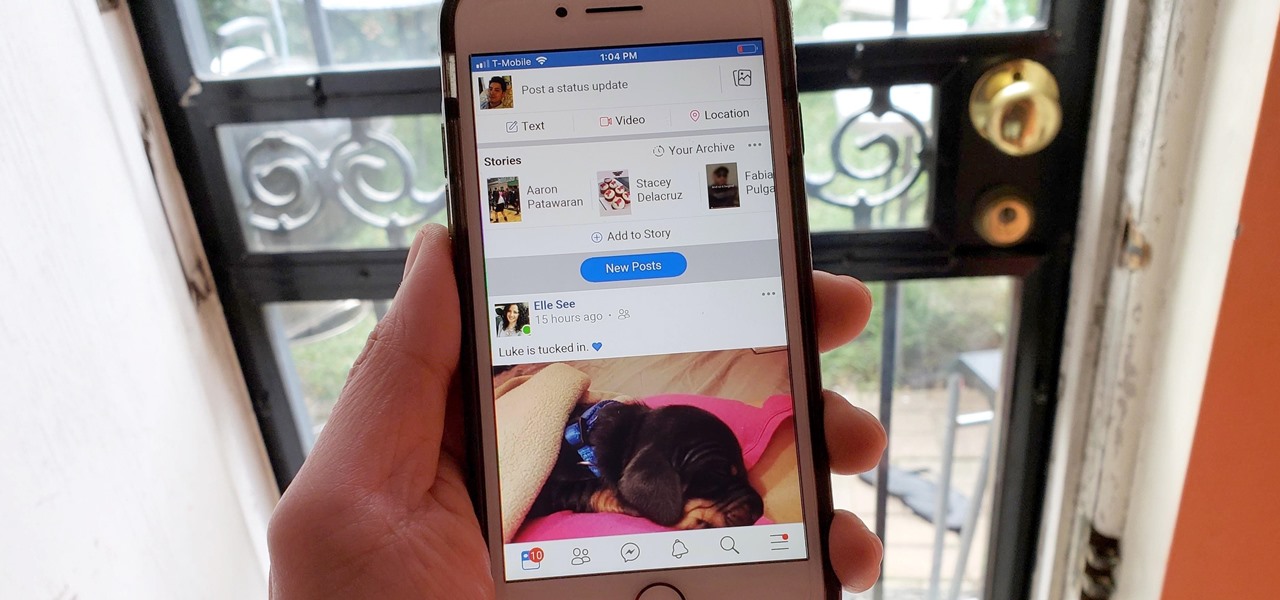
In an ongoing effort to improve its services and become more accessible to users from all regions, Facebook has released a streamlined version of its social media app. Though the leaner Facebook Lite is only officially available in Turkey for now, there's a simple workaround you can use to get the app in any country.

While WhatsApp remains one of the world's most popular messaging apps, you could only call or video chat with one friend at a time. To group audio or video chat, you'd have to use a different app, but that's no longer the case. Announced on July 30, 2018, WhatsApp now lets you group audio or video call with up to three more users on Android and iOS.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

By default, when you receive a FaceTime video call on your iPhone, the speakerphone kicks in immediately after answering unless you're wearing headphones. It's the exact opposite when it comes to FaceTime audio calls, but it's pretty easy to remedy if you'd rather have the speakerphone kick in instead of the built-in ear speaker.
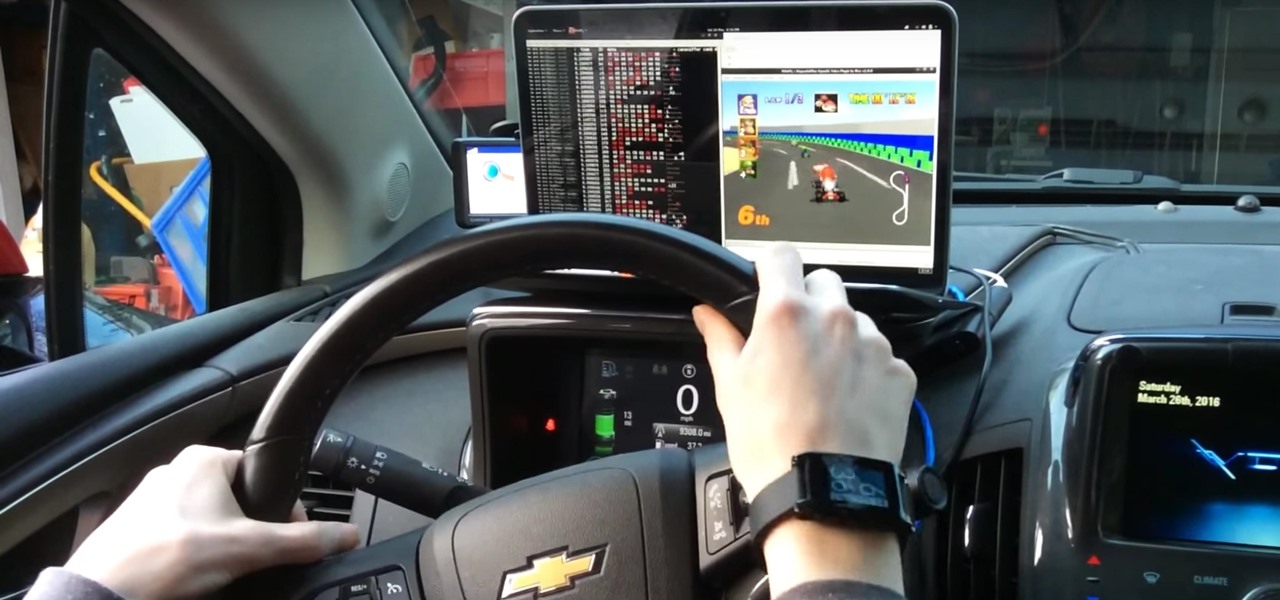
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

360world, a Hungary-based tech company involved in motion control and augmented reality, released information today about their latest products, the CLAIRITY HoloTower and CLAIRITY SmartBinocular. These tools are designed to bring augmented reality into the hands of air traffic controllers, via Windows Mixed Reality, to greatly improve their workflow over tools already in use.

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

Android's Google Play Games app has let you track your feats and accomplishments in the games you play for quite a while now, but for some, the immersion experience might be broken after you finish dominating a game only to see your regular-ass name from your Google account on the leaderboard.

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Since version 4.4 (KitKat), Android has taken the album artwork for any song that's currently playing, as well as videos, podcasts, and other media, then used it as the background image for your lock screen. While many users have enjoyed this little tweak, others aren't quite as fond of it.

Mac keyboards are great when listening to music or watching a movie, since you can control what's playing without going back into iTunes or QuickTime Player. However, when you're using an app like Photoshop that uses the F7, F8, and F9 as shortcuts, it gets pretty annoying to have to hold down the Fn key. Why can't you just hit the back, play/pause, and skip buttons alone?

Google debuted YouTube Music Key in November, and for $10 a month, this essentially turned YouTube into a music streaming service. With ad-free music videos and background audio playback, YouTube serves as a viable alternative to Spotify or Pandora for Music Key subscribers.
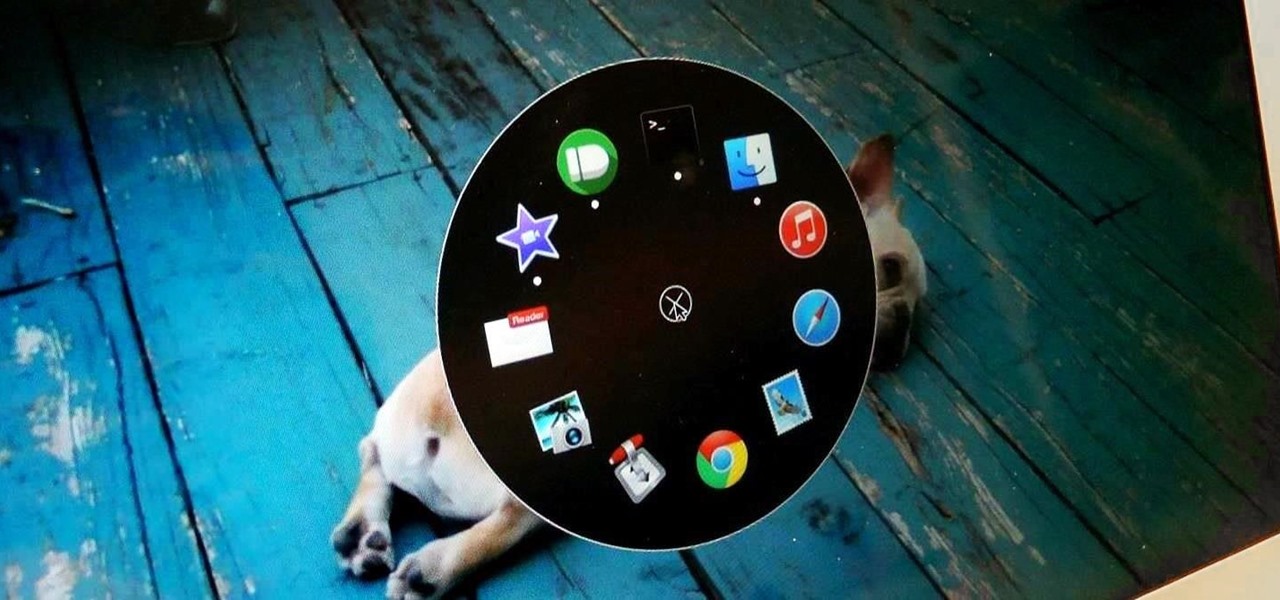
The dock has been a staple of Mac OS X since its creation and not much has been needed to improve its functionality, but when you add theming to the mix, you can run into some issues.

Using a combination of my phone, laptop, and an arsenal of apps and plugins, I can send pretty much anything to my Chromecast. However, nothing is ever perfect, and the file type that was still giving me headaches were torrent and magnet files.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

With Halloween fast approaching, social media sites are abuzz with ghosts stories and pictures of cool costumes. By contrast, regular photos just seem to be lacking that macabre feel.

Even the best-maintained kitchens occasionally get a fruit fly infestation. These critters descend, lay eggs (up to 500 at a time!), and then disappear usually only after extreme cleaning efforts (i.e., finally attacking that weird puddle of goo behind your refrigerator).

A huge chunk of my life revolves around my computer, and whenever I'm on my laptop and get a text message notification on my phone, I find it extremely distracting to stop whatever I'm doing to hunt it down. That's why I'm a big fan of text messaging via my computer.

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.
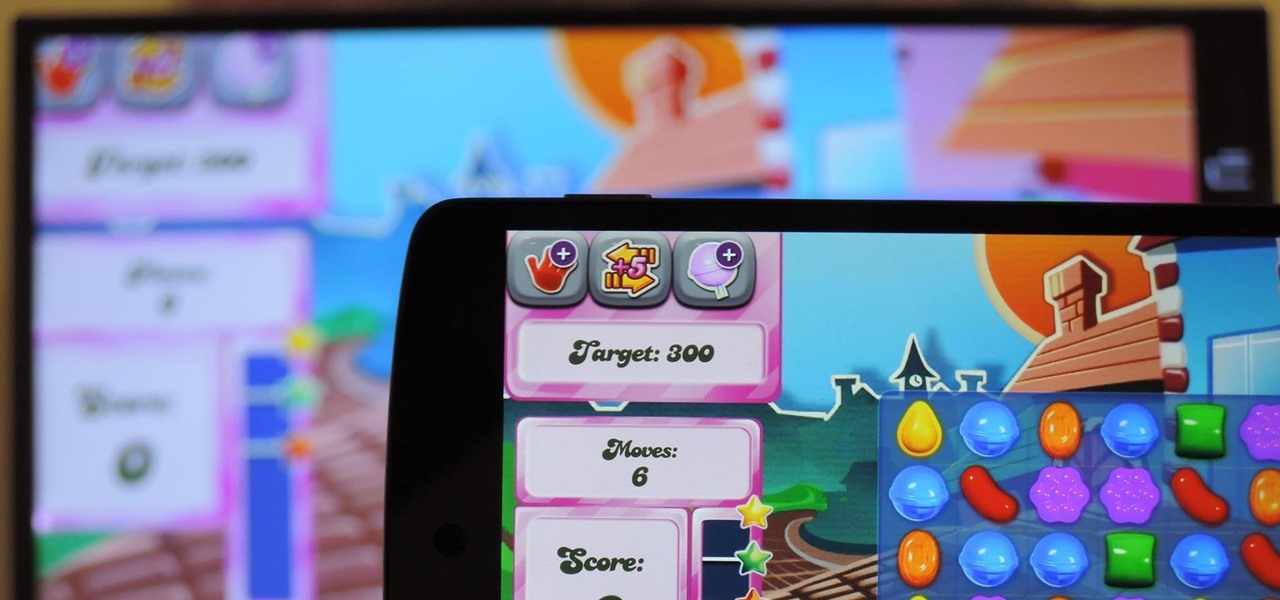
With Google's recent release of the Software Developers Kit for Chromecast, Android gurus now have a roadmap of sorts to guide them in adding Chromecast functionality to their apps. The results are beginning to pour in.

"What is dead may never die." That's easily one of the best lines (and episode title) from HBO's Game of Thrones series. While the saying may ring true for the Ironborn, it's not quite as catchy when it comes to batteries.
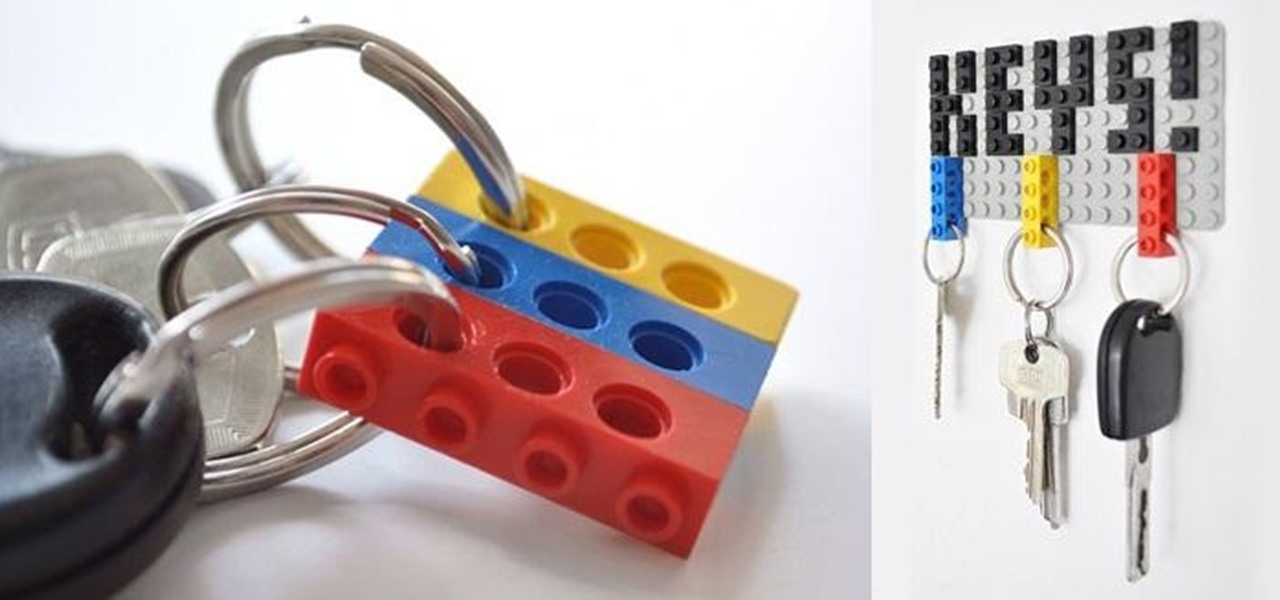
LEGO may no longer be in its heyday, but those colored building blocks of joy can still make some really cool and creative things. I mean, take a look at these pieces from LEGO artist Nathan Sawaya. While making something like that is undoubtedly impressive, it could be just a little too difficult for the common LEGO enthusiast—and expensive (LEGOs aren't cheap these days). So, for the regular LEGO-builders, usefulness is more important that extravagance.

Touchscreens are all the rage these days, and it seems that the stylus has become a relic of the past thanks to newer and better fingertip responsive smartphone displays. But when it comes to phablets like Samsung's Galaxy Note line, the added S-Pen is definitely helpful for more accurate and precise actions (and a less greasy screen). Of course, there are disadvantages of using an S-Pen too, one being hardware issues. Unlike your finger, the S-Pen can malfunction and become a huge problem, n...
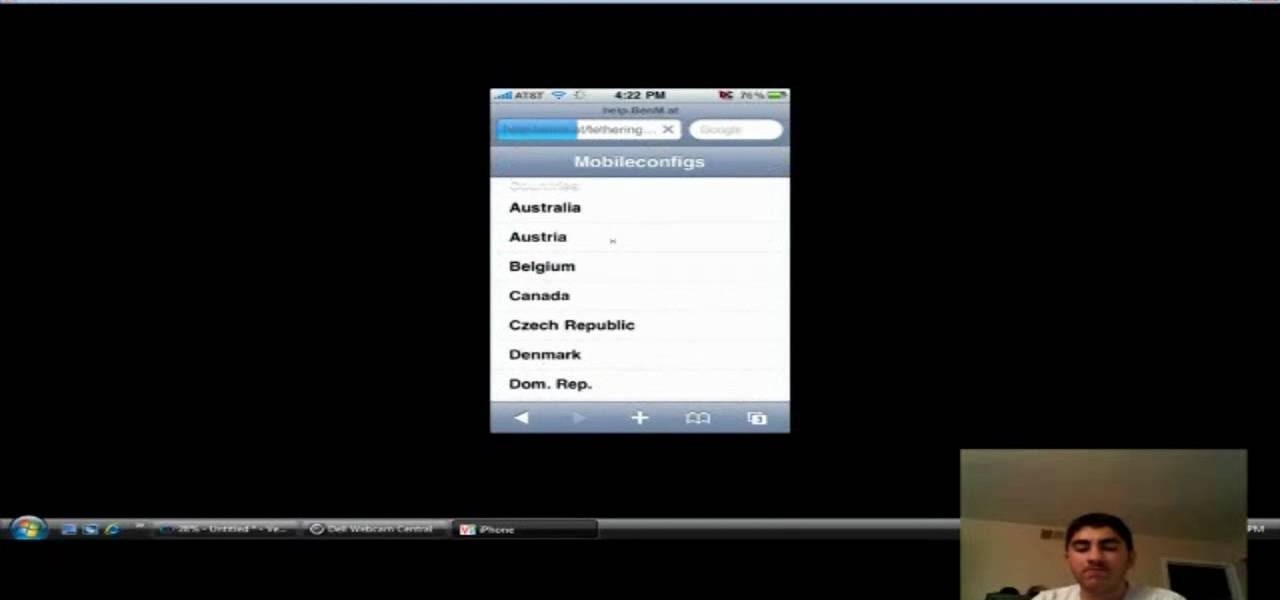
This video shows you how to enable internet tethering on your iPhone 3GS. What are the perks to internet tethering? Well, for starters, it allows you to log into the internet from just about anywhere by sharing your laptop's internet connection. This will also allow for faster browsing speeds if you don't have the fastest cell service at the time.
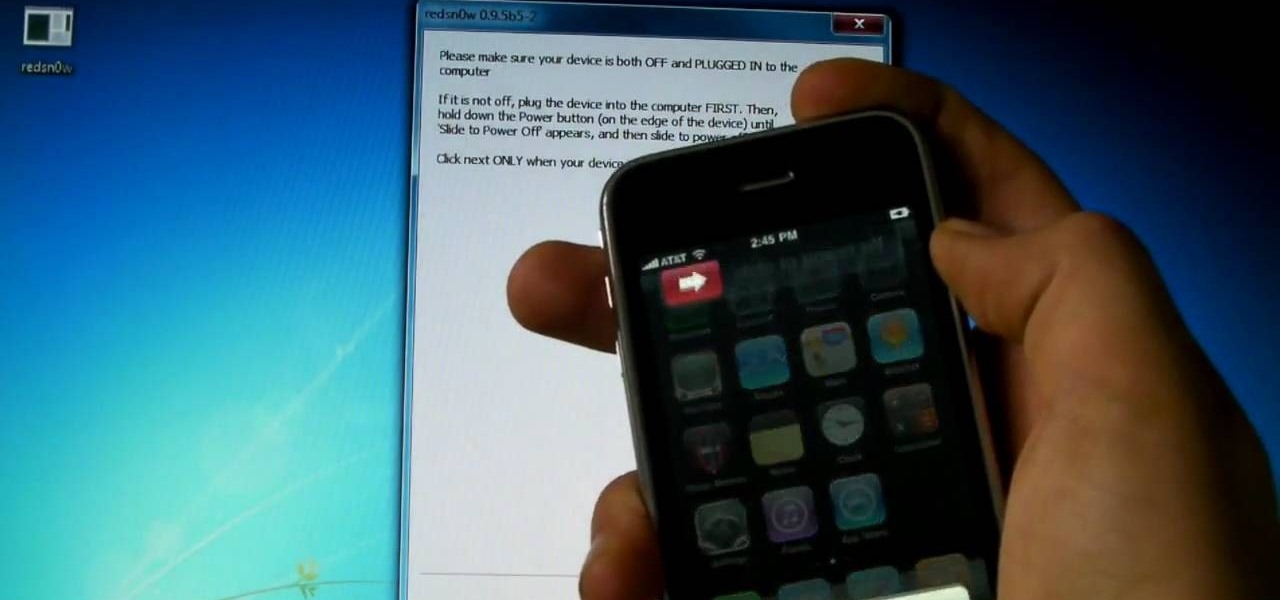
As of today, there are no legal barriers standing between you and jailbreaking your iPhone, iPad, or other mobile device. Hooray! If you were afraid of Apple coming to your house at night if you jailbroke your phone, you can finally let go of the fear and make your iDevice the beast it should have been all along! This video will show you how to jailbreak a iPhone 3G or iTouch 2G with iOS version 4.0 or 4.0.1 using Redsn0w. Now you can fully enjoy your Apple device.

Kevin demonstrates how to make a paper frog. Take a regular sheet of construction paper. Fold the outer ends towards the center forming a triangle. Fold a crease at the base of the triangle and cut it out. Open the folds and you can observe two creases. Create two X-shaped creases by bending the opposite corners. Hold the triangles on the side of the X and squash it down such that the other two triangles meet. Repeat the process on the other side. This forms a square with a diagonal cut conta...
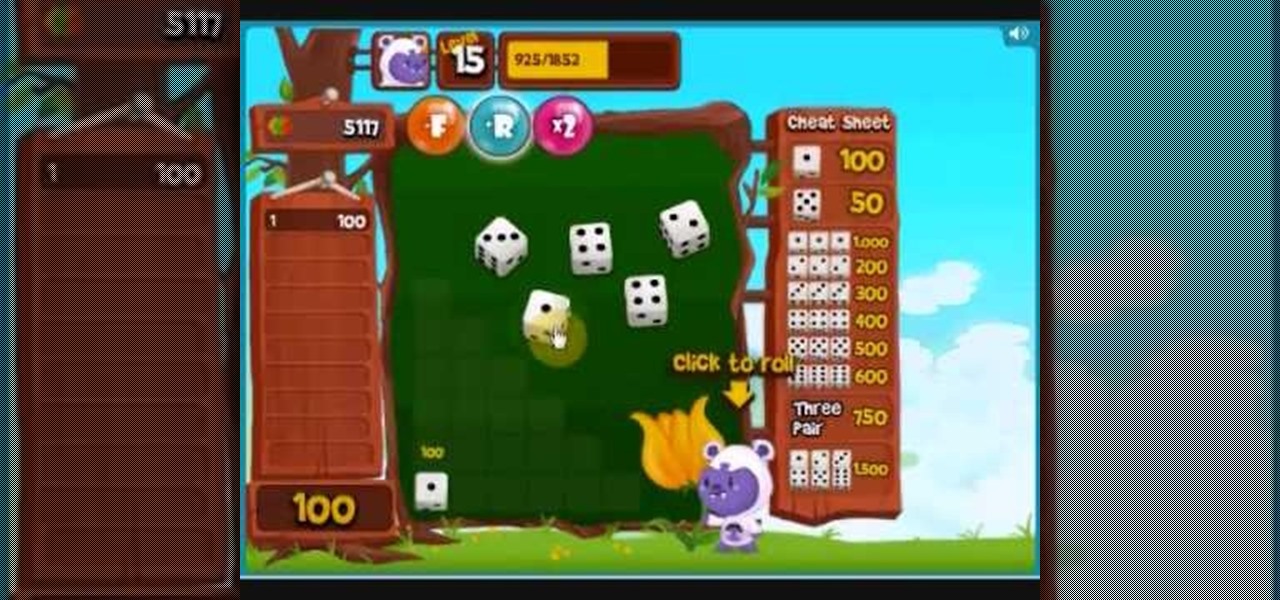
Super Farkle is here! Better than the regular Farkle, Super Farkle has more everything to enjoy on Facebook. If you haven't played Farkle before, you don't know what you're missing. It's one of the best dice game on the web.