Taking photos is great, but what about being able to share them with the world wide web? There are countless of image hosting options out there to get your photos on the internet, but imgur is probably one of the simplest and easy image uploading sites out there.
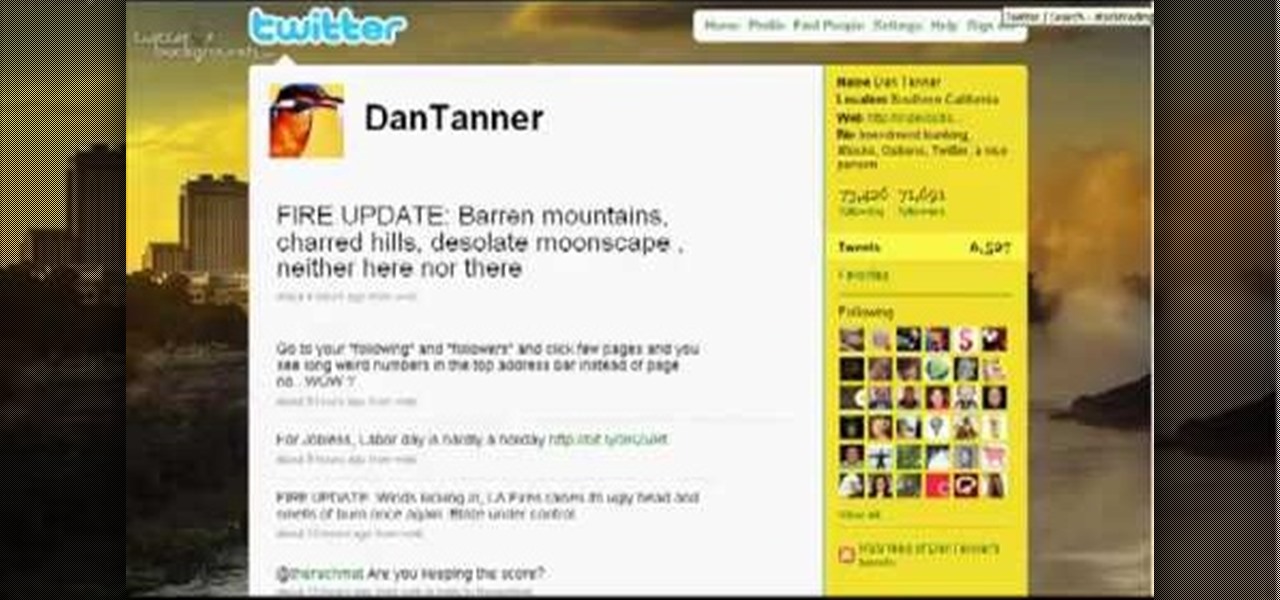
Are you a Tweeter? One of those Twitter maniacs? Or are you just starting out with free social networking service? This video tutorial will help you Tweets by showing you how to find and get more followers on Twitter.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install UbuntuOne on Ubuntu Linux.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.
Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this video tutorial, you'll learn how to use the new CSS, or Cascading Style Sheet, management tools in Visual Studio 2008 in the service of enhancing an existing stylesh...

Insects can be a big nuisance while you are hiking. Different parts of the country and different parts of the world have different kinds of stinging, nasty, biting insects. Preventing insect bites is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this how-to video.

Hiking is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: pace yourself, don't take too many long breaks, maintain good posture, keep a light spring in your step, and bring plenty of food and water. John Flaherty, the instructor of this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and ...

Packing for a hiking trip is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take Action: pack heavy items at the bottom, bring extra water, and include a first-aid kit in your pack. John Flaherty, the instructor in this how-to video, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and biking services for those wanting to be closer...

Breaking-in hiking boots can be a pain. Get tips and advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: use more time to break in bigger boots, wear boots around the house first, and avoid long hikes. John Flaherty, the instructor in this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and biking services for those w...

Picking hiking gear is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: purchase a quality backpack with a good hip belt, bring some sort of shelter, bring plenty of food and water, and pack clothing for appropriate weather. John Flaherty, the instructor in this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provid...

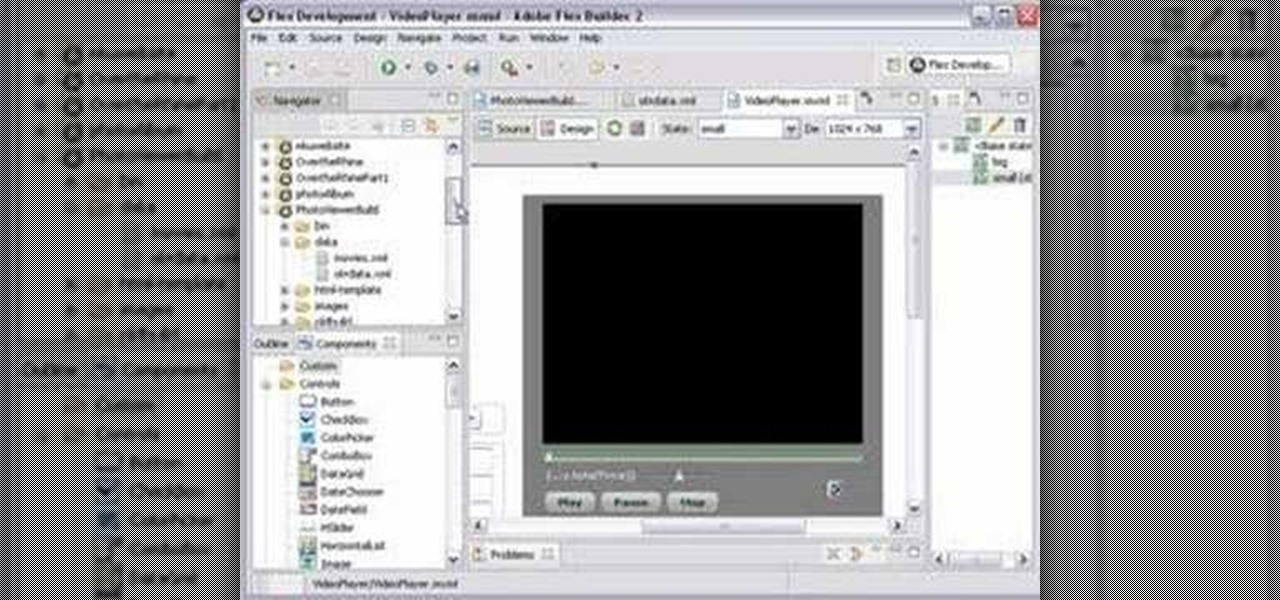
This is a simple Adobe Flex Photo Viewer. It uses a number of techniques that are not found in any one place in the literature - data shorting, tile repeater, xml http services, inline mxml actionscripting, click on double functions, use of CDATA Tags, tooltip, glow and fade effects - all done in less than 100 lines of code (once you take out the blank lines). This was created by Mike Lively Director of Instructional Design at Northern Kentucky University for the Over The Rhine project.

Zune is a digital media players and services sold by Microsoft. It includes portable media players, client software, and the Zune Marketplace Internet music and video store. If you hate the Apple iPods, you probably have one of these MP3 players.

With a few simple steps, you can change your motor oil yourself -- no need for an expensive mechanic to do it for you.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

Instead of making regular old cup cakes try something new and show the people in your life just how much you care with a fun heart-shaped cup cake. The best part is you don't need a heart mold. All you need is your regular cupcake tin and a marble to create the shape.

Stir fry is easy to make and always a lively dish to bring to the table. Join Betty as she makes her favorite sirloin steak stir fry recipe with asparagus and rice. It's delicious!

Make your underwater dreams come true by turning yourself into a bona fide swimming mermaid. If mermaids did exist, you would be the perfect candidate to transform into the mythical creature. So check out this video tutorial form Little Orca to learn how to make your own mermaid tail costume.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time.

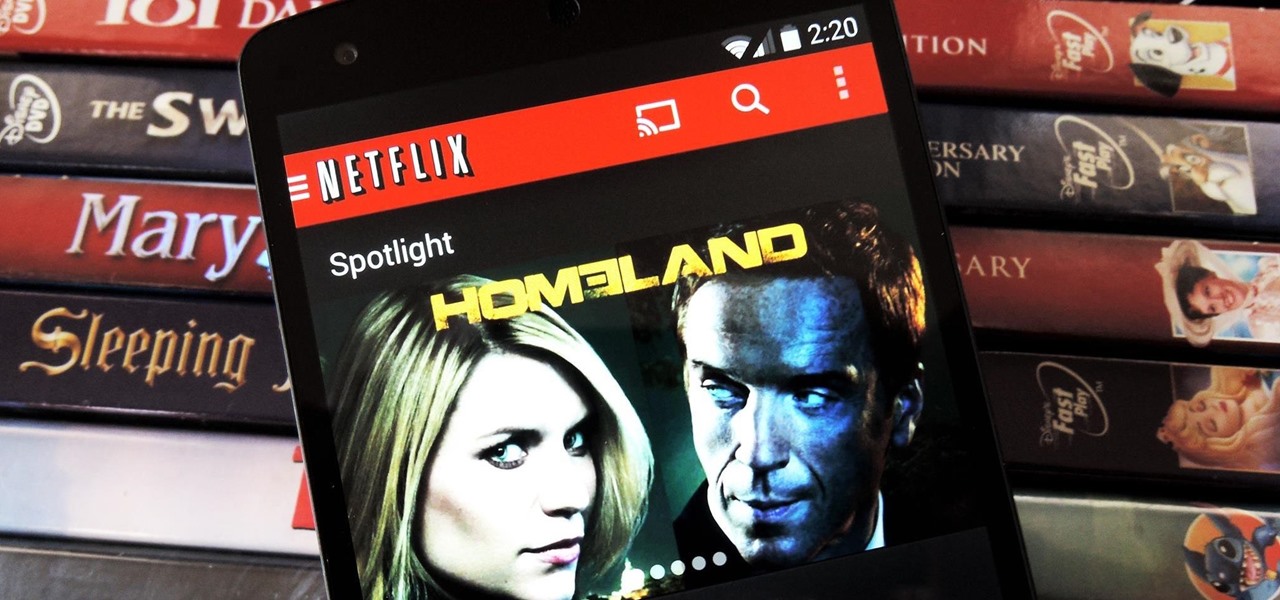
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Old people are usually perceived as wise and enduring, whereas an old smartphone, like my iPhone 4, becomes the butt of a joke every time I take it out of my pocket. I mean, come on, it's not like I'm still rocking one of these... And if I was, I guarantee you wouldn't beat my score on Snake.

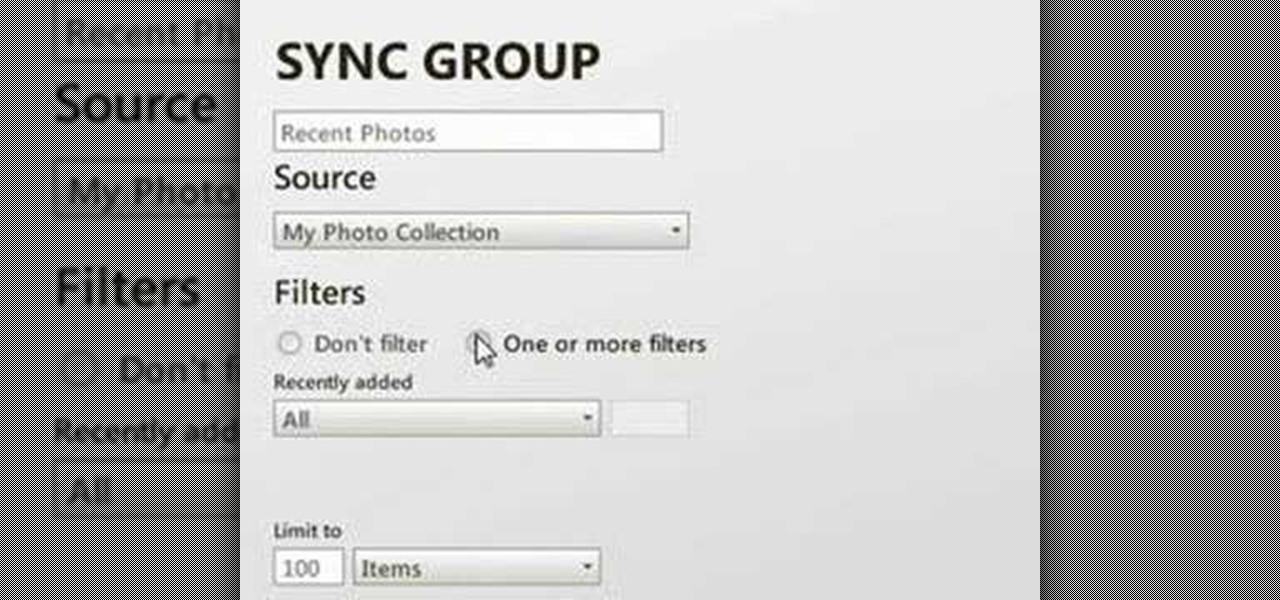
There are quite a few flaws with Apple's mobile products, and one that drives me crazy is their reliance upon iTunes for all your music syncing needs. If you want a song on your iPhone, you pretty much have to use iTunes to get it on there. Either that or buy it directly from the iTunes app on your device.

Turn the unmarked and unlined moleskine notebook into a productivity tool! All you need are a few small multi-colored Post-It tabs, a Hi-Liter and a regular pen. By color coding the separate sections of the notebook, you can easily flip to needed sections.