If you're going to do this, be careful, as your fingers get close to operating high voltage devices & potentially fatal current! Remember that TV's can store a lot of energy for a long time, so don't be poking your finger everywhere - even if the TV is off.

When a quarter in pushed into dry ice, a strange thing happens. The quarter starts to quiver. It is a normal room temperature quarter. I did nothing to the quarter. This is not a trick but really happens. The evaporating CO2 creates a small air current causing the quarters to vibrate.

Tired of grandpa's baseball card collection rotting away in your attic? Well, unlike his pop bottle collection, baseball cards could yield a decent amount of income for you, if you know how to sell them. There are different outlets available for selling an individual baseball card or card collection. Know how to sell the fruits of your hobby and avoid getting ripped off.

Whether you've just bought a brand new shiny surfboard, or your current wax job is a grimy, slick mess, here's how to get that perfect grip so you don't slip off.

Start by clicking start and type regedit in the search box. Hit enter and when the screen opens go under hkey current user and click on control panel and then desktop. Under desktop go to menushowdelay. Under menushowdelay right click and then click modify. In the box that pops up set the value to zero and click ok. Then close the registry editor. Next you will want to download ram booster 2. 0. Once you have downloaded and installed the ram booster program you will want to edit your options....
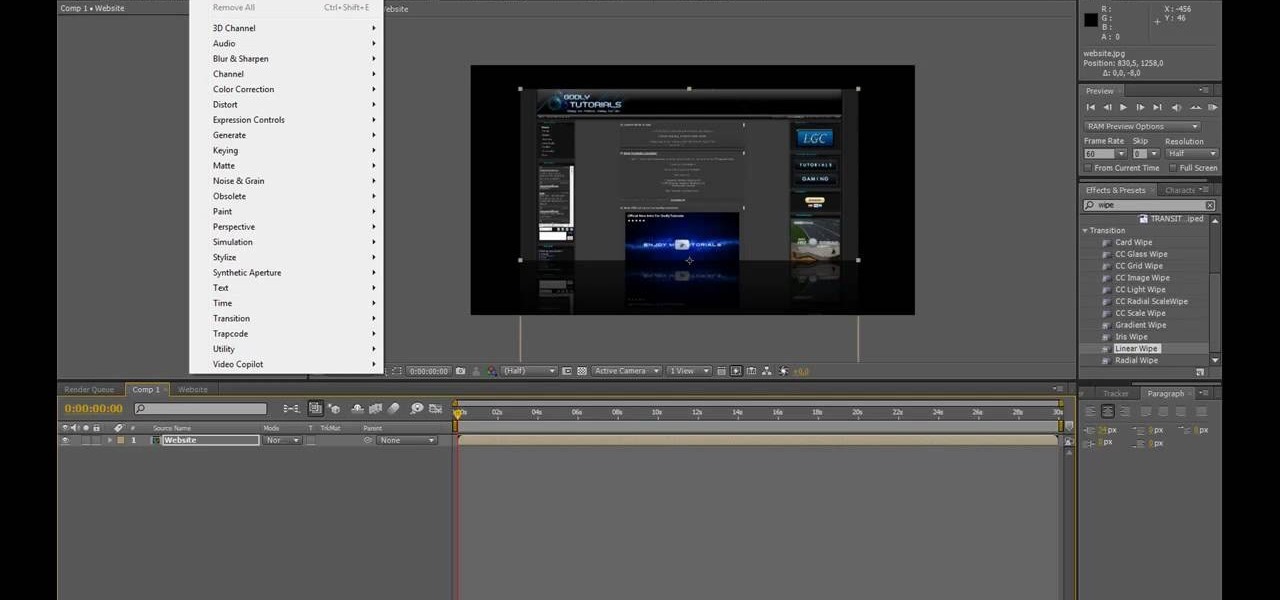
Open After Effects. Create a new composition by selecting "Composition" and "New" from main menu. Use default NTSC DV preset. Keep 30-sec default duration unless you need more time for the video scene to edit. Import several video clips by selecting "File," then "Import" from menu. Navigate to video files you want. Import at least 3 different video files using Import File dialog box. Double click on 1st video file you want to add to your timeline. The file will now open in a video monitor win...

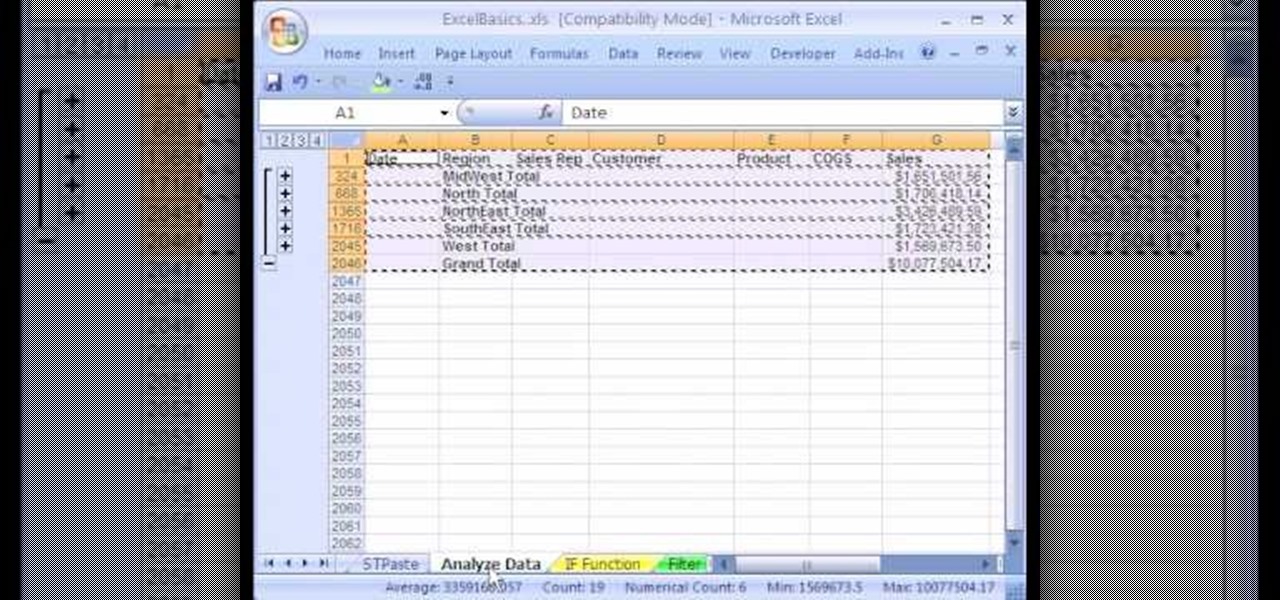
1. The following instruction describes how to generate sub totals in Microsoft Excel Sheet. 2. Take Region as a Primary column and Sales Rep as a Secondary Column. 3. First method to sort: Select a cell in Region and goto Data select A to Z. 4. Second method to sort: Select a cell in Region and Right click and select Sort A to Z 5. Then click a cell in Region and select Data->OutLine->SubTotal 6. In the SubTotal Window select 1.Each Change in: Region 2.Use function:Sum 3.Add subTotal to:Sales...

Got school spirit? The cheerleading squad's the perfect place for you. Here's how to make the team. Step 1

Step 1 Launch the Adobe Flash program and select “Flash File (Actionscript 3.0)” under the “Create New” menu. Change the workspace layout to “Essentials” by clicking on the drop-down menu in the upper left of the top menu bar.

A good party guest should live by this motto: Ask not what the party can do for you, but what can you do for the party!

Watch this video tutorial to learn how to color your hair at home. You'll save a bundle using a coloring kit instead of heading to the salon every six weeks. Plus, dyeing your tresses at home has never been simpler.

You know this is the job for you. Here’s how to convince the person doing the hiring. Learn how to do well in a job interview.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

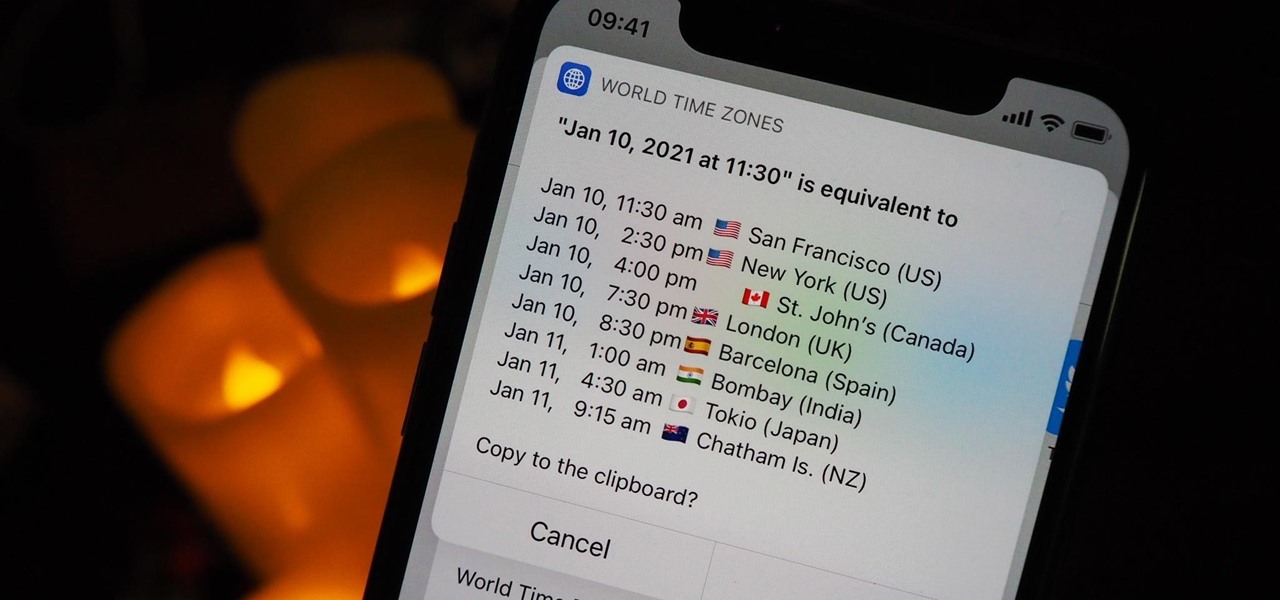
Working with people in different time zones can be difficult when scheduling a time to meet up virtually, whether it's on Zoom, FaceTime, another video chatting app, or just a good old-fashioned phone call. The time needs to be good for all parties, and trying to remember UTC offsets and doing mental math isn't easy. Luckily, there's an easier way to deal with time zones on your iPhone.

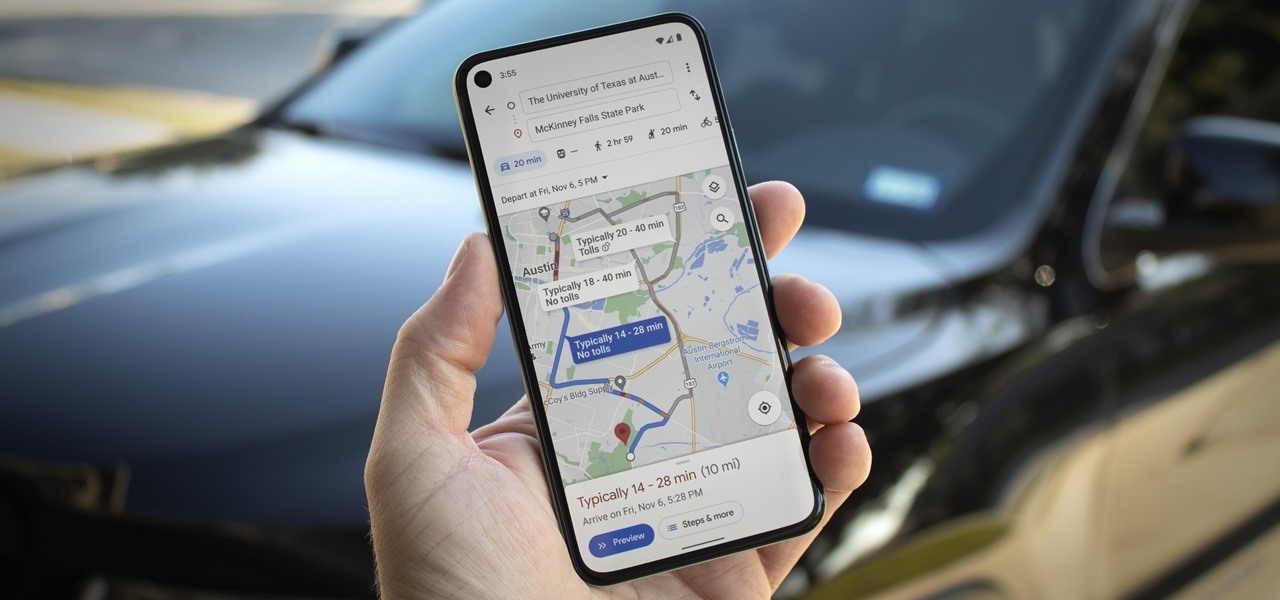
If you're in the market for a new house, how do you know what your commute would be like if current traffic is unseasonably low? Or if you're considering a new job across town and want to weigh the pay raise against the extra time stuck in a gridlock, how do you measure the discrepancy? Google Maps can help.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

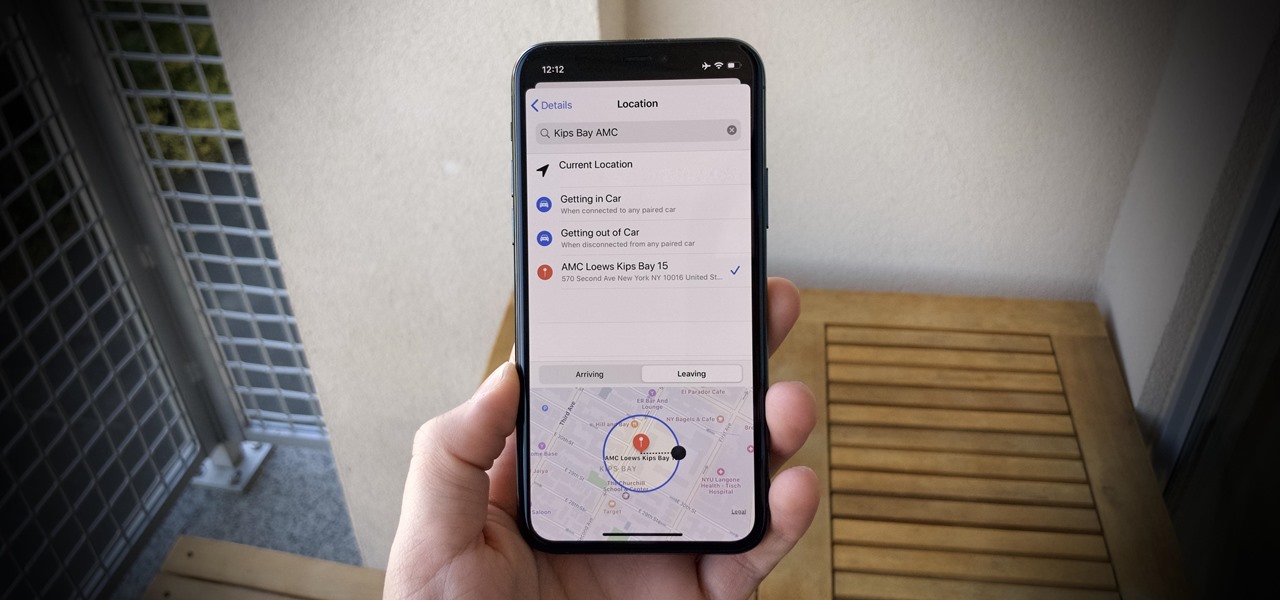
Apple's Reminders app is essential for those of us with a forgetful memory. But a standard Reminders entry isn't foolproof. They aren't great if you need to do something right when you get somewhere, since it can be tricky to set a specific time for that reminder. That's why Apple's location-based reminders are so darn useful.

Apple Maps has had a rocky history since its introduction, which included limited features and questionable data, earning it a reputation as a lesser alternative to Google Maps. Since then, Apple has worked to close the gap, and in iOS 13, they're introducing Collections, which allow you to create groups of locations on your iPhone that you can then quickly access and share with others.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Filmic Pro has a superb suite of professional settings — bit rate, frame rate, and mic choice, to name a few — which can enable you to capture the best footage possible. But different shots require different setups, and it can be frustrating to change settings on the fly. Filmic Pro lets you skip that whole process by saving your favorite settings as presets for quick and easy access.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

So you forgot to send that super important email to your boss, teacher, or another important contact. We've all been there. Spark makes these panic moments a thing of the past. With "Send Later," you can schedule emails to send at any time you want, even when you're not by your phone or computer. You just need to remember to write the email in the first place.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

All of the the tech industry giants, including Apple, Facebook, and Google, are working on new smartglasses and/or AR headsets, but this week, Google took a major step forward with gesture recognition technology that could make its way into AR wearables, posing a threat to Leap Motion and its hand-tracking controllers.

When you set up your MyFitnessPal account for the first time, it asks for a checklist of personal info to create nutrition and fitness goals for you. Whatever you decide then, it's important to know that the goals provided to you are not fixed. If your doctor or nutritionist recommends a new plan, or you simply want to change up your routine, you can customize your weekly and daily goals.

While there were a ton of features added in iOS 12, one that Apple had been bragging about since June was nowhere to be seen. Until now. With the iOS 12.1 update, your iPhone gets a huge feature, as well as a few smaller ones to boot.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices access to their visual voicemail apps. For that, there's Google Voice.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

With beta testing coming to a close, it's quite likely we will see the stable Android Oreo OTA roll out for the Galaxy S8 in late January. Yesterday, a Reddit user posted a link to an official Oreo OTA build for the Galaxy S8. We've already detailed everything that's new in this stable build. Now, let's take a look at how you can install the update on your device.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.

Flu vaccines can help prevent us from getting or suffering the most severe effects of the flu. But, each vaccine only protects us from three different strains of the flu. If we don't have a vaccine against all types of flu, it leaves us open for an epidemic with a flu virus we didn't expect.