Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

There's been a whole lot going on at this year's Consumer Electronics Show, from the latest in virtual reality gear to televisions that continue to slim down while producing higher quality images.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.
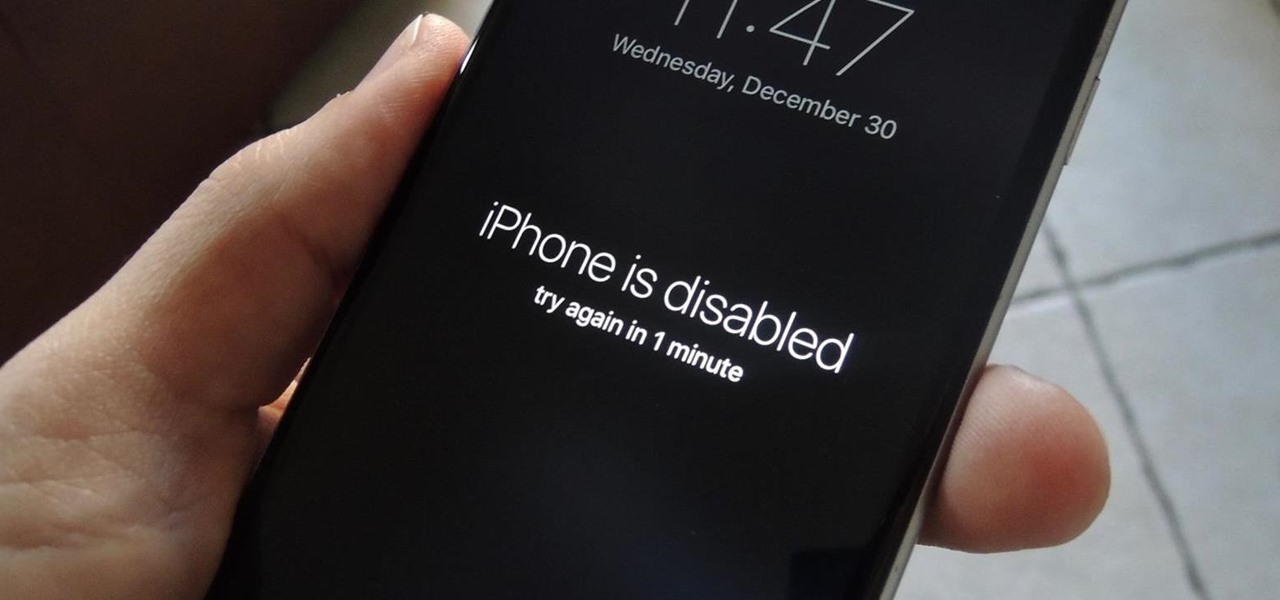
With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Amazon is slowly trying to gain as much influence in the tech world as it has in the consumer market, and with the Amazon Fire HD 7, they have their eyes set on taking on the "budget tablet" space.

Yes, screen savers are fun to look at for a few seconds, but those animations actually used to serve a purpose beyond simple entertainment.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Welcome back, my rookie hackers!

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Whenever you buy a newer iPhone model, you get a set of Apple EarPods with remote and microphone built-in. Aside from their comfortable design and high-quality sound they provide, these headphones offer additional functionality beyond just pausing and playing music.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Sometimes it's hard to remember that lasagna, pizza, cannoli, and other dishes are actually Italian in origin; they're so much a part of the American culinary landscape at this point. Wherever they come from, Americans of all kinds love to eat 'em. This guy was released from a North Korean prison, and after two years, the first thing he wanted to eat was fast-food pizza.

Minor mishaps occur all the time in the kitchen, whether you cut your finger while dicing an onion, scorched your hand in a grease fire, or burned the roof of your mouth because you were to eager to taste-test your killer pasta sauce.

You either love kimchi or you hate it, but for those of us who love it, its salty, briny, spicy crunch is the stuff of life. Honestly, if you're not eating it regularly, you should start, since it's being studied for an amazing list of health benefits, including anti-cancer, anti-aging, and antioxidant properties; obesity and high cholesterol prevention; and promotion of immunity and skin health. The beauty of kimchi is manifold:

At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...

Aluminum foil is one of those things that every cook, experienced or just starting out, has in their kitchen. And while we may think we know how useful this handy material can be, there are hundreds of ways we could be utilizing tinfoil to make our lives a whole lot easier.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

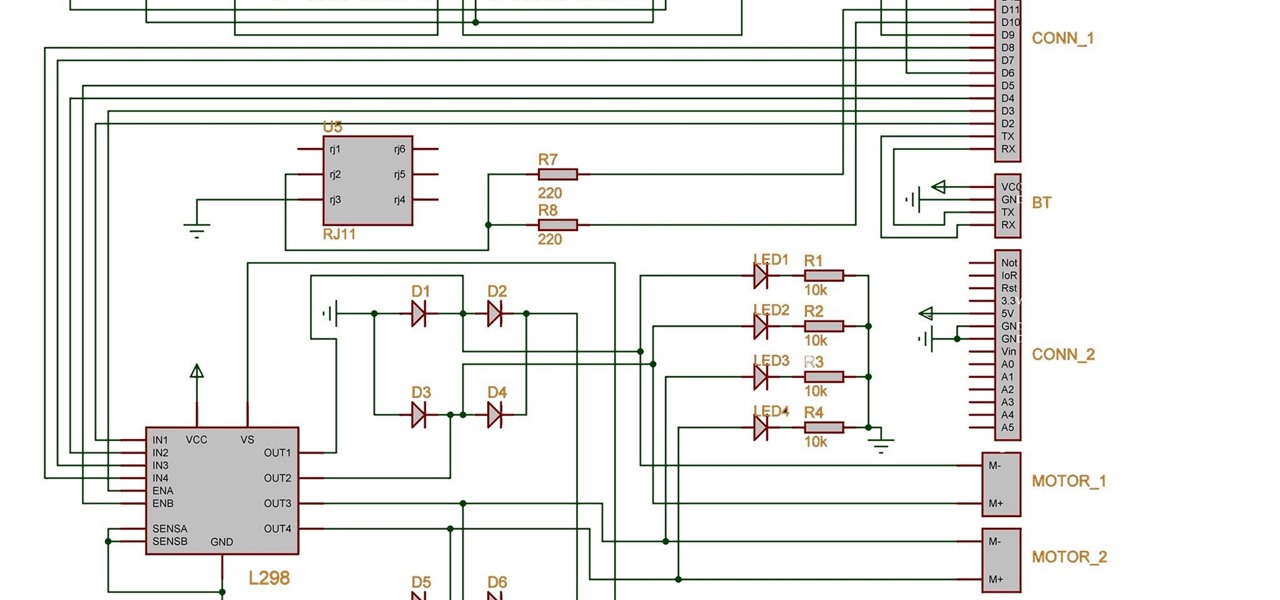
Two years ago, driven by a good friend of mine i decided to give it a try on timelapse photography. I had a DSLR camera but didn't had an intervalometer, so i assembled a small electronic circuit on top of an Arduino Uno, made some basic code and did my first timelapse movie. The result was awful, but for some reason I was hooked.

Although your friends might roll their eyes every time you talk about playing Clash of Clans, Call of Duty, or Candy Crush Saga, your excessive gaming habits might actually be making you healthier than everyone else.

The new LG G3 is the latest Android flagship-level device to be released this year, and it's ready to give the Galaxy S5, HTC One M8, and the OnePlus One a run for their money. Sporting a gorgeous 5.5-inch QHD display, 3GB of RAM, and a huge 300mAH battery, the device looks great and has tons of power to boot.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

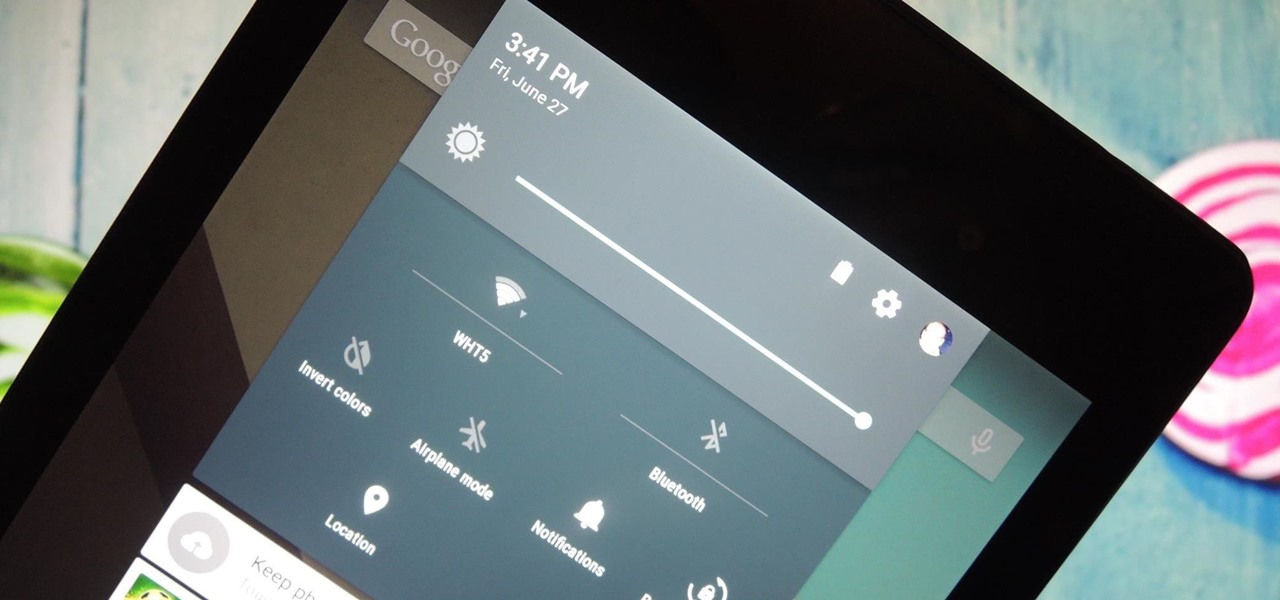
It was the star of the show, but now that Android L has been released for preview to Nexus 5 and Nexus 7 owners, there's a lot that Google didn't tell us about their latest mobile operating system, rumored to be called Lollipop.