Apple unveiled a 9.7-inch iPad Pro at their keynote event today, filling their roster to four different iPads. The smaller iPad Pro has the same screen size as the iPad Air 2, but comes with significant improvements under the hood. Keynote speaker Phillip Schiller rolled into the details: it's 40% less reflective than the Air with only 1.8% screen reflectivity, 25% brighter, produces 500 nits of light (making it "the brightest tablet available"), and has 25% greater color saturation. It also ...

The volume buttons on the side of most Android devices—also known as the volume rocker—make it easy to adjust sound output without having to dig around in any settings menus. But the trouble is, they control notification and ringtone volume by default, and will only adjust media volume after a song or video has started playing.

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.
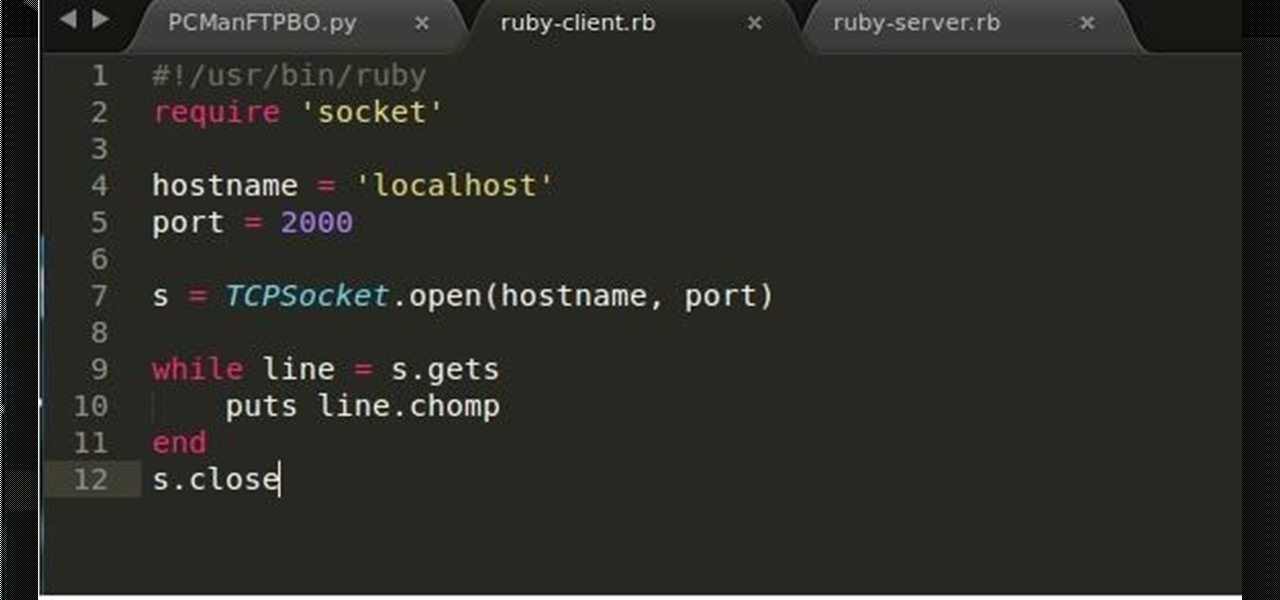
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

Maps is great for making sure you always get to your destination, until you miss that critical turn because you couldn't hear the turn-by-turn directions.

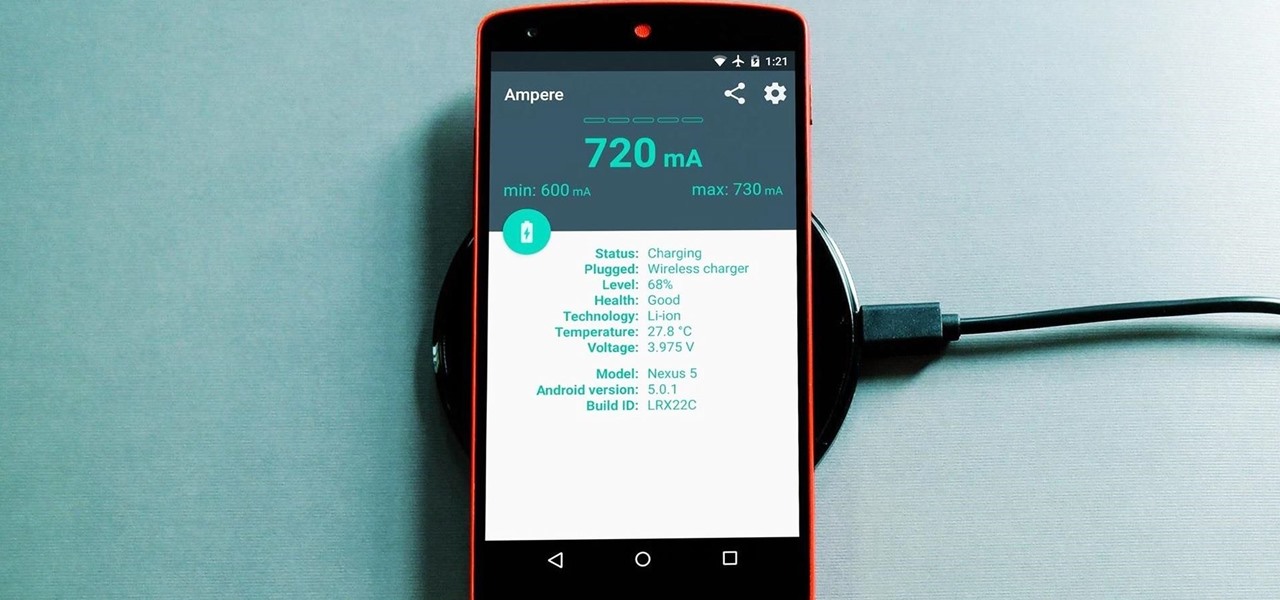
Not all smartphone chargers put out the same amount of current. The adapter in your car probably charges your phone a lot slower than the one plugged in at your bedside, and if you use wireless charging, it may be a bit slower still.

Converting files from one format to another can be a pain. Sometimes you have to download software that you'll only end up using once. Other times you have to use a shady third-party conversion site that's riddled with ads. Not to mention that after a while, unless you're extremely organized, your converted files will be scattered all across your hard drive.

One of the more talked-about features of Android Lollipop is a new Priority Mode that allows you to mute all notifications except for those coming from starred contacts. As simple as that sounds, this can still be a bit confusing—or at least lead to some unwanted interruptions.

You don't need to be a hardcore audiophile to know that Dolby is pretty much synonymous with rich and immersive sound. While we often associate them with home theater systems, Dolby has brought their surround sound processing to the mobile phone arena with Dolby Digital Plus being offered on several Android devices.

Anyone who is familiar with Linux knows that to use your OS to the max, you will need to use the terminal every now and then. Whether it is to install a package or update the system or even delete a file.

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

The new 007 film, Skyfall, comes out this Friday, and dreams of becoming a super-spy have taken over my mind. Only I can't afford any of James Bond's awesome gadgetry or amazing cars—and you probably can't either.
Converting Movies To Psp Format. Hey again, this is a real quick guide for anyone interested to get a movie onto there PSP without all the fluff i have seen elsewhere. I just watched Africa the Serengeti on my PSP and heres is the lowdown.

Control is important. Mankind inherently wants to control its environment, which is why we have things like indoor plumbing, electric lights, air conditioning, and more. Likewise, Minecraft has redstone, which is a way for users to control their environment and manipulate it to suit their needs.

Sore muscles are no fun, but the only way to make it stop is to continue working out. The more you work your muscles, the stronger they will get and the less they will hurt when you use them. No matter how much it hurts you have to work through the pain. Check out this tutorial for info and advice on how to get past the aches and reach your maximum potential.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

Drone mishaps, such as the collision that scratched a military helicopter in New York, are becoming something of an everyday hazard.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

A robust appetite for imported foods is leading to increased disease outbreak in the US. Despite the locovore and slow food movements, America's demand for foreign foods is picking up. According to a study published in the journal of Emerging Infectious Diseases, demand for imported fresh fruits, vegetables, and seafoods has jumped in recent years.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

I'll admit it: I ignore expiration dates. No matter if it's a sell-by date, "best if used before" date, or even a use-by date, I don't care. I just check for signs of food decay and keep on eating.

We are visual animals. So when it comes to food, presentation is everything. In deciding what to eat, certain colors and textures instantly turn us off or on. Think of runny sautéed spinach versus a salad of fresh vibrant spinach. Which one would you reach for first?

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Access your computer's BIOS settings

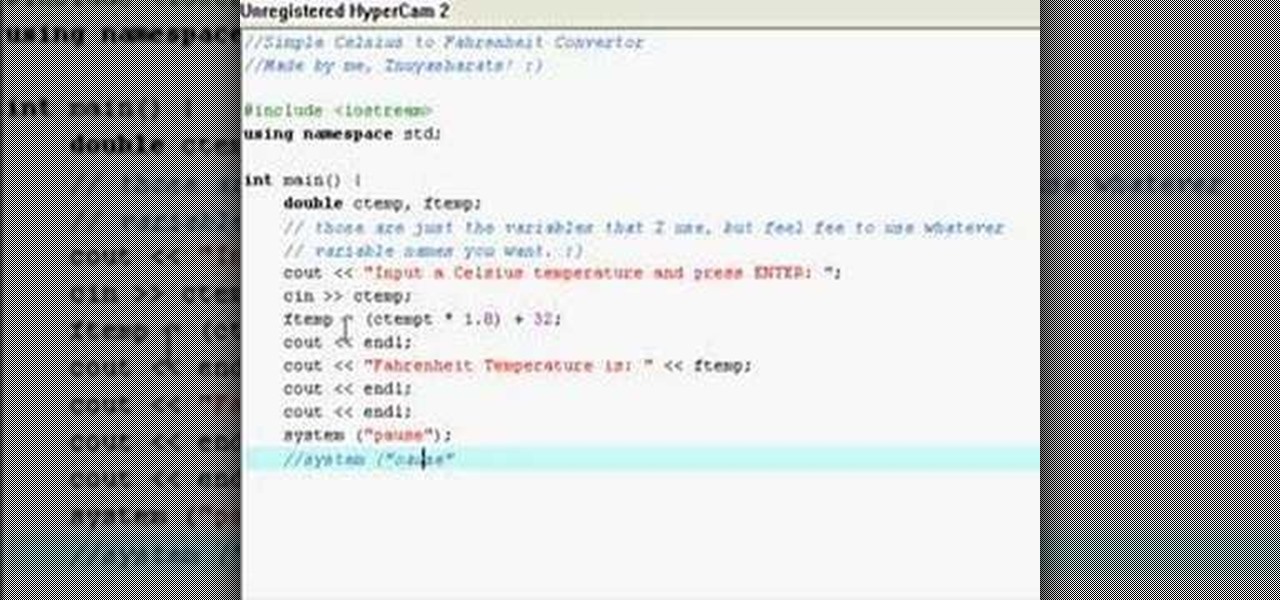
In this video, the instructor shows how to convert Celsius to Fahrenheit using a C++ program. This video shows how to do this by a live example where the instructor writes down the code to do it. First, code the basic structure of a c++ program that contains the include and all other statements. Now accept the value of temperature in Celsius from the standard input. Now multiply that value by 1.8 and add 32 to it to get the value in Fahrenheit. Display the value to the output. Finally, compil...

First you need a CRT TV, one Laptop, Headphone jack, Male and Female RCA jack, and output and input male female jack. And than one is audio cable and another one is video cable, and than connect it to your TV video out and audio out, and another one are connect to Laptops video out and audio out. And to get the video quality is good let set the Graphics property on your laptop and there are one option to TV set graphics and set them. And set the Screen Resolution and video stranded, and then ...