See how to use Wondershare DVD Copy to copy and back up DVD's on a Mac. DVD Copy for Mac is a professional DVD copy program designed for Mac OS users to copy D9 and D5 DVD movies. It can copy your DVD with the original quality 100% preserved and at the same time remove DVD protections such as CSS, RC and RCE.

Check out how to back up and copy DVDs on a Mac with iSkysoft DVD Copy. Mac DVD Copy is a fast and easy-to-use Mac DVD burner and Mac DVD copy software which can Copy DVD to DVD, such as D5 to D5, D9 to D9, and D5 to D9.

If you ask Apple Support if the 18-watt power adapter that came with the iPhone 11 Pro, iPhone 11 Pro Max, and four different iPad models will work with the MagSafe Charger and your new iPhone 12 or 12 Pro, the answer is "yes." But that's not the whole story.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

If you just got a new iPhone, chances are you picked up the iPhone 11, successor to the iPhone XR, the most popular device in Apple's 2018 series. Since the XR did so well, it was predicted that the iPhone 11 would too, and so far, it has lived up to that prediction, beating the 11 Pro and 11 Pro Max in sales in 2019.

In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price tag.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

A new iPhone is only as good as its accessories. Whether it's a case, screen protector, or charger, your iPhone's ecosystem depends on accessories to keep it powered, protected, and personal. Prices on all of these extras are going to be at an all-time low this Black Friday weekend, so we've rounded up the best deals around to help you get the essentials you want and prices you can afford.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

Starting February 21, you can preorder your Galaxy S20, S20+, or S20 Ultra. Samsung includes everything you need to get started in the box, but probably not everything you'll want. Let's go ahead and bridge that gap.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

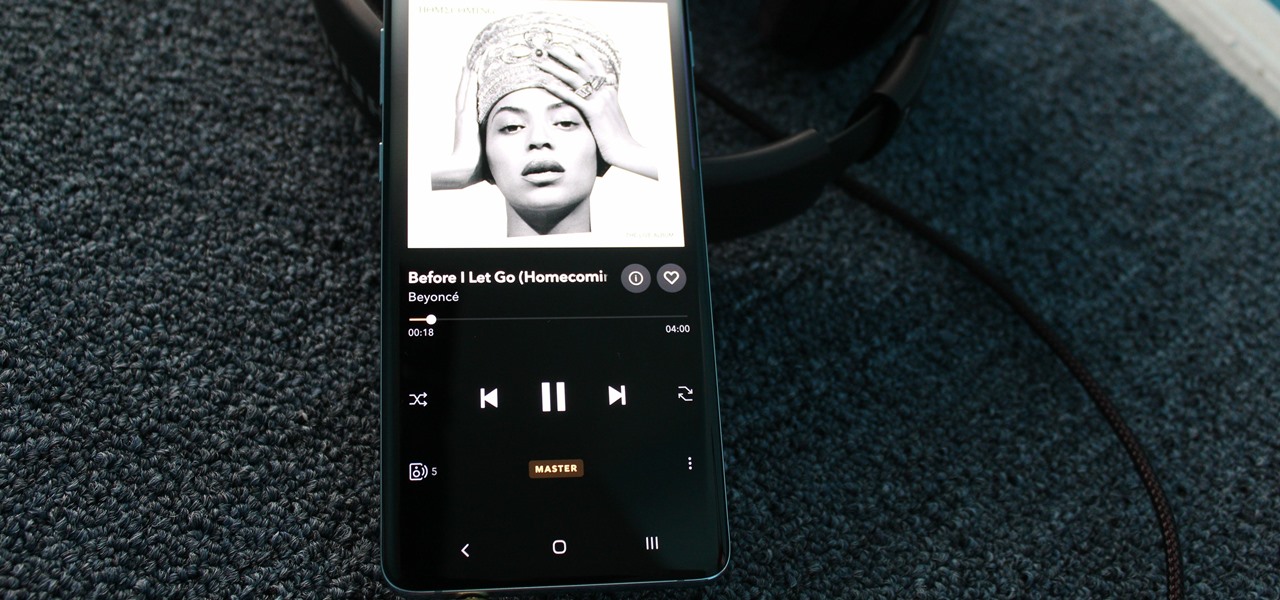
As you might know, Tidal differentiates itself from the competition with its audio quality. Unlike Spotify and Apple Music, it aims to give its subscribers studio quality audio from any device. However, before you sign up for Tidal, be aware there are few steps you need to take in order to stream such high-quality music.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

It turns out that attending the L.E.A.P. conference last month may have mostly been best for demoing the Magic Leap One in person, as the company has now uploaded the majority of the insider panels held at the event in Los Angeles.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

The Daily Prophet, the enchanted newspaper from Harry Potter lore, is no longer the sole source for magical moving printed photos.

Traditional media institution The New York Times continues to break new ground in its augmented reality news coverage, this time with a 3D volumetric capture of model Ashley Graham.

OnePlus pulled out almost all the stops with their latest flagship, but there are a few areas where the phone falls just short of perfect. The single bottom-firing speaker leaves a lot to be desired, for instance, but thanks to the awesome development community for the OnePlus 6, you can already give your phone true stereo speakers with a software mod.

The Augmented World Expo is winding down in Santa Clara, where Qualcomm, Vuzix, and Meta Company were among the companies making big announcements.

The Galaxy S9 is an audio powerhouse. It has the first set of stereo speakers on a Samsung flagship, and it even comes standard with a set of AKG-tuned earbuds that would normally cost $99. But if you want to further enhance your audio experience, there's a feature that will customize audio output to your own specific hearing.

A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe.

If CES 2018 is the starting gate for this year's race to release smartglasses, then Vuzix is already racing down the augmented reality track with its Blade smartglasses.

With Google's release of Poly API on Thursday, the search giant has found a way to simplify the workflow for AR creators by enabling the ability to integrate its 3D object search engine Poly directly into an application.

Meta Company has filed its response to allegations that the user interface for their augmented reality headsets infringe on six patents owned by a mostly-unknown company.

When Disney teased an augmented reality game called Star Wars: Jedi Challenges running on a headset from Lenovo, fans had more questions than Disney had answers. When? How much? Can I be a real Jedi?

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

When it comes to playing videos from your personal media library, VLC is hard to beat. But let's say you want to play videos from an Android device by connecting it to your TV — what app should you use then? VLC is still the answer, particularly once you've enabled its TV-friendly UI.

The LG V20 went on sale on September 29, 2016, and is the second flagship phone in the V series to be released by LG. Both the V20 and its predecessor, the V10, have been audio-oriented phones from the start, but the V20 has a much nicer Hi-Fi Quad 32-Bit DAC, which makes the output audio from the 3.5 mm headphone jack sound amazing. It's loud, it's crisp, it's full, and everything from the higher frequencies to the lower ones can be heard.

Google's Pixel and Pixel XL flagship phones are a rousing success, with consumers praising the fluid user experience and overall performance as two of the devices' biggest strengths. But even though Google may have knocked it out of the park with a set of Apple-like smartphones that "just work," there's still room for improvement in a few areas.