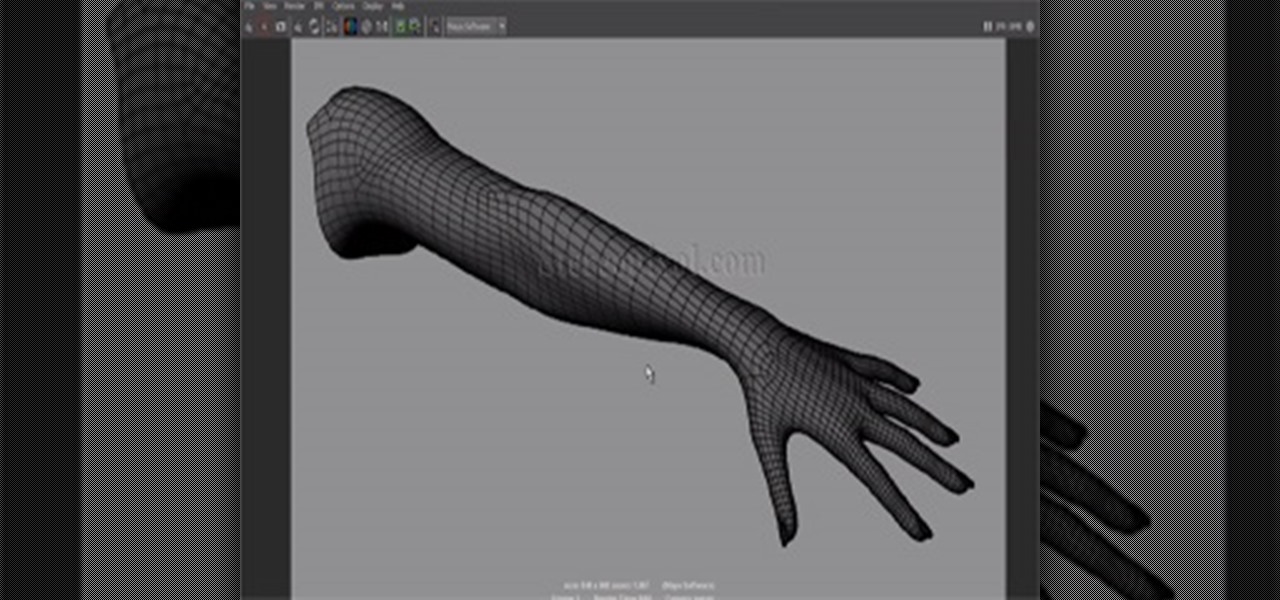
This is a very essential tutorial for Modelers to present their showreel. In this tutorial we are going to learn how to render a wire frame of a model. Wireframe render in Maya is bit tricky but easy also, just you have to know right button to press. This tutorial will cover the output in Autodesk Maya Software renderer. Later we will discuss through Mental Ray render engine. Hope you will enjoy.

In last Saturday's workshop, the tutorial was on the ABBA switch, so named because it fires redstone pulses in A-B-B-A order. While the turnout was low, it was a really productive workshop! We experimented with a lot of things and had a great time. Hopefully you'll consider joining us next time!

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Android does a great job at multitasking. Split-screen mode and picture-in-picture are terrific at letting you manage more than one app at a time. But there are some limitations. For instance, when you're playing a video and you open a second video in split-screen, the first one pauses. Thankfully, Samsung has a fix for this.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

While Vuzix is beefing up the processing power of its next-generation smartglasses with the Qualcomm Snapdragon XR1, the company will also give its devices an upgraded display engine.

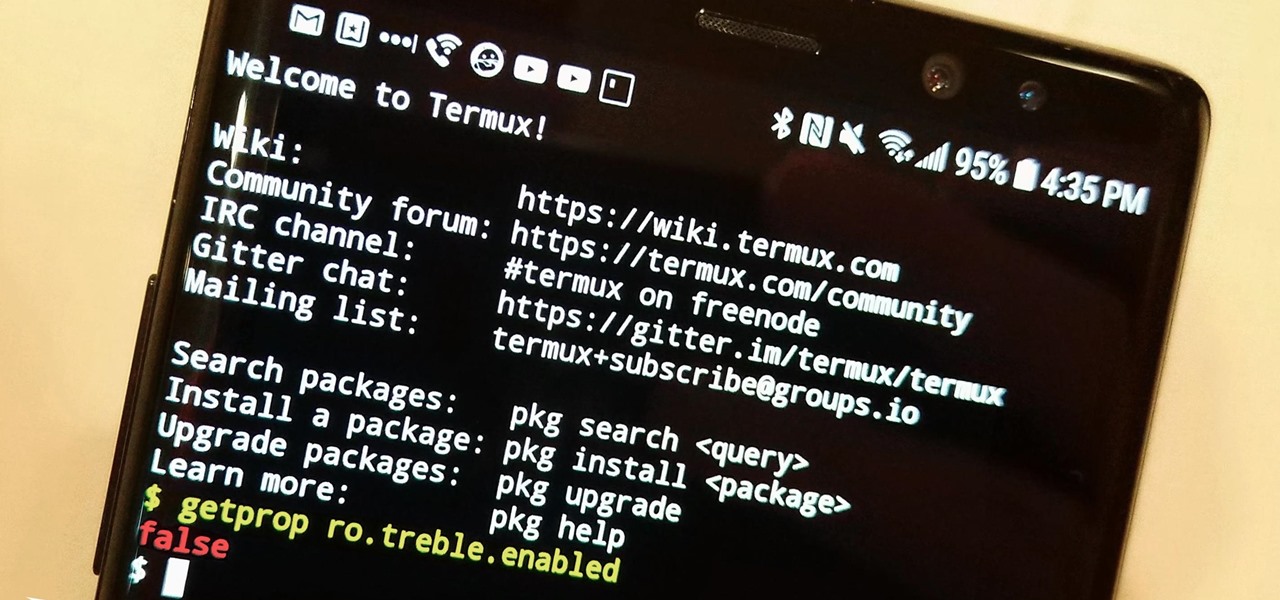
The Oreo beta updates for the S8 and Note 8 have been avilable for some time now. If you're interested in running Oreo on your Galaxy Note 8, you can check out our guide on how to do so. As we dig deeper into the updates, one question on the minds of Galaxy fans is whether or not the Oreo update will support Project Treble. Today, it appears we have an answer.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the attacker portion of the shell. In this article, we'll just be testing it to see if everything works correctly.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is healthier than tap water. But is it? Here are 5 reasons why tap water is probably better than that bottled stuff you drink. 1. It's Not Cleaner (& Might Be Dirtier) Than Your Tap Water

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

The front-facing stereo speakers on the Nexus 6 certainly pump out some awesome sound—but it could always be better, right?

The Geminid meteor shower 2010 is tonight, climaxing sometime between midnight and dawn Tuesday. Usually, the Geminid meteor showers in December are awesome spectacles, one of the most intense meteor showers of the year, but this year the moon will be out until after midnight, lessening visibility. But just because you can't see the meteor shower this year, doesn't mean a meteorite or two didn't sneak into Earth's atmosphere, hurdling to the ground, waiting for you to find it. So, get your me...

With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

With all due respect to the fine folks at DrinkTanks, it's a little surprising that no one came up with their idea sooner. After all, last I checked, beer was pretty darned popular.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Mixing water and electricity is extremely risky and potentially lethal, yet that's exactly what I did with the Scariac. In its simplest form, the Scariac is just a glorified version of two wires in a bucket of water, but it's actually one of the cheapest power controllers you can make.

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

Males fight for dominance in order to gain access to the limited supply of female eggs. This is why male birds expend energy on brightly colored plumage, but female birds do not.

I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist reach for the burning miasmas of plasma. But to get to the stars, we need to start with the basics.

A medical pacemaker regulates ones heartbeat, but the DJ pacemaker regulates the music's beat, plus a whole lot more. This tutorial teaches you how use the pacemaker as a portable DJ setup. The pacemaker is one of the best inventions for the DJ/ music industry has ever made. But the pacemaker will not replace the typical DJ setup. Find out how you can mix music portable with a pacemaker in this how to video.

While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

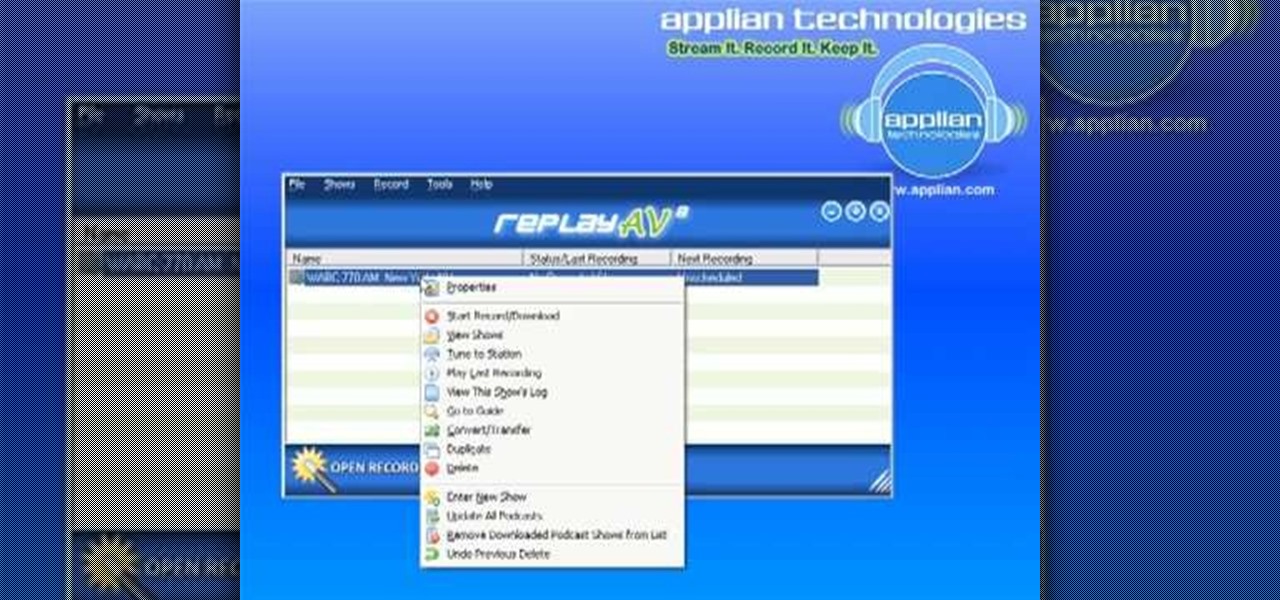
Replay AV is the newest software to come out for downloading steaming audio from the web. Replay AV allows you to download audio from different sources all over the web. You can even record radio broadcasts and set your account to record the station. This video will show you how to add a radio station to Replay AV.

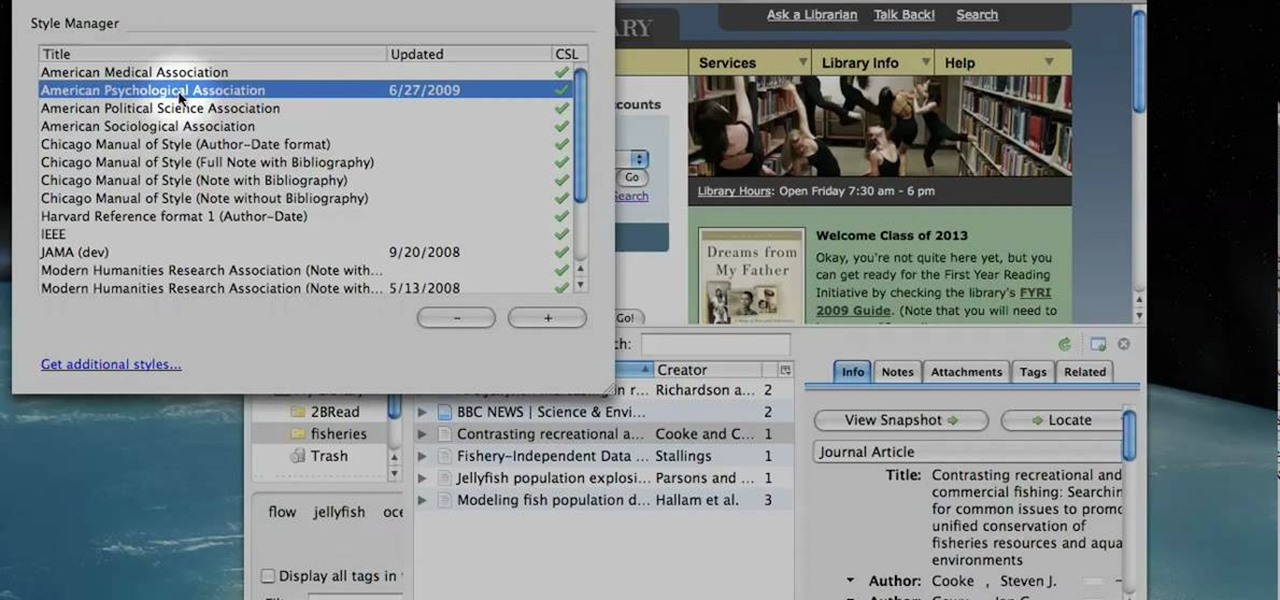
Learn to use Zotero to create bibliographies and citations with this tutorial. In addition, collect and organize information from all sources. So help correct the sources research paper. Before using the excitation features, make sure to select and prepare the style of your paper. If you are not sure ask your instructor. She has a preference style. You will select by clicking on the action button +preference then choose the style. It will include the number of most common style. You can downl...

If you've ever had a little trouble trying to program your calculator, you may find a little relief with this four-part video tutorial. Here, a Texas Instruments (TI-84 Plus) calculator will be used to explain the programming process. The four parts include:

This 7 part Houdini 9 tutorial series is about how to transfer color using dynamics is a great place to start to understand Houdini's dynamics in a significant way. Part one covers painting setup, two establishing a paint source, three creating paint, four defining paint colors with a solver, five painting with dynamics, six reviews how it works, seven setting up for render output. Learn to paint and transfer color with dynamics in Houdini 9 and get more control over your work in this tutorial.

Want to know what a septum is? An aorta? The bicuspid valve? These are all parts of the human heart, and in these educational tutorial videos, you'll learn all you need to know about the physiology of the human heart. Anatomy, biology, physiology... it's all science, so no matter what field you are studying, these will be very helpful for you in your further medical studies, or for just know-it-all knowledge.

This video shows you how to output information from Unreal Tournament 3 into a log using Unreal Script.

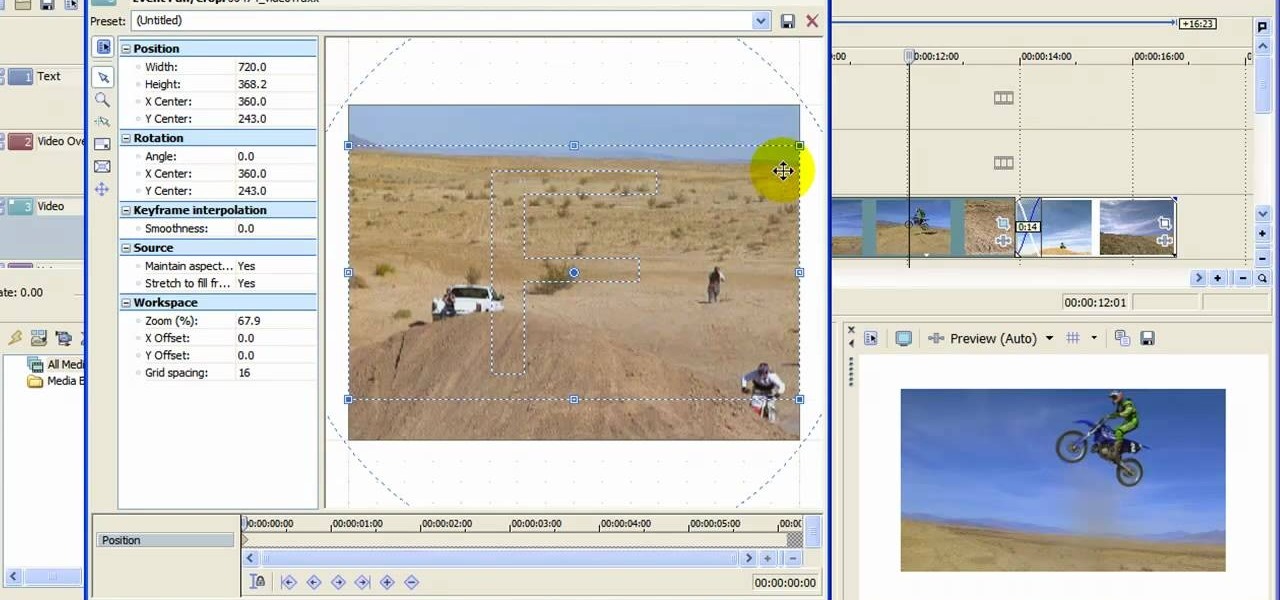
When you upload your videos onto YouTube, you will need to have your video in wide screen format, if you want to avoid having black bars on either side of your video. In order to do that, with Sony Movie Studio, you will need to go to "project". Click on "properties".