
How To: Convert movie files for use on an iPod or iPhone
The iPod kids shows viewers how to covert movie files that are already on your computer into a format that will work with your iPhone or iPod Touch (2nd generation).


The iPod kids shows viewers how to covert movie files that are already on your computer into a format that will work with your iPhone or iPod Touch (2nd generation).
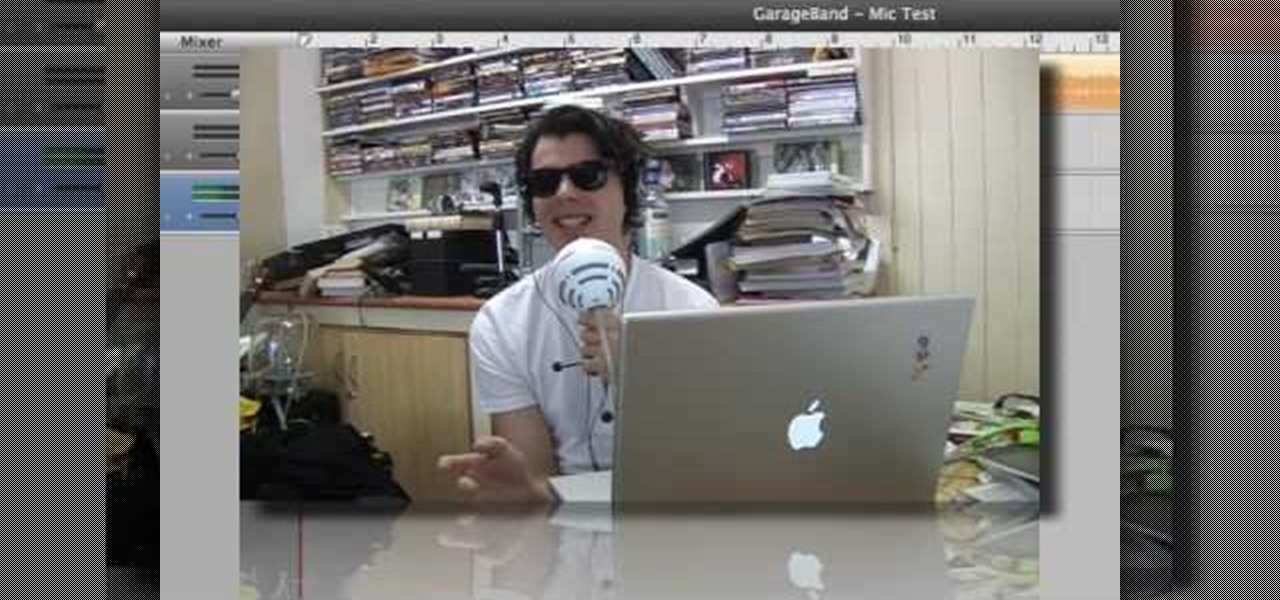
Yes, you can use GarageBand's Auto Tune to sound like T Pain and Kanya West. To start with, in GarageBand, click the plus sign in the bottom left hand corner to create a new track. A window will pop up, Real Instrument Track should be selected by default. Click the Create button. In the Track Info window check to make sure your Monitor is set to On. In the bottom left hand corner, click on the button with the scissors in the middle of the sound wave. This is the Edit Track button. Click on Ad...

This easy to follow silent and accurate video will guide you quickly and easily through what you'll need, (like a Power Supply, a sound system that has a Subwoofer Pre-output and a High Input adapter, which may already come with your amp.) First learn what colored wires should be connected to simulate your PC starting. Then connect the amp to the power supply to simulate the car Head-Unit starting. Once the power issues are handled, the video assists you with connecting your audio input. It i...
Everybody is going digital these days, so everybody has a reason for software like HandBrake. You can save your entire DVD collection on your computer in digital files, and you can convert videos into different formats. Check out this video tutorial on how to rip DVDs and convert videos on Ubuntu Linux, Windows, and Mac.
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Congratulations! You're the proud new owner of an Xbox 360. But before you can play, you need to hook it up.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Many of us rely on our smartphones for all our media needs. Now more than ever, we're using Bluetooth connections to play audio over speakers, headphones, car sound systems — the list goes on. If you own a Samsung smartphone like the Galaxy S9, there are a number of Bluetooth tweaks and hidden tricks that can maximize your audio experience.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Apple caught a lot of flak for removing the headphone jack in their iPhone 7 models, but they definitely got the last laugh when preorders with a delivery date of September 16 sold out within minutes. Headphone jack or not, the iPhone 7 and 7 Plus are still highly desirable products, and consumers have confirmed this by voting with their wallets.

The hatred is almost universal—by now, even late night TV hosts are bashing Apple's move to ditch the headphone jack in the iPhone 7. It's not like the disdain is baseless, either, because there are plenty of problems that come along with removing the iPhone's only analog sound output.

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!
If you're looking for a cool way to add text to your videos, like for an opening sequence to a film where the credits are displayed, embedding the text directly into the scene is the way to go, especially if you like the hit television show "Fringe", who used these kind of embedded title effects in establishing shots. Car adverts use this technique a lot, as well. "Panic Room" also use this effect in the opening title sequence.
Bates numbering can be used with Adobe Acrobat 9 Pro. Place all of the documents that you want to number in a single file. Then, go to the Advanced menu. Then, go to Documents Numbering. Then, click on Add.

In this tutorial, we learn how to rip a DVD with a free DVD ripper. If you want to rip a DVD that you own so you can play it on your computer, this is an easy way to do it for free. To do this, download and install Free DVD Ripper 2.25. First open the software and then open your DVD up and select the title. Next, change the language and other settings as you prefer. Play the DVD just to make sure it works after this. You can change the output settings as well, if you want the movie to be play...
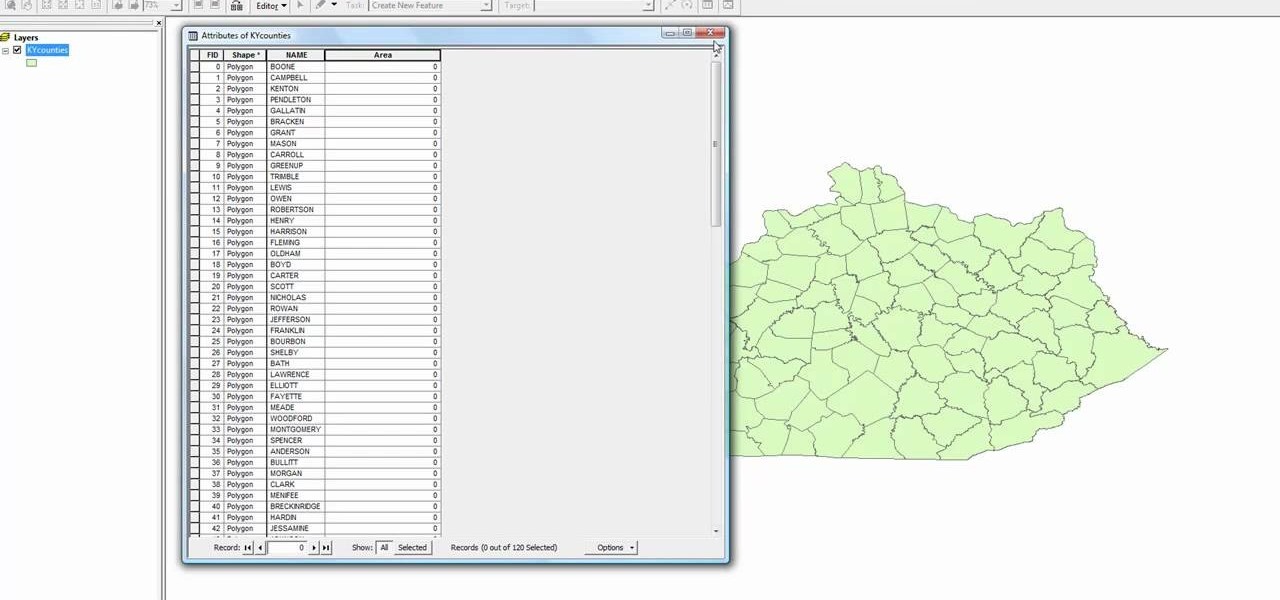
In this how to video, you will learn how to calculate the polygon area in ArcMap. First, open the program ArcMap. Next, go to the left column and right click it. Select attribute table. From here, go to options and click add field. Type in Area and click double. Next, right click area at the top and select calculate geometry. Next, select area disabled. Exit the windows. Next, click the red icon at the top and select data management tools. From here, select project. At the top drop down menu,...

This video tutorial from Magix presents how to burn (S)VCDs and DVDs using Magix Movie Edit Pro 15 application.First you need to group videos you want to burn.If you want to play movies using remote control you have to place chapter markers. You can set markers manually or choose automatic? marker setting which places markers before each new scene.Once all chapter markers are placed, click Burn button.Here you can choose Start Menu Templates. To change movie titles and chapter headings double...
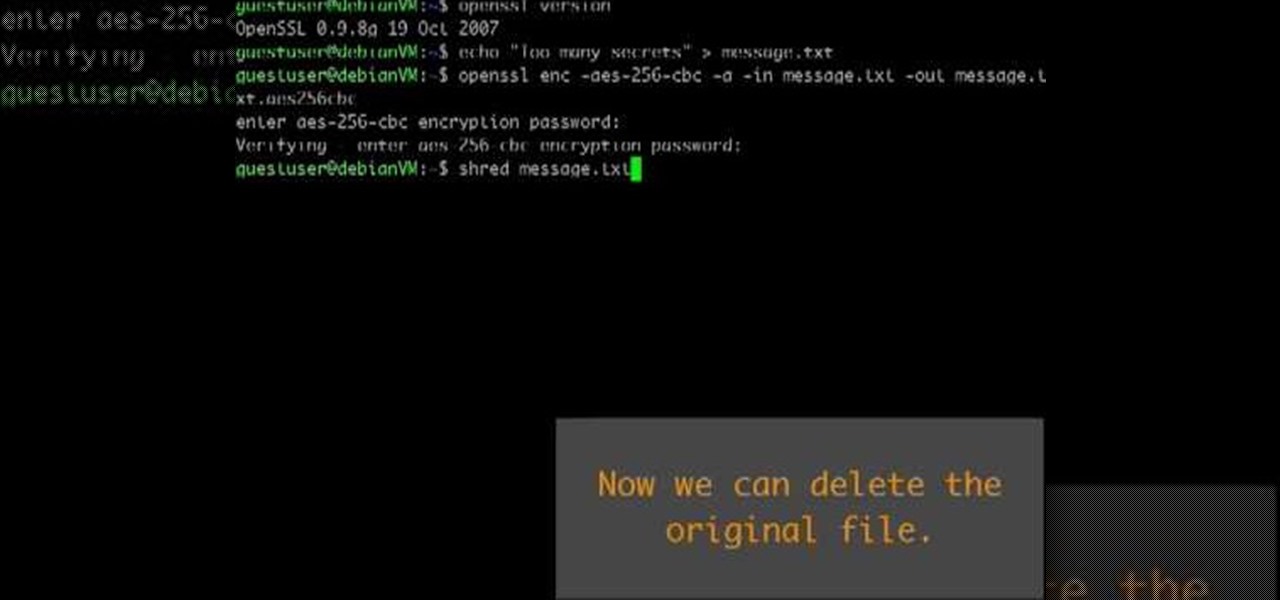
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...
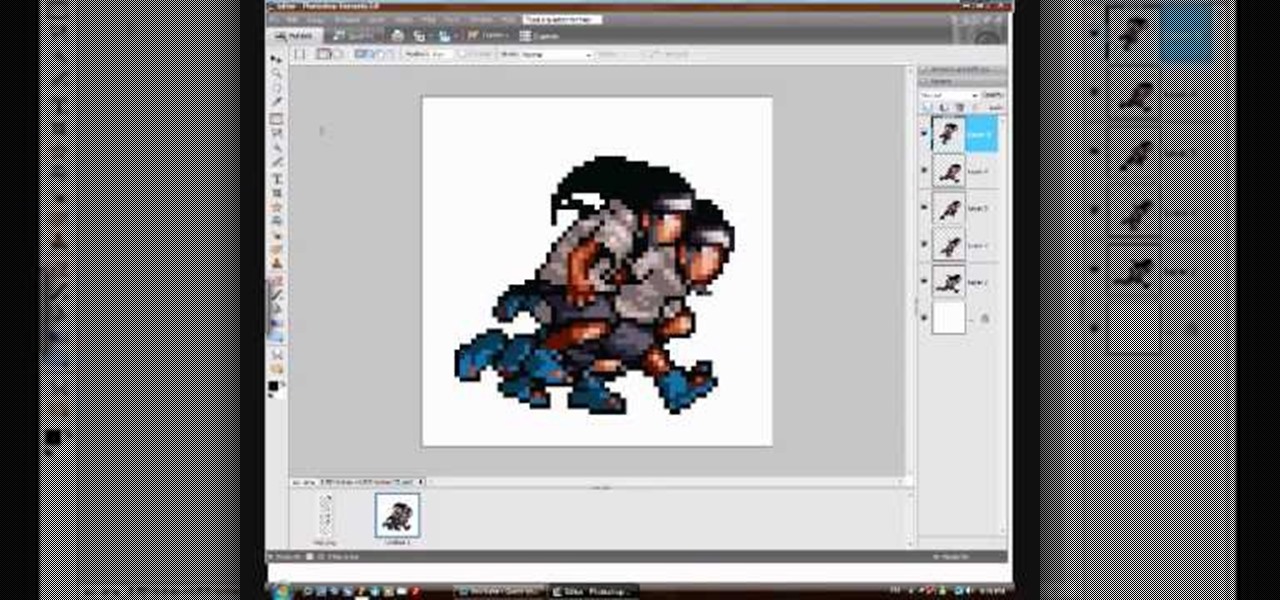
Steps to make Sprite animation in Photoshop are:1. Open a spreadsheet of your own choice; in this case we are going to take running animation.2. Once your spreadsheet is loaded, zoom-in until you get a four page, for ease of use.3. Zoom-in to the required movement, after zoom, select the image and open File and from that click New File and click OK (Dialog Box), and you will get a work space to work on with your selected image. The feature makes it simple for one character animation (work).4....
SchizoFilms brings the viewers instructions on how to make an animated GIF in Windows Movie Maker. First open up Movie Maker. You will need to import pictures. To do this, click the button on the top left of the screen that reads 'Import Media'. Find your files here and import them into Movie Maker. Now, you will want to order the pictures in the sequence you want them to show up in. To do this simply drag and arrange them. Now, you can make adjustments for how long you want each to run by dr...
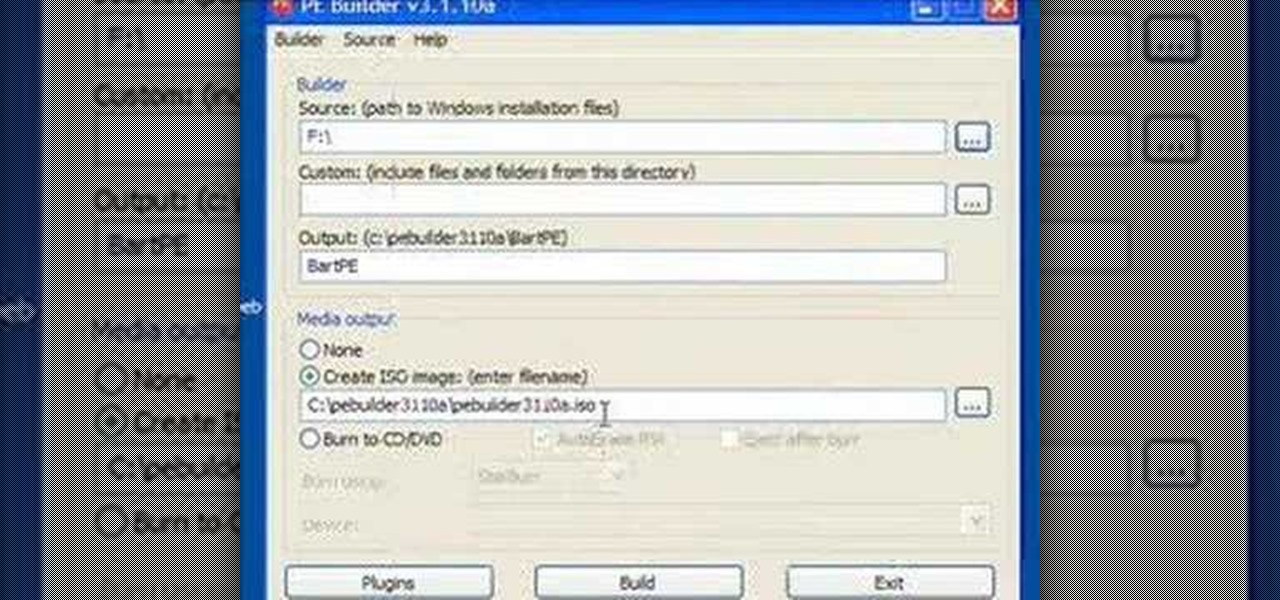
Steve Lee Ignacio explains the procedure to be followed to build a Bart PE Professional Rescue CD. He says that the basic requirements for completing this process is a Windows XP Pro or Home CD, a Bart PE builder, a Windows Computer, a program to burn .ISO files and a CD burner. He then explains the various steps involved in building the Bart PE CD, the first of which is to download latest version of Bart PE Builder using a search engine like Google. Then he explains the second step which is ...
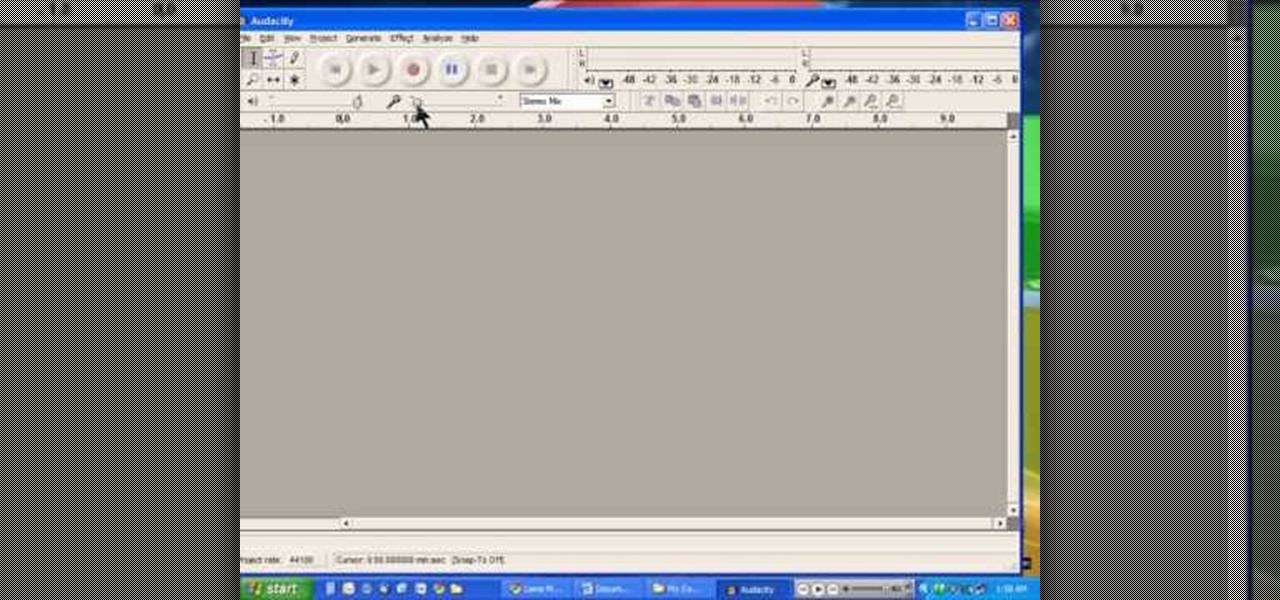
In this video from PCRescueRepair we learn how to record streaming audio from any website using audacity. To get audacity just go to google, type in audacity, click on the link for audacity, and download audacity to install this on your computer. Also you need the LAME mp3 encoder which is on the audacity website. Now he takes you through the steps to do this task. Go into audacity and from the drop down change to stereo mix from microphone. On output adjust to max. and on input adjust the vo...

View the absolute value of a number as its distance from zero. When you take the absolute value of a number, you always end up with a positive number (or zero). Whether the input was positive or negative (or zero), the output is always positive (or zero). For instance, | 3 | = 3, and | _3 | = 3 also. This property that both the positive and the negative become positive makes solving absolute-value equations a little tricky. But once you learn the "trick", they're not so bad. Let's start with ...
Looking to change your YouTube Favorites to an mp3 to carry them with you everywhere? In this video, learn how to do so with the help of a download from dvdvideosoft.com, and this tutorial. Instructions for are listed below as listed by videomaker, vakama380:

You want to transfer your cassettes to digital music but don’t have a clue where to start. With these tips and the right equipment, your old music will sound brand new.

If you want to maximize your work output, follow these simple steps. You Will Need

The Galaxy Note 20 series has one of the largest screens on any smartphone. Such a massive display not only makes it easy to enjoy videos, but it also makes split-screen mode more viable, as each half of the screen is large enough to enjoy the content — including two different videos.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

Even though smartphone audio quality has improved in recent years, the tiny built-in speakers aren't always loud enough. But if you want to turn the volume up to 11, all you need is a few household items to make a rig that will amplify your phone's speakers throughout the whole house.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.