Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

When Android 5.0 rolls out to the Nexus 5, several changes and new features will come along with it. The over-the-air update is already rolling out, and if you don't want to wait, you can get it right now.
Since its creation, Arduino has been growing exponentially more popular as DIY enthusiasts and Makers alike realize its potential. As new versions of the device are released, many easy-to-use peripherals are showing up on the market also.

BEATS by Dr. Dre started making their studio-style headphones and speakers over four years ago, which claim to help listeners actually "hear" music as it was intended by the artists, since commodity headphones and earbuds are known for producing lackluster results. But you can only go so far with Beats Audio headphones, since your computers and mobile devices weren't built to take advantage of high quality audio equipment.

If you're like me, the words 'monostable circuit' mean nothing to you. Until just recently, I had no idea what a monostable circuit did, or why anyone would ever need to use one.

Okay, you can't really become the king of the world by stacking three pistons. For that, you have to stack four pistons.

The guitar is a double-edged sword. I've played all my life, and though I love the act of guitar playing, there are quite a few people I could live with never hearing play again—ever.

What's the first thing you would do once you realized you were lost in, say, a desert? If you're like me, you would immediately pull out your cell phone and start dialing every number. But what if you have no service? What if your battery is dead?

This video tutorial is in the Software category which will show you how to convert a video file to play on your iPod with Super. A video file to play on iPod, it has to be MP4. Any other type of video extension will not work on iPod. So you will need to convert other video files in to MP4. For this you will need software that is free and it is called super. You can do a Google search for 'super software', download and open it. You can use this software to convert a lot of files. The output co...

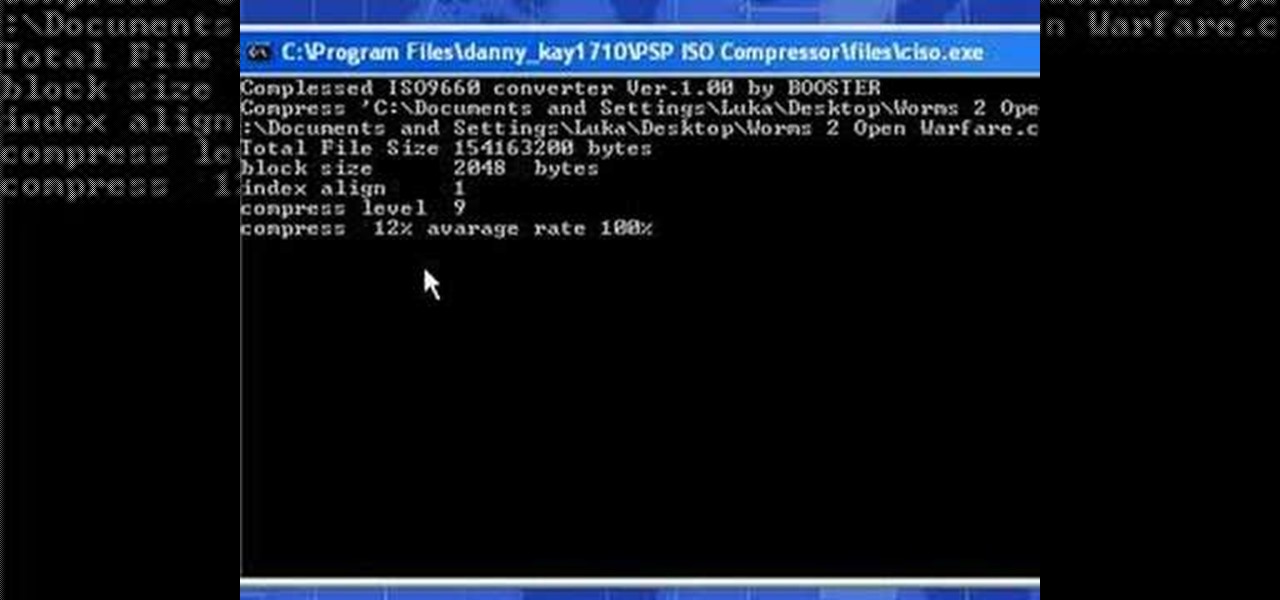
In this video the instructor shows how to compress PSP ISO games. Normal size of a PSP .ISO game is too big. This can consume a lot of space on your hard drive or other storage media. One thing to do to solve this problem is to compress it using PSP ISO compressor which reduces the size. Download the software from the link given in the tutorial. Now open it and select the option Compress ISO to CSO in the left side. Now where it says input files click on the end with the three dots. Now brows...

If you just got some banging new subs for the trunk of your car, then you're just about ready for the ultimate car stereo. But what kind of amp are you going to get to power those subwoofer speakers? Learn about the basics of car amplifiers in this video from Sonic Electronix, where they discusses the purpose of a car amplifier, as well as the parts of the amplifier. This includes the terminals, adjustments, types of amplifiers, and amplifier channels. Before putting together your first after...

Video may have killed the radio star, but will volumetric capture and augmented reality kill the video star?

While a new museum to house the original torch of the Statue of Liberty is under construction on Liberty Island and scheduled to open in May 2019, New York Times readers can now view the sculpture in their own space through augmented reality.

Epic Games released Unreal Engine 4.21, bringing a number of new features, bug fixes, and improvements for augmented reality development, including deeper support for Magic Leap One and the addition of support for the Windows Mixed Reality platform and headsets.

In stock Android Oreo and below, the volume rockers change ringer volume by default unless audio is currently playing. In order to adjust media volume when media isn't playing, you have to tap the down arrow next to the ringer volume slider that appears at the top of the screen to see the option. Now, Android 9.0 Pie has flipped things around, giving media volume the limelight.

Do you know when you're going to die? Your iPhone or iPad does. That's the premise behind Death Mask, an experimental app developed by Or Fleisher and Anastasis Germanidis.

It was a long overdue announcement when wireless charging was revealed as a feature in Apple's 2017 iPhone lineup. While certainly a welcome addition, wireless charging would only work with up to 5 watts of power, which meant no fast-charge capabilities. That's not the case anymore — here's how to fast-charge wirelessly with the iPhone 8, 8 Plus, or iPhone X.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

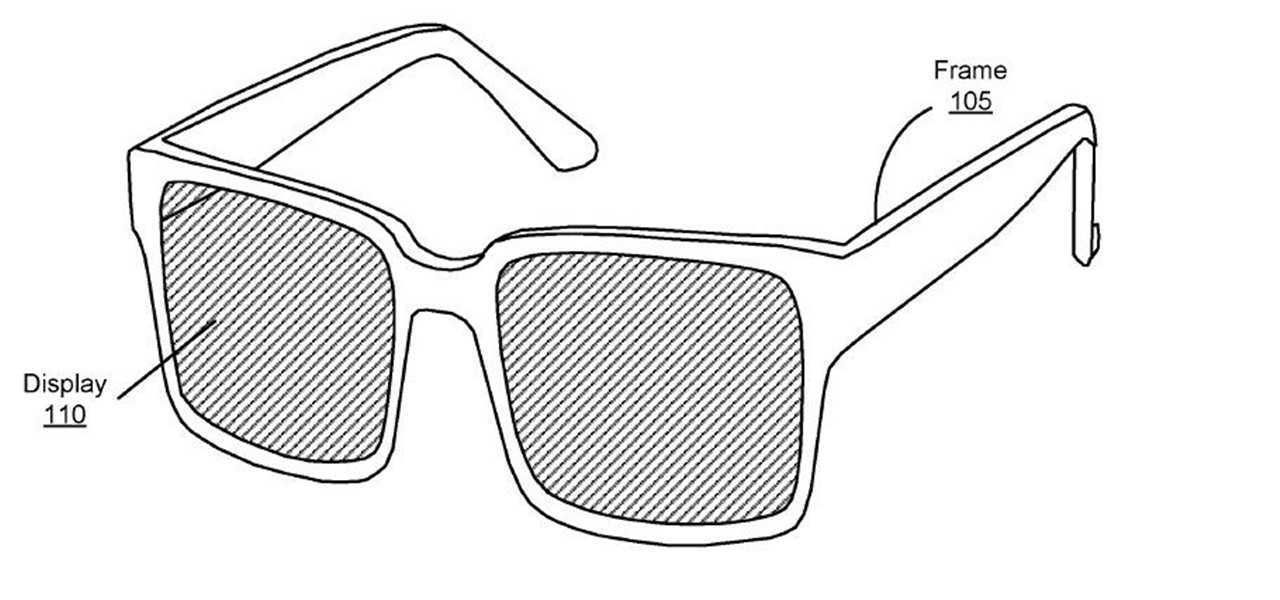
A patent application for waveguide-based smart glasses submitted by way of their subsidiary Oculus sheds light on Facebook's plans to escalate their augmented reality efforts.

Theorem Solutions, a company that helps engineering and manufacturing companies reduce their costs, has taken the next step with their mixed reality technology. The company has now added their own app, called Visualization Experience, to the Windows Store for the Microsoft HoloLens

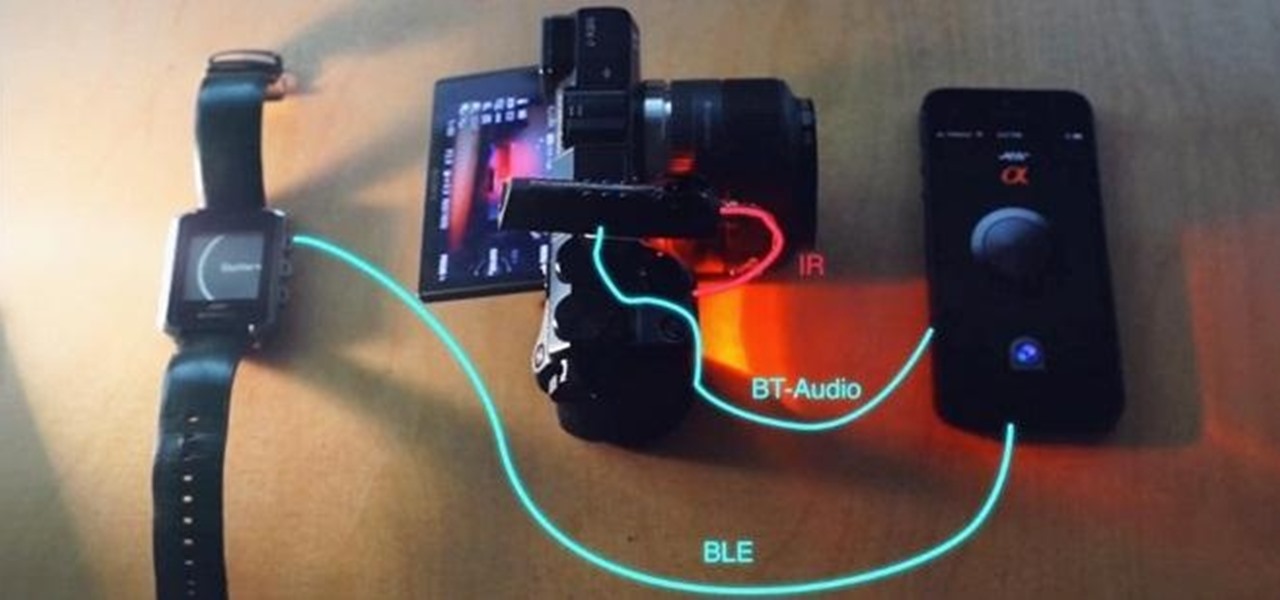
Google Camera, the default shooting app on Nexus devices, is finally getting a feature we've been anticipating for years. As evidenced by a recent APK teardown done by Android Police, the beginnings of a new RAW capture mode have already been baked into the latest version of the app, which indicates that Google Camera will soon have the ability to store an unprocessed copy of the exact image your camera sensor captures.

Welcome back everyone. This article isn't going to contain anything related to scripting, but rather some updates about the series. We'll be quickly discussing what we've covered so far and what is to come.

According to the American Osteopathic Association, "1 in 5 teens has some form of hearing loss," and some experts believe it's because of an increase in headphones use. While I understand that music, movies, and video games help keep children preoccupied, there's no reason why they can't be entertained at a healthy hearing level.

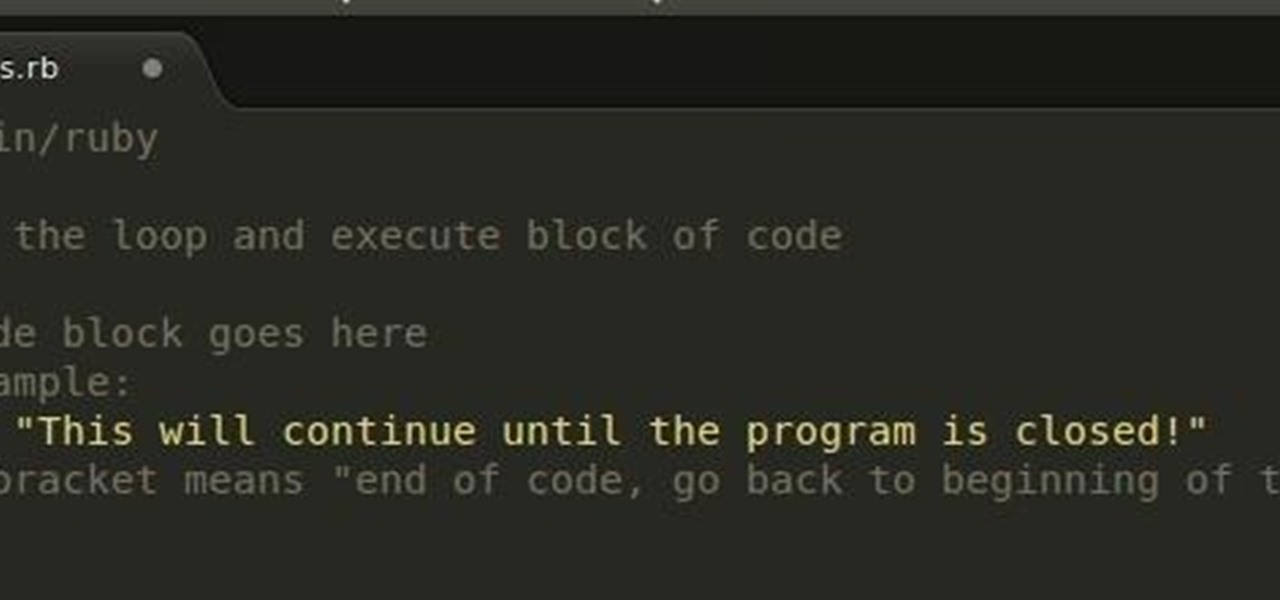
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

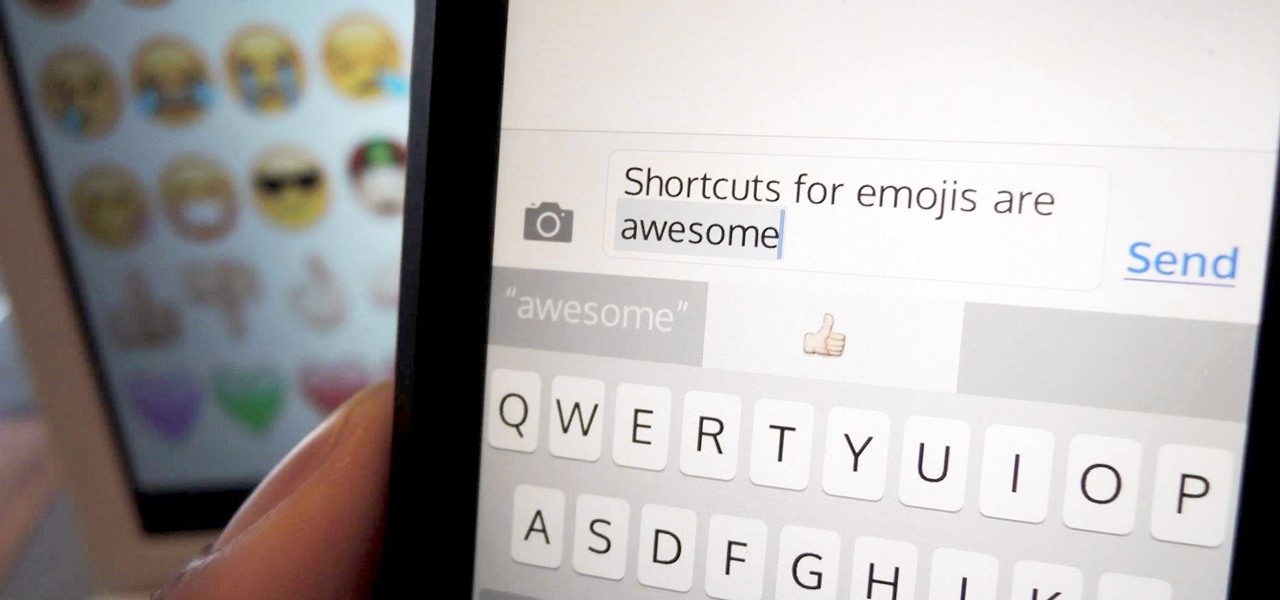
If I told you that people who use emojis in their conversations have more sex than plain-text users, would you believe me? According to a recent study launched by Match.com, men and women that use emojis have more sex than those who do not. If you were looking for an excuse to increase your emoji output, you may not find a better one than that. To make your emoji typing as smooth and seamless as possible, I'm going to show you how to create shortcuts in iOS 8 for all your favorite use cases. ...

Well Welcome Back My Fellow Hackers. What is Slowhttptest? You may be asking. Slowhttptest is a Application Layer Denial of Service attack aka an attack on HTTP. You can read more about it here and also download it if you don't have Kali Linux. slowhttptest - Application Layer DoS attack simulator - Google Project Hosting.

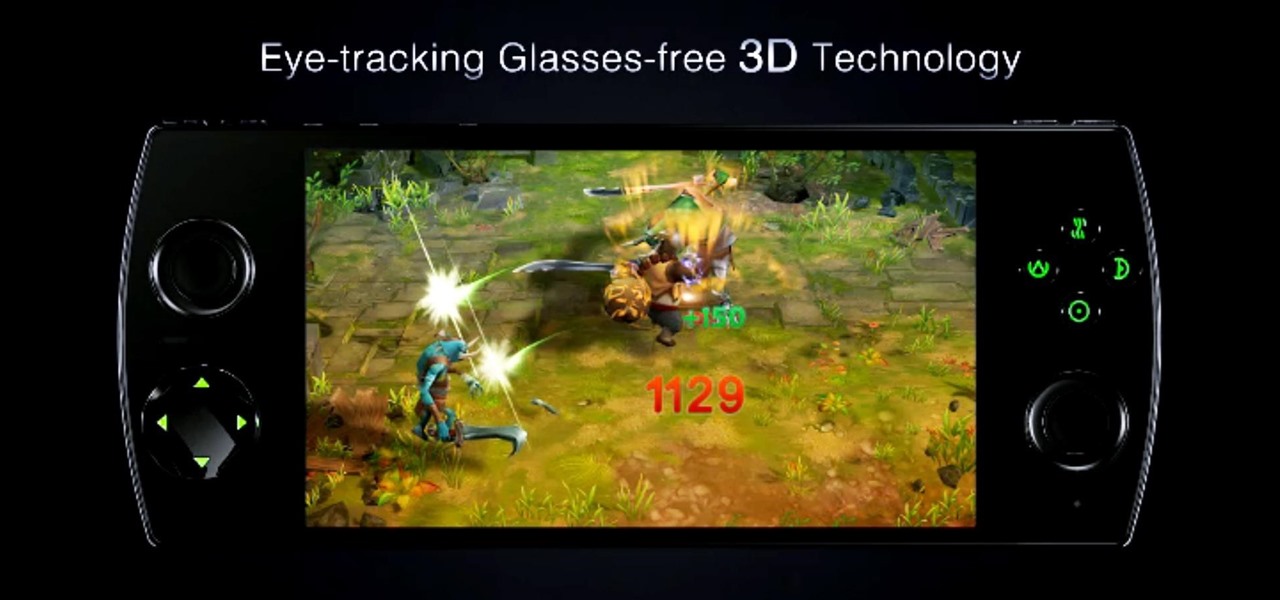
The upcoming W3D gaming smartphone by Snail isn't like anything you've ever seen before. It's pretty much a cross between an Android phone, Nintendo 3DS, and PlayStation Vita. It runs on Android, has a 3D screen similar to the 3DS, and gamepad controls like the Vita, making it one hell of a portable gaming device (that's also a phone).

Headphone cords are one of those things we all deal with because it beats the alternative (no music). But they can be so obnoxious—they're always getting caught on things, and they seem to be perpetually tangled. If you have ear buds, you can make a simple a cord container to keep them organized, but over-ear headphones are a little more tricky.

Unless you're a pretty avid home cook, you probably don't know a lot about sous vide. Sous vide is a low-temperature cooking method where food is cooked in vacuum-sealed plastic bags in a water bath for a prolonged period of time.

Being able to run mobile apps on a computer is nothing new. Maybe you don't have a mobile device, or maybe you just like seeing the apps on a larger screen. Whatever the reason, with programs like Bluestacks, you can use your laptop to Instagram, play Angry Birds, and run countless other apps made for smartphones.

You can add Bluetooth capability to an old stereo, a retro mouse, or even your car's cassette deck. If you can think of a device, someone has probably found a way to control it with Bluetooth.

Most of us have given up our big, bulky stereos in favor of smaller, sleeker models, but how many of us actually get rid of the old ones? If you don't like the idea of throwing out or giving away electronics you spent good money on, you can always upgrade them instead!

Looking to transmit some super-secret audio communications to your other spy buddies? A laser is the perfect tool for getting your sounds heard from a small distance—without anyone intercepting them— even if it's just a cover of your favorite pop song. A laser audio transmitter uses light rather than radio waves to transmit sound. This is a much more secure way to send audio communications because the laser is a focused beam of light, whereas radio waves are not controlled, so they can be pic...

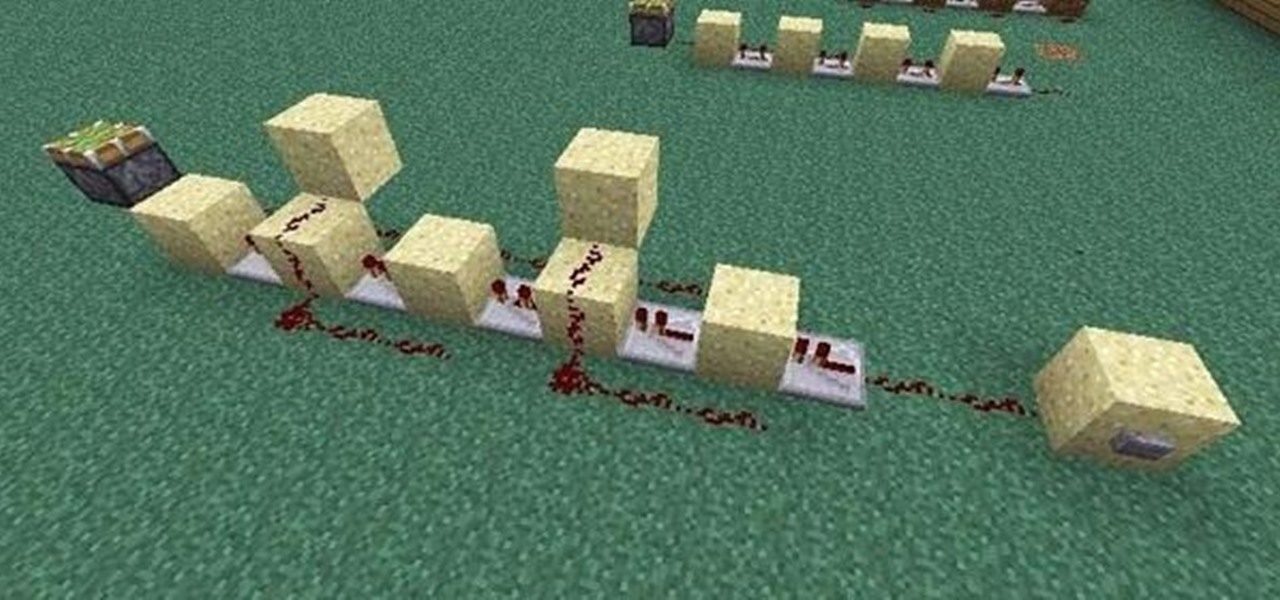
If you're at all like me, you constantly get frustrated that repeaters only boost redstone signals in one direction. It's annoying!

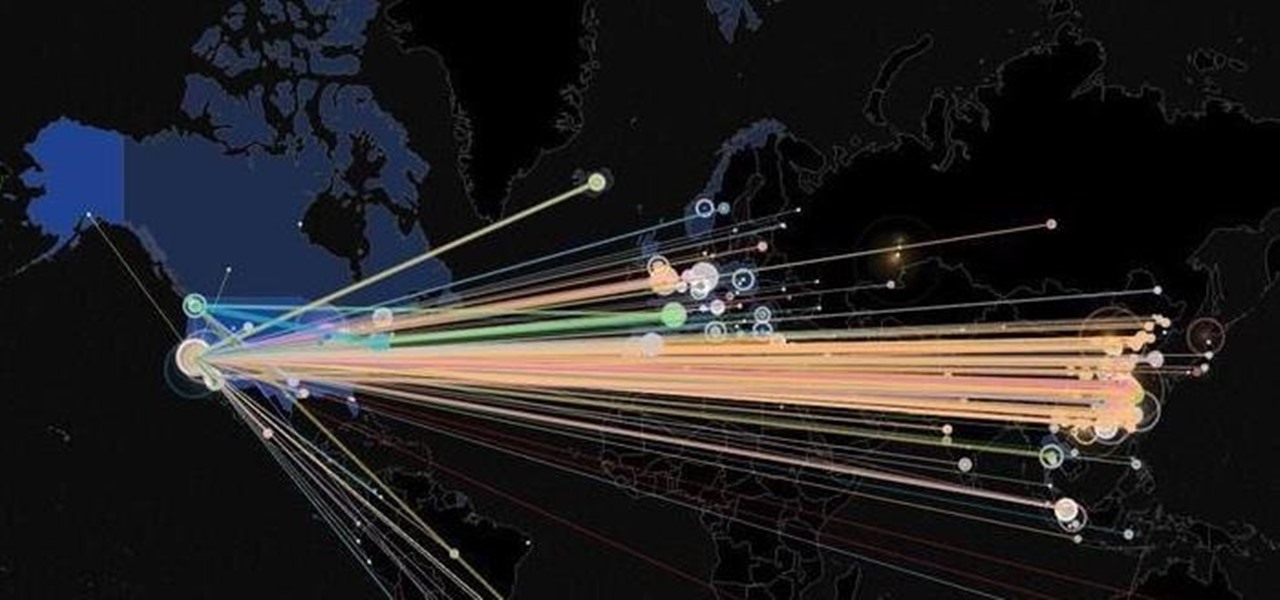
Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.