It looks like all the unregulated fun and games we were having promoting products on Instagram is about to get, well ... regulated. According to a new report by Mediakix, 93% of celebrities on Instagram are not in compliance with the Federal Trade Commission when it comes to posting paid content.

The smartphone has become one of the basic reasons for sore eyes. If you are addicted to your beloved smartphone, there is a fair possibility that your eyes will be paying off its expensive price. If you use your smartphone, tablet, laptop or any other similar gadget consistently, you may experience tired, dried, itchy eyes and also severe headache. Your vision can also become blurred by the time, which it means it is affecting your eyesight. However, you can lower down your eye strain by mak...

Tequila is a hard liquor that's often been misunderstood. Produced from the agave plant, this aged spirit has complex flavors that bloom the longer it's aged and can rival the finest scotch.

True story: a friend of mine regularly started a fight with her boyfriend everyday at 4 p.m. Every day. This went on for years until he finally got the bright idea of shoving a granola bar at her the minute she came home from work. Shazam! The fights were a thing of the past.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

Work is commonly composed as a Microsoft Word document but if you would like to convert that document into a PDF file that any operating system can ready you will need to follow a few simple steps.

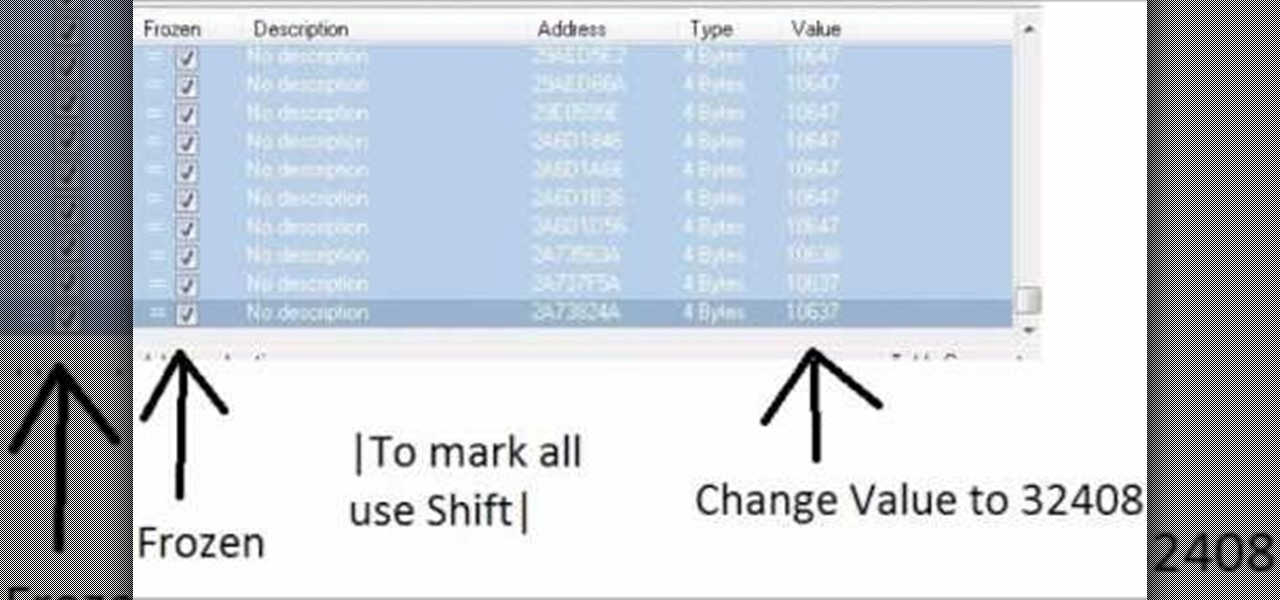
Increase your damage output in World of Warcraft! This tutorial won't work on all servers, and is better on private servers than public. All you need is Cheat Engine - buy some mundane items, and then use the program to turn them into rarer, better items.

Change your damage output, and make sure that every time you land a blow, it is a critical hit. You can also hack Ninja Saga to rocket your character to level 60 - all you need is Cheat Engine and Firefox.

This tutorial goes over using the crop tool in iMovie '08 to change the orientation of your clip or crop the clip. This tool is very useful for auto-fitting your videos to letterbox, or ipod output sizes.

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

The landscape of podcasting has exploded in recent years, with everyone from dedicated longtime podcasters reaching the mainstream spotlight, to traditional media personalities moving from TV, radio, and newspapers to grab a slice of the listening pie. The good news is that the barrier to entry is relatively low, so even if you're not a celebrity or media luminary, you can still get your voice out there by starting a podcast.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Hello friends. This is actually my first how to.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

This video will help you learn how to create an Explosive rainbow color swath in Photoshop. First open a new file, keep the width 845, height 475, RGB color mode and white background.

Download the P2 Step-by-Step Reference Guide. With Avid, editing footage captured with the Panasonic HVX200 camera is fast and easy. Avids system uses the same native file format as Panasonic P2 memory cards, so theres no need for any transcode, capture or file conversion process at all. You can edit directly and immediately from the P2 cards if you like or have Avid Media Composer create a rapid backup of your files. Nothing could be simpler or more immediate.

This software tutorial shows you how to create good renders from 3ds Max 8. It's one thing to create cool models in 3D Studio Max but if you can't get the lighting right and output a good render, then it's pretty useless. So watch this tutorial and get tips on creating a good render in 3ds Max 8.

This tutorial is for ultra beginners in .NET, it shows how to create a simple console output and simple form in VB.NET and C#. It is done through notepad and without any IDE.

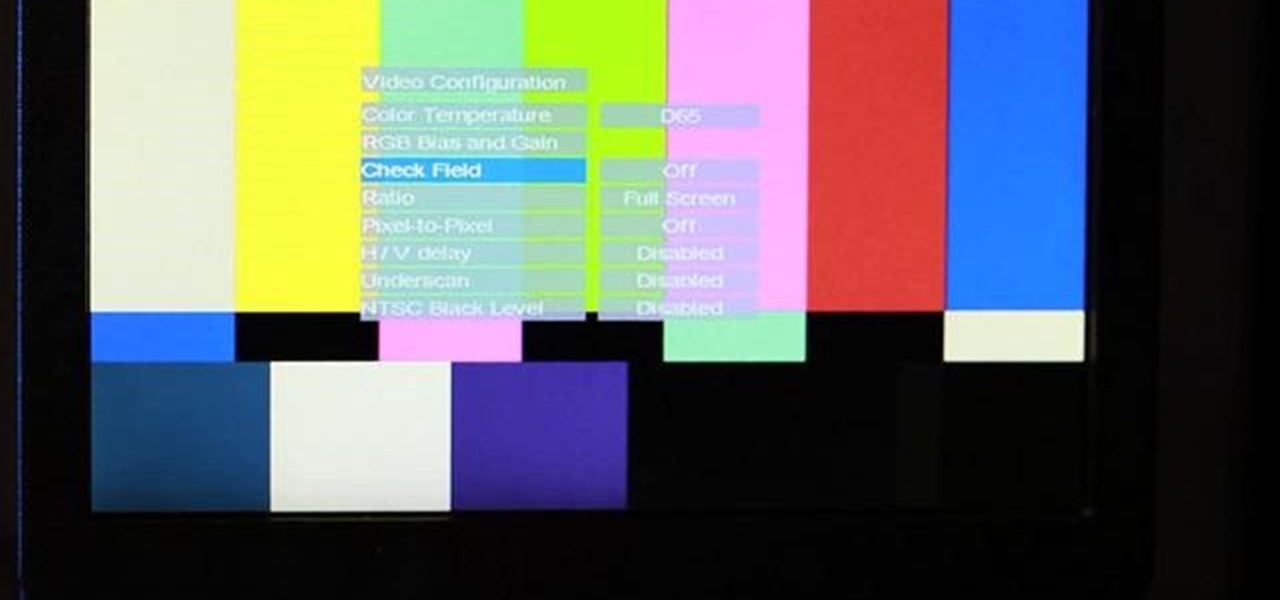
Check out this cinematography video tutorial on how to use calibrate an NTSC camera monitor, specifically a Marshall monitor.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.