This is a great website to browse if you're not into slathering unpronounceable ingredients onto your skin. The beauty industry is very much self-regulated, which means it is not required by the FDA or by any law to disclose all of the ingredients in a product. And there is also no legal definition of "natural" or "organic." So yes, that "natural" jar of cocoa butter you're using might be no better for you than your generic body lotion, and it may still contain cancer-causing agents.
"Your bathroom is a minefield of toxins." Sounds a wee bit dramatic, no? But the video isn't kidding around here. A lot of the shampoos, lotions, creams, and soaps you use have ingredients linked to birth defects, cancer, and learning handicaps. And just think about it - we're using these gnarly ingredients on our skin every single day.

Papercraft + Transformers = Fanboy nirvana. Papercrafting is enjoying a renaissance thanks to its nerd-love. Popularity of card modeling boomed during World War II when paper was one of the few items whose use and production was not heavily regulated. Micromodels, designed and published in England, were a popular source of military-themed modeling designs.

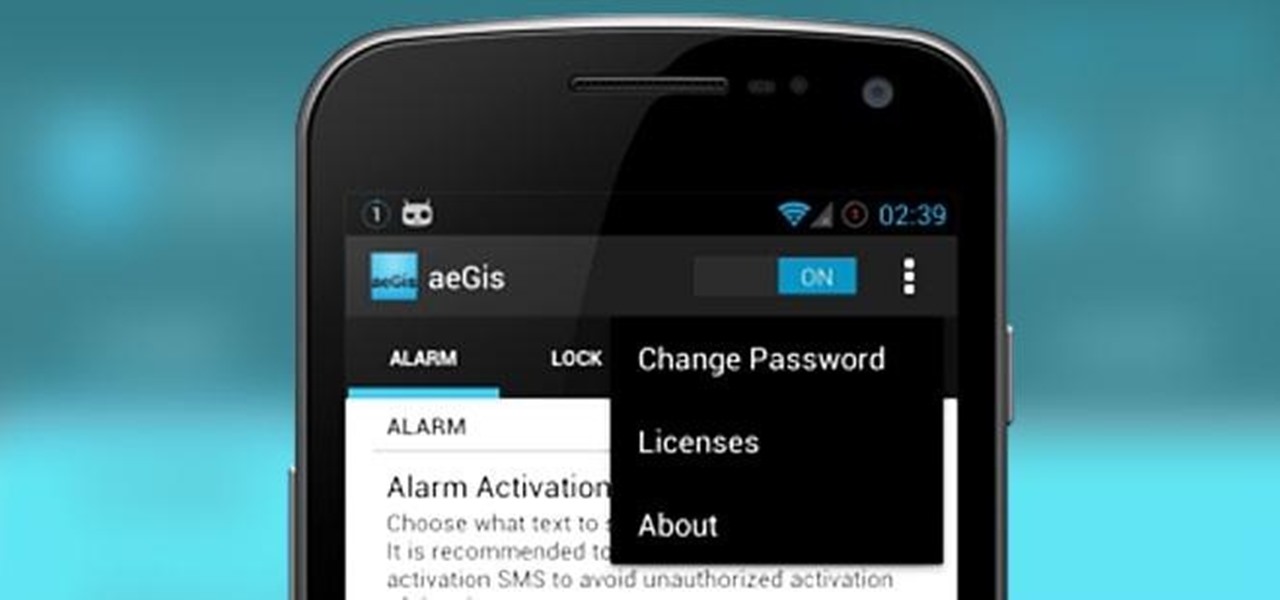
How many of you have or know people who have a smartphone? There's a lot of you, right? Well, depending on how most of you use those smartphones, there could be all kind of sensitive information stored on it, and that doesn't just mean sensitive personal information, but it could also contain all sorts of sensitive corporate data for work.

MAME/SNES/GENESIS/NES/+ Arcade style 2 player cabinet. Features

Blizzard Cam, a 40 mph mobile spycam on skis, spies on a group of adorable polar bears (um, minus the blood stained faces) as they devour a pile of remains. Operated remotely, Snowball Cam is released from the Blizzard if scientists detect the bears may attack the device. The decoy can roll across most terrains (even up hill), and easily distracts the bears into a game of soccer. From a BBC TV program on polar bears.

In this Computers & Programming video tutorial you will learn how to establish a Remote Desktop connection in Windows XP. 1st you got to enable remote desktop. To do this go to start, right click on My Computer and click on properties. Then click on the remote tab and click on ‘allow users to remotely etc’ and click on ‘select remote users’. Click add and add your account. Click OK, apply and again OK. Now get your IP. Click start > run and type cmd. In the cmd prompt type ‘ip config’ and not...

Here's a two-in-one "tutorial" for you today; how to fold a paper airplane, and how to execute a belated St. Patrick's Day manicure. Just follow along and do as the da Vinci does—our adroit instructor is a surgical robot, with a hefty price tag of approximately 1.3 million dollars, plus several hundred thousand dollars in annual maintenance fees. In truth, the da Vinci doesn't have the brain power to dictate the folding of a simple origami plane, nor does it know how to paint orange and green...

Maybe your kids are using iPhone/iPad too much, as a parent, you want to know what they are having to deal with to help guide them through of that. Here is the tutorial on how you can parental control your kids on iPhone/iPad. You are able to monitor as well as take control of their devices. Kids’ activities on iPhone/iPad like SMS, chats, web browsing will be recorded and you can check them remotely with e-mail without getting access to the devices. OK, here comes the steps: Step 1:

For some time now, I've been dying to make the trek to the world's largest airplane graveyard outside of Tuscon, AZ. The ultimate field trip that I never seem to get around to.

For a long time, Apple has had Remote—an app that can be used on any iOS device in order to remotely control iTunes. Remote allows users to walk around their home and change the music by simply going through their phone. And now, Android has released its own version of the Apple Remote app! Retune is a free app found on Google Play that has the capability to control iTunes—change songs, TV shows, and movies—using your Android device. You can view the entire iTunes library on your Android devi...

Wow, this robot has incredible movement. "A-Pod is an ant inspired hexapod robot with a 2 DOF abdomen (tail), a 3 DOF head with large mandibles. 6 legs with 3 DOF each. Total 25 servos. This video demonstrates body movement and mandible control... The robot are remotely controlled with a custom 2,4 GHz RC transmitter."

Make Magazine presents UC Berkeley's professor of architecture, Cris Benton.

The only thing better than successfully pulling off a new experiment is doing it with household materials. You get to laugh in conceit as professional scientists everywhere spend all their grant money on the same project you just accomplished with some under-the-sink chemicals! However, there are times when DIY gets dangerous. Some household chemicals are not pure enough to use and some are just pure dangerous. Let's take a look at two problems I have encountered in the course of mad sciencing.

You're rocking out to your favorite new song playing in iTunes on your Mac, and you've got to go for a run or meet your friend at the local coffee shop. But you're grooving to the music and don't want to leave until you've found the same song on your iPhone, to continue jamming your heart out. There's a few problems with this scenario though: First, it's time consuming. Second, you're most likely to start the song from the beginning, ruining the groove you had going.

If you're the kind of person who misses the bright, sunny days of summer during the colder months, Michail has the perfect addition to your home. He built this "Nuclear Explosion" Chandelier that's as bright as daylight, so you can recreate the feeling of summer, no matter what time of year it is. It puts out 99,400 lumen (a typical 60W light bulb only produces 800 lm), so it takes quite a bit of electricity to run. Michail used 7 metal-halide lamps, which are much brighter and more energy ef...

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Last week, I introduced a project that demonstrated how a BB machine gun could be made out of a soda bottle using only a handful of readily available parts. If you missed it, you can check out that project here before reading on.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

WonderHowTo is currently seeking a new staff member to head up FarmVille World as a highly active community admin. This new community leader would clean up any and all troublesome issues relating to the World, write extensive guides, and be available for all World member FAQs. Help us continue to grow FarmVille World into an increasingly vibrant FarmVille community!

If you're the proud owner of a Canon EOS DSLR, then you'll be glad to know that you no longer have to use EOS Utility on your computer to enable remote live view shooting with your camera. Now, all you need is your Android equipped smartphone (sorry iPhone users) and a new mobile app called DSLR Controller from Chainfire.

Every experienced gardener knows that the secret to better blooms, brilliant greens, and tastier fruits and vegetables is a healthy soil. Improving the soil before you plant is the best head start to growing healthy, hardy growth in your garden.

Looking to go "Green" When I'm looking to do new remodeling projects around the house, I find myself asking, is this Eco-Friendly? Is this main stream America brain-washing me into a "Greener Tomorrow?" I doubt it! Embracing Eco-minded products is not just good for preserving the natural environment, but it's about creating a healthy living environment in your home as well.

The da Vinci robot has proven to be an endless source of amusement to surgeons everywhere; in Japan, it folds origami cranes, at the state of Washington's Swedish Medical Center, it flies paper airplanes and gives manicures. It's a battle of the hospitals—who can make their pricey pony perform the greatest trick?

What would it be like to have a super-realistic humanoid modeled after you...and then come face-to-face with the moving, life-like version of yourself... Creepy? To say the least.

This is the first of two Video's introducing you to your fingers from a Hand Analysis perspective. The Fingers mainly govern the mind and thinking. Somewhere in the vast fabric of time somebody discovered that the length and inclination of each particular finger can bring out certain personality traits. I still find it amazing and satisfying to see somebody with a longer than average 'little finger'(Mercury-communication), that sticks out that can't stop talking and buzzing around all excited...

BPA: Why Plastic Ain't Good For You BPA or Bisphenol A is in many of the products we use. Everything from Ziploc bags to shower curtains, we are exposed to BPA all the time.

Robots are great for performing tasks that are otherwise too dangerous for man (e.g. dead body extraction bot). BeetleCam is a cute little bot that takes all the danger out of wild life photography. Controlled remotely from a Range Rover about 50 yards away, BeetleCam ventures where no sane photographer dares to go (at the feet of a charging elephant, say). "We thought that Elephants would be an easy subject for BeetleCam’s first outing. We were wrong… we quickly learned that Elephants are wa...
Be honest about your pet's ability to travel. If your pet is very young or old, or is ill, pregnant, or recovering from surgery, it may be better for all concerned to look into a pet sitter or kennel rather than take a chance on injuring your pet by taking it with you. If you are in doubt, ask your veterinarian. If your pet has not traveled before, try a short overnight or weekend trip first.

Google has caught a lot of flack for various privacy infringements over time. Google Buzz was the latest uproar, when lack of proper prior testing allowed the tool to expose a slew of information users did not necessarily want shared, resulting in massive complaints. A Harvard student even went so far as to file a lawsuit (read more).

We've had to resort to actual spying to get information on the highly anticipated Tesla Model 3, but today Elon Musk himself gave out some exciting news. The Model 3 is going to be officially unveiled in July, according to Musk's Twitter. Musk also revealed that Tesla will unveil their electric semi-truck in September. It will be interesting to see if Tesla plans to add Autopilot to that truck and get themselves in the autonomous truck game with Otto.

Windows users have looked on with envy at Mac owners wrangling torrents with ease for years. Now, finally, a new Windows torrent client is making downloads easier, safer, and more customizable.
I assume you are on the same network with your router 1 - open a terminal window

Charlie Miller and Chris Valasek conducted an experiment earlier this month that ended up with a Jeep in a ditch, although the driver didn't drive it there. The two remotely hijacked the car, controlling it through a laptop and a cell phone. FCA says vehicles from the 2013 and 2014 model years with 8.4-inch touchscreen are affected. That includes Ram pickup trucks, the Dodge Durango, the Jeep Grand Cherokee and the Viper. Some 2015 Chrysler 200 sedans are also affected.

If getting Christmas presents ready ahead of time has never been your forte, be assured that it has never than easier than before to assemble together a last-minute Christmas gift for all your loved ones and favorite people (and maybe not-so-favorite people you are obligated to buy gifts for) on Christmas eve.

Security is always a top priority for our smartphones. Leaving your phone at the bar or even at a friend's house can leave you open to hacks and lead to the loss of sensitive information.

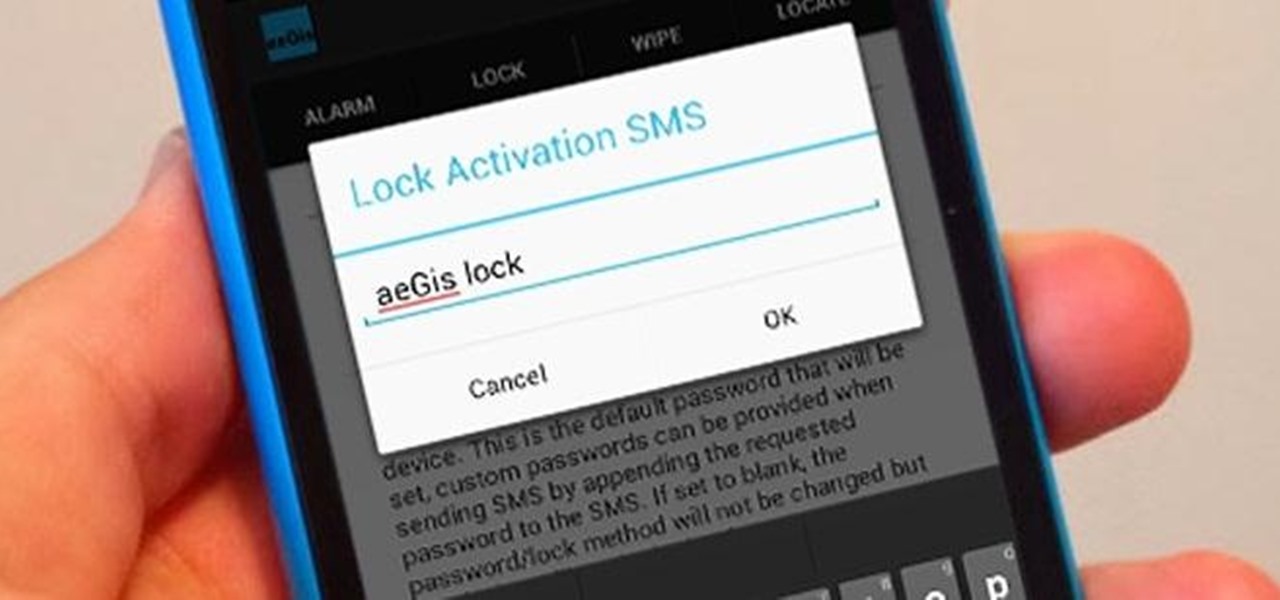
The great thing about security apps (other than the obvious) is that there is an abundance of them littered throughout the Google Play store. Cerberus, Got Ya!, Avast! Mobile Security, Norton Security & Antivirus, and Android Lost Free are just a few of the gems you can find in the plentiful sea of security apps for Android. Once in awhile, though, a new security application comes along that stands out from the rest, like AeGis.

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

Uh oh. Somebody screwed up big this time. It has recently been reported that Iraqi insurgents have used $26 software to intercept live video feeds from U.S. drones located in Middle East conflict zones. The drone (a remotely piloted aircraft) is considered one of the U.S. military's most sophisticated weapons. Apparently not sophisticated enough, however.