Burning Man 2018 is underway, but Intel and the Smithsonian American Art Museum are giving those not in attendance the ability to view the art from the event through Snapchat.

We can't be in two places at once, but with virtual touch interfaces we can theoretically use a machine to act as our second body in a remote location. Over at MIT, Daniel Leithinger and Sean Follmer, with the advisement of Hiroshi Ishii, created an interface that makes this possible.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

One of the major criticisms of virtual reality, and much modern technology in general, is the antisocial nature it creates. But vTime wants to overcome the isolating nature of VR headsets with a virtual hangout space for you and your friends.

To take group shots and better selfies on your iPhone, you can use your Apple Watch as a remote shutter for the Camera app—but what if you want to take a snapshot or video with a different app?

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

With all due respect to the fine folks at DrinkTanks, it's a little surprising that no one came up with their idea sooner. After all, last I checked, beer was pretty darned popular.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

As most everyone knows, Android and Apple don't get along so well. Even the users don't get along well, with Android and iPhone users constantly berating and insulting each other online—any chance they get. I should know, since I was one of them, but I'm now rare breed who's learned to appreciate both. People just need to realize that they have their own unique strengths—Android with its customization and Apple with its simplicity.

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

Males fight for dominance in order to gain access to the limited supply of female eggs. This is why male birds expend energy on brightly colored plumage, but female birds do not.

You can use Twitter to print Instagram photos, track news and weather events, or even remotely shut down your computer, and if you're familiar with IFTTT, there's no shortage of ways your account can help automate your life.

A faulty or broken thermostat can be one of the most annoying things to ever happen to your house. It's always too hot or too cold, and you can end up wasting money on your electricity bill.

The streets of Tokyo are about to get a lot scarier (or more awesome), after Suidobashi Heavy Industries unveiled their latest project: a 13-foot tall, customizable, piloted robot. It's armed to the teeth with a water bottle rocket launcher and a BB Gatling gun capable of firing 6,000 rounds a minute; all for the very reasonable price tag of around 1.35 million dollars.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Open TikTok, and you might find yourself spending hours watching video after video. While each video is usually pretty short, it's highly possible to binge-watch hundreds at a time. It's even more fun to create your own. But as a parent, you may not want your children falling into this same trap, and it's easy to limit how much time they spend watching TikTok videos on their iPhone.

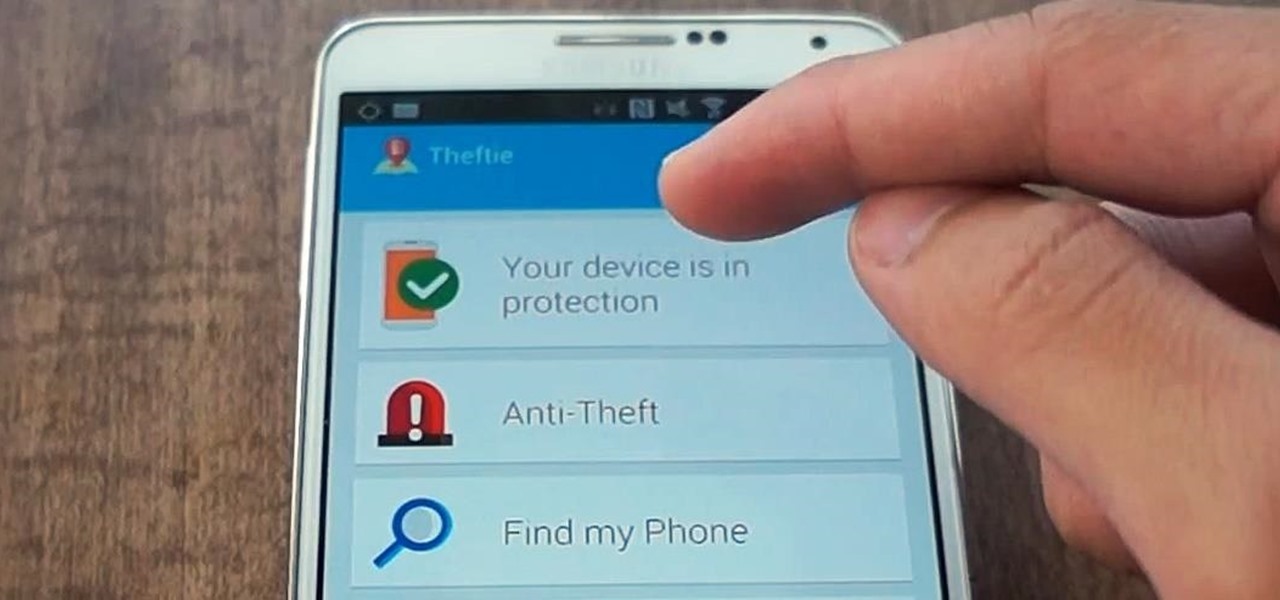
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

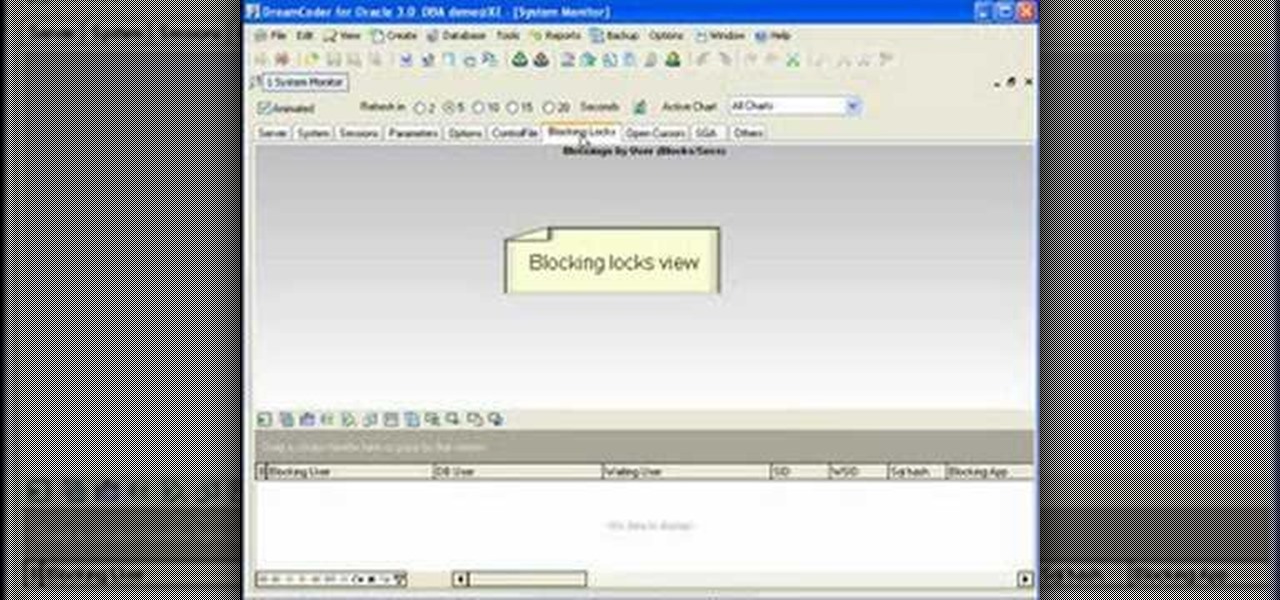
If you're new to DreamCoder for Oracle, one of the first things you may want to know how to do is to monitor a remote Oracle database. Happily, this tutorial will walk you, step by step, through the process. To learn how to monitor a given Oracle database remotely via DreamCoder for Oracle, take a look!

One of the greatest trends to emerge from this period of home isolation is the live concert broadcast from bedrooms and living rooms across the planet. Though public gatherings are on hold, you can still impact people with your music and mixes. In fact, it's helping many people get through this confusing time.

The HoloLens 2 hasn't even reached most of the market, but it's already a big-time TV star. Microsoft's augmented reality device made its primetime debut on FOX TV last night on an episode of the hospital drama The Resident.

Sure, Tony Stark was able to build the original Iron Man suit in a cave with a box of scraps, but can the average do-it-yourselfer replicate the EDITH smartglasses from Spider-Man: Far From Home in a similar fashion?

Simulated training can help soldiers and sailors learn how to use their weapons safely, but simulations can sometimes lack the stressful environment of a real firefight.

With barely a whisper of augmented reality during the first day of its developer's conference, Samsung came out swinging on day two with the introduction of its version of the AR cloud and a partnership with Wacom that turns Samsung's S-Pen into an augmented reality magic wand.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

Another AR cloud candidate has emerged in YOUAR, a startup that has developed a new system that enables persistent augmented reality experiences on iPhones and Android devices.

Following up on a preview of the deal we reported during last week's CES, Dell has officially announced the details around its role as the first company to resell the Meta 2 augmented reality headset.

Shortly after we detailed several indicators that the Galaxy S8 Oreo Beta Program would begin rolling out in the month of November, we now have a full changelog for the update.

With a pair of new APIs and low-latency media servers, Twilio's Programmable Video platform could soon help ARKit and ARCore app developers build shared AR experiences between multiple users.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

The Asphalt series has been a staple in the racing genre since its first incarnation all the way back in 2004 — I still remember buying it for my newly-obtained Nintendo DS. It warms my heart to see that, after all this time, Gameloft continues to produce mobile Asphalt games, releasing the latest for Android today. Unfortunately, that's about all Gameloft has taken from its previous efforts. To be frank, this game ain't good.

It looks like all the unregulated fun and games we were having promoting products on Instagram is about to get, well ... regulated. According to a new report by Mediakix, 93% of celebrities on Instagram are not in compliance with the Federal Trade Commission when it comes to posting paid content.

Uber's legal team may have finally sold their engineering golden boy down the river as their war with Waymo continues. Anthony Levandowski isn't your average sacrificial lamb either — given the alleged stealing and all that — but Uber seems set on distancing themselves from this whole fiasco as fast as they can.

The Drug Enforcement Agency (DEA) has been purchasing spyware from the Milan-based Hacking Team and its US subsidiary Cicom USA since 2012. Public records reveal invoices between Cicom USA and the DEA that have ranged between $22,000 to $575,000 from 2012 to 2015.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.