In this clip, you'll learn how to use the Accordion toolkit to set parameters programatically in a Silverlight application. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look. Set properties with the Silverlight Accordion toolki...
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.
President Barack Obama and Afghan President Hamid Karzai signed an agreement that provides a framework for a lasting U.S. commitment to Afghanistan after the long and unpopular war comes to an end.

For more than a decade, free-to-play games with microtransactions (also called In-App Purchase or IAP) by which players can pay real money for in-game content have been the industry standard for online success in Asia. Mainstream American gamers have long resisted these "freemium" games, with World of Warcraft and other subscription based online games reigning supreme, and being seen as more AAA than their free-ish counterparts. Casual games developers have encountered no such problems, and m...
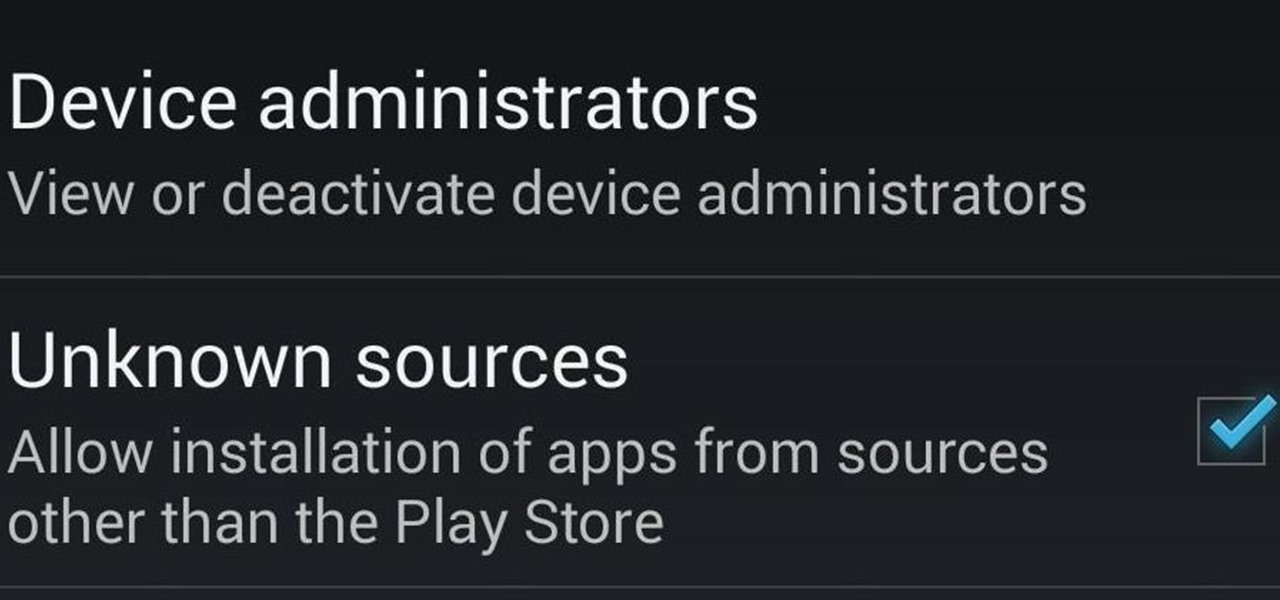
Here's one of those modding must-haves that's basic, yet easy enough to forget about. If you're going to install apps that don't live in the Google Play Store, like the Google Experience Launcher, the OnePlus One lock screen, or something that needs root privileges like the Xposed Framework, you need to turn on this setting.

Elisa Strozyk's wooden textiles fold and drape in beautiful forms. Incredible how a hard material combined with a simple, pieced construction can take on both sculptural and fluid qualities. Truly innovative.

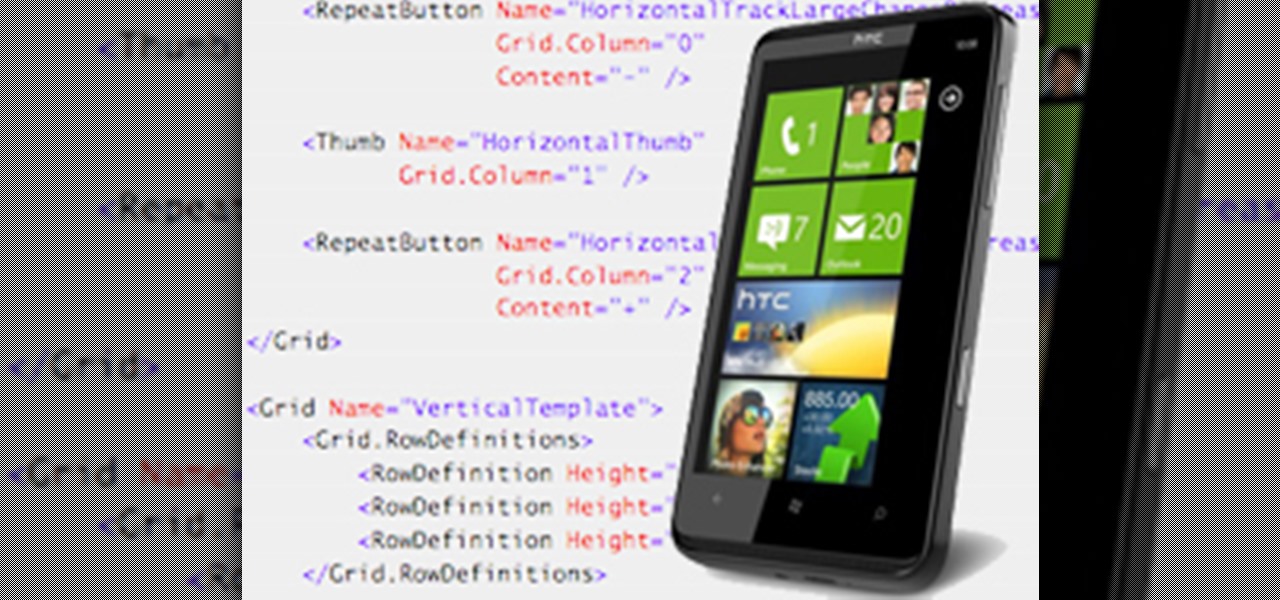
Microsoft's new mobile operating system is officially out on the market, and programmers are hard at work developing new mobile apps for Windows Phone 7 devices. But there's a lot going on in this new platform, which means there's a whole lot to be learned, and the only man in the world with a Windows tattoo is here to help— Charles Petzold.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo cammands plz notise that sudo commands are harmful both pysics and fyskel

Toy Story 3 has received rave reviews across the board. Curious, a couple of us here at WonderHowTo went to see it last night. We found it to be decent. Not fabulous. The opening was exhilarating. Full of action and humor and a thoroughly dynamic use of 3D, but the rest of the movie didn't exude the same energy. The story was sweet and touching, and the characters were as lovable as ever. However, I was looking for a little more action.

Before I start. This Collection is for educational purposes only and I am not the author of the Contents.

BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.

Amazon's Appstore has come a long way since it launched in 2011, with over 250,000 apps to its name. That being said, their app numbers pale in comparison to Google's Play Store, which currently boosts over 1.3 million apps.

If you're reading this, chances are you're utilizing Xposed Framework to apply unique customizations to your device . We've covered various Xposed mods, like how to how to unlock KitKat's full screen capabilty and make your battery percentage easier to read on the Nexus 7, but today, we're showing you an Xposed module for Xposed. In order to access the modules on your device, you typically enter the Xposed Installer, go to Modules, then select your mod. Easy enough, right? Well, things just g...

You've seen it in action before, but now it's finally got a solid release date, well... release month.

One of the most important marketing tools we should always be developing to help reinforce our brand is our references. Just like many companies use their client list and client references to build credibility and confidence for their products and services, we should also leverage our references to build credibility and confidence in our capabilities and brand. Sometimes reference checks are just a formality, but in most cases potential employers (i.e., potential clients) use reference checks...

This is a brief introduction to the new Spry features for Adobe Dreamweaver. You can now easily click one of the 12 or so Spry widgets and they are instantly embedded into your page with the required javascript and cascading style sheet to go along with them. In this Dreamweaver 9 video tutorial you will learn how to create collapsible content boxes with the Spry framework. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll ne...

Minecraft was first released just a few years ago, but when a paradigm-shifting piece of media comes along the rest of the world is quick to take inspiration from it. The absolutely terrible XBLA knock-off FortressCraft was the first, and last month a much more interesting game called Terraria came out on Steam for $9.99. It is clearly inspired by Minecraft, and there is a long checklist of identical features. It is, nonetheless, a very different product, and just might be called the first in...

Today concludes our Gamer's Guide to Video Game Software (see Part 1 & Part 2). In our final installment, we will shift away from engines toward video games that allow you to make your own games within them.

What's your training about? Would any of it matter if your life depended upon it? If not, what is your training providing you with?

I first heard the term molecular gastronomy while watching an episode of Bravo's Top Chef a few seasons back. Intrigued by the concept, I sought to find out more about this modern, deconstructed type of cookery. If you happen to be around foodies and the topic of molecular gastronomy comes up (which very likely will at some point) you'll want to have a few points to contribute and maybe even give them a run for their money.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Some people are what is labeled a power user. I am one of these people. No matter how fast I get my system, or how quick of programs I have, it is never good enough. There is always at least one program that I could swap out for a more advanced, text-based counterpart that increases performance just a bit. Luckily, you don't have to use text-based programs without graphical user interfaces to get blazing fast speeds on Linux. There are tons of open source alternatives to the mainstream progra...

PVC isn't something you want to send to the landfill. It's not going to do anything good for the ground when it's buried. It is also something you really, REALLY don't want to send to an incinerator. When burned, PVC releases some really nasty chemicals, including hydrochloric acid and dioxin.

I've been unreasonably excited about Dungeon Defenders (NOT DUNGEON DEFENDER!) for almost a year. Playing it at PAX did nothing to damper that enthusiasm. I had a chance this week to speak with co-founder/development director Jeremy Stieglitz and marketing diretor Philip Asher from Gainesville, Florida based developer Trendy Entertainment to find out a little more about the game, and how it came together.

This week's 6-part series on Making Art on Your iOS Device comes to a close today with our last segment: a collection of useful apps for touring museums, galleries and street art. The apps below cover some of the world's greatest art meccas, so read on if you're planning an upcoming trip, if you live in one of the destinations listed below, or if you simply want to see what a faraway museum has to offer—from the comfort of your couch.

Minecraft is unique among computer games in that some users have created such breathtaking works of beauty and ingenuity that it challenges the very idea that Minecraft is even a game at all, but suggests that it is instead a tool for artistic expression much like Photoshop.

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.