Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?
Apple released the first public beta for iOS 14.6 today, Friday, April 23, one day after the company seeded iOS developers 14.6 beta 1. The update introduces an easy way for testers to update from an iOS RC (release candidate) to the latest beta, via a simple option in Software Update.

Apple released the first beta for iOS 14.6 today, Thursday, April 22. The new beta (build number 18F5046e) comes just two days after Apple's spring event, as well as the iOS 14.5 RC, and features an easy way for beta testers to update to the latest beta software when running an RC.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

You can't get the same gaming experience on your iPhone as you would on a PlayStation 5, Xbox Series X, or gaming computer. The processing power is less, the controls inadequate, and there are many on-screen distractions, all of which make mobile gaming less enjoyable. While you can't fix many of these issues, there is a way to prevent some problems, and that's thanks to Guided Access.

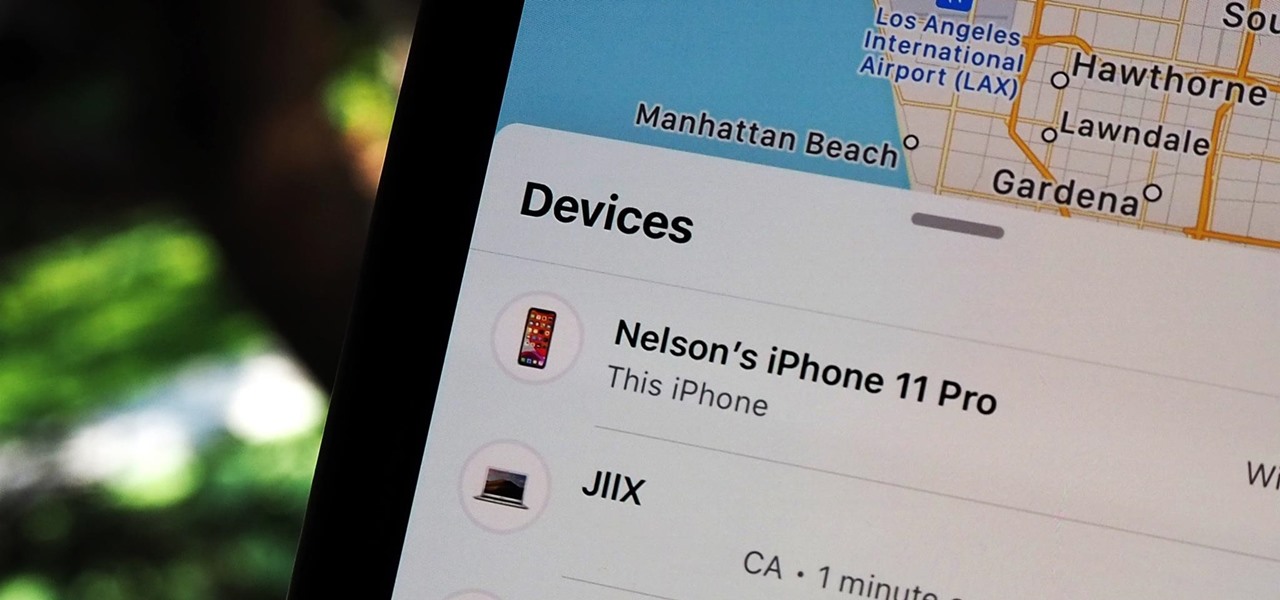
You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

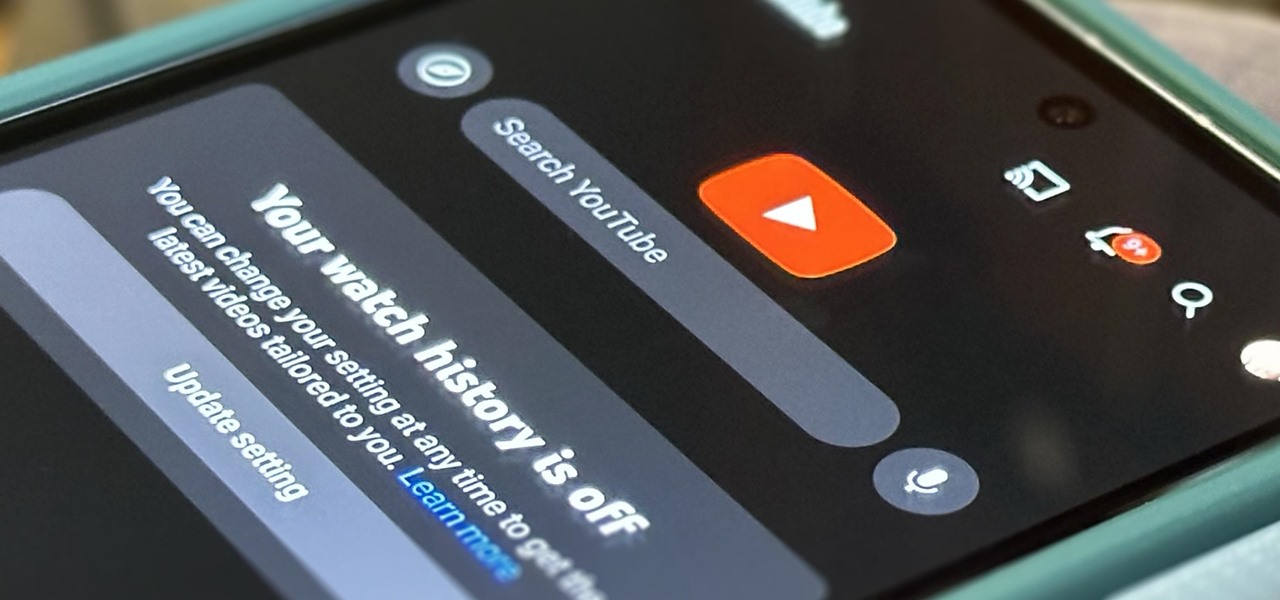
If you're an avid YouTube viewer, you may find yourself overwhelmed on the home page by recommendations from your past viewing habits. But now, you can have a clean slate on your YouTube home screen, free of recommendations.

Apple released the second Release Candidate for iPhone on Friday, May 21. The new update, build number 18F72, comes four days after the company seeded the first 14.6 RC to developers and public testers, and two days after the first beta for iOS 14.7.

Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for Apple Music, new features that will require iOS 14.6 to run.

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

The economic impacts of the COVID-19 pandemic have been felt in practically every business sector. Now, as we look back at the top augmented reality investments of 2020, the AR industry has been no exception.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Apple's "Spring Loaded" event introduced us to many new and exciting products, including iMac and iPad Pro models with the M1 chip, an upgraded Apple TV 4K, a purple iPhone, and the long-awaited AirTag. However, one of the most anticipated announcements came in the form of a software update — the biggest update since iOS 14.0 and iPadOS 14.0 came out — and that's iOS 14.5 and iPadOS 14.5.

Apple's new iOS 14.5 will be coming out very soon, and that's even more evident now with the release of the iOS 14.5 Release Candidate (RC) on Tuesday, April 20. Anyone can install this update and get all of the same features iOS 14.5 will give everyone for iPhone; only you'll have a head start to using all of the updates in Maps, Music, Podcasts, Reminders, Shortcuts, Siri, and more.

Scrabble Bingo of the Day: CABRESTA [n/pl.] A cabresta (also cabestro or cabresto) is simply a lasso, a rope formed with a running noose that's used on ranches and Western plains for catching horse and cattle. Cabresta comes from the Spanish word halter, which refers to the headgear used for leading or tying up livestock and other animals. But halter also used to mean to hang someone by roped noose, which could be how it became popular as a term for a noosed lasso.

Definition Declare is a card game played by 3 or more people. If 4 people are playing the game, then one pack of 52 cards (without the jokers) is sufficient. For 4 to 8 people, two packs of cards are required, without jokers.
Qualifications and Powers I. Executive (President)

Gears of War fans around the world are excited (possibly drooling) over the upcoming release of the third installment in the series, Gears of War 3. There's a lot of hype about the game and its new features, which includes a 4-player co-op mode and a slew of new female characters. But there's one problem—it doesn't come out until September 20th. But for a lucky circle of gamers, the Multiplayer Beta just opened up today.
In a recent tweet, Notch has declared that we (the community, not just this World) will develop the OS to be distributed with 0x10c. I hope we're up to the task. Notch thinks we are, and that gives me all kinds of warm fuzzies.

For some minutes Alice stood without speaking, looking out in all directions over the country—and a most curious country it was. She found herself on the flat bottom of a shallow, felted basin. 'I declare it's marked out just like a large billiards table!' Alice said at last.

Introduction In this post we will look at how to access a PosgreSQL database in your C/C++ application. It's not as hard as you might think, but you need to understand the procedure and the functions used.

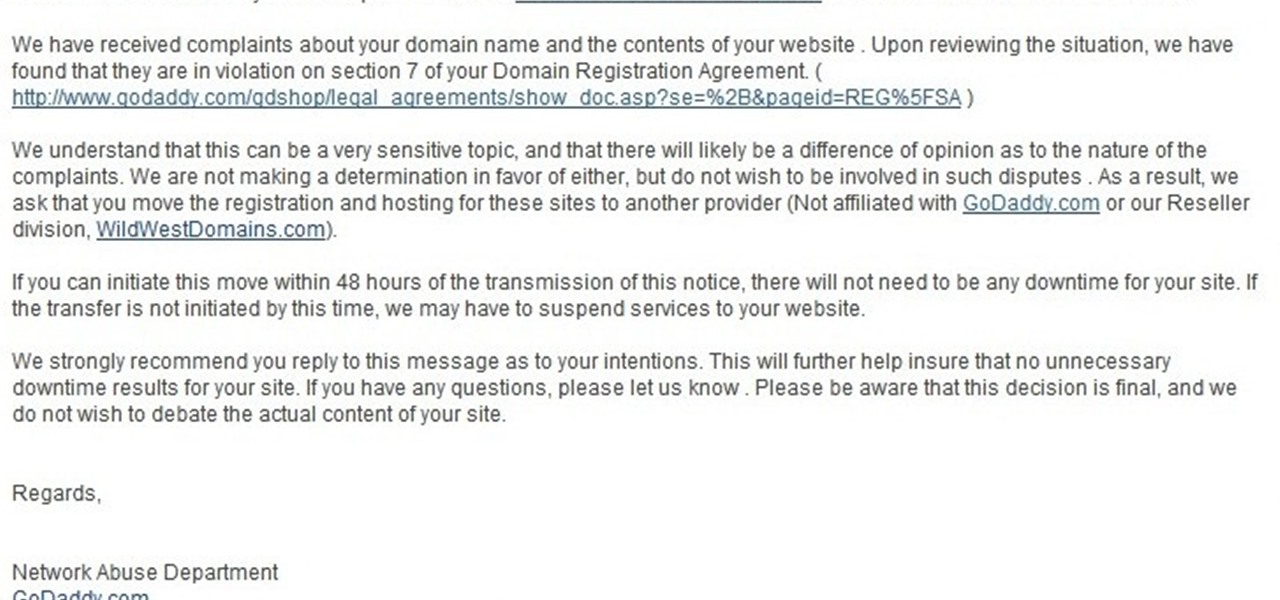
» ‘Obama Truth Team’ Orders GoDaddy To Shut Down Website. A political website that contained stinging criticism of the Obama administration and its handling of the Fast and Furious scandal was ordered to be shut down by the Obama campaign’s ‘Truth Team’. » Former Bush Attorney General Alberto Gonzales Confronted On Torture.

Dress up the Jackass guys like women, including high heels. Place them in a rodeo arena. Have the Jackass crew sit at a table in the middle of the rodeo. Act out a bad theatre play with the crew discussing random thing and drinking coffee. Release a bull into the arena to chase down each of the Jackass guys. The last person to leave the arena is declared the winner. The losers get to enjoy a nice cup of bull piss.

via AdAge Argentina's Head Coach Diego Maradona declared that if his team won the World Cup, he would streak nude through the streets of Buenos Aires. Well, the trend is catching on.

Have you ever heard of Jamaica? Of course you have. It's that island right next to Cuba and Haiti. Well, that's not really what I'm talking about though. I'm talking about the board game Jamaica. This video series will show you how to play the board game with a presentation of the playing cards, the game round, the action types, combat, cost of spaces, penury, treasures, and the end of the game.

Johnny Knoxville and the Jackass boys have finally returned from their whirlwind world tour promoting Jackass 3D. Along with their return comes the long-awaited Honorable Mentions for the Jackass 3D Prank Contest. So, straight from the source, a note from Knoxville: