
How To: Use French vocabulary relating to la literie (bedding)
Learn some French words relating to bedding and the bedroom, such as "mattress" and "sheet."


Learn some French words relating to bedding and the bedroom, such as "mattress" and "sheet."

In this tutorial, we learn how to say words and phrases related to dating in Polish. "Czy umowisz sie ze mna" means "would you like to go out with me". So, if you want to ask someone out on a date, that is how you would do it! "Czy chcesz pojechac do kina" means "would you like to go to the movies". To say, "I like you very much", you will say "bardzo cie lubie". To tell a woman that she is beautiful, you would say "jestes piekna". Finally, to ask someone if you can kiss them, say "czy moge c...

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

In this video, Robert Ahdoot becomes "surfer dude" and shows us the ways of deductive reasoning, as relating to geometry. He begins with a simple example of a syllogism, taking two premises and using them to form a conclusion. This is called the Law of Syllogism. This concept is then used for geometric statements. If two angles are complementary, they sum to 90 degrees. If two angles sum to 90 degrees, then they are acute. By the law taught, it can be said that if two angles are complementary...

This video shows the procedure to draw a face. The video shows various stages to draw a face. These include drawing an egg on the paper, dividing the egg into various parts by horizontal lines, drawing the nose and lips, drawing the eyes and ears. The video cleverly deals with issues relating to the evidence of not being a professional. The video shows the various choices that can be made by the artist in drawing the face like the pencils to use.

Today's word is "aesthetic". This is both a noun and an adjective. As an adjective, it means relating to a sense of beauty.
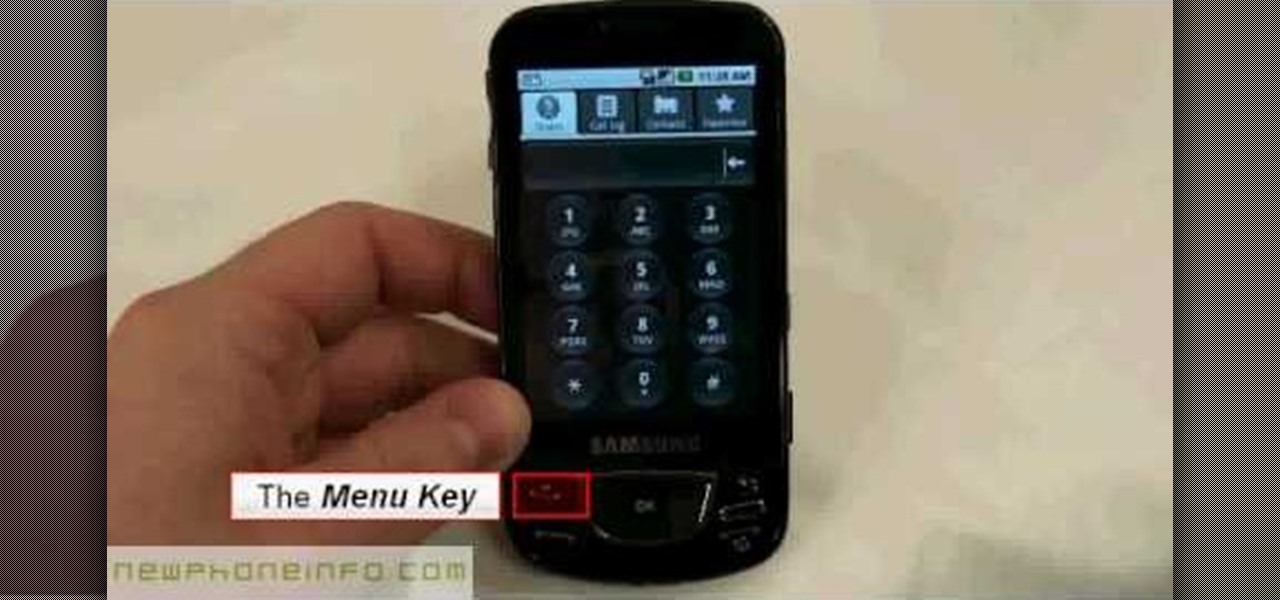
Follow this video to learn some basics on how to use a Samsung Galaxy I7500 mobile phone. Switch on the phone by pressing the power key in the bottom right corner. To navigate around the screen press with your finger on the touch screen and swipe to the left or right. If you want to open a particular application simply press the icon relating to it. Press the menu key to open the home screen with its various options. Press the dial key to open a screen where you can dial in the numbers for a ...

Ben from mechanical mashup shows you how to make a fig rig for a small video camera out of PVC pipe. It gives an ingredient list and tells you the measurements of each piece you must cut. He recommends dry fitting everything at least once, to be sure everything goes together as it should. He then shows how the camera mounts on the rig. In transition of how-to's is a short scene relating to tools, with a man and a boy arguing over ownership. Then Dave shows how to neatly engrave your tools. He...

In this video the tutor explains the 5th Law of Exponents. He reminds the viewer that when polynomials are multiplied, their exponents get added. Now he states that when a polynomial is raised to another power, the exponents are multiplied instead of adding. The 5th Law of Exponents states that when a polynomial with a power 'a' is raised to a power 'b', then the final power of the exponents is the value of the product of the exponents, i.e., a * b. This video states the 5th Law of Exponents ...

The video shows how to calculate weight if the mass is given and vice versa.Later on in this unit you will learn about Newton's laws of motion and Newton's second law of motion gives us a way to change mass into weight and vice versa.This law will tell you what is happening to objects when the net force on the object is not equal to zero and the easy way to say what will happen is that the object will accelerate.But how much the object accelerates depends on two things,firstly the mass of the...

This chess tutorial from Grandmaster Alexandra Kosteniuk is a perfect example of Retrograde Analysis.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.
Hello and Welcome back to another How-To on the Xbox Community Ambassadors World! In this How-To, I am going to tell you and kinda show you how to deal with or avoid angry Xbox Customers.
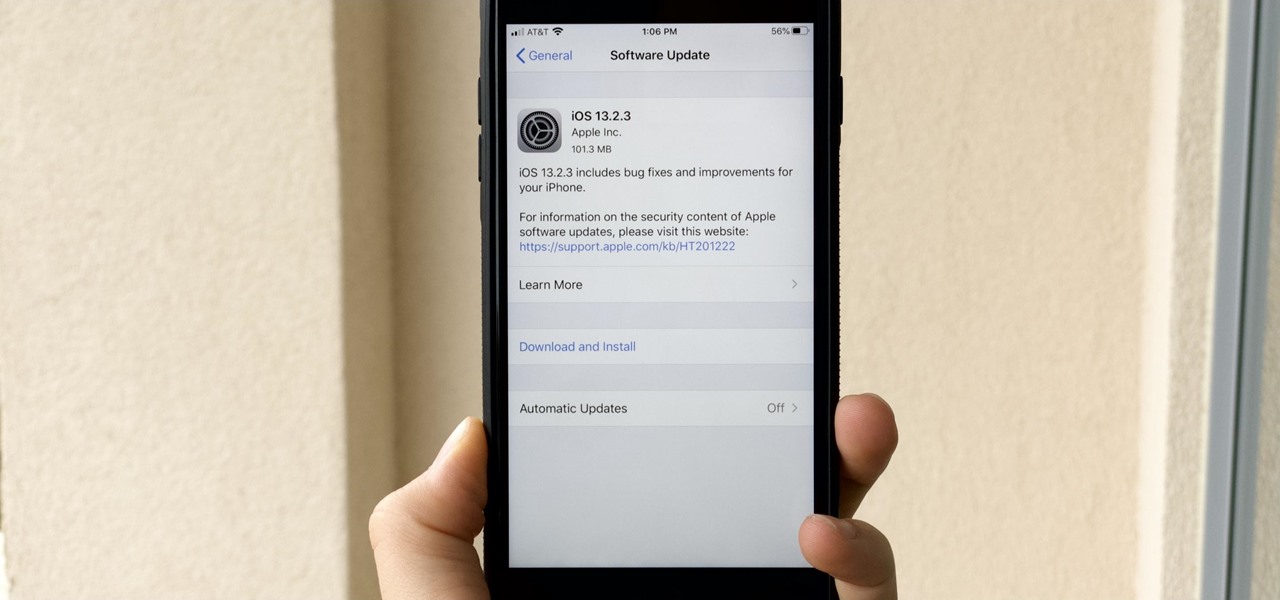
While we all refer to Apple's latest iPhone operating system as iOS 13, in truth, we're well beyond that number. The company has issued numerous updates to its big 2019 release since September, including major steps like iOS 13.1 and iOS 13.2. We've also seen minor updates, like iOS 13.2.2 eleven days ago. Today, Nov. 18, Apple releases another "minor" update, this time dubbed iOS 13.2.3.

From all the demos we've seen, we know for sure that the marketing world is going to change drastically thanks to Apple's ARKit.

Online lives could be made easier now that Facebook, Instagram, and Messenger are testing merged app notifications. 'Could' being the operative word!
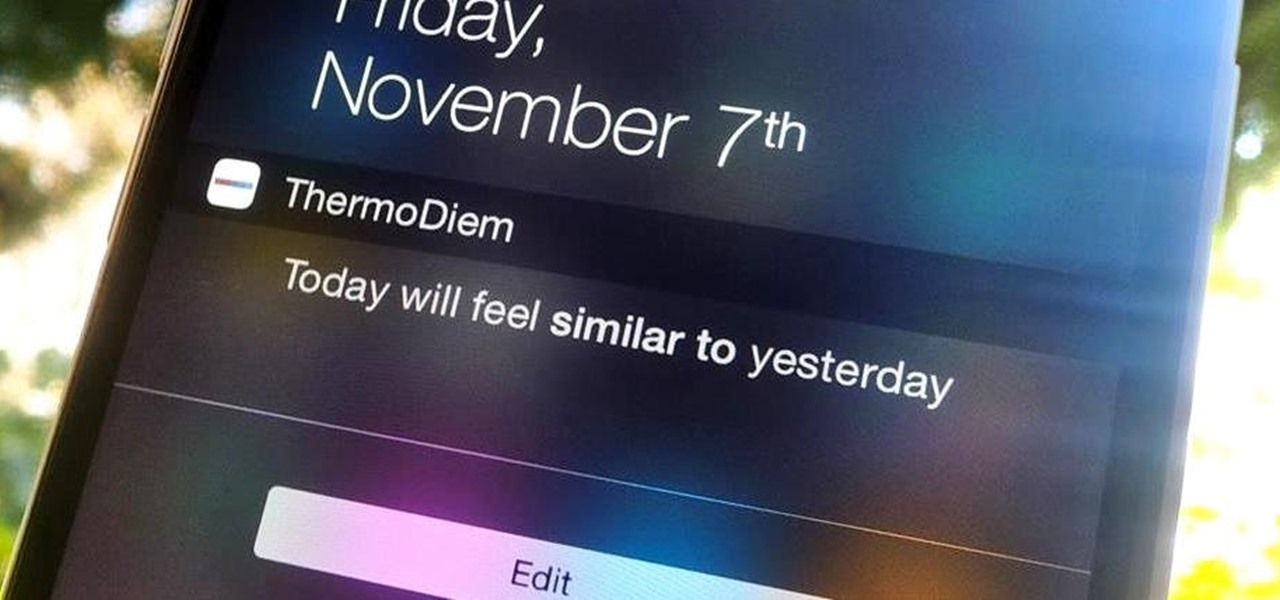
When I get weather information, I prefer to receive it in a straight-forward, minimalistic fashion. Living in California, I could care less about wind speeds, humidity, or any other calculations that I can't analyze in a second. I essentially use the information to help decide whether I'll be wearing shorts or pants on a given day, so give it to me bluntly.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

There's nothing quite as exciting in the beta testing world as a new update. Battling overloaded servers to download the latest update as fast as possible, just to scour through the new OS looking for the biggest features to the smallest changes. It was only Thursday that Apple seeded iOS 13.2 developer beta 2, so count us surprised that we get to experience today's release of developer beta 3 so soon.

Last year, Motorola released their Moto G5 Plus, a fantastic mid-tier machine that earned praise from both reviewers and consumers. Starting at $229, it was well-built and inexpensive considering everything Motorola managed to jam into it. This year, Motorola is looking to replicate the success of their G series with the G6 Plus.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

Uber's chance at driverless domination may be ripped away as its legal battle with Waymo escalates. The company's self-driving program is now under threat of closure if the allegations of premeditated theft are proven

Google Assistant has introduced tappable shortcuts on the Google app for Android, iOS, and Google.com this week.

Netflix releases monthly reports on major ISPs relating to how well their service works on each provider. The purpose is to educate the public on their choice of service provider, but since many of us hardly have any choice at all when is comes to an ISP, it backhandedly works to shame them (if they're even capable of feeling shame under all those millions of dollars).

Drilling holes in wall tiles is a fairly easy skill to master once you know how. Follow these simple steps on how to drill a hole in a tiled wall for a hassle free experience.
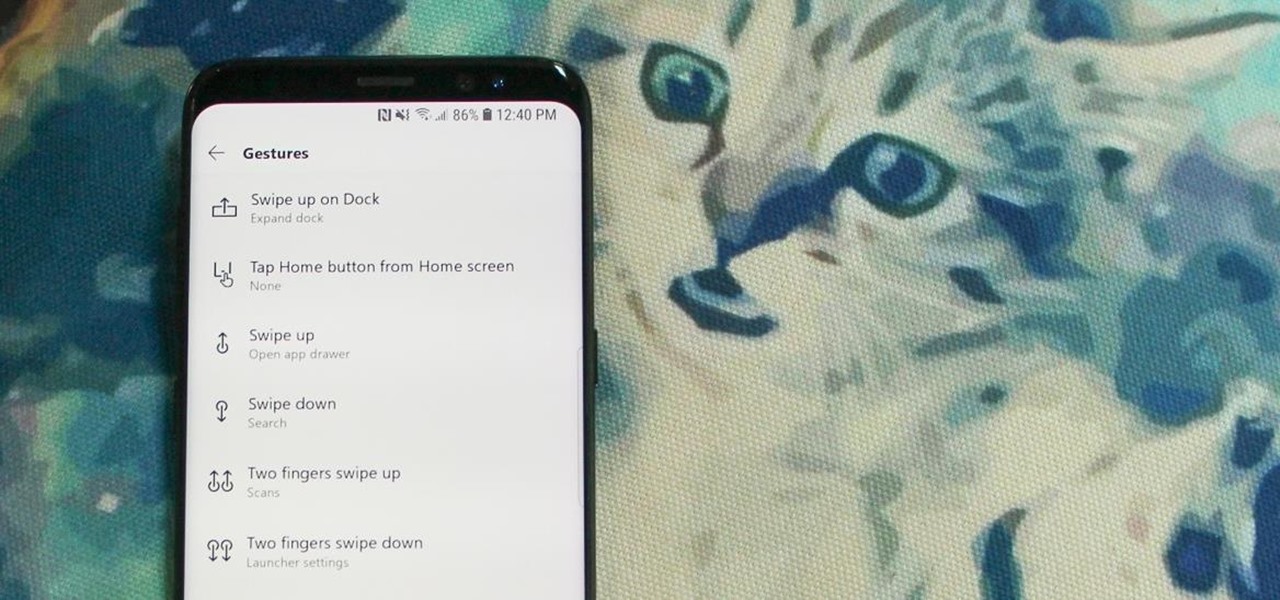
Ever-shrinking bezels and disappearing hardware buttons make for good looking phones, but they also increase the need for gesture controls. Android Pie comes with seven new swipe gestures, but if you don't have the update yet (or find its default gesture options to be lacking), you should take a look at the Microsoft Launcher.
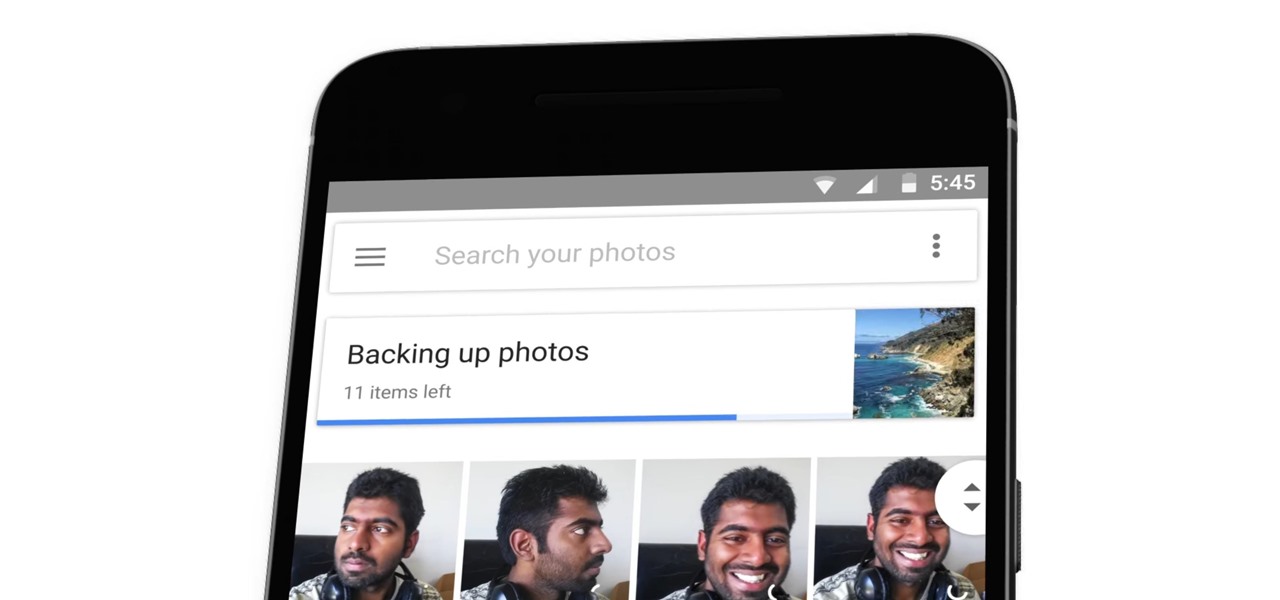
The latest Google Photos update for Android has added a number of cool new features, like video stabilization and a rumored Google+ integration. The latest update started rolling out to devices on April 11, 2017, and includes the video stabilizing feature we've been waiting for.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.
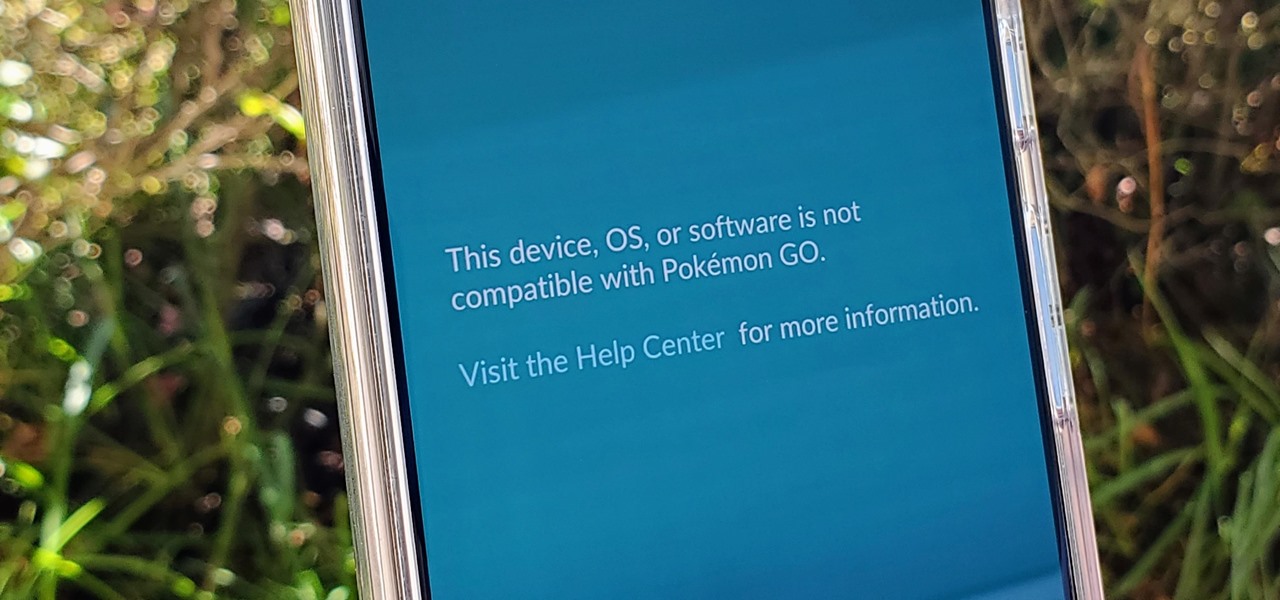
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.

Two viral liver diseases could help us find the path toward the cause of Parkinson's disease. Researchers from the University of Oxford and UCL Institute of Neurology in London have reported an association between hepatitis B and C infections and an increased risk of Parkinson's disease. Their findings were published early online in the journal Neurology.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...
The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.
Everyone listens to music. I've got over 3,000 songs in my iTunes library, but am always looking for more, and I'm sure you are too. You can never have enough tunes to rock out to, right? If you're using Windows 8 like I currently am, these are some of the best apps in the Windows Store right now that will help you find new jams for your collection.
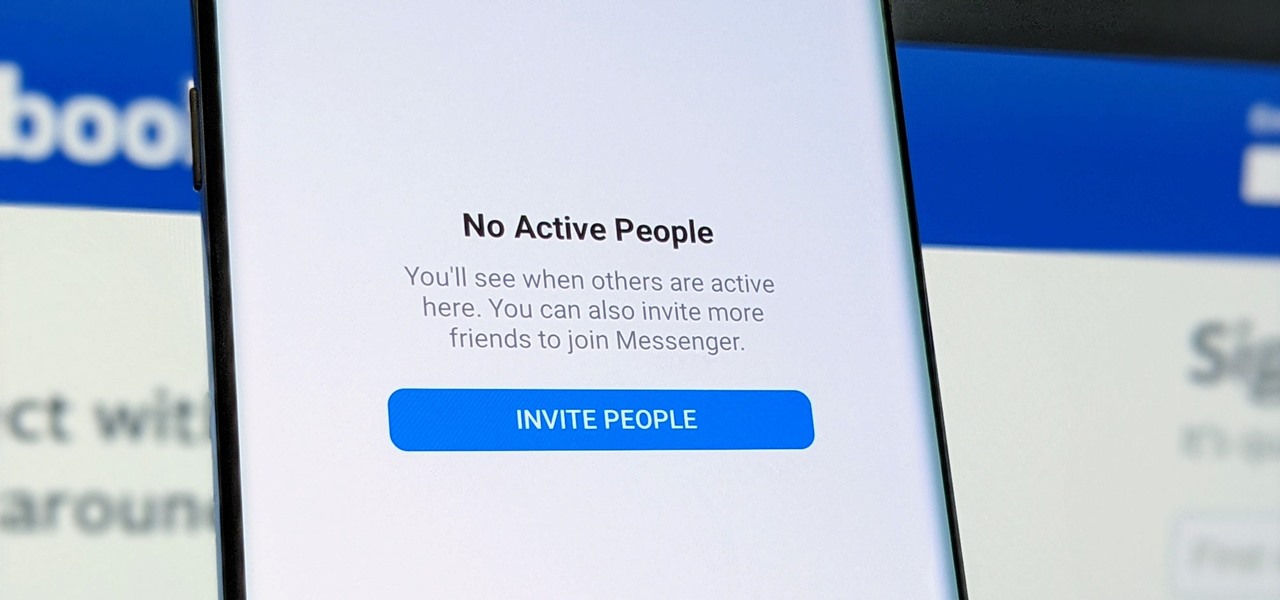
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.