In this tutorial, we learn how to clean skateboard bearings. You will need: a socket wrench, a dirty skateboard with dirty bearings, super glue, rubbing alcohol, and an empty glass jar. First, use the wrench to remove the bearings from the skateboard. After this, pour the alcohol into the jar, then drop the bearings inside. You can also drop in other parts that need cleaning if they fit inside the jar. Now, place the lid of the jar on and shake it for about a minute. When finished, let the so...

This video demonstrates how to take apart the head set of an XBox 360. You will need two small screwdrivers - a flat head and a Phillips. First the head band is removed by pressing the lock hold. The foam is removed and set aside. The rim of the speaker is removed by pressing the locks and pulling it up. Now the speakers are exposed and the wiring is checked to see if it is connected properly if you cannot hear it properly. Now the transmitter boom is also checked for proper connection if tra...

Having a healthy lifestyle is very important. In this video, learn how to do a forearm stand with Tara Stiles in her "Let's Get Physical" Challenge. First, lay your forearms on the ground. Make sure your elbows are directly below your shoulders. Have the rest of your body in plank pose (your feet on the ground and your body flat.) After a little bit, walk your feet back up so that your body now forms an arch with your butt in the air. Walk back to your plank pose and stay there. If you're loo...

Create softly folded drapery panels with our universal tempo pleat tape. It's the perfect subtle look for flat panel drapes. Learn step by step how to sew on our universal tempo pleat tape to create soft folds by watching this video sewing tutorial series.

This how to video teaches you how to make a guitar pedal board. All you need is: 1. One piece of flat scrap board

This how to video is designed for people who wanted to start glowstringing but has never done it before. The tutorial starts by answering some of the most common questions such as how to tie the strings and how to hold them, then moving on to teach the Weave, Windmill, and Butterfly. All you need is a pair of shoelaces and a pair of 6 inch glowsticks (either used or unused) then you can start here. Some people like their shoelaces round and thin, some like theirs flat and thick. It doesn't ma...

Learn how to create a shimmery gold and green eyeshadow look with this how to video. This makeup tutorial uses the following products: water-based mixing medium, a soft white gold base (Gold Dusk pigment), an emerald green base (Emerald Green pigment), an emerald green eyeshadow (Humid eyeshadow), a white gold eyeshadow (Gorgeous Gold, Casablanca), a dirty gold eyeshadow (Rye eyeshadow), a cool mint green eyeshadow (Aquavert), a brow bone color (Casablanca), a black liner (Graphblack technako...

In this lesson, I will demonstrate how to play on the lyre, the traditional melody usually sang to "Adon Olam"(Lord of the World); one of the beautiful closing hymns sang at the end of a traditional Shabbat Service.

Get a new perspective on computing with an HP Tablet PC. HP's Tablet PCs are well-equipped personal notebooks, with a significant twist. The display turns around one hundred and eighty degrees, transforming your notebook into a flat tablet touchscreen PC.

The most important part of breastfeeding is getting the baby to latch on correctly. Find out the best breastfeeding positions so your baby can get the proper latch. The second part gives extra advice for women with flat or inverted nipples.

A good endoscope camera can be an incredible tool for a variety of jobs. Whether you have to look under something heavy before you move it, look down a pipe before you clean it, or just give yourself extendable, bendable vision, an endoscope camera can be a fantastic tool when it works.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

Whether you're at work or just away from an outlet, nothing is more annoying than suddenly having to go through your day with a dead phone.

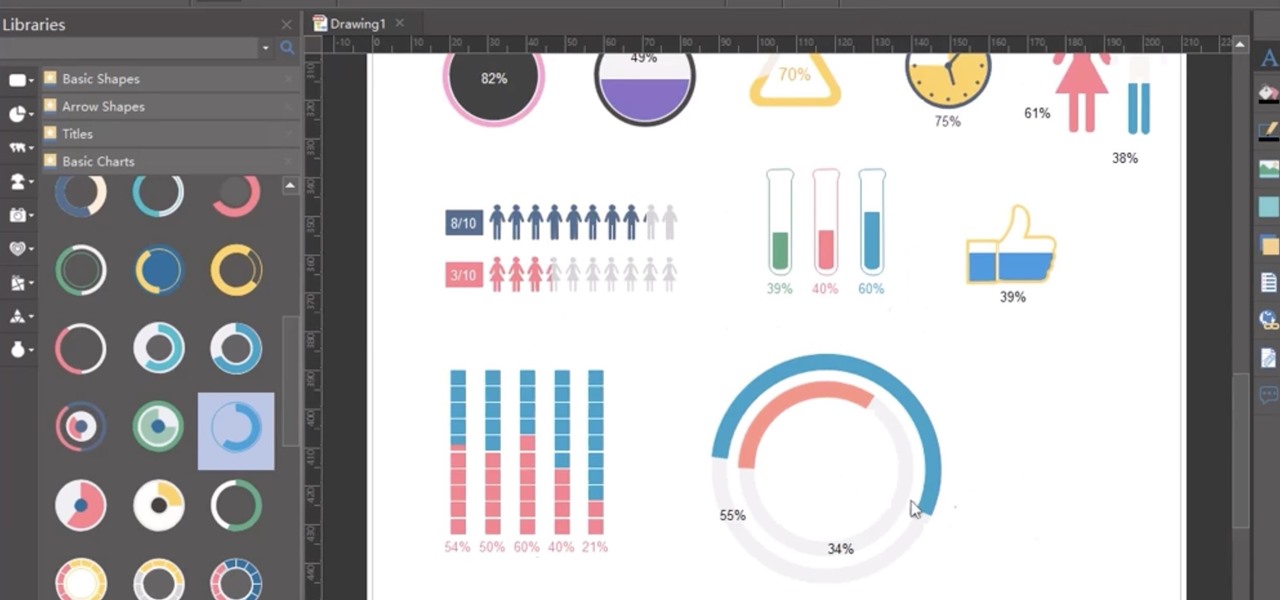
Anyone who's worked in web development or graphic design long enough knows that one of the most difficult job elements is finding high-quality stock images that aren't tangled in red tape. Whether you're trying to build a website, ad campaign, or email newsletter, you need to have reliable graphics that are easy to find and use across multiple platforms.

Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

Many people get into audio and video production out of a passion for making music, films, or documentaries. Yet once they're locked in, they realize the endless possibilities at their fingertips. With more digital content being created every hour, reliable engineers are needed.

Whether you're calling the unemployment office, a popular radio contest, or any other phone line that gets super busy, having to recall the number manually is a pain. Whatever you do, however, don't punch in the same digits over again and again — our smartphones can help do it for us, saving our time (and sanity).

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

It wasn't Christmas, but for Amazon Prime members, it was darn close: Amazon Prime Day, one of the biggest shopping days of the year, came and went earlier this week. Unfortunately, there weren't many Prime Day-specific deals to be had for augmented reality fans, but that doesn't mean AR-loving Amazon Prime members were completely left out.

The on-screen gestures on the iPhone X have taken touchscreen interaction to a whole new level. While they're needed due to a nearly bezel-less display and lack of a Home button, you can actually get these iPhone X-exclusive swipe gestures on any other model iPhone. The only catch is that you need to be jailbroken.

It's been a long road, but the guys over at CoolStar have finally come up with a stable, semi-untethered jailbreak for 64-bit iPhones, iPads, and iPad touches running on iOS 11.2 up to 11.3.1, with the latest update extending coverage to 11.4 beta 3. So if you've held off on updating to the latest iOS 11.4.1, your patience has finally paid off.

Native screen recording, one of the hottest features that Apple included in iOS 11 and later, is easily started from the optional Control Center toggle on your iPhone. From there, you can stop recording from the same place or from the red status bar or bubble. It's a very convenient addition to iOS, but there's one obvious downside — that red indicator, which can appear in your recordings.

Despite years of user complaints, OEMs are still preinstalling third-party apps on brand new devices. Even in 2019, you'll still find plenty of phones with Facebook preinstalled. What's worse, it's installed as a system app, so it can't normally be uninstalled without root access. However, there are a few workarounds.

For some of you, whether or not to delete Facebook is a daily struggle. One reason you might not have pulled the trigger on your Facebook account yet could be because of Messenger, which provides millions of people with different devices an easy way to communicate with each other. But here's a secret you might not know: you don't need to have a Facebook account to use Facebook's popular chat app.

HMD (the company currently making Nokia-branded phones) only released one flagship device last year, with the rest of the phones falling in the mid-range and entry-level tiers. However, at Mobile World Congress 2018, HMD announced their ambition to become a top five smartphone maker in 3–5 years. Meeting this goal will require penetration in all markets — especially the United States — and it looks like Nokia will get the ball rolling early this year.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

A week into my internship, I experienced pretty serious back pain and slight difficulty breathing. I scheduled a doctor's appointment to make sure nothing was wrong, and I got a surprising diagnosis: bad posture.

Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

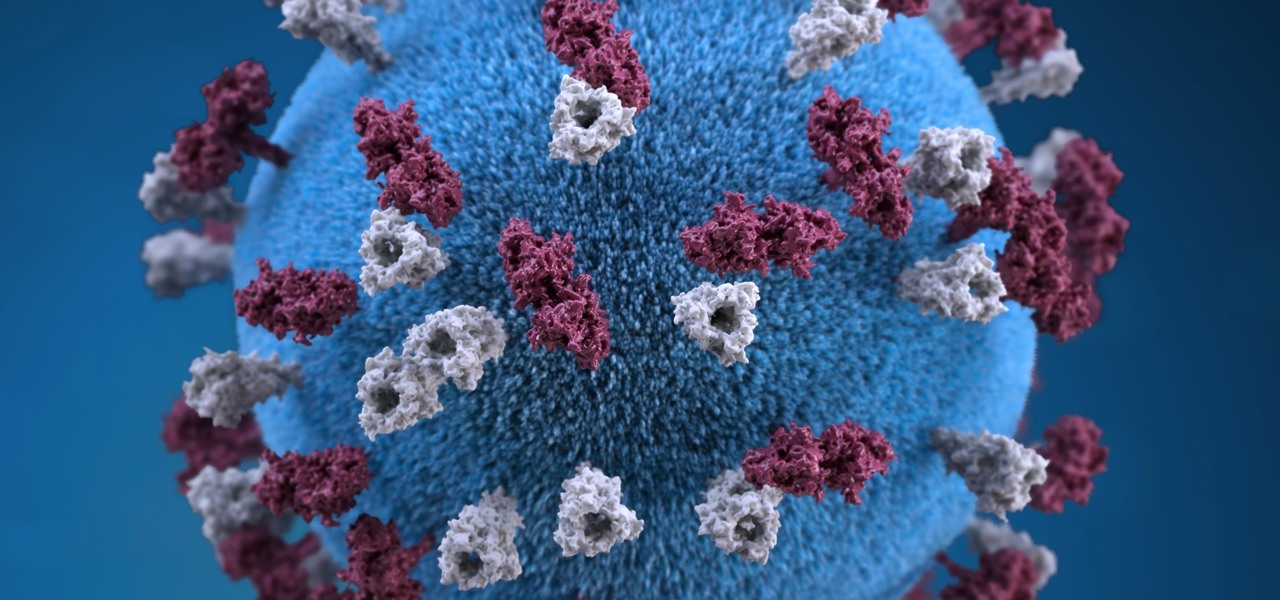
Maine reported their first measles case in 20 years yesterday, June 27, in a press release from the Maine CDC. Many other people may have been exposed and could show signs of infection soon, with the potential for outbreak brewing. The last measles case in Maine was in 1997.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

The technology driving the automated vehicle revolution relies on the car's ability to see and understand the world around it.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.