First thing you should do is invest in a reliable good quality digital camera. No, you do not have to spend big bucks on one. Kodak, Sony and Nikon make inexpensive digital cameras that are ready to be bought everyday. Make sure you find a camera that fits your needs.

The witch is the blue-chip stock of Halloween costumes — reliable return, low risk. You Will Need

This how-to video quickly outlines exercises to get your dog walking on a loose leash by your side. Put very basically, teach the dog what you want them to do! And secondly, stop reinforcing them when they pull! A clicker training method is used, but if you do not have one, you can always use a verbal marker like yes. However you will get much faster and reliable results by using the clicker. If you hold the clicker in the same hand as the leash, and keep the treats in the other hand, you wil...

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

Parents TV demonstrates how to safely bathe your baby, and features the products that make bath time a "splashing" success!

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Watch this video to learn how to cap off a water pipe with a push fit fitting within seconds. Useful for when you absolutely have to cut a pipe.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Have you ever felt like you wanted to totally annihilate someone in Minecraft with a machine gun? Yeah, me, too. Thankfully, you can!

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Tired of walking everywhere? Does your only ride have two wheels and a bell? Check out this video and learn tips and tricks for convincing your parental units to buy you a car. Pretty soon you will be cruising through town and the envy of all your friends.

You've boxed up and shipped all your other possessions for the big move and all you're left with is the little issue of how your getting your car there. There are companies out there that will ship your car to you, just make sure your car is prepped for the journey.

The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD wasn't fireproof.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

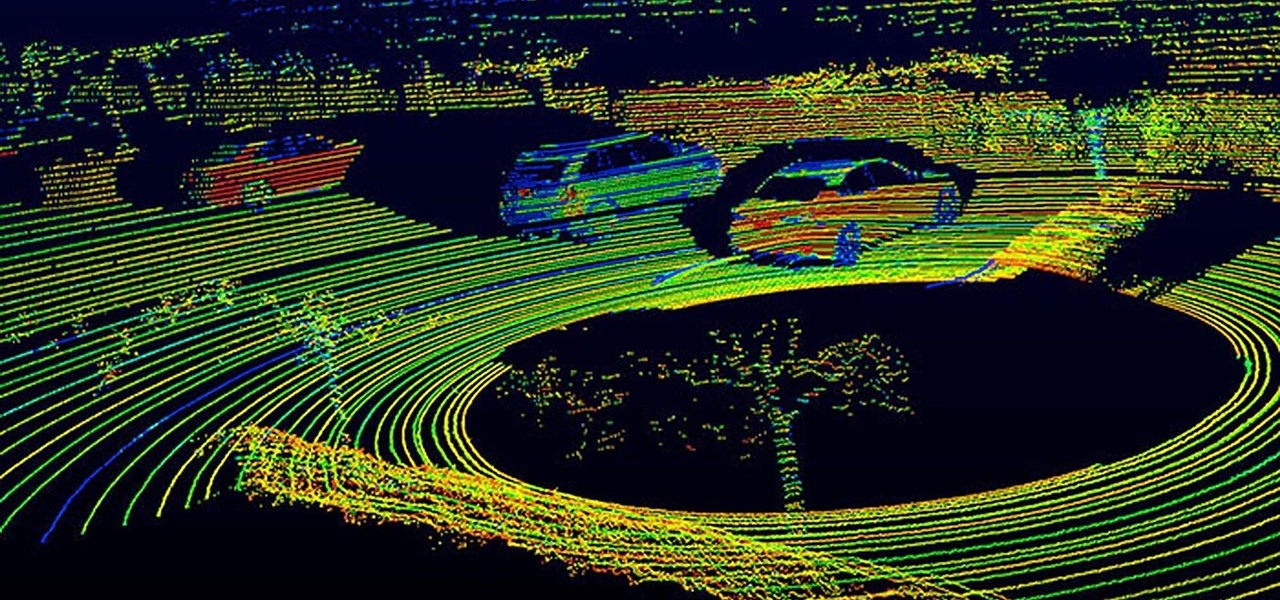
Solid-state LiDAR is cheap, robust, and compact in size — this is why the device is seen as the LiDAR of choice for future high-volume production of level 3 and level 4 cars.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Yes, you read that right—you can now get Google Maps back on your iPhone again. It may not be officially replacing Apple's notorious Maps app, but it sure is a sight for sore eyes.

When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan H. Lents, a molecular biologist at the John Jay College of Criminal Justice in New York, is the first of its kind to show how microbes colonize a body's ears and nose after death.

One of our favorite kitchen items, hands down, is a good old-fashioned wooden spoon. It's practical, versatile, and can last for decades if cared for properly. There are specific ways to nurture wooden utensils in order to keep them from cracking and to help them maintain their glossy sheen.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

Songs new and old are given a fresh purpose through the TikTok meme machine, but it can be tricky to figure out where a track originally comes from. Sure, you can tap the name of the song to see the source on TikTok, but if it were a snippet uploaded by someone other than the track's creator, the song title likely wouldn't be listed. Luckily, there is an easy way to figure it out.

Rumors are what Apple dreams are made, so most of the time it's best to ignore the juicy ones -- but some Apple rumors demand a least a little attention.

So, someone on your shopping list has an iPhone. Lucky for you, Apple's line of smartphones are practically made for accessories. From AirPods to adapters, there's something for every iPhone user in your life. Are you feeling overwhelmed by the options? You've come to the right place.

The iPhone 11, 11 Pro, and 11 Pro Max are the most advanced flagships Apple has to offer, but that doesn't mean they're immune to occasional bugs. Anything from an app plagued with issues to a faulty software update still can cause your device to freeze up, so having the ability to force a restart can come in very handy.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

Apple released the fifth build of the iOS 11.3 developer and public beta on Monday, March 12. The update comes exactly one week after the March 5 release of beta 4, which mostly introduced bug and stability patches. At this time, this new beta appears to do much of the same.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Sherif Marakby has returned to Ford as the VP of AVs & Electrification after a brief stint with Uber. Marakby's VP title will be effective June 12.

Rumor has it that Google Assistant will be coming to an iPhone near you. A "trusted source" broke the news of GA's arrival on iOS to Android Police ahead of Google's I/O conference this week.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving cars "see" the road with much more accuracy than any other camera sensors available for vehicles currently.

We've heard a lot about self-driving taxis, as car and ride-sharing companies compete to win the driverless gold rush. But FedEx wants to bring its enterprise into the mix, as the head of its freight division has asked the US government to develop laws for self-driving trucks.