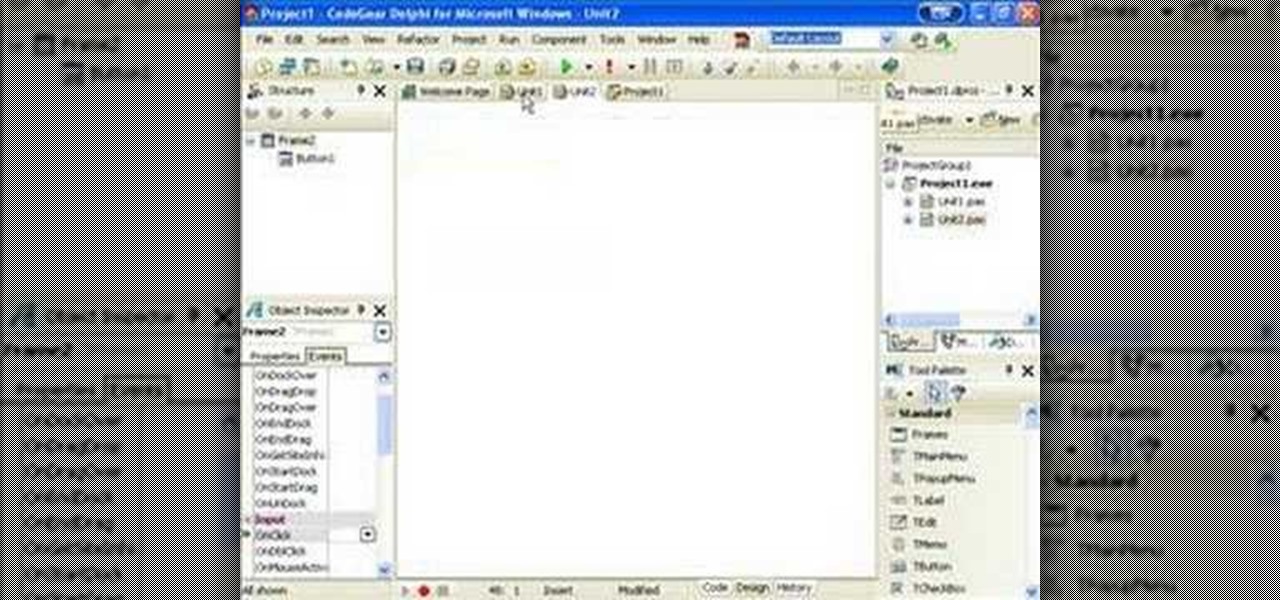
How To: Use owner and parent properties in Delphi programming
Delphi controls have an owner and parent property, find out what the difference is and how to use them when programming in Delphi.


Delphi controls have an owner and parent property, find out what the difference is and how to use them when programming in Delphi.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this tutorial you will see how to use Jimmy's speed math program that he wrote in Flash. A download to the program is included. This is a GREAT way to help your kids or students (or maybe adults?) get better at math.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

As demand for AR and VR developers continues to increase, particularly with the advent of Apple's ARKit platform, Unity has partnered with online learning company Udacity to help developers sharpen their skills for these jobs.
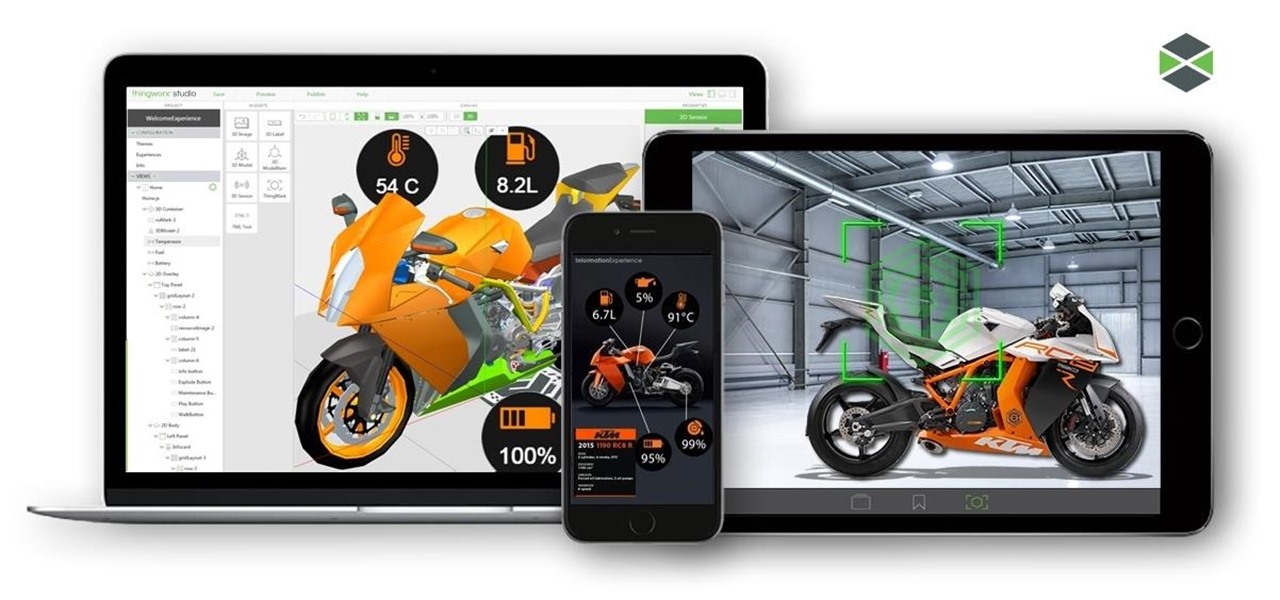
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.
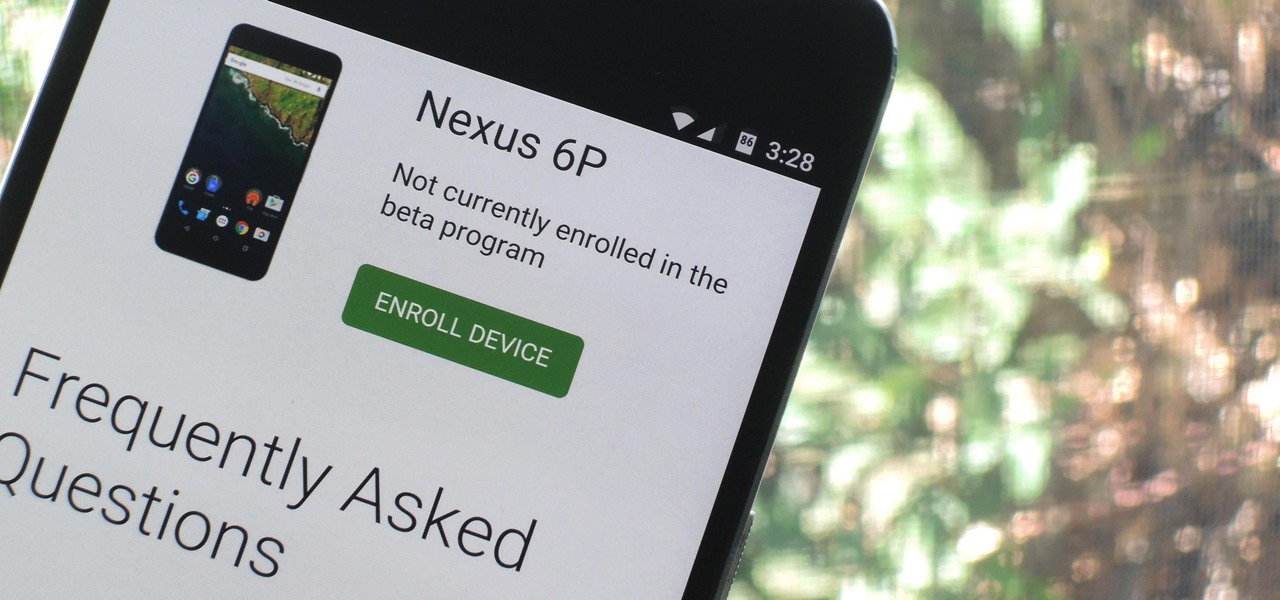
Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

bObsweep robotic vacuums automatically clean whenever instructed to do so by an owner or because of a pre-programmed schedule.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...
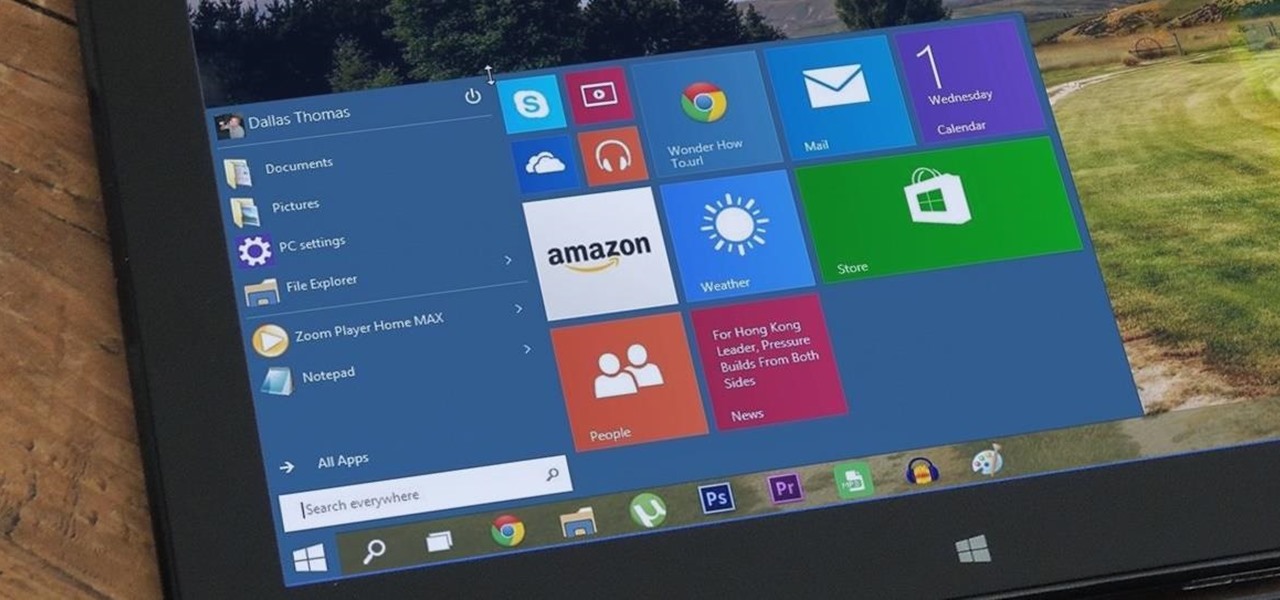
At a closed-door presentation on September 30th, 2014, Microsoft unveiled the latest iteration of its industry-leading operating system. Dubbed Windows 10 (seems as if Redmond isn't too fond of the "9" moniker), this new version brings along with it many UI optimizations and under-the-hood tweaks. With a particular focus on optimizing the interface for traditional mouse and keyboard computers, one of the most noticeable changes is the return of the Start Menu. While touch-optimized devices wi...
I have shown here to install Java development kit. It also contains the settings of path and classpath to prepare for java programming.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...
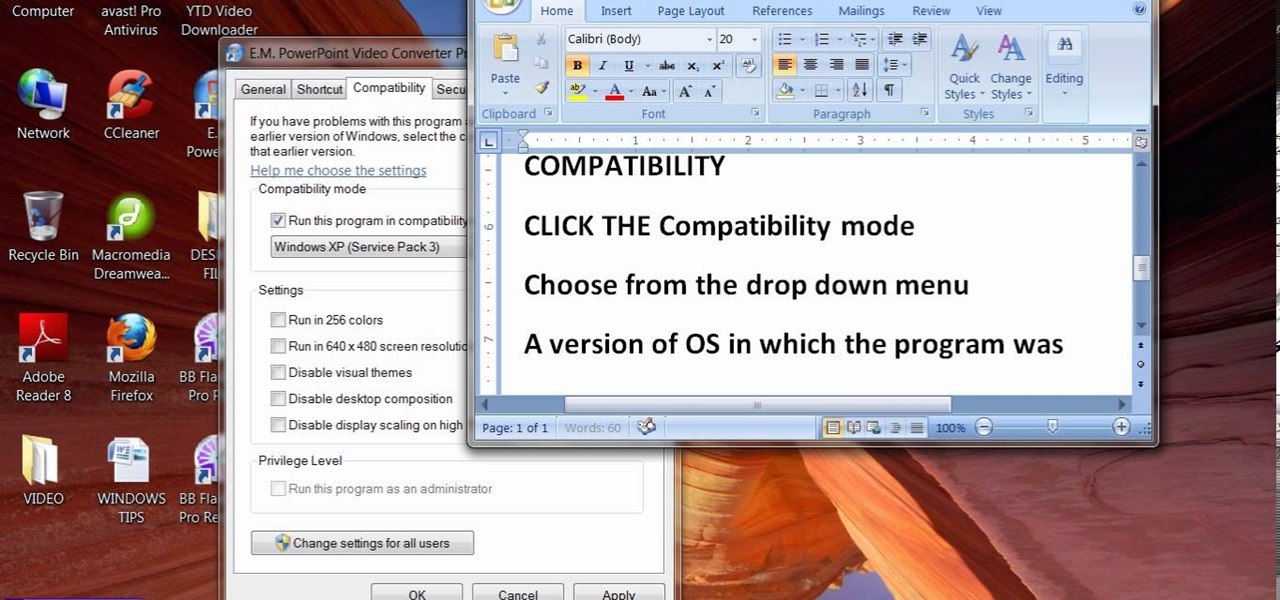
When people upgrade their windows few software don't run on new OS. How to fix the problem? Setting program compatibility solves the issue. Watch the video we made and submitted earlier in You tube.
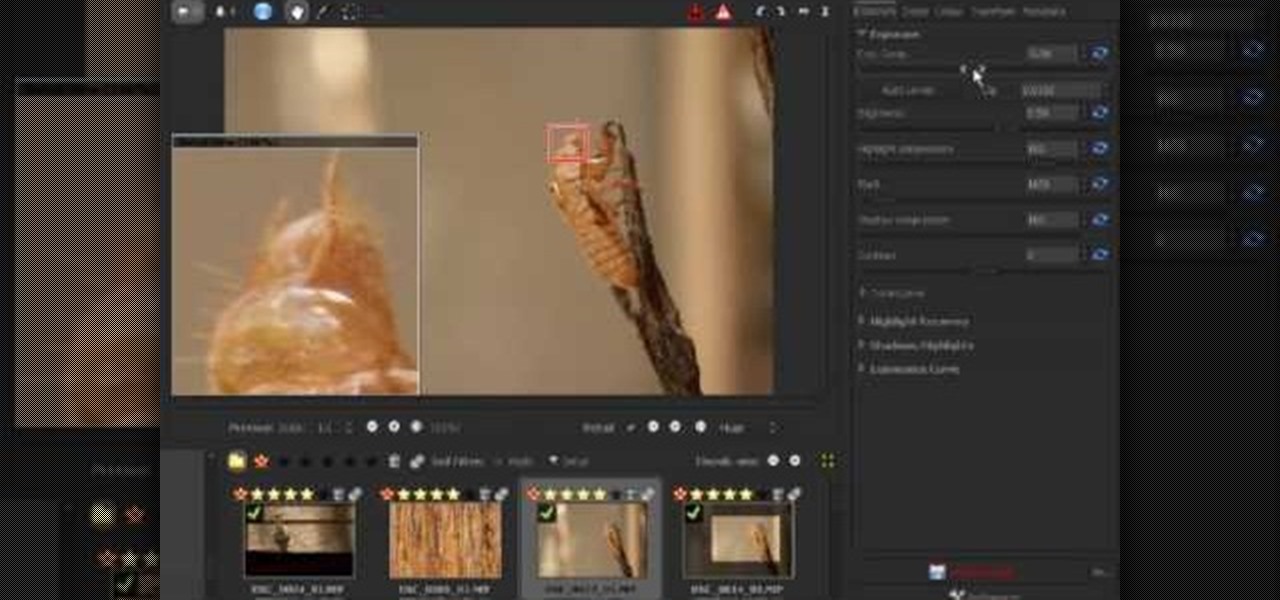
In this video, we learn how to use Raw Therapee with Gimp. First, you need to go online to Raw Therapee, then download and install Raw Therapee. Once you have this, open it up and familiarize yourself with the layout of the software and where the different tools are at. Next, change your preferences and pick your settings throughout the different folders. Next, find GIMP through the program folders as your installation directory. Now, it will export your images to GIMP automatically. This way...

In this video tutorial, viewers learn how to play DVD movies on the computer for free. Usually, users will need to purchase expensive codes or plug-ins for a media player in order to play a DVD movie. This video introduces the VLC Media Player. This media player is able to play any DVD movie and is a free program. To download it, open your the Google website. Then search for the media player and select the first result. Then click on Download and install the program. This video will benefit h...
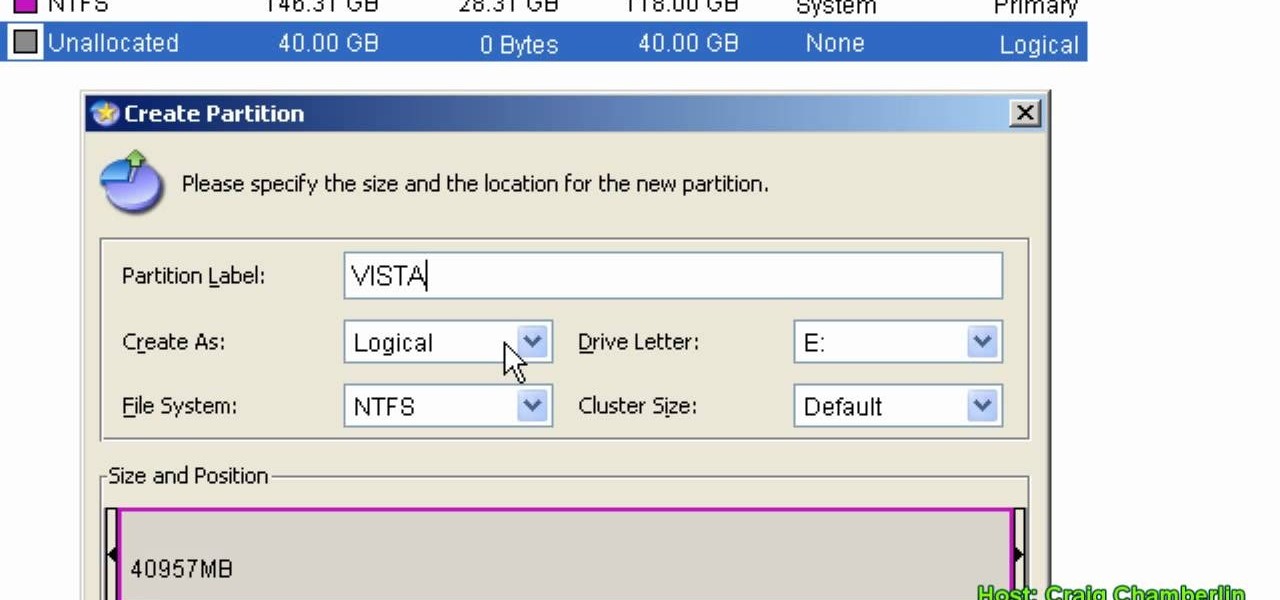
In this Computers & Programming video tutorial you will learn how to format a hard drive to boot a second operating system. First, do a Google search for EASEUS partition master, download and install it. Launch the program. Right click on the unallocated space on your hard drive and then click ‘create’. Now create a new partition for the new OS. Name it Vista, select ‘primary’ in the ‘create as’ window, choose ‘NTFS’ in the ‘file system’ window, select drive letter as ‘V...

Having downloadable files on your website is often an essential. It is an easy and fast way to share programs via the web and allow your visitors to experience software and files that you enjoy. In this tutorial, you will learn how to make a file downloadable for you website, so your visitors can easily download any file. This process is surprisingly straight forward and easy. You can follow this same process whether it is a text file, image, movie or music file. You will also learn how to tu...
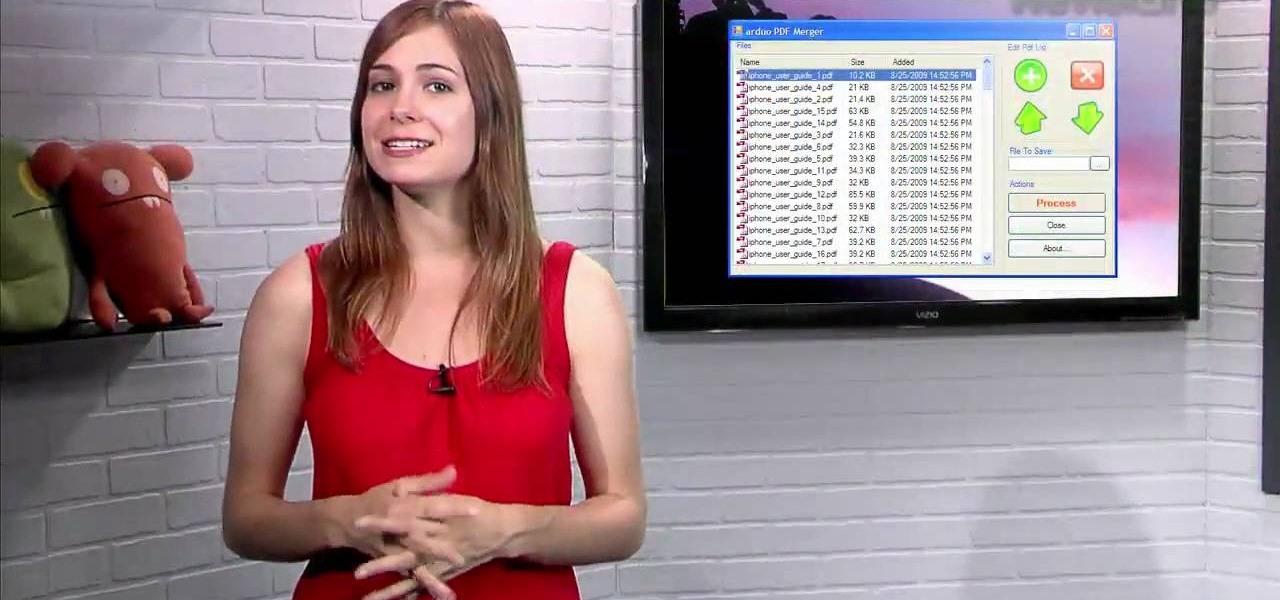
This video shows us a tool that can be used to split and merge pdf files without having to buy any software.
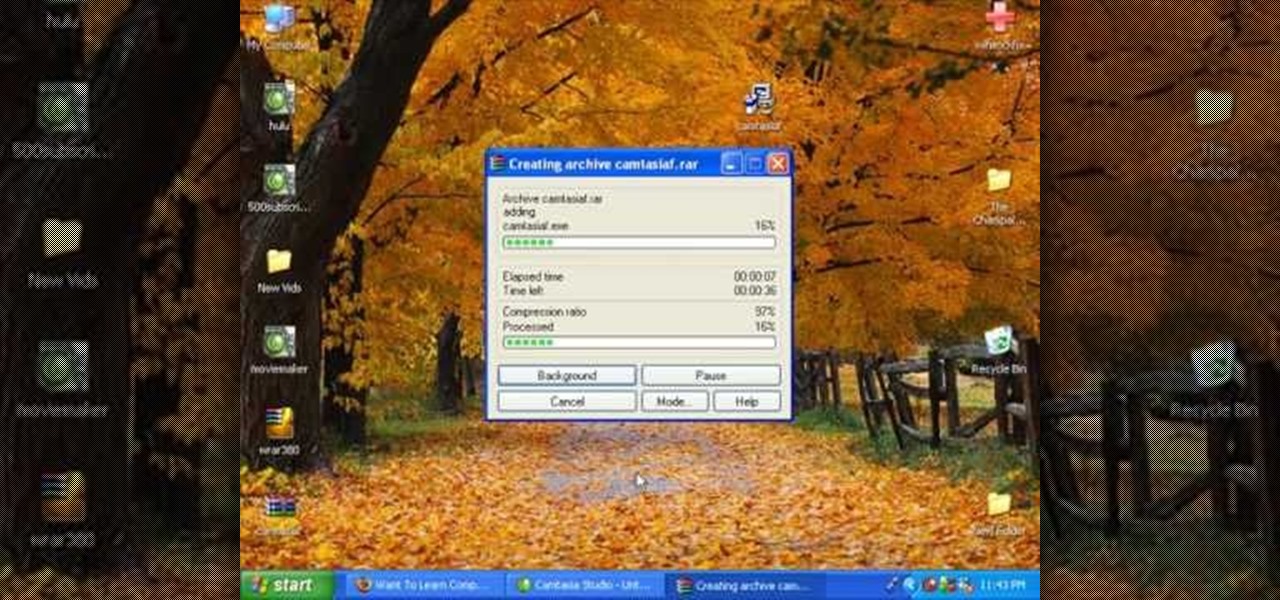
In this video tutorial, viewers learn how to break up large files to easily send through email. Go to the website: and search "winrar". Download the program. Then double-click the file and follow the instructions to install it. Now right-click the file and select Add to Archive. Users will have an option to split the files into volume bytes. Then press OK wait for the program to compress the file into several parts. This video will benefit those viewers who...

In this how to video, you will learn how to make an RSS feed as an alarm clock. To do this, you can use the Microsoft speech program. Open the alarm batch file. Modify the Perl script so that it downloads the RSS feed from the Digg website. It will strip all the tags and html so only the text is left. From here, you run a script that converts the text to a wave file. From here, the alarm m3u will start. You can then run the command prompt to schedule the alarm time. Go to schedule tasks to ac...
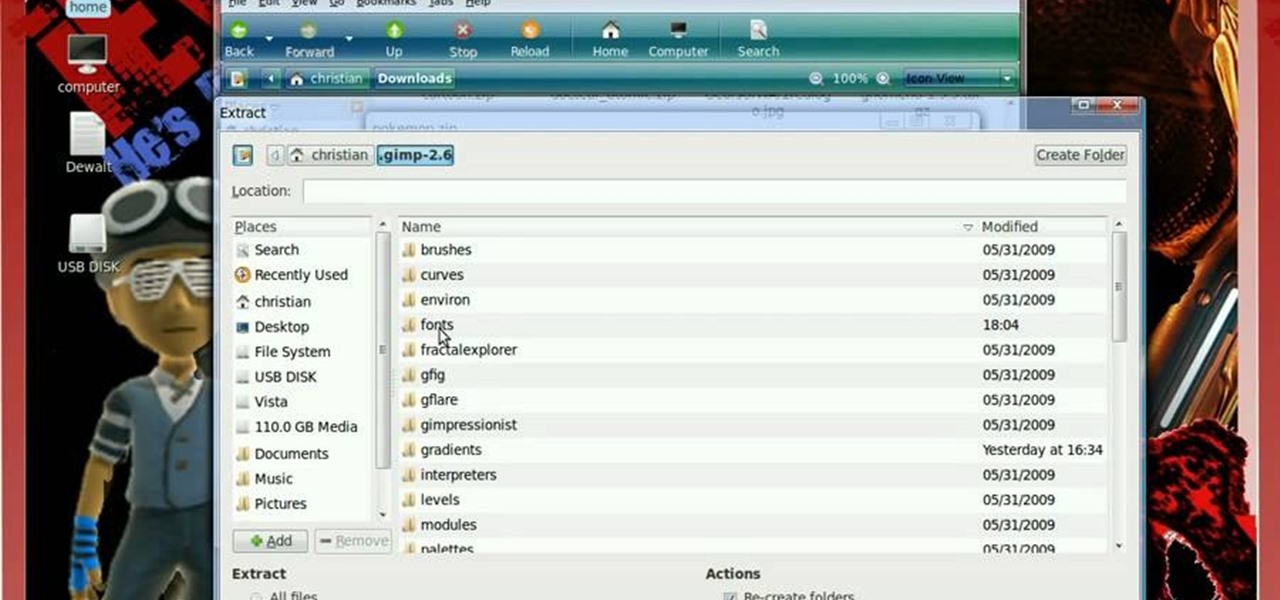
Linux is a fully functioning free operating system that you can download online. Just because you are using Linux Ubuntu doesn't mean your projects have to suffer or look less professional that those made on traditional operating systems like Windows or Mac OS X. In this tutorial, learn how to download and add fonts to the GIMP photo program on a Linux Ubuntu system.
This how to video shows you how to change the voice in the VoiceOver Utility program on a Mac. This will be useful if you want a voice that is more realistic or more understandable. First, open the program and choose the speech pane. On voices, click the drop down menu to choose which of the voices you want to use. At the side of this, you can change the rate, pitch, volume, and intonation. To change the voice settings with just the keyboard, press control option and command together. Use the...
This video tutorial shows you how to program your ESC for your RC vehicle. This is an important tutorial since this will help make your "remote control" vehicle be controlled by a remote. So sit back and enjoy!
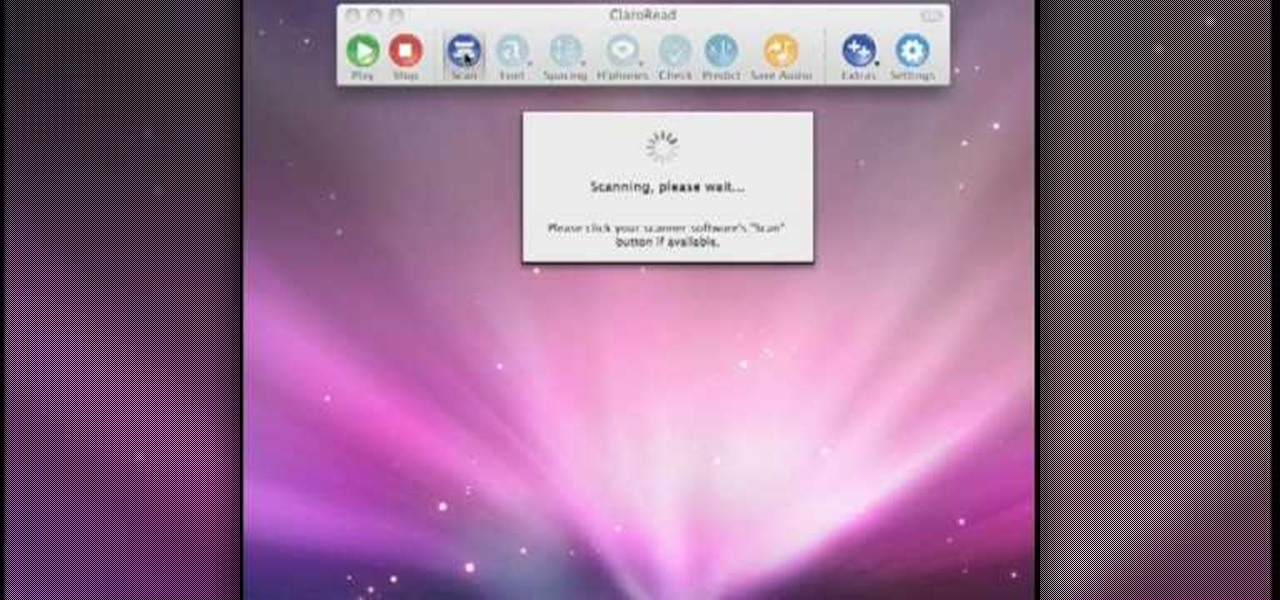
Scanning is an awesome, fast way to transport a document into your computer. But, what if you want to edit it once you've scanned it? Most scanner programs will import your document as a read-only PDF or image file. With this tutorial, learn how to use the program ClaroRead on a Mac to scan your document directly into Microsoft Word for editing. This will save you a lot of time and a lot of annoying formatting and copy and pastes!

In this how-to video, you will learn how to change the font size with Microsoft Word 2007. First, open the program and type in a sentence or two. Now, move your cursor to where the font name is. To the right of this should be a drop down menu with numbers. These are the sizes of the font. Highlight the text. Now, click and change the number to change the size of the text. The larger the number, the bigger the font will become. This video shows you just how easy it is to change the font with t...
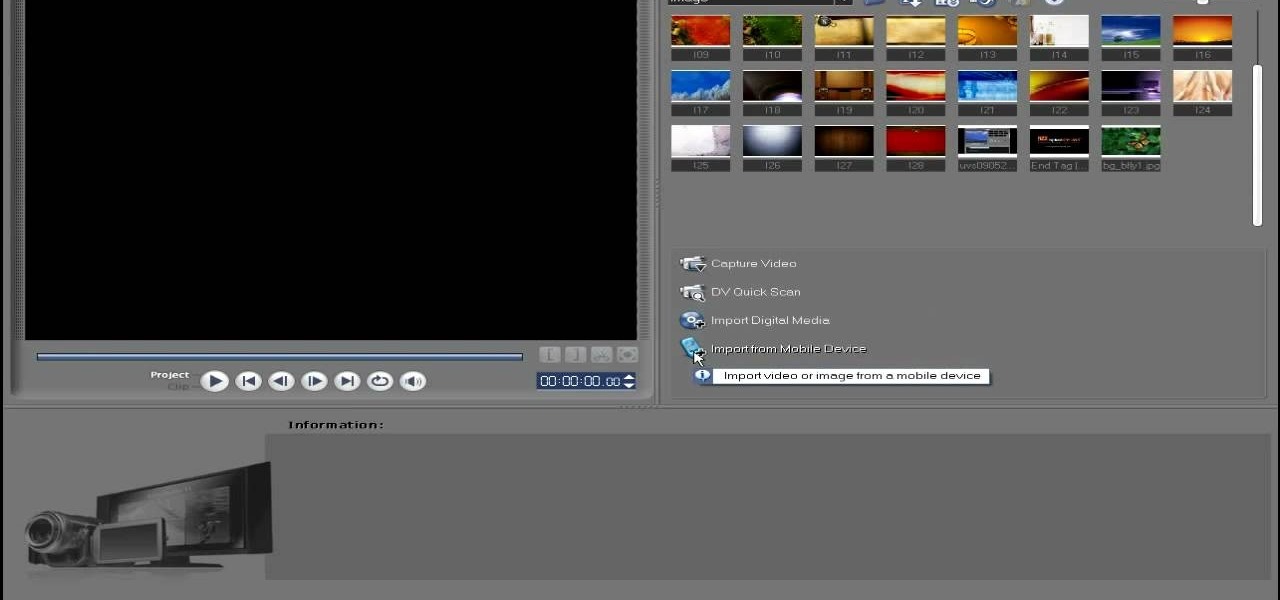
In this video tutorial, viewers learn how to import media from devices in Corel Video Studio. Begin by connecting your mobile device to the computer. It can be any device with a memory card or hard drive. Open the program and click on the Capture tab. Click on the option, Import from Mobile Device and select the device that you want. Select the file(s) that you wish to import and click OK. The program will then import the media to your selection window. This video will benefit those viewers w...
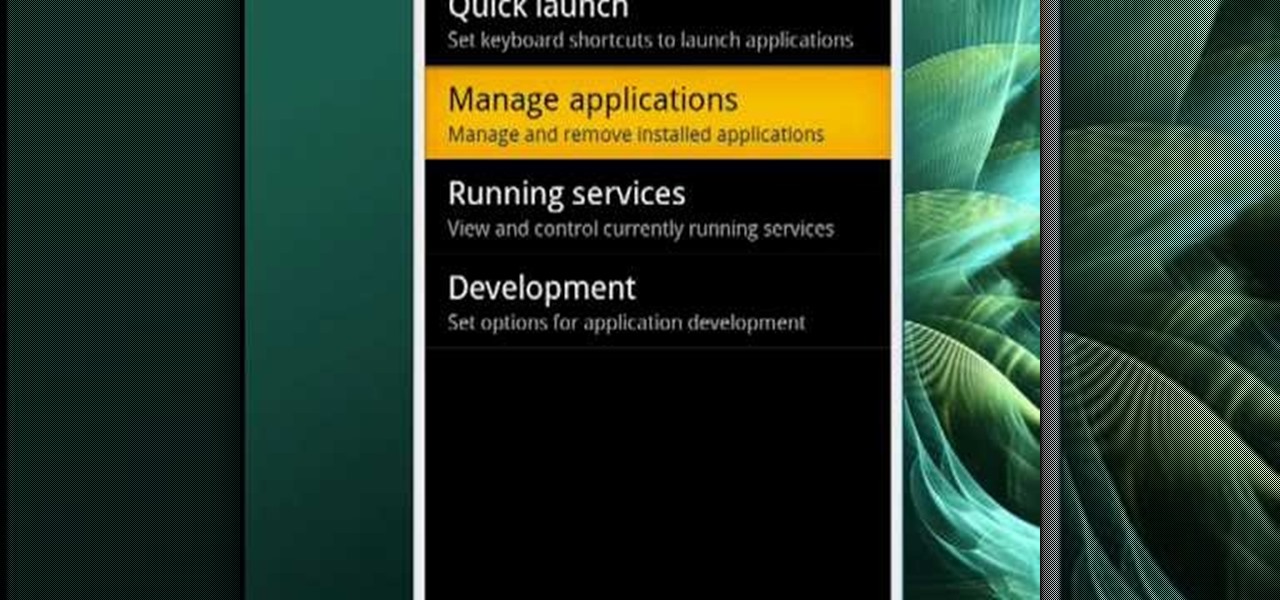
In this video tutorial, viewers learn how to uninstall the program on an Android phone. Begin by clicking on Settings and select Applications. Click on Manage applications. Now users will be revealed a list of all the applications that are installed on the phone. Simply scroll through the applications and select the unwanted application(s). Users will now see the information about the application, click on Uninstall. Now click OK and click OK again when the application is finished uninstallin...
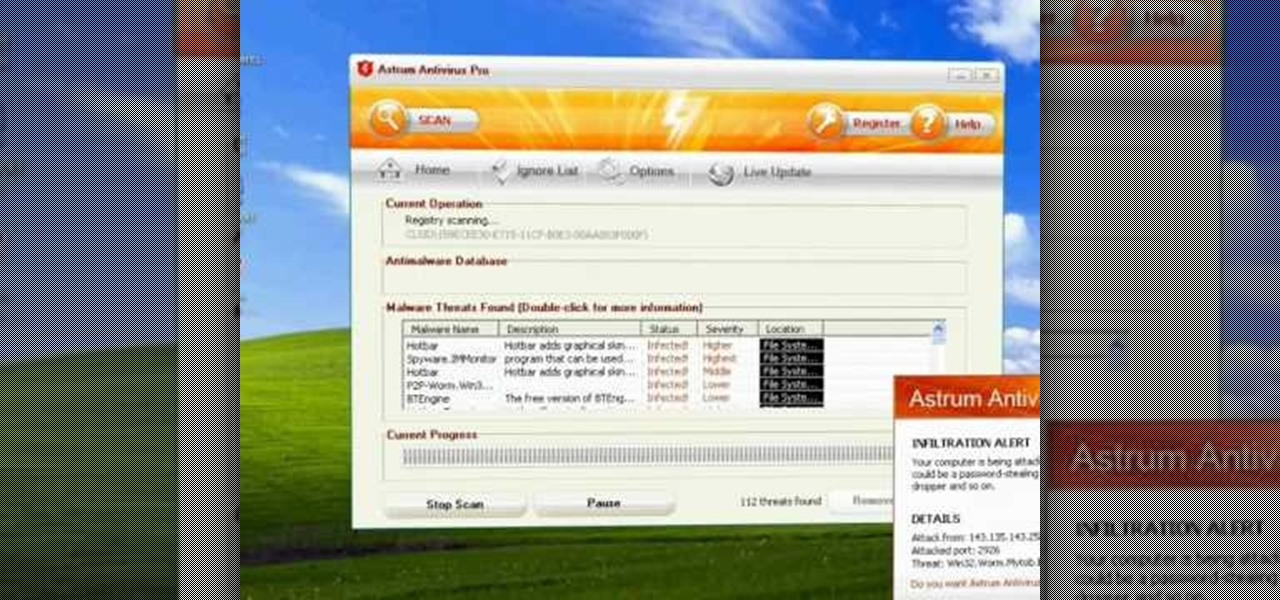
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...
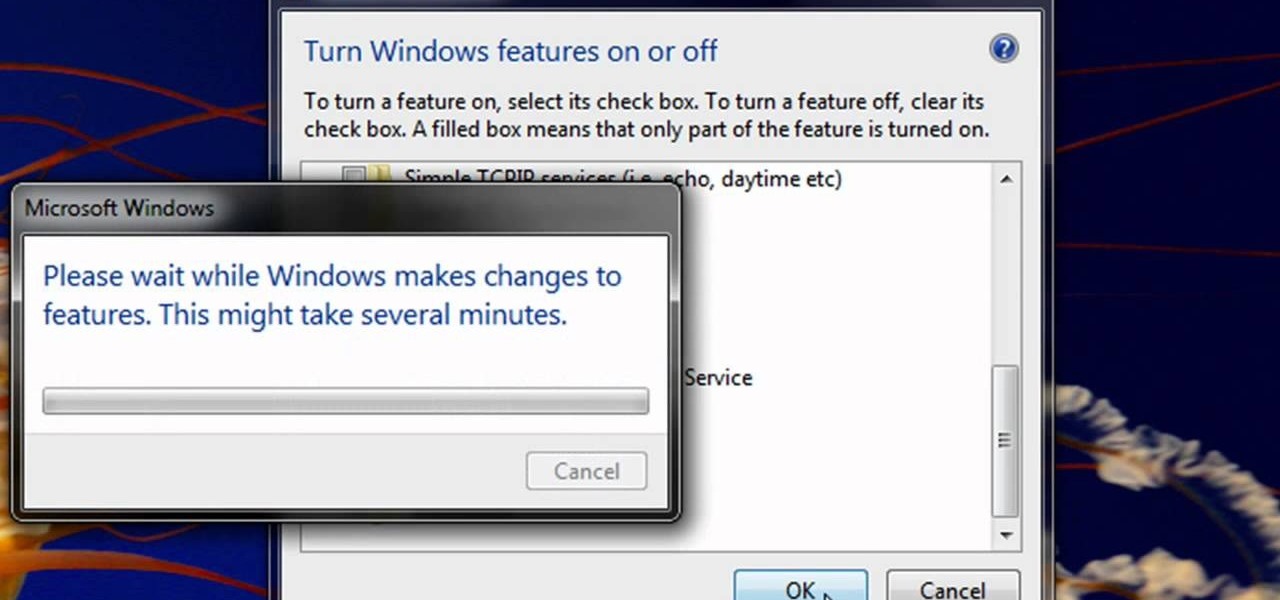
Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.
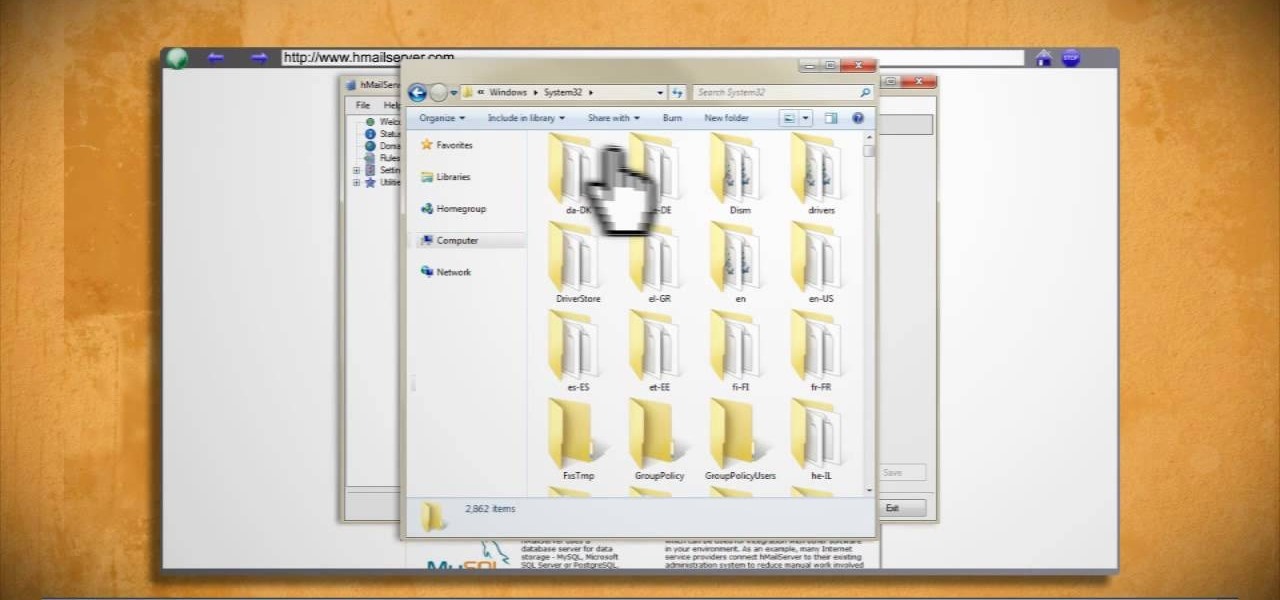
Learn how to make an e-mail server on your home computer to host your own web page and webmail service by following the steps outlined in this video tutorial. You will need a web server, an e-mail server, and a webmail interface. For the server, the most common program is WampServer, which you will need to download. Run through the installation process and grant the program access to your fire. Click on the new icon on your desktop and click Put Online and then Start All Services. This will g...

In this video from modernmom we learn exercises to reduce your breast size. You can't lose weight in your breast the personal trainer says. But when you want to lose weight, and you get into an exercise program that is consistent, you will begin to lose weight, and our bodies shed pounds all over, and because there is lots of fat in the breast tissue, you will notice they will get smaller. There's no one specific exercise though. But doing a walking program and watching calories will make you...

This video describes the process for inserting a 3D animation into a video clip. The video starts by outlining several software programs you will need to complete this project. Don't worry, the presenter gives web addresses and titles for all of the programs needed. After all software is loaded, the presenter beings inserting key frames and x, y coordinates to make the 3D animation move along the correct path. Finally, after the animation path is complete, the video shows how to render the fo...

VvCompHelpvV teaches you how to use a Nintendo Wii-mote to control your Mac computer. You need three things: a Mac with bluetooth, a Wii-mote and the program DarwiinRemote. You start the program and configure it so that it recognizes the Wii-mote Go to DarwiinRemote Settings, then Preferences, and configure your buttons. Go to the main window of DarwiinRemote and click the mouse mode and select on. You can use the Nunchuck as well, All you need to do is configure it in DarwiinRemote. Now you'...