It's no secret that more and more talented computer science gurus and programmers are turning toward high-paying careers in engineering. Today's engineers stand at the forefront of some of the world's most important and exciting technological innovations — ranging from self-driving cars and surgical robots to large-scale construction projects and even space exploration—and our reliance on these talented data-driven professionals is only going to grow in the coming years.

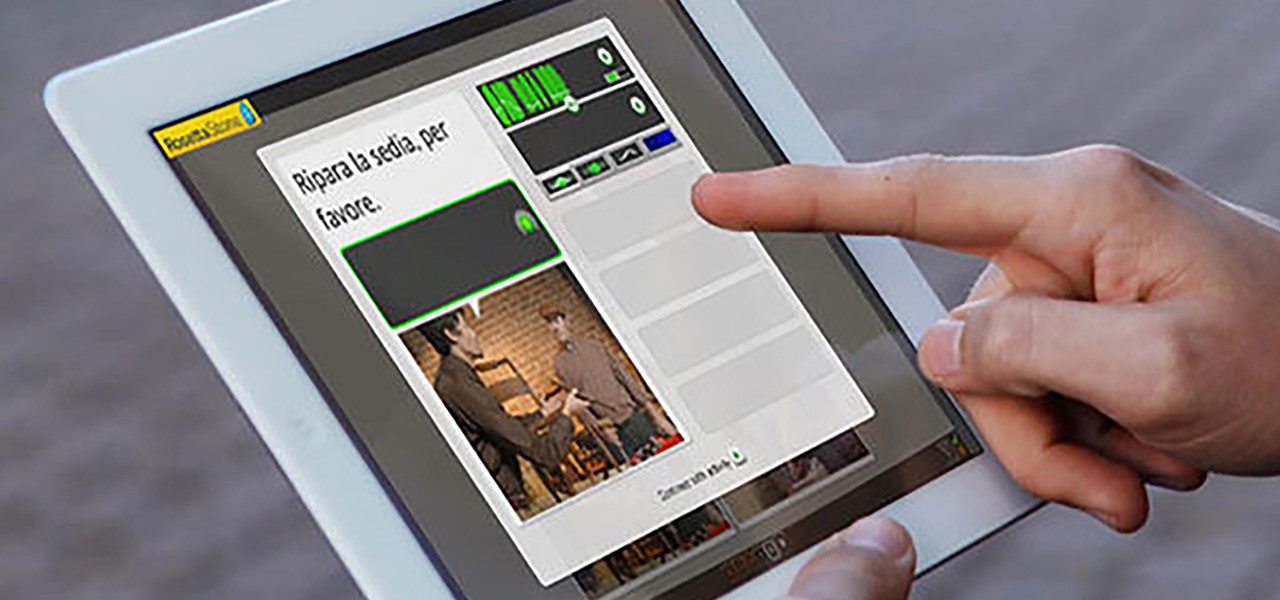
Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding education to get the skills you need to thrive.

Adobe sets the standard for graphic design. Since launching its subscription-based Creative Cloud in 2011, Adobe has consistently updated its suite of applications to serve the needs of the modern designer.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

As we settle into our new normal, this extra time provides a perfect opportunity to learn new skills. Speaking a foreign language is a great way to expand your cultural boundaries while also training your brain. Not only will you pass the time more effectively, but you'll also be doing something positive for your health.

Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actually help you, rather than just bring you further down.

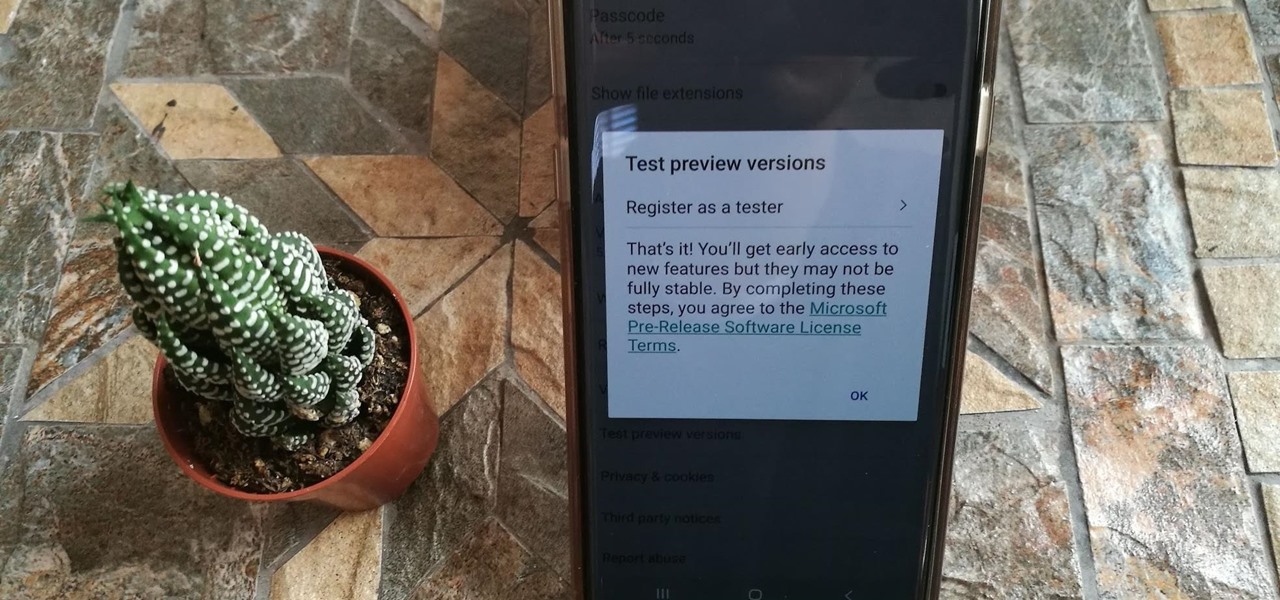
OneDrive has some really cool features, like being able to lock your files with a fingerprint. If you want to be on the forefront of these new features, you can sign up to the OneDrive beta testing program to get new feature before anyone else.

Many of us know that you can make a few bucks from Amazon by helping the company sell its wide array of products, but now there's a very different way to make a buck with the company, and it involves 3D technology.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

With the release of Android 9.0 Pie, Google's focusing on digital health. Digital Wellbeing is a new set of features designed to help you curb your own smartphone addiction. Starting now, the beta version is available, and Google's looking for testers.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

While Magic Leap may have plans to eventually introduce sign language translation for smartglasses in the near future, students at New York University have demonstrated that such a feat is possible today with a smartphone and a prototype app.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

With four major carriers, buying an iPhone X or iPhone 8 can be more complicated than you'd think. While Apple has its own iPhone upgrade program, AT&T, Sprint, Verizon, and T-Mobile all have versions of their own. Which plan you choose depends on your needs and, of course, your carrier. However, getting around to upgrading can be challenging to say the least.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.

Faraday Future's all-electric super sports car concept attracted a lot of attention at CES earlier this year, but now it is struggling to replace key driverless engineers and program directors who left the company amid its recent financial troubles.

Lyft officially laid its stake in the ground to develop driverless fleets following its Friday announcement, but how fast it is catching up to ride-hailing competitor Uber's driverless initiative remains to be seen.

An innovative new wound dressing has been developed by a research team at Lodz University of Technology in Poland that uses crustacean shells to create a bandage that packs an antimicrobial punch — and even more potential to help solve a global problem.

Have you ever had a burning sensation when you urinate? Low fever, back pain, and maybe cloudy urine? Male or female, it could have been a urinary tract infection. If it lasted long enough, the chances are good you went to the doctor for help. For about 20% of women, standard testing for a UTI does not reveal the presence of infection-causing bacteria, even though bacteria may be causing their symptoms. Well, a new test may provide better answers.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Oh, Uber. It's not often to hear your name in the news and have it mean something good. You're being sued, you're crashing, your driverless program is falling behind. But I have to hand it to you; when the world is crumbling around you, you continue to fight against it. You've even made it to Canada.

Mercedes-Benz's parent company, Daimler, announced their intention today to put self-driving taxis on the road in three years or less in a partnership with Bosch.

The big Waymo versus Uber trial isn't scheduled until May, but the heat between Uber and Waymo is rising fast; Waymo wants Uber's driverless trials shut down by a court injunction, unless ex-Google employee Anthony Levandowski testifies in court.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.