Adam from Chemical Reaction wants to show you a little movie magic. This video tutorial will show you how to shoot and edit a cool dance effect for your homemade film. You will see how to position the camera, set up the scene, shoot it twice (once with your legs dancing and once with you standing still), and then edit it in your favorite editing program to make it look like you're dancing without the top half of your body moving.

Watch this video tutorial to see how to make stop-motion animation with Windows Movie Maker. First, you'll have to take all of the pictures for your animation, with your action figures, Legos... dolls. Import all of your pictures onto the timeline in Windows Movie Maker. Now, just learn how to edit it and time it out right in the software program. Before you know it... one sweet ass animated video.

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel. All training and refresher courses must be done in accordance with federal and provincial regulations and the Canada Labour Code.

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video explains how you can use the MIX CONTROLE 10 from DJ-TECH. This mixer comes with the Mix vibes program enabling you to use the music off your PC and the mixer. Watch this DJ tutorial and you can learn how to use MIX CONTROLE 10 from DJ-TECH.

This tutorial shows you how to download, install and use the free program Stop Motion Animator. See how to set up and configure your animation settings, how to set the proper compression and then use the camera on your computer to shoot the frames for a stop motion animation. When finished, just output directly from the Stop Motion Animator software and you'll have your stop motion film done. Stop Motion Animator makes creating films as easy as this three minute tutorial.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn how to create a clown picture from an ordinary photo from a Photoshop expert in this free video series.

No matter the field you work in, tech dominates every industry in 2020, and that means that you can always increase your earning potential by adding valuable coding skills to your arsenal. Coding can lead to dream software development career paths, lucrative freelance work, and it can be an impressive boost to your résumé. Now, you can learn these valuable skills at home with The Complete One Hour Coder Bundle, an offer at an unmissable 97% off its usual price, at just $34.99 (usually $1,200).

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

As a native of Alabama, Apple CEO Tim Cook has a special place in his heart for the state. He also empathizes with the struggles that African-Americans have historically faced in the state, particularly during the 1950s and '60s civil rights era.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

When it comes to the business of augmented reality, companies that aren't already introducing new products or apps are focused on producing the AR technology of the future. But in the realm of real products and apps, Magic Leap continues to show off what its headset can do, this time via a new app that transports users to the ocean's depths.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

Snapchat is joining the ranks of Netflix, Hulu, Amazon, YouTube, and Apple in the trend toward streaming original programming, but with a twist that rings true to its roots.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

The march towards mainstream adoption of eSIM technology got a massive boost with the arrival of the iPhone XS, XS Max, and XR. We're now one step closer to ditching physical SIM cards altogether. If you're on the fence about this new technology, you may be surprised by the benefits it brings to the table.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Hours after iOS 11.4.1 beta 4 was released on Monday, June 25, Apple's webpage for its public beta software programs was unavailable because of an "update." Sure enough, that meant the public beta for iOS 12 was being prepped to drop shortly thereafter, which is exactly what happened. In other words, you can now install iOS 12 on your iPhone without a developer account!

Between acquisitions, hirings, patent applications, and insider reports, all signs point to Apple building a smartglasses product that could ship as soon as 2020, but the company has not officially confirmed such plans.

Continuing to take the steps necessary to reign supreme among the top game engines of the world, with a steady stream of major updates, enhancements, and new features, the team at Unity are keeping the user base in a regular state of surprise. At this rate, it's almost like Christmas every few days.

Every dollar that comes your way is a blessing, especially when it comes to trading in the volatile world of bitcoins. Thankfully, Coinbase rewards you for sending much valued customers their way, giving you more money to feed your cryptocurrency trading needs.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

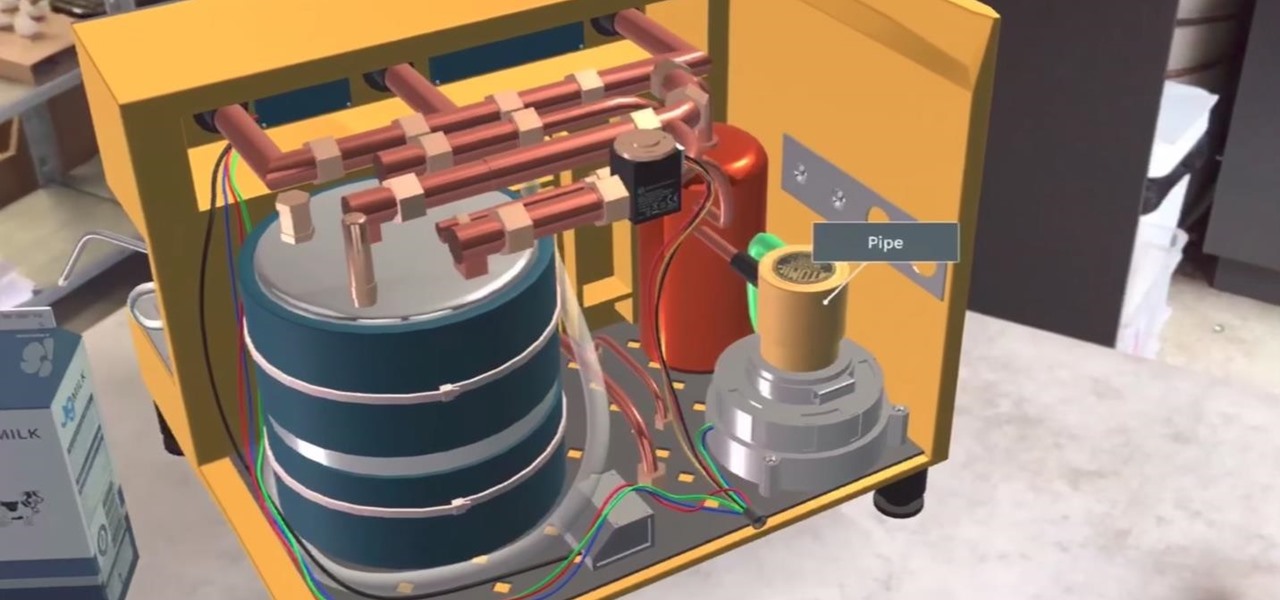
JigSpace, a company that uses 3D renderings to give instructions, showed off a fun new way to learn how things work using Apple's ARKit. The video released shows the anatomy of a range of things, including an espresso machine, an Archer Hb Plus chair, and the manual transmission of a car. Not to mention, they also used ARKit to show a 3D how-to of removing an iPhone's SIM card.

Get ready to step up your game, explorers! Google Maps is releasing an update for its gamified program to encourage reviewing of businesses and other locations within the Google Maps app.

It's about time people acknowledged that judging drug users would do nothing productive to help them. In the US this week, two new programs are launching that should help addicts be a little safer: Walgreens Healthcare Clinic will begin offering to test for HIV and hepatitis C next week, and Las Vegas is set to introduce clean syringe vending machines to stop infections from dirty needles.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

Somewhere around 600–800 million people in the world are infected with whipworm (Trichuris trichiura), an infection they got from ingesting soil or water contaminated with feces of infected animals or people containing the parasite's eggs.

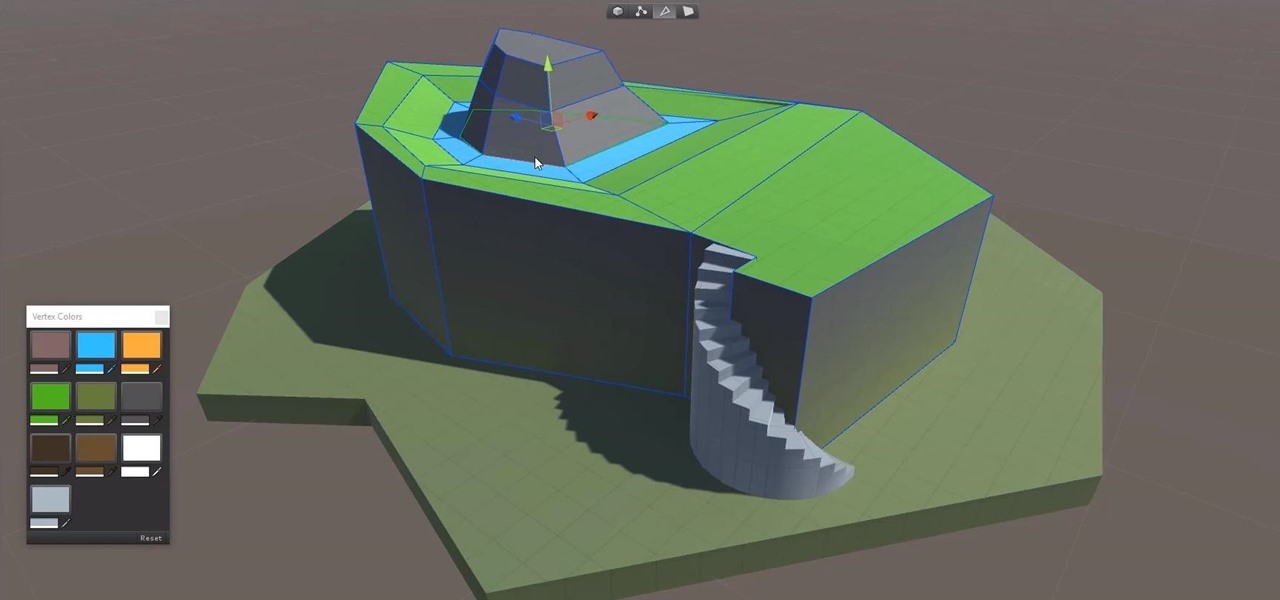
3D modeling is usually a very long and complicated process. Manipulating the thousands to millions of vertices, faces, and triangles to the correct shape you want is just the first part of the process, and can take a good while depending on the level of detail needed. From there, you need to texture the model by applying the UV coordinates and placing the textures in the correct places. And all of this isn't even including the process of creating normal maps.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

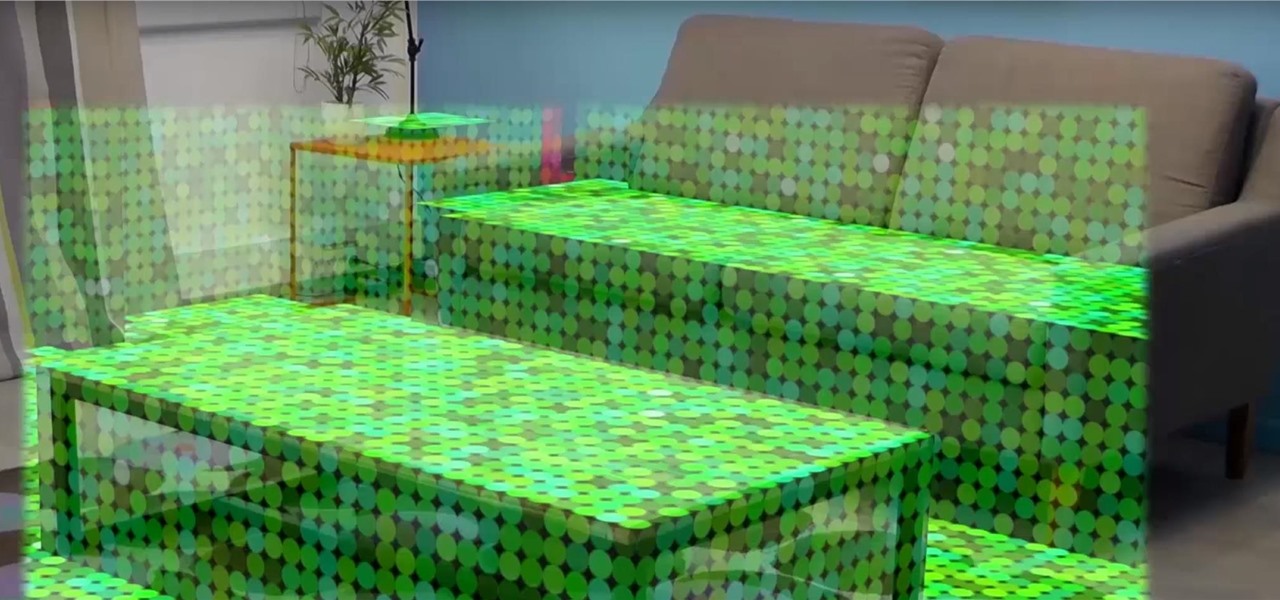
Once you've designed some holograms with HoloLens, you'll need to get them to interact with the environment. That's where Spatial Mapping comes in. There are five basic purposes for using HoloLens's Spatial Mapping with your app:

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.