Most people have multiple email addresses these days. Gmail is one of the more popular services, but did you know you can access your Gmail account using the Mac OS X mail program? Not only is it possible, but it is incredibly easy!
In this video tutorial, viewers learn how to turn off the system firewall without admin privileges. Begin by clicking on the Start menu and open he Run program. Type in "system.msc" and click OK. Scroll down the Services list and look for Windows Firewall. Double-click on it and under the General tab, click on Stop. Then click Apply and OK. This video will benefit those viewers who use a Windows computer and would like to turn off the firewall, even if they are not running the administrator a...

This video demonstrates how to surf the web without ads. The first step is to download Mozilla Firefox. Go to Get Firefox and click on 'free Mozilla download'. Do not select on e-bay or campus edition. Download the file and install the program successfully. Go to Get Firefox once again. Select on add-on and type in 'ad block' in the search tab. The results come up and select on 'Adblock Plus'. Install the program. Restart Firefox. ON the top right corner of the window a small red icon that re...
This is a tutorial that will learn you how to extract or unzip files on a Mac using UnRarX. First go on the site mentioned in the video scroll down and click on download. Go where you selected to download the file and open the program. Drag all the files you need to extract or unzip there then select the folder or destination where you want to get the files and the program will do all the work. The file you have selected to be unzipped or extracted will be in the place you selected and ready ...

Microsoft began shipping the Development Edition of its much-anticipated HoloLens—the world's first untethered holographic computer—back in March. As the name implies, it was only available to developers (we got ours near the end of April), but Microsoft has recently opened up the program to anyone who wants one—not just developers.

Your iPhone might have a great camera, but it can be irritating to get things like exposure and focus right when your fingers are all over the 'viewfinder.' The Pictar aims to change that by making your iPhone as much like a DLSR as it can, keeping your fingers from obstructing your next great photo.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

This is a nice project that you can continue to work on and modify as you learn more Arduino projects. The Instructable linked below goes through the complete build for the Bluetooth-enabled robot seen in the first half of the video.

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

Welcome to the first coding tutorial on SQL here on Null Byte. Typo:

Welcome back my friends !! Today we'll go through the second part of this C# series

Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Screenshots are an indispensable tool when it comes to relaying information about what's currently showing on your monitor. Whether you need help troubleshooting an issue or you just want to save and share a protected image, screenshots are often your best bet.

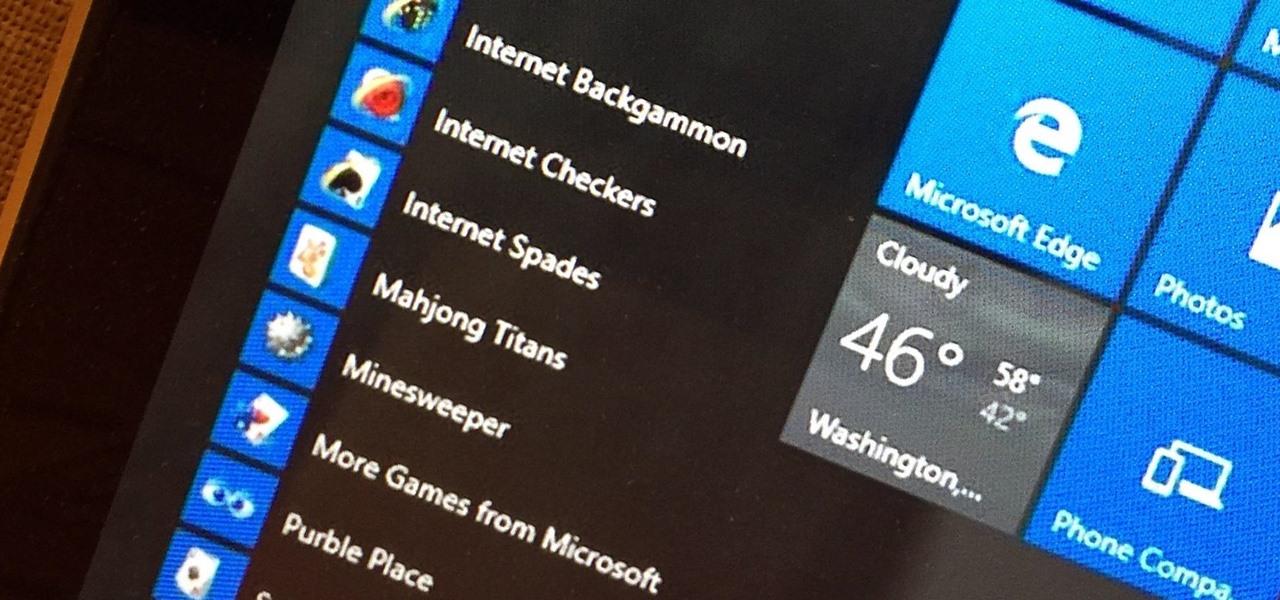
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

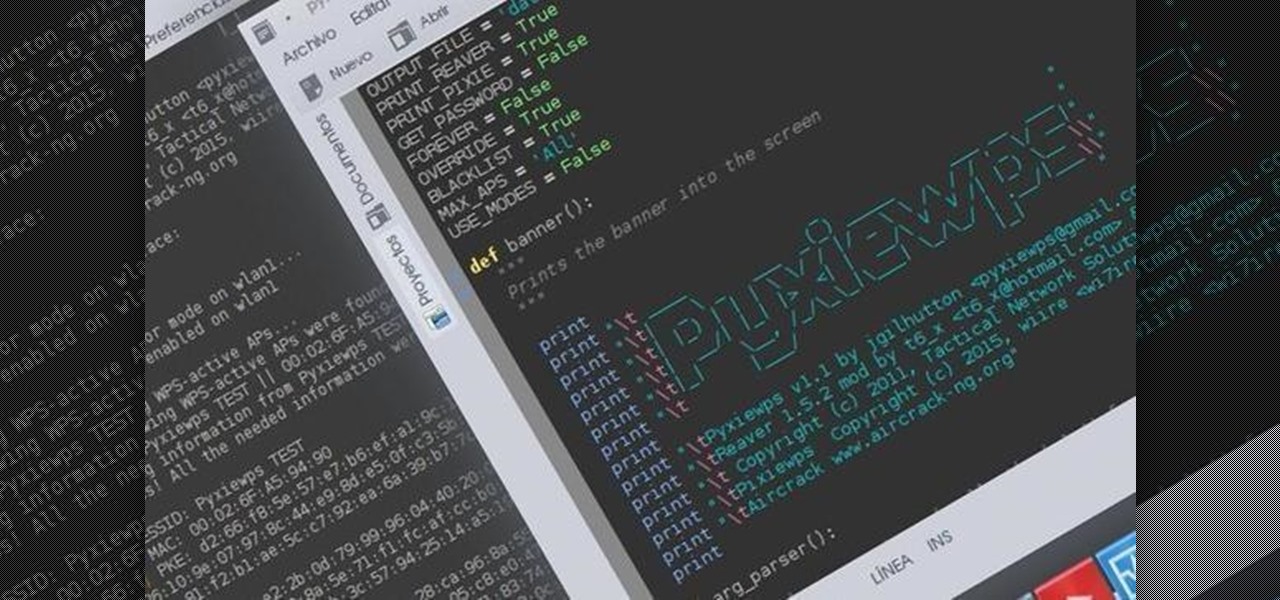
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

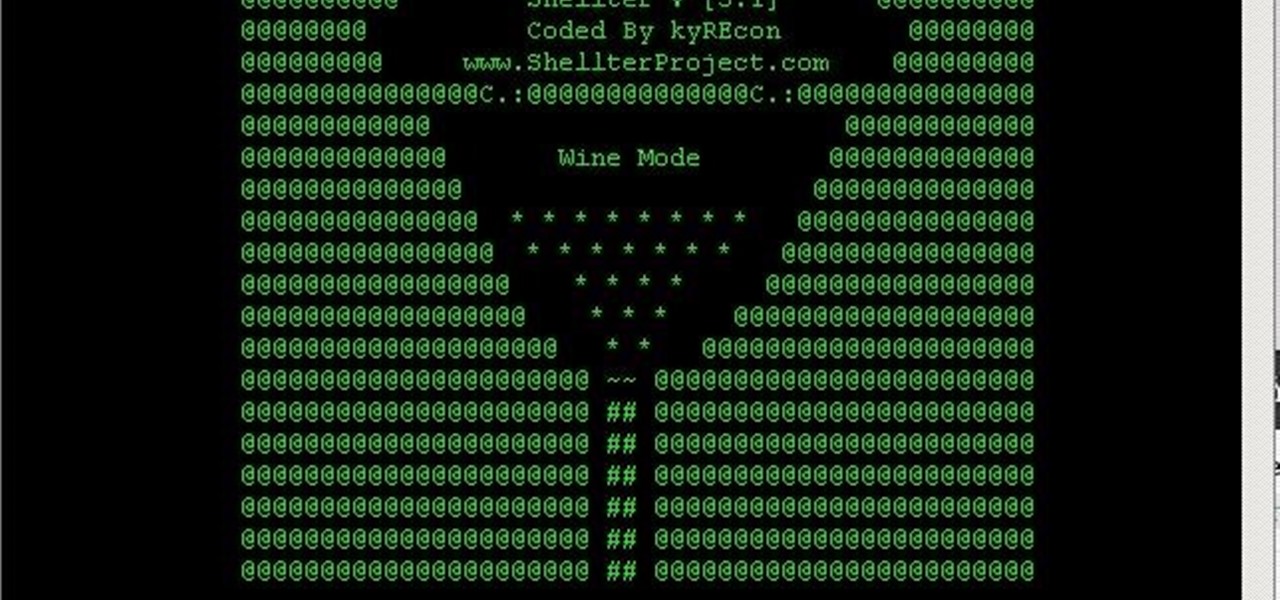
You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

There has been a huge shift over recent years to alternative medicine as people get disillusioned with conventional medicine to overcome anxiety. Natural and herbal supplements are becoming popular as people re-engage with nature. The list of potential side effects from drugs and the rebound effects from withdrawing often make the thought of taking medication unpleasant. Often the promise of how effective the medication can be is exaggerated or it simply does not have the effect it should bec...

Whether it's delivery drones or getting the U.S. Postal Service to ship packages on Sundays, Amazon continues to remain innovative and ahead of the game, as further evidenced with their mobile app, Amazon Underground.

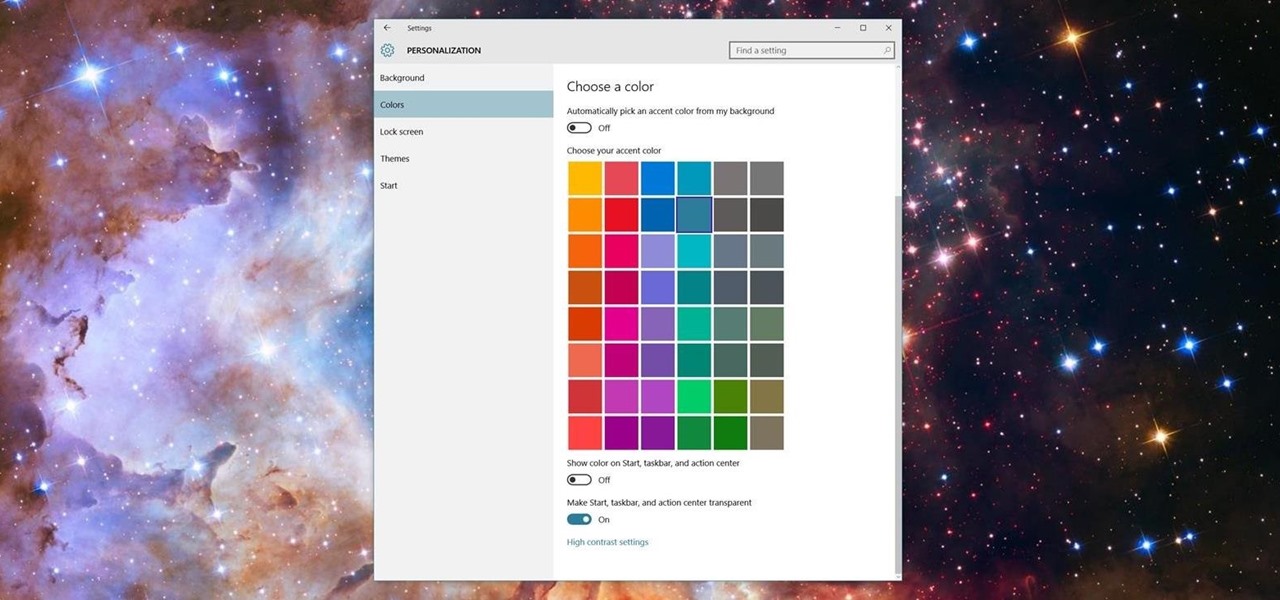
Microsoft has been listening to user feedback, and they've finally done something about one of the most common minor gripes with Windows 10. As of build 10525, there's now an option for changing the title bar color in apps, so you won't have to use this old workaround to personalize your window coloring anymore.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

Windows 10 makes it a cinch to change the lock screen background: simply go to Setting -> Personalization -> Lock screen, then change the background to whatever you'd like. But, trying to change the login screen background—the screen where you enter your password—was a long, complicated, and possibly dangerous process. Luckily, developer Krutonium has published a tool that automates the entire process, and it's very easy to use.

I wrote a python script that allows you to easily ask what service runs on a specific port and vice-versa. Now, I am sure that such a program already exists on our lovely linux OS's, but... I didn't think of that before I started, and haven't found it yet. So if you haven't found it yet either, maybe you'll find this of some use. It's just called getport. If I have a port number, and want to know what services run on that port, I do:

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

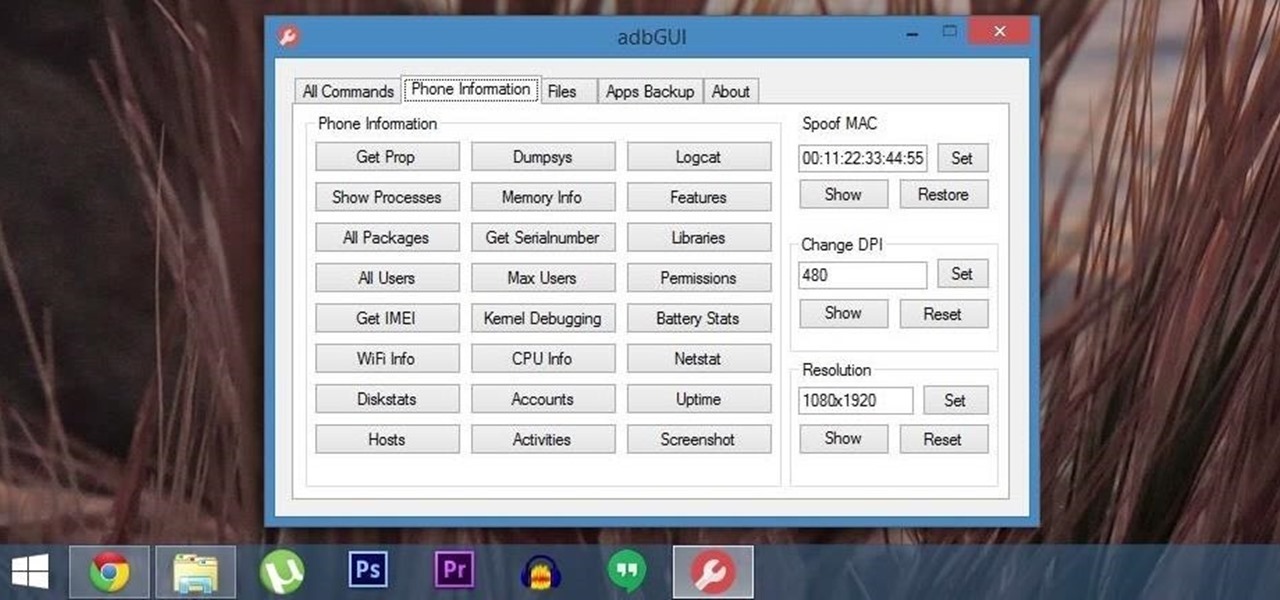
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!