The stock music player on the iPhone hasn't changed much since its inception. Sure, with the recent iOS 6 update the design became sleeker, but it's not really what you'd expect from a top of the line smartphone. And when I say "MEH," it isn't directed towards the Kendrick Lamar album (which is awesome). It's the layout of the application, the lack of gesture control, and the sometimes tedious job of shuffling through certain albums and artists.

The Geminid meteor shower happens every December and has been observed for over 500 years. It's is also known as Winter's Fireworks because when viewed from the right location, there are enough meteors to light up the whole night sky, and some of them can even be different colors. The shower appears to come from the Gemini constellation, but is actually caused by Earth passing through the tail of dust and debris left behind by the comet 3200 Phaethon.

Over the past few years, indie game developers have gathered together to release their products in the widely popular Humble Indie Bundle, a collection that gamers can purchase for whatever price they want. It's a win-win for both. Developers get more exposure for their games, and customers get tons of games for whatever they could afford. Heck, charities even get a little piece of the pie.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

The pumpkin is everyone's favorite cucurbit come Halloween time, and while there are only a few types of Halloween-friendly pumpkins out there, there is definitely no shortage of what you can do with them.

For some people, a costume is just a necessary prerequisite to get into Halloween parties. If you're female and you're going the sexy route, it's not too hard to find something to wear, but transforming yourself into something terrifying takes a little more work.

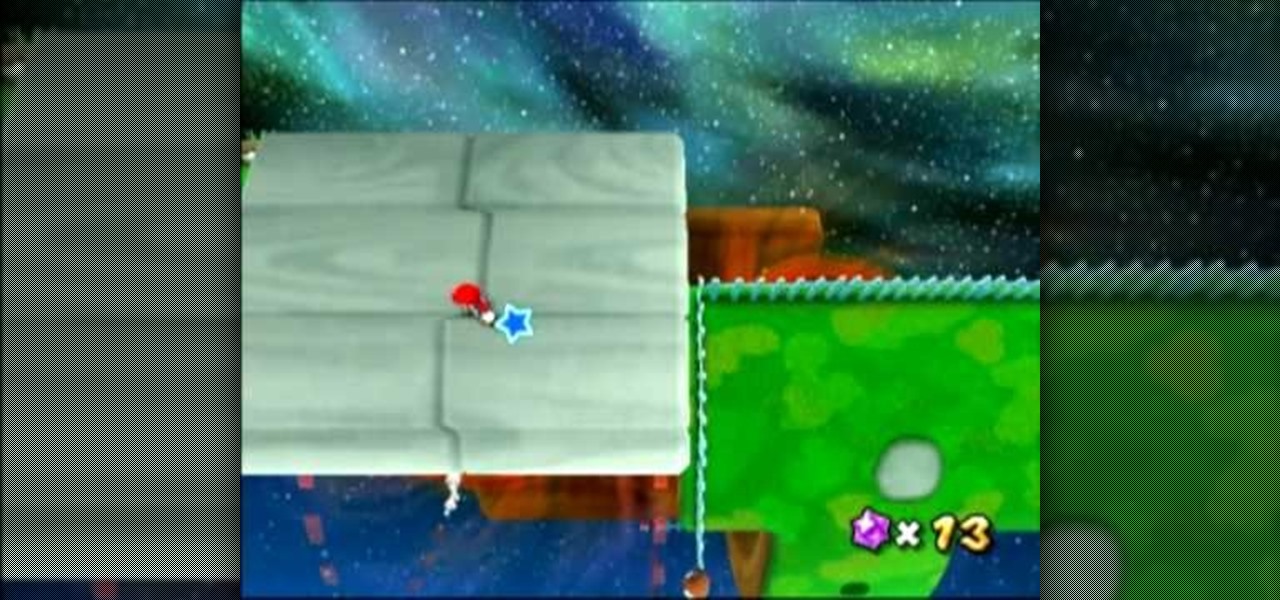
If you think you can get all 242 stars in Super Mario Galaxy 2 on your own, you've got another think coming. It's a lot harder than it looks. Sure, getting those first 120 normal stars seem like an easy enough task, but finding all of the remaining 120 green stars is the hard part. But then you have those last 2 that are even tougher.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

This will hack speed on Typing Maniac. Sometimes slowing down the process is the only way you'll win. If that's the case, then use Cheat Engine to slow down time and become the ultimate typer.

Cheat your way to the top of Typing Maniac with Cheat Engine. Cheat Engine solves all of your playing woes by doing all of the work for you.

Bejeweled Blitz is a hard game to play, but easy game to cheat. These new hacks are sure to get you your next record breaking game for the whole Facebook community to admire.

Tower Blocks is a Facebook game that allows you to test your speed at building the tallest tower ever! Watch this video tutorial to learn how hack Tower Blocks on Facebook (09/02/09).

This video series will teach you tips, ideas and techniques on how to catch and throw a disc in fun unique ways as well as the rules and regulations of disc golf. It will explain the history of the disc and how the throw has evolved over the years and, as a bonus, instructions on how to play disc football and it's rules.

In this video clip series, our expert will discuss the game of solitaire in both traditional, table-top games and computer versions. Learn the basics of the game, tips for improving the game and information on the foundations of the game and its rules. Tips for keeping score, dealing the cards, shuffling and playing through the stacks are included, as well as bonus footage of fun tricks to play with the card deck and Vegas pointers.

When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

It looks like Pokémon GO players may get a surprise gift from the game's developer, Niantic, this holiday season.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

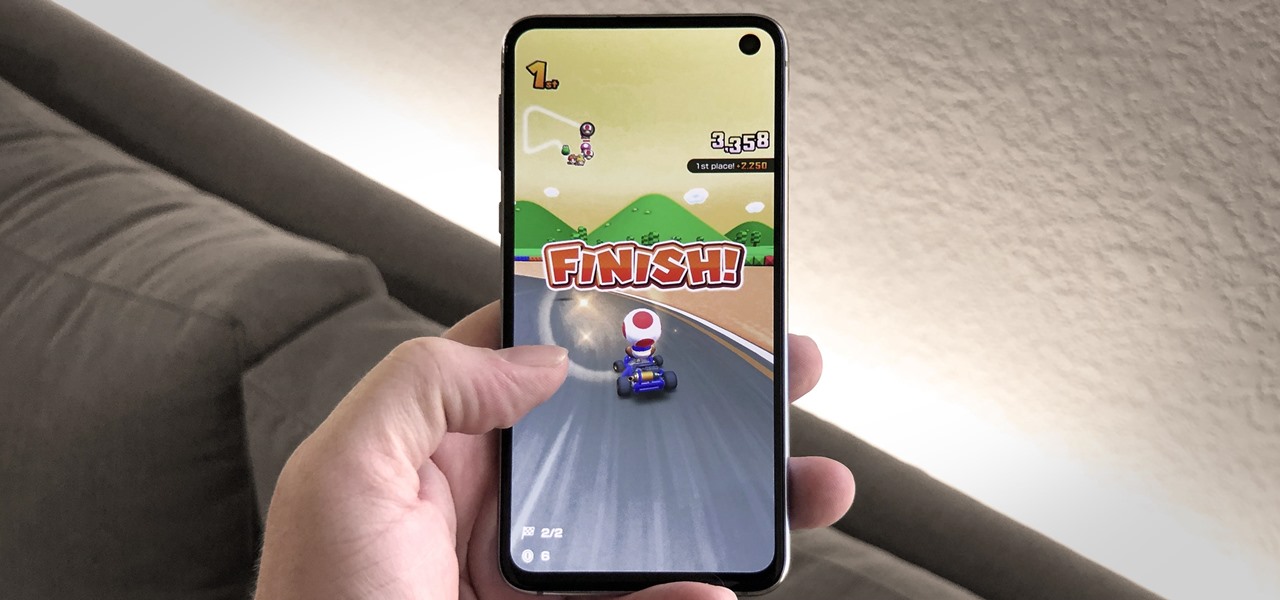
So you can't seem to win in Mario Kart Tour? Whether it's your first game in the Mario Kart series or not, Mario Kart Tour can be challenging, especially when you don't know the tracks. Instead of struggling your way through the cups, try out these five tips to get a leg up.

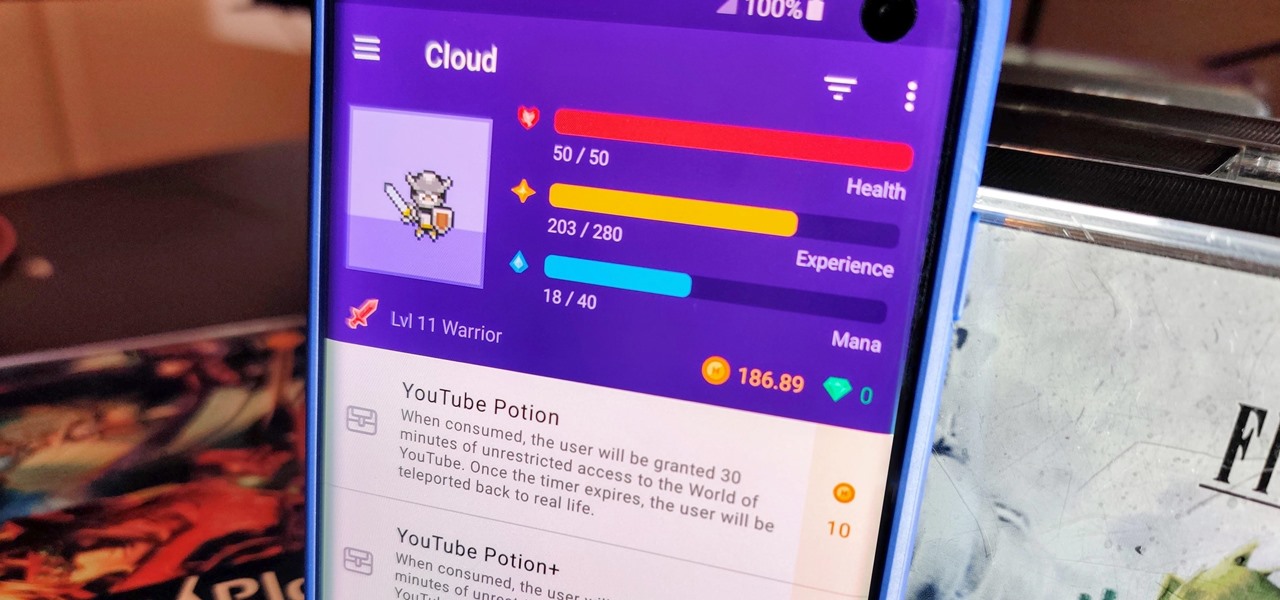
When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose motivation. What if you could take those tasks and turn them into something awesome instead? Now you can.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

With Mobile World Congress fast approaching, all eyes in the industry are set on Samsung's Galaxy S9 announcement on February 25. While leaks and rumors about the S9 and S9+ have been flooding in for quite some time, we're getting a much clearer picture of these handsets as the announcement draws near.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Thanks to ever more powerful smartphones — the iPhone X with its advanced A11 processor and the Galaxy Note 8 powered by Snapdragon's 835 come to mind — the mobile industry is fast closing in on consoles and PCs with regards to gaming. Game developers have been aware of this fact, and have ported many games once dedicated to computers onto our handheld devices.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

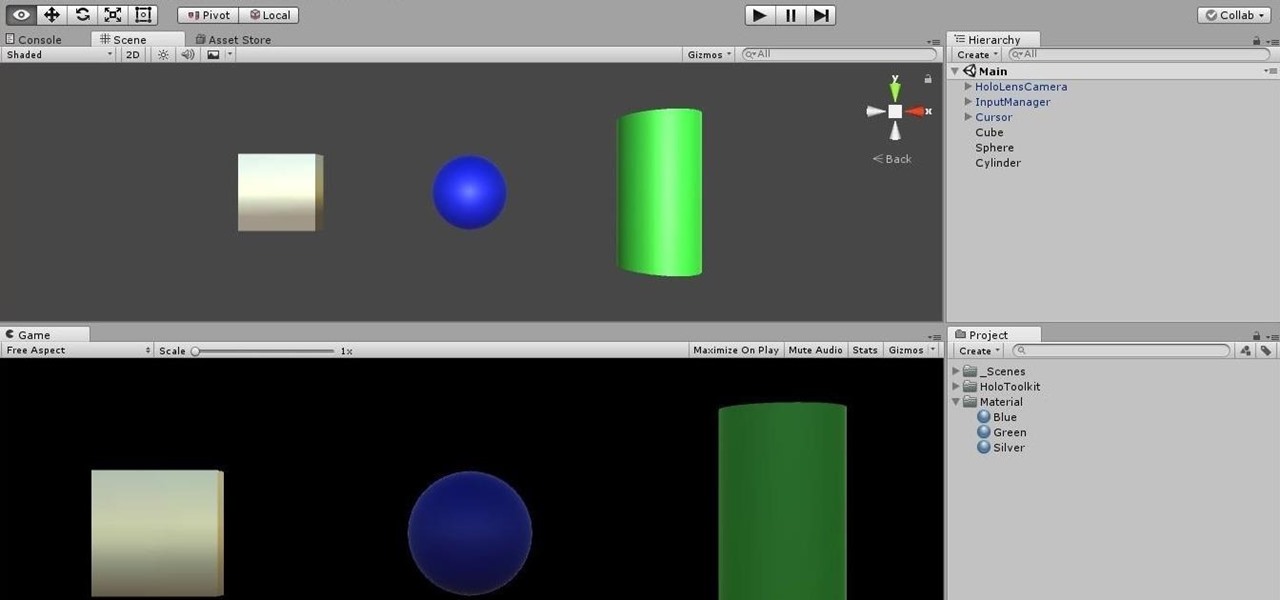
Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

The new Samsung Galaxy S8 and S8+ are two of most head-turning phones we've ever seen, thanks to gorgeous build quality and a seemingly bezel-less Infinity Display. Combine that with flagship-grade internals for top notch performance, and you can almost guarantee that Samsung has a hit on its hands—which means it's probably not going to be easy to get your hands on one of these beauties.

Pumpkin pie is a symbol of autumn, and it's the traditional dessert to whip up for your fam when Thanksgiving Day arrives. But year after year of the same old thing can be a total bore if you're not a strict traditionalist. So, we found 8 unique ways to make that pie a little less snooze-fest and a little more interesting.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

LG announced their latest high-end device on September 6 and its specs are pretty amazing: The new V20 sports three cameras, two displays, three microphones, four DACs for high-end sound, and it's all powered by a removable battery.

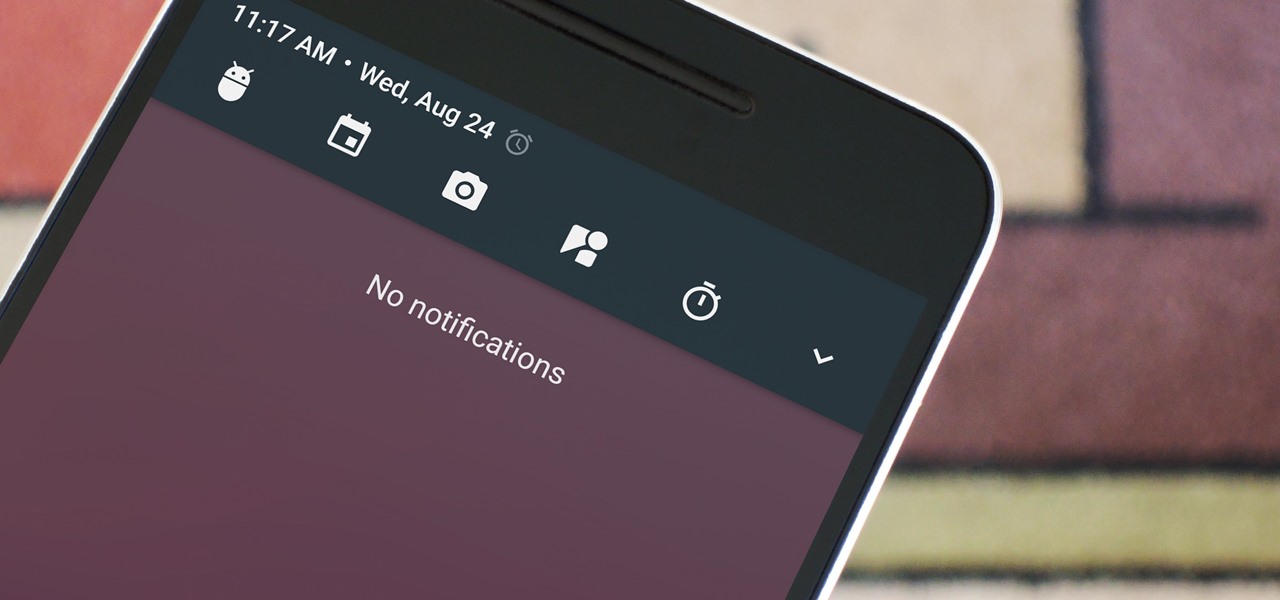
Among the many changes in Android 7.0 Nougat, a less talked-about feature may very well be one of the most interesting. As part of a new system-wide API, apps can now create their own Quick Settings tiles, and it doesn't require any complicated workarounds like it has in versions past.

Summer is a time for sangria sipped on the patio, enjoying the fruity refreshment with a friend while the smell of barbecue wafts from a distance. It's the perfect way to spend a lazy, hot August afternoon.